Could you be a threat hunter? Humio and Corelight make it easy for customers to get started with threat hunting

This blog was originally published May 20, 2021 on humio.com. Humio is a CrowdStrike Company.
Threat hunting can seem like an intimidating discipline to many. Something that is shrouded in mystery and the preserve of highly experienced and trained cyber specialists in companies with huge resources. Operating a world-class 24/7 threat hunting team like the experts in CrowdStrike’s Falcon OverWatch is far from simple and in reality many companies never even try. We want to encourage people who are new to threat hunting to give it a go and make it easy to get started. You won’t become an expert overnight but threat hunting even as a beginner can deliver some useful outcomes for companies.
With the release of a new package in the Humio marketplace we are providing an easy way to get started with the basics of threat hunting amongst your Corelight network data. Network data is a great source for threat hunting and we hope this blog helps you get started on your threat hunting journey.
With a little guidance on the basics and access to the right technology we believe Threat Hunting is something that every security team can get value from.
What Is Threat Hunting
Most organizations will have security monitoring technology such as a SIEM, that will be configured to search their logs for evidence of known threats. Once an alert is triggered a SOC analyst may then do further log searching and analysis to work out what is happening and how to respond. These disciplines are fairly static and reactive.
Threat Hunting is the practice of proactively searching for potential signs of an attacker in your environment. A hunt will usually start with a hypothesis or the observation of an anomaly which is then investigated. Once underway a hunt can pivot and change direction rapidly – following the instincts of the hunter and leveraging their understanding of attacks and what is normal for their organization.
To get the most long-term value out of threat hunting, customers should establish a basic methodology and ensure that every hunt hypothesis and outcomes – whether successful or not – are documented. The Falcon OverWatch team have developed their own methodology called SEARCH which leverages the unique and advanced properties of the Falcon platform.
A more generic threat hunting approach that could form the basis of an initial methodology for a customer new to threat hunting is outlined in the below diagram.
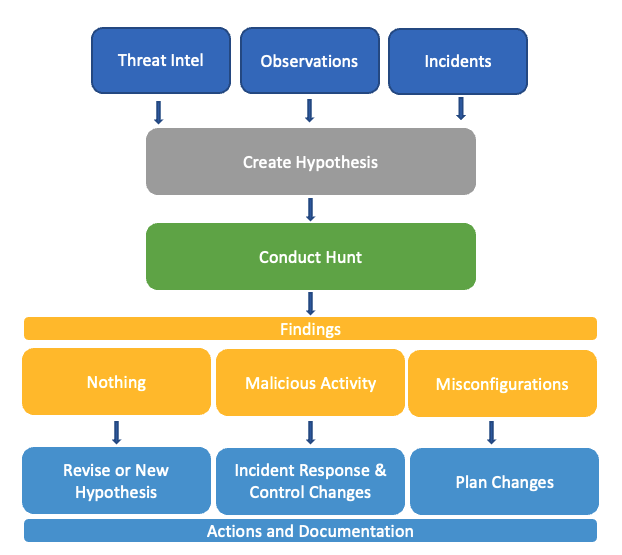
The outcome of threat hunts can often be surprising and the benefits can be significant and wide reaching. Clearly detection of malicious activity would trigger an incident response process and result in new detection rules and improvements in prevention controls.
In many cases threat hunts identify activity that is not a sign of a successful breach but may highlight some prevention control weaknesses and room for security improvements. Finding and fixing these types of sub-optimal configurations proactively boosts defense measures and drives a deeper understanding of current control effectiveness.
Often threat hunts triggered by observations of anomalous behavior or statistical outliers can uncover operational misconfigurations that don’t necessarily present a security risk but do explain weird or intermittent problems. Identifying these and solving them through the required changes can improve operational stability and performance.
So threat hunting is great for discovering security improvements but can also really help increase understanding of systems at a deeper level than ever before and finally uncover the root cause of some of those lingering, difficult to pinpoint issues that frustrate IT teams.
Why Corelight Data Is So Valuable to Threat Hunters
Corelight network sensors are available as software or appliances and use a specialized version of the open-source Zeek (fka Bro) framework to provide detailed insights into what is happening in your network. This rich source of data covers over 35 different protocols and hundreds of different log fields, making it a valuable data resource for security operations.
Packets don’t lie and at some point every attacker and every piece of malware is going to need to use the network. So Corelight data is a great place to go hunting and provides effective detection across a wide range of the ATT&CK tactics with particularly good coverage across a lot of techniques within Command and Control, Lateral Movement and Exfiltration.
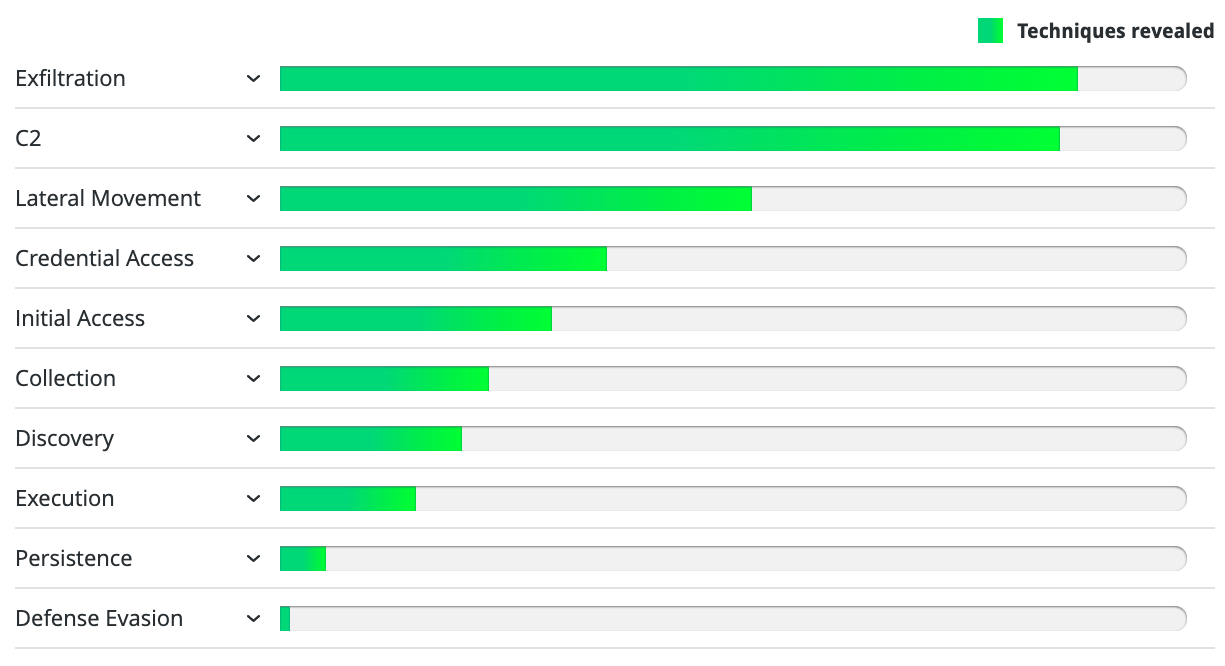
New Threat Hunting Guide From Corelight
Corelight just released a new Threat Hunting Guide that helps organizations realize the value of Corelight data for security threat hunters. The guide references the ATT&CK framework and explains what to search for to uncover potentially malicious activity that warrants further analysis. Download the free guide Corelight Threat Hunting Guide.
New Humio Package
Humio has created a new package of pre-defined content for Corelight available in the Humio Marketplace. The package is free for all users and can be installed directly from the marketplace with a couple of clicks. It includes around 60 different saved searches and is designed to accompany the new Corelight Threat Hunting Guide. All searches are tagged with the relevant ATT&CK tactics and techniques, making it easy to work out which searches are relevant for each section of the guide.
Get Started – Threat Hunting with Corelight and Humio
Forward your Corelight logs to Humio
If you don’t have Humio – register for a free trial account on our cloud service
If you don’t have Corelight then a great way to try it out is to apply for the Corelight@home package which provides a Raspberry Pi based sensor that you can install on your home network and send your logs to Humio for analysis – you can register for interest here Corelight@home.
If you have Corelight but don’t already have your Corelight logs in Humio then follow the instructions here.
Install the Humio Package for Corelight Threat Hunting Guide
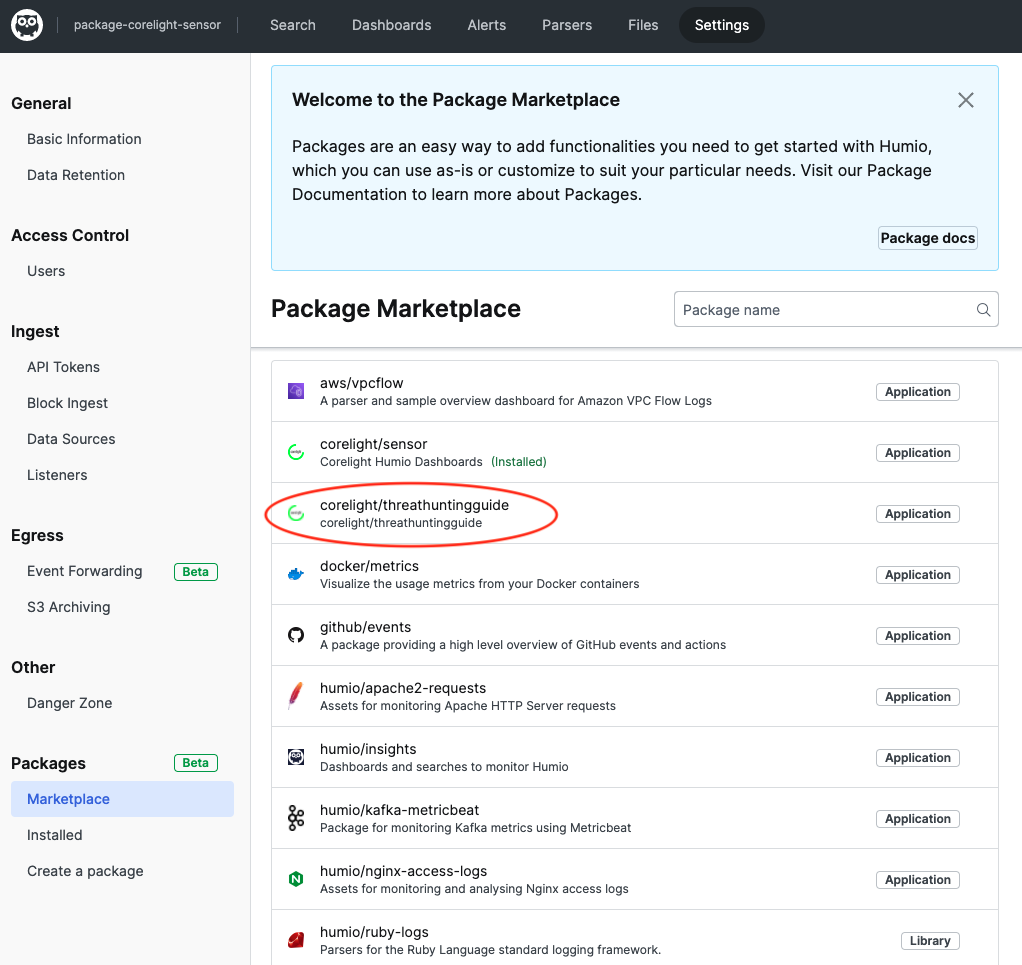
If you are using Humio’s SaaS Cloud service or are on V1.20 or later on a self-hosted Humio platform then you have access to the marketplace. Navigate to the repository where your Corelight logs are ingested and select ‘Settings’ then ‘Marketplace‘ and select the package named corelight/threathuntingguide. Click install and the package will install the required parser and all saved searches. If you have already installed a previous corelight package then the parser is the same as the one you already have (corelight-json).
The Humio corelight/threathuntingguide package uses logs from the following log files from Corelight (all suffixed with .log): conn, dce_rpc, dnp3, dns, files, http, kerberos, modes, notice, rdp, smb_files, smb_mapping, smtp, ssh, ssl, weird. Please make sure all these log types are sent to Humio as otherwise some of the searches/alerts may not work.
Get Hunting
With the guide downloaded it is easy to read a section which covers a particular ATT&CK tactic or specific technique and then locate the relevant searches and run them from the Humio package.
For example, on page 16 of the guide it introduces the concept of Forced Authentication. This is a specific ATT&CK technique ‘T1187 – Forced Authentication’ to use its full name!
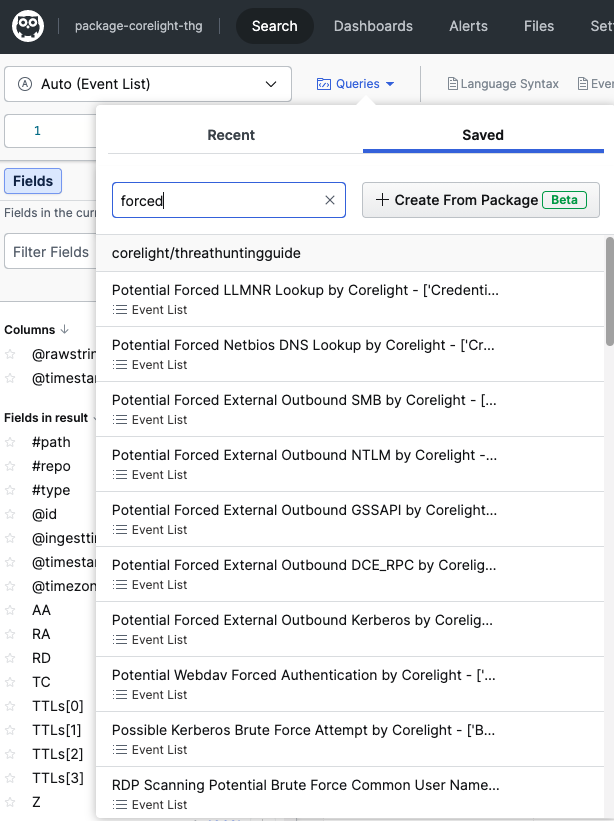
To find relevant searches in Humio select Search – Queries and Saved Searches and enter ‘Forced’ in the search box – you will see 9 different saved searches that find forced authentication attempts in different authentication protocols. Click the saved search and it will run a live search back over the last hour of data. To search a different time frame simply click the ‘Last 1 hr (live)’ and select the required timeframe.
Find Out More
We hope you have fun getting started with Threat Hunting amongst your Corelight data and expand the same methodology across your other logs sources in Humio to get even more great outcomes for security and operational performance.
For more information on Corelight, the Open Source community, and their Open NDR product offering, view an on-demand webinar with Humio CEO, Geeta Schmidt interviewing Gregory Bell, Chief Strategy Officer and Co-Founder at Corelight.
Listen to a recent podcast introducing Corelight@Home for anyone looking to bring Corelight’s enterprise-class network detection and response to their home network.