In this blog, we describe a recent incident that highlights the CrowdStrike Falcon® Complete™ managed detection and response team’s ability to act as an extension of our customer’s security team to quickly detect, triage and contain an active attacker before they were able to complete their goal. In this example, we outline an RCE (remote code execution) vulnerability being exploited in the wild as it impacted multiple customers at the same time. The Falcon Complete team provided a quick and effective response by triaging and successfully determining the source of this activity. Once the incident was contained, the Falcon Complete team further investigated the affected hosts and provided relevant customers with pivotal information to patch impacted systems to prevent any further exploitation attempts.
Detection and Triage
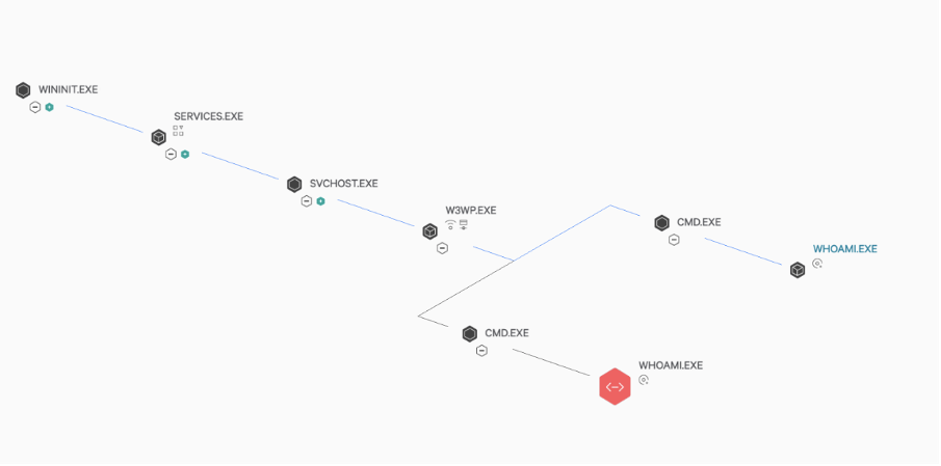
A detection involving a web server was identified by the CrowdStrike Falcon® sensor. This was associated with activity which is often indicative of anomalous behaviour on this type of host.
The Falcon user-interface provides a graphical view of the detection, and upon review of the process tree, the Falcon Complete analyst noticed the Internet Information Services (IIS) Worker process “W3WP.EXE” spawned a child process “CMD.EXE” which ran the command “WHOAMI.EXE.” Experience in the Falcon Complete team tells us that this is indicative of exploitation by either a threat actor or a penetration tester; The command itself is not malicious in nature but has to be observed in context — by itself it might appear expected and valid, however when looked at from a perspective of other actions taken on the host it can be indicative of an active attacker.
Shortly after the first detection, a similar activity was observed on other customers’ machines and the analysis and investigation efforts of multiple Falcon Complete analysts focused on correlation and confirmation of where the activity originated. As this behavior was confirmed to be consistent among all of the observed customers, a common denominator had to be determined.
The CrowdStrike Falcon® sensor alerted the team to this suspicious activity on the first host early in the morning; this was followed by a number of further detections on different machines and new customers’ hosts. This broad visibility allowed the Falcon Complete team to collaborate and analyse these detections in parallel enabling timely investigation and response to numerous separate alerts in various environments.
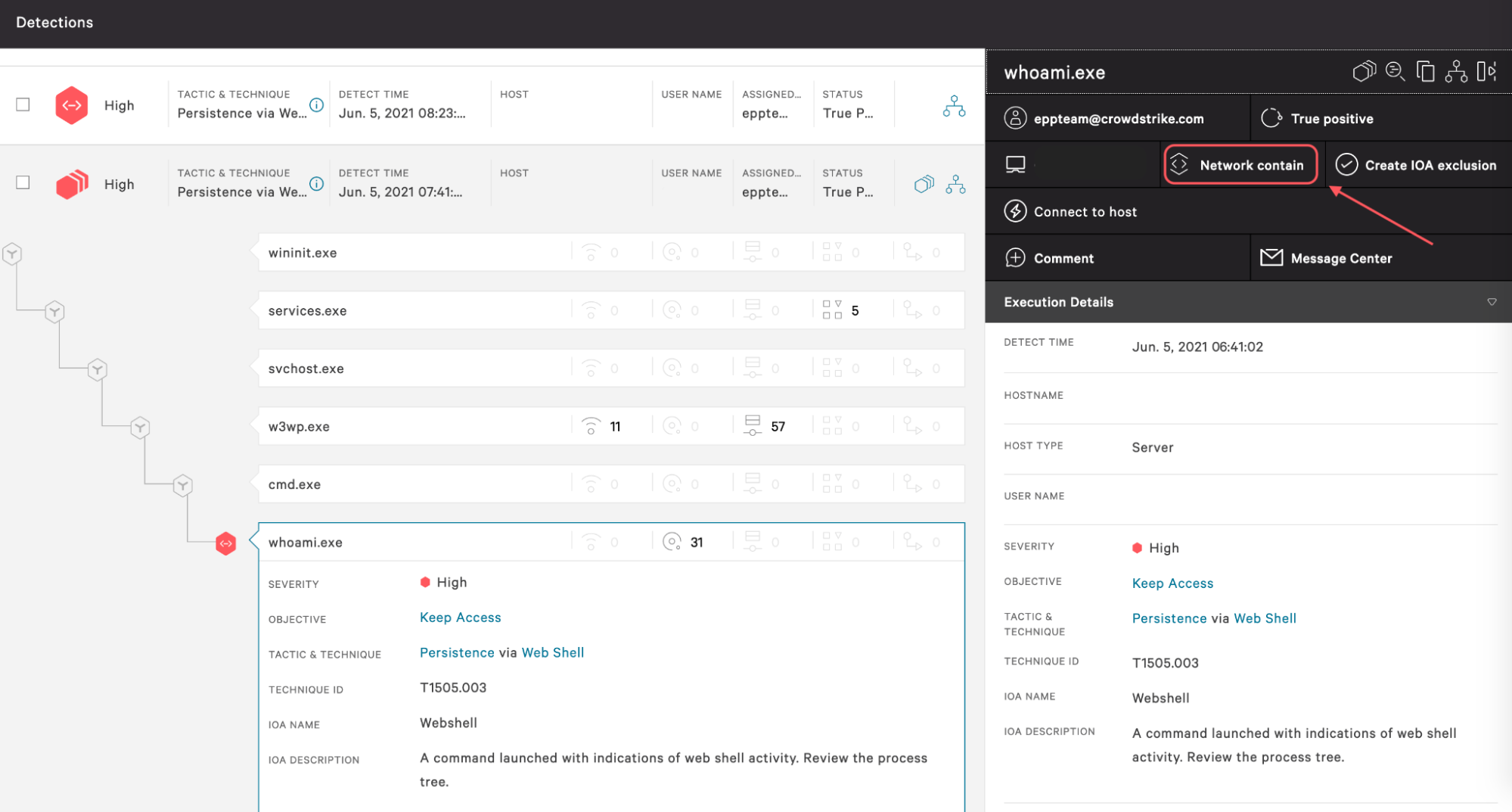
The affected customers were immediately contacted and informed about the observed suspicious activity and to confirm that they were not conducting testing on the specific web servers. The Falcon Complete analysts then used the “Network contain” feature of the Falcon sensor, which breaks off all connectivity to and from the affected machines except to predefined and configurable allowed IP addresses. This allows Falcon Complete to conduct further investigation without the risk of a potential threat actor reaching the host or spreading laterally. Each affected customer was contacted as soon as this activity was detected in their environment.
Detections Timeline
Jun. 5, 2021 06:41:02 - Customer A: Host A1
Jun. 5, 2021 06:41:20 – Customer B: Host B1
Jun. 5, 2021 06:55:24 - Customer B: Host B2
Jun. 5, 2021 07:06:06 - Customer C: Host C1
Jun. 5, 2021 07:21:11 - Customer B: Host B3
Jun. 5, 2021 07:23:18 - Customer A: Host A2
Jun. 5, 2021 07:46:39 - Customer A: Host A3
Jun. 5, 2021 07:55:09 - Customer B: Host B3
Jun. 5, 2021 08:32:18 - Customer A: Host A4
Jun. 5, 2021 08:32:48 - Customer D: Host D1
Jun. 5, 2021 08:50:45 - Customer E: Host E1
As similar processes were noted on other hosts in multiple environments, it was characteristic of a suspicious activity, most likely targeting a vulnerable application running on the affected web servers which is where further investigation was focused. This is generally due to outdated software where patches have not been applied in a timely manner as the risk of using vulnerable tools allows easier identification and exploitation of weaknesses by adversaries.
With the web servers contained, efforts focused on finding the root cause of this command being run. The “WHOAMI.EXE” command is one of many commands commonly used by threat actors to confirm successful exploitation of a webserver and is usually followed up with a payload and/or hands-on-keyboard activity by the threat actor. In this case, because Falcon Complete performed network containment on the target web servers in the crucial minutes before further exploitation commands were run, further damage was prevented.
Investigation and Next Steps
As all of the detections and observed malicious activity were related to the parent “W3WP.EXE” process, analysts focused their efforts on the “W3WP.EXE” process to try and find commonalities between the detections. By clicking on the “W3WP.EXE” process in the detection, and expanding the “Command Line” details, the analysts were able to quickly find the location on disk of IIS configuration file used by the “W3WP.EXE” process:
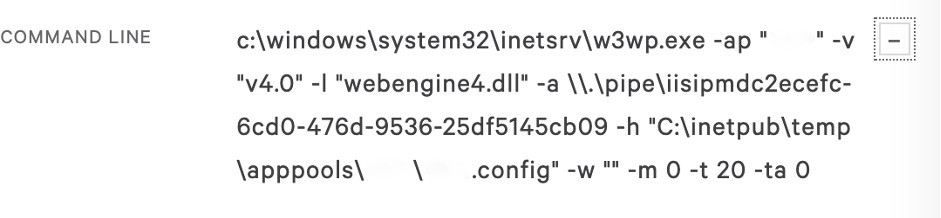 Figure 3. W3WP.EXE Command line
Figure 3. W3WP.EXE Command lineThe analysts then used the Falcon sensor’s Real Time Response (RTR) function to connect remotely to the web server to retrieve and review its configuration file, without the need to interrupt any customer operations.
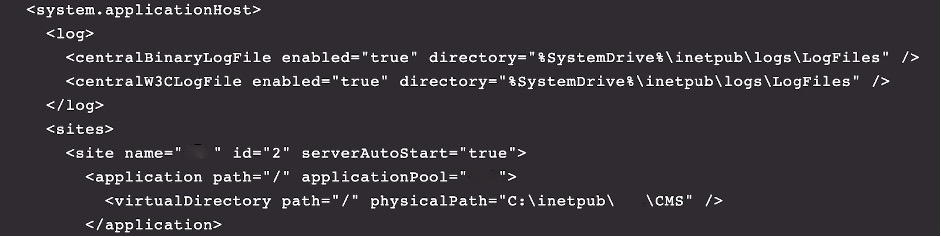 Figure 4. Configuration file including log file locations
Figure 4. Configuration file including log file locationsThe config file revealed the physical path for the target web server. Armed with this information, the web server logs were analyzed, focusing on activities that occurred around the same time of the detection. Analysts noticed similar events in the log files on all servers around the time of the detection, which included two connections to the web server, one connection to the web server with HTTP status code 500, followed shortly after by a connection with HTTP status code 200. This proves that the original request encountered an error to then succeed shortly after. The time of the web requests seen closely correlates with the suspicious activity being detected by the Falcon sensor signifying that this exploit was indeed accepted by the server.
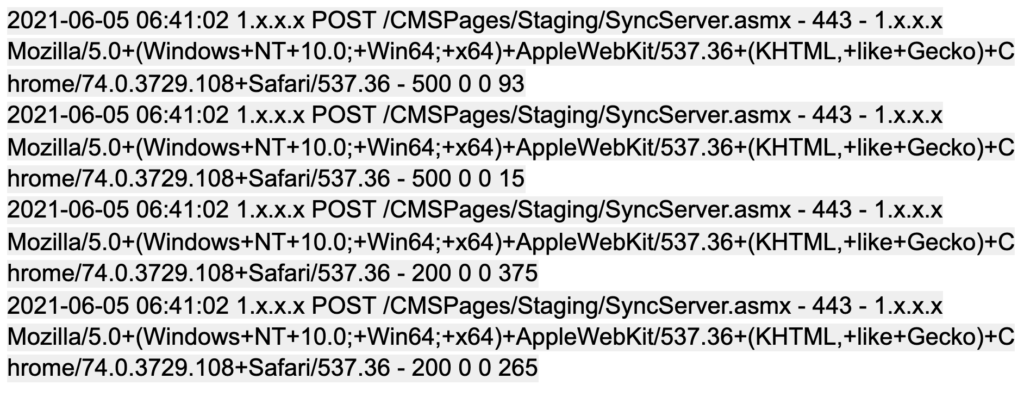 Figure 5. Web logs as seen on the affected server
Figure 5. Web logs as seen on the affected serverAdditional investigation focused on review of the relevant configuration files and verifying software present on the hosts, after which Falcon Complete analysts were able to conclude that the detected activity was targeting a CMS service present on all of the affected machines. A locally stored .dll file contained a description of the application and its version number, allowing analysts to determine that this reconnaissance activity involved Kentico web content management systems, with Kentico versions ranging from version 10 up to version 12 in the affected customers’ environments.
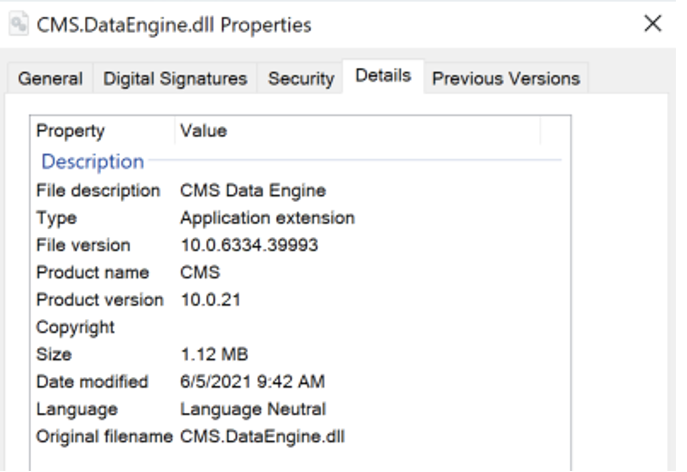 Figure 6. CMS.DataEngine.dll file properties
Figure 6. CMS.DataEngine.dll file propertiesUsing Open Source Intelligence research, the Falcon Complete team correlated the attack method with an existing vulnerability affecting the Staging Service component (“/CMSPages/Staging/SyncServer.asmx”) of Kentico CMS version 12.0.14 or earlier. This is known as CVE-2019-10068 and based on this investigation it can be concluded it is being exploited in the wild.
Conclusion
As a result of the investigation by the Falcon Complete team, customers were advised to update their Kentico CMS management systems to mitigate this vulnerability. In a typical intrusion case, all of the identified malicious binaries and persistence mechanisms are removed by the Falcon Complete analysts during surgical remediation. In the described case, there were no artifacts found as the threat actors did not manage to place anything on the targeted hosts thanks to timely containment of the machines by the Falcon Complete team during the early reconnaissance phase of the attack.
By identifying the reconnaissance and containing related web servers, Falcon Complete helped protect the vulnerable hosts and mitigate further risk associated with lateral movement, download and execution of additional tooling, data exfiltration, and others. This was possible without requiring any reboots or reimages and provided clients with valuable insight into their environment and how to best protect it.
Additional Resources
- Learn more by visiting the Falcon Complete product webpage.
- Read a white paper: CrowdStrike Falcon® Complete: Instant Cybersecurity Maturity for Organizations of All Sizes.
- Test CrowdStrike next-gen AV for yourself: Start your free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)