CrowdStrike Provides Free Dashboard to Identify Vulnerable Macs
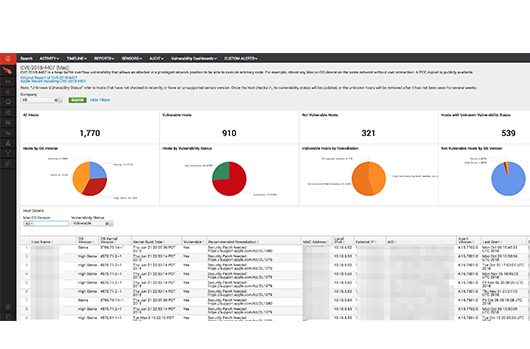
Image above is a screenshot of the CrowdStrike CVE-2018-4407 dashboard for macOS (click for larger image)
The recent discovery of the Remote Code Execution (RCE) vulnerability CVE-2018-4407 in Apple’s XNU operating system kernel may have been a cause for concern among organizations using Macs but CrowdStrike® is helping customers identify vulnerable Macs in their environments with a new dashboard.
The XNU OS is used in macOS as well as iOS, so this vulnerability impacts all types of Apple devices, including iPhones, iPads, MacBooks, etc. The vulnerability was first discovered in August, but disclosed publicly on October 30, 2018 when Apple released security updates for the affected operating systems. First reported by Kevin Backhouse, the vulnerability was fixed by Apple in their October security patches. CrowdStrike moved quickly to identify the potential risk associated with the successful exploitation of this vulnerability by providing its Mac user community with an easy way for them to gain instant visibility into vulnerable macOS hosts in their environments.
Why Customers Should Care About This Vulnerability
The risk of any vulnerability stems from the likelihood of a successful exploit and the potential impact resulting from that exploit. It is also critical for organizations to understand the size of their vulnerable population and the actions required to remediate the vulnerability. In doing so, they should consider the following facts regarding the CVE-2018-4407 vulnerability:
- Exploit: Proof of concept (POC) exploit code is publicly available, and currently demonstrates its ability to crash the kernel to reboot any device on the same local network as the attacker — including public WiFi networks.
- Impact: While the current POCs illustrate a kernel crash leading to a reboot, Apple does classify this vulnerability as a Remote Code Execution (RCE), which could allow an attacker to corrupt memory (heap buffer overflow) with a malicious IP packet and potentially execute arbitrary code.
- Scope: The vulnerability exists for all versions of macOS, with the exception of Mojave, which was patched prior to release. A detailed chart for each macOS version is included below, explaining the mitigation path for each version.
- Remedy: For newer macOS versions (Sierra and High Sierra), the October security patch has been made available to address the vulnerability. However, for older versions of macOS, there is no patch and an OS upgrade is required. Note that Mojave is not vulnerable.
The Steps Mac Users Should Take
Depending on the macOS version you are running, Mac users need to update to a new version or install the security update with a fix. The table below can help you determine which case is applicable based on the current version of macOS running on the host.
Table: How to Bring Vulnerable MacOS Versions to a Non-vulnerable Version*
| macOS version | Percentage of worldwide distribution* | Vulnerability status | OS
release date |
Path to remediate
CVE-2018-4407 |
| macOS Mojave | 11.44% | Not vulnerable | September 2018 | No action required against CVE-2018-4407 |
| macOS High Sierra | 45.44% | All versions through and including 10.13.6 | September 2017 | Apply patch: Security Update 2018-002 |
| macOS Sierra | 16.37% | All versions through and including 10.12.6 | September 2016 | Apply patch: Security Update 2018-005 |
| OS X El Capitan | 13.18% | Vulnerable | September 2015 | Upgrade to (at minimum) macOS Sierra with security patch 2018-005 |
| OS X 10.10 Yosemite | 7.85% | Vulnerable | October 2014 | Upgrade to (at minimum) macOS Sierra with security patch 2018-005 |
| OS X Mavericks | 2.57% | Vulnerable | October 2013 | Upgrade to (at minimum) macOS Sierra with security patch 2018-005 |
How CrowdStrike Protects Mac Users from This Vulnerability
CrowdStrike has worked to expand its assistance to customers in the face of this risk by creating a dashboard to identify vulnerable systems. The dashboard is provided free of charge to customers who have the CrowdStrike endpoint detection and response (EDR) solution, Falcon Insight™; CrowdStrike’s vulnerability assessment solution, Falcon Spotlight™; and those who have purchased a CrowdStrike Falcon® endpoint protection bundle. The new dashboard provides visibility into the vulnerability and patch status of the systems running macOS in their environments. A screenshot of the dashboard is included in this blog — click on the caption below the image above to see a larger version.
CrowdStrike customers can access this new dashboard by navigating to Investigate > Event Search > Vulnerability Dashboards > CVE-2018-4407 (Mac)
Please Note: The dashboard will be deployed to all customers by Monday, November 12, 2018.
Additional Resources:
Apple Security Update Content.
Kevin Backhouse Original Disclosure.
Learn more by visiting the CrowdStrike Falcon® platform web page.
*Sources:
http://gs.statcounter.com/macos-version-market-share/desktop/worldwide.
https://support.apple.com/en-us/HT201222.
https://lgtm.com/blog/apple_xnu_icmp_error_CVE-2018-4407,
https://en.wikipedia.org/wiki/MacOS_version_history.


