CrowdStrike Falcon® Insight XDR
The leader in endpoint security
Stop breaches with pioneering detection and response backed by world-class intelligence and native AI.
From missed attacks and slow response to unbeatable protection with immediate ROI
Third-party test
100%
protection, visibility, and analytic detection in the 2023 MITRE ATT&CK® Evaluations1
Customer assessment
95%
reduction in mean time to respond, speeding triage from 4 hours to <10 min2
Third-party test
100%
ransomware protection in 2023 SE Labs test3
State of Wyoming chooses CrowdStrike to secure their endpoints
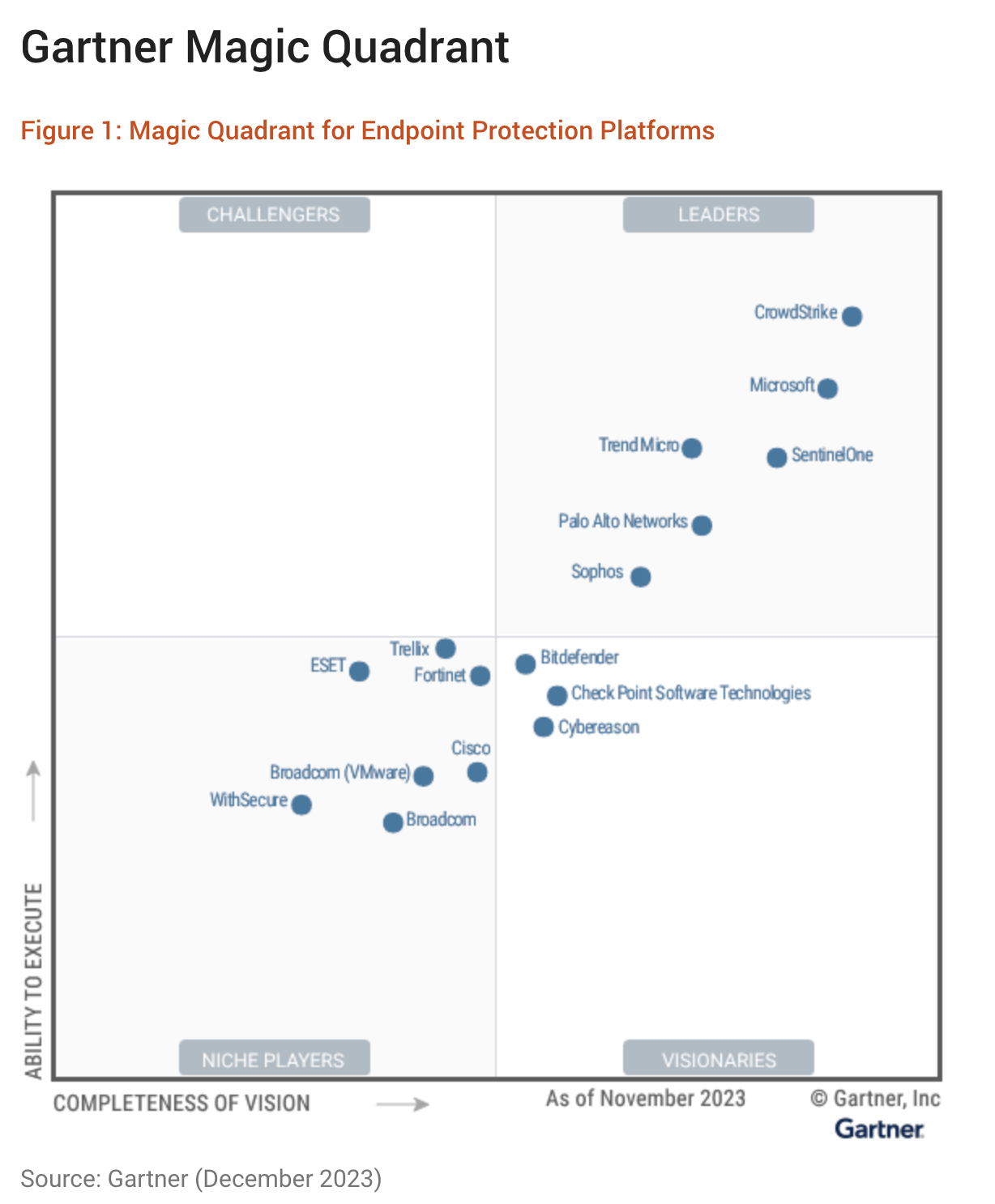
The unrivaled leader in endpoint detection and response
CrowdStrike pioneered EDR to consolidate dozens of point products on a single platform, single console, and single agent, shutting down the most advanced adversaries in record time.
Detect and defeat the adversary
Stop the adversary with AI-powered detection enriched with the world’s best threat intel and expert insight. Our unique adversary-driven approach uncovers the most elusive threats with tactical precision, setting the industry standard for the most trusted detections with the fewest false positives.
Activate instant protection and maximum SOC efficiency from day one. Our lightweight, unified agent deploys and secures in minutes — no reboots, manual updates, or complex tuning required.
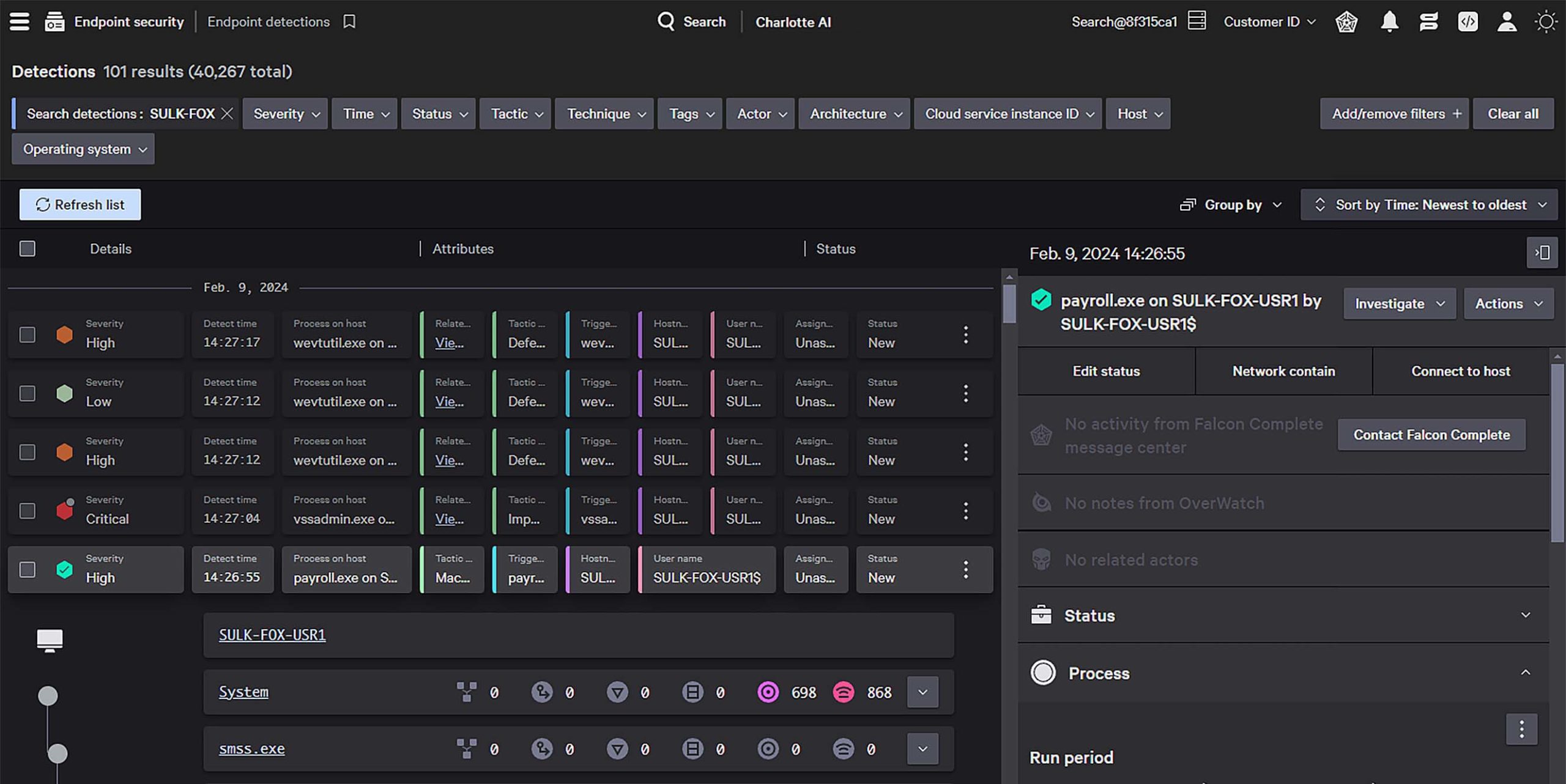
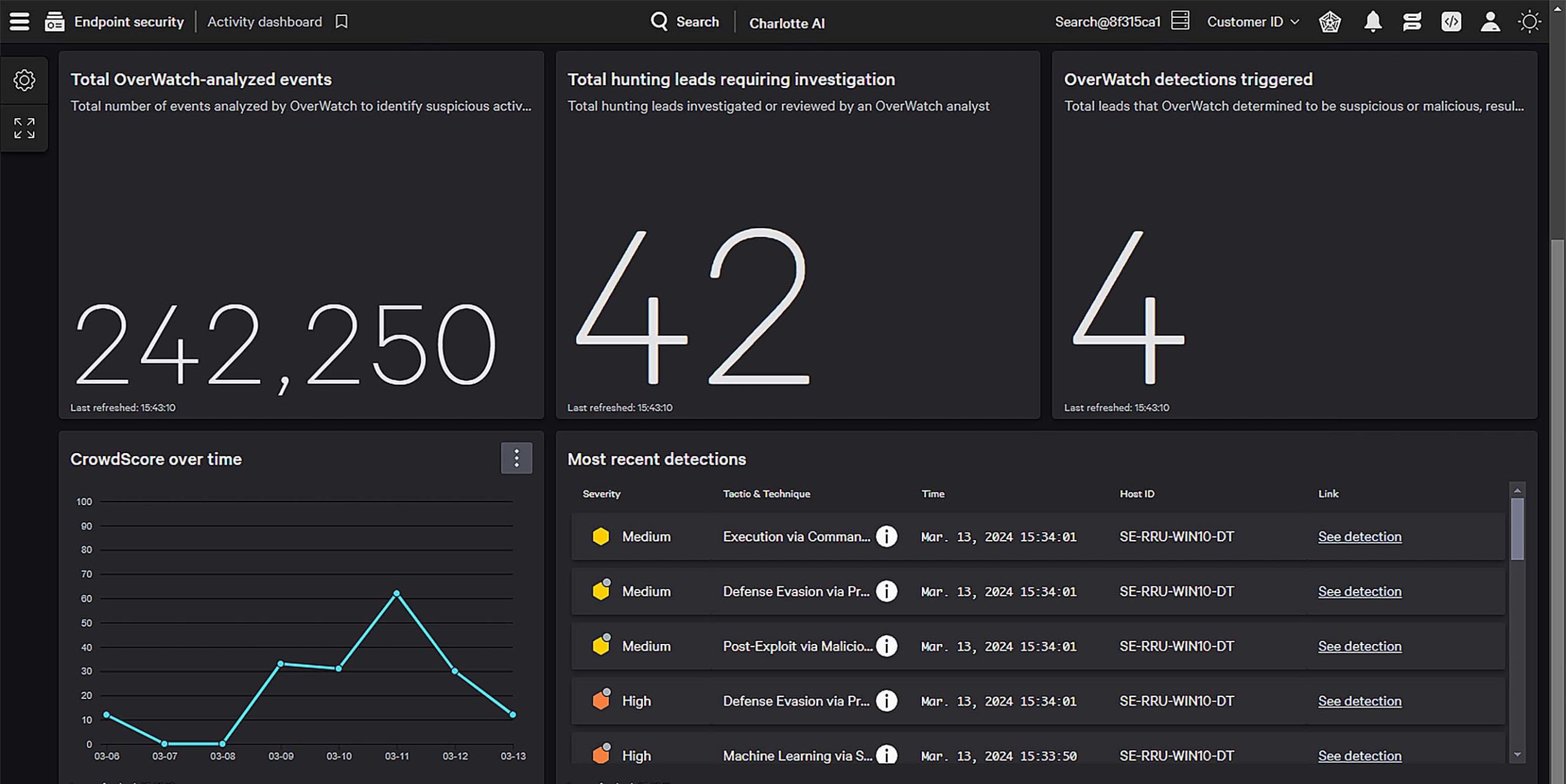
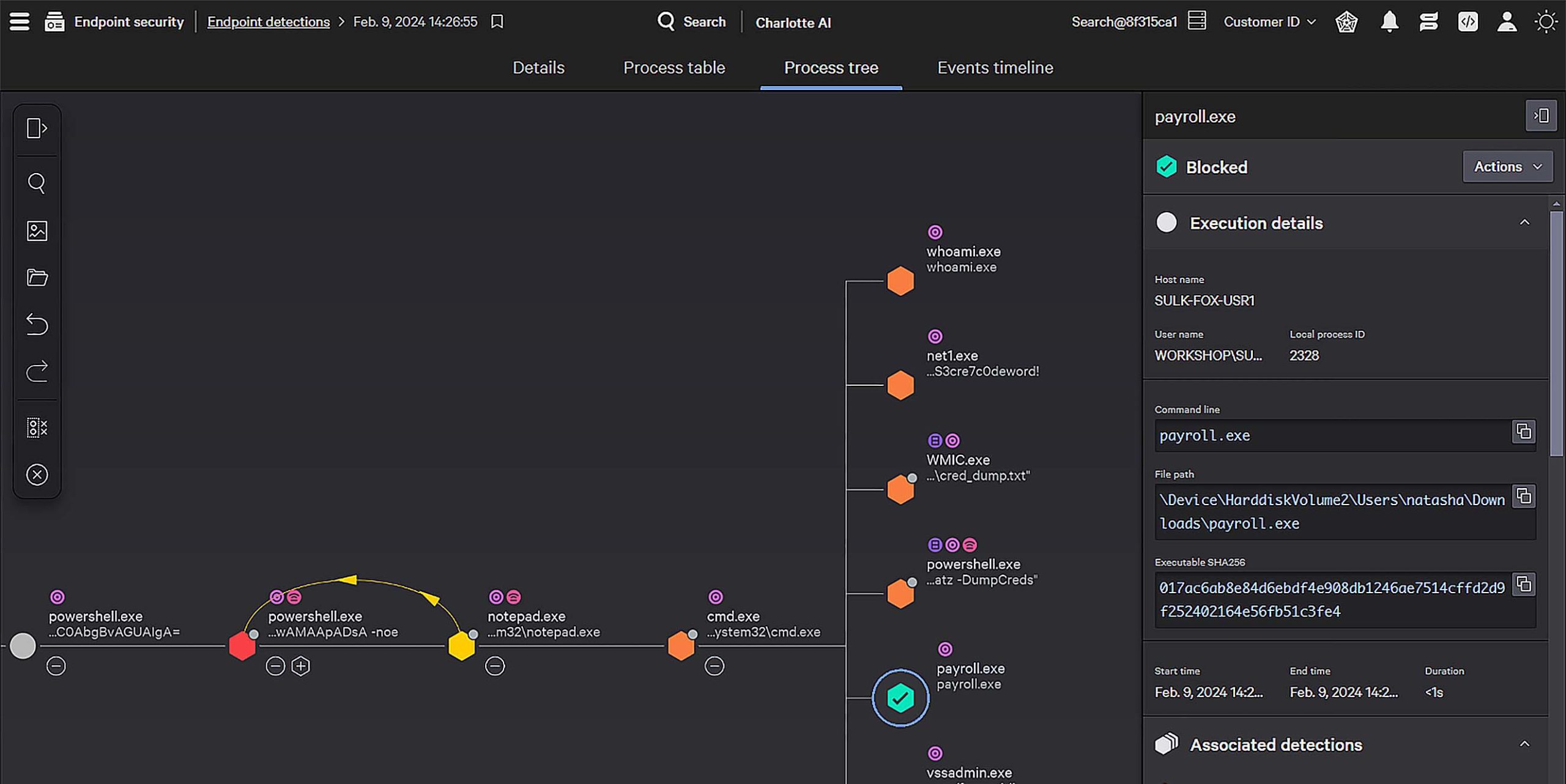
Accelerate investigations with AI
Harness the power of Charlotte AI and AI-powered risk scoring to intelligently prioritize threats and turn hours of work into minutes or seconds. Radically transform security operations and empower all of your analysts to stop breaches like the most seasoned experts.
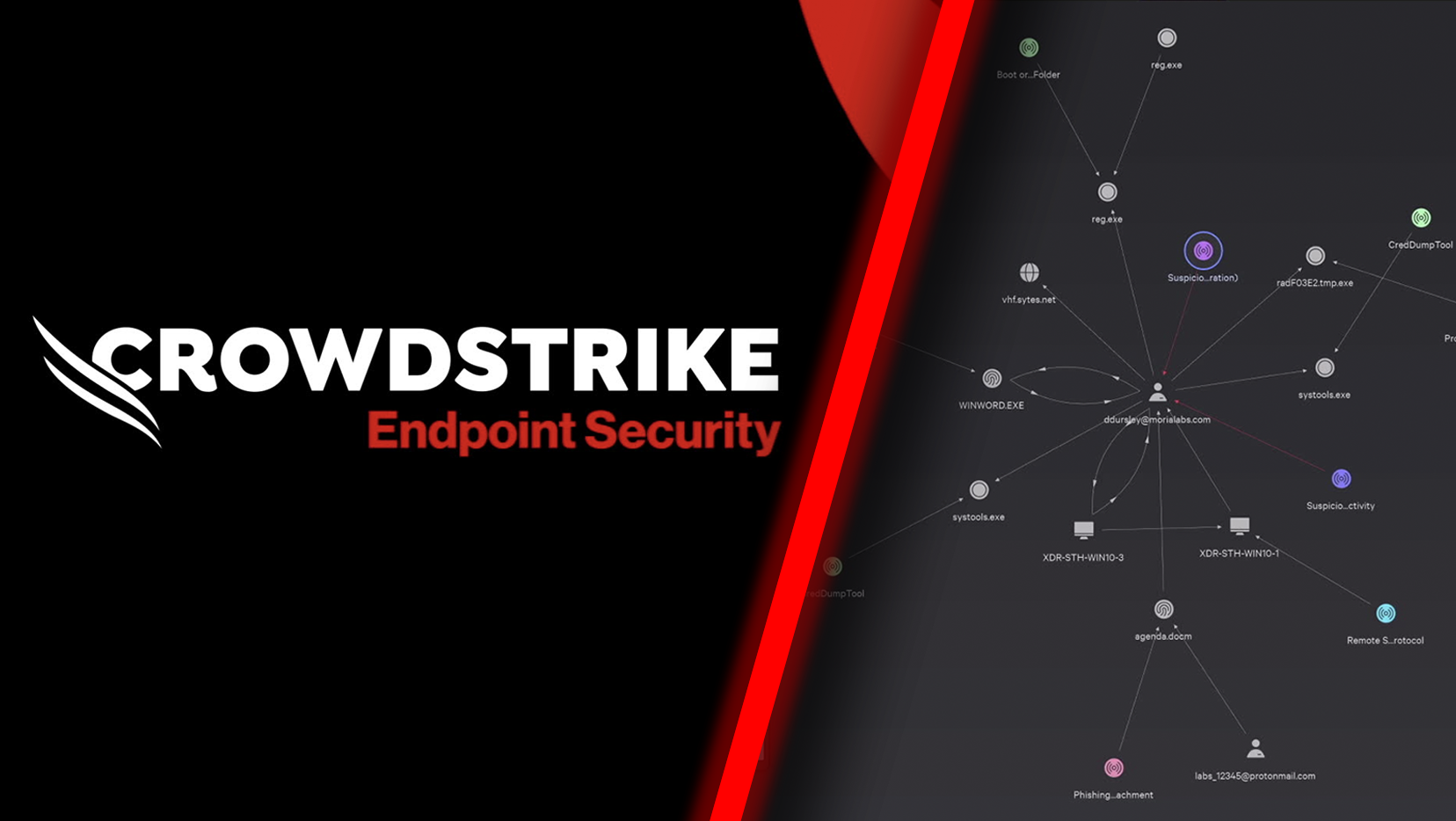
Unparalleled attack path visibility, adversary context, and MITRE ATT&CK mappings empower analysts to quickly understand threats and take decisive action. Triage, investigate, and remediate faster with real-time global collaboration from a unified source of truth.
Extend the world’s best EDR with context from identity, cloud, mobile and data flows for unified, lightning fast investigations. CrowdStrike EDR customers get native XDR at no additional cost and can extend visibility across third party data with Falcon Next-Gen SIEM, available in the same console.
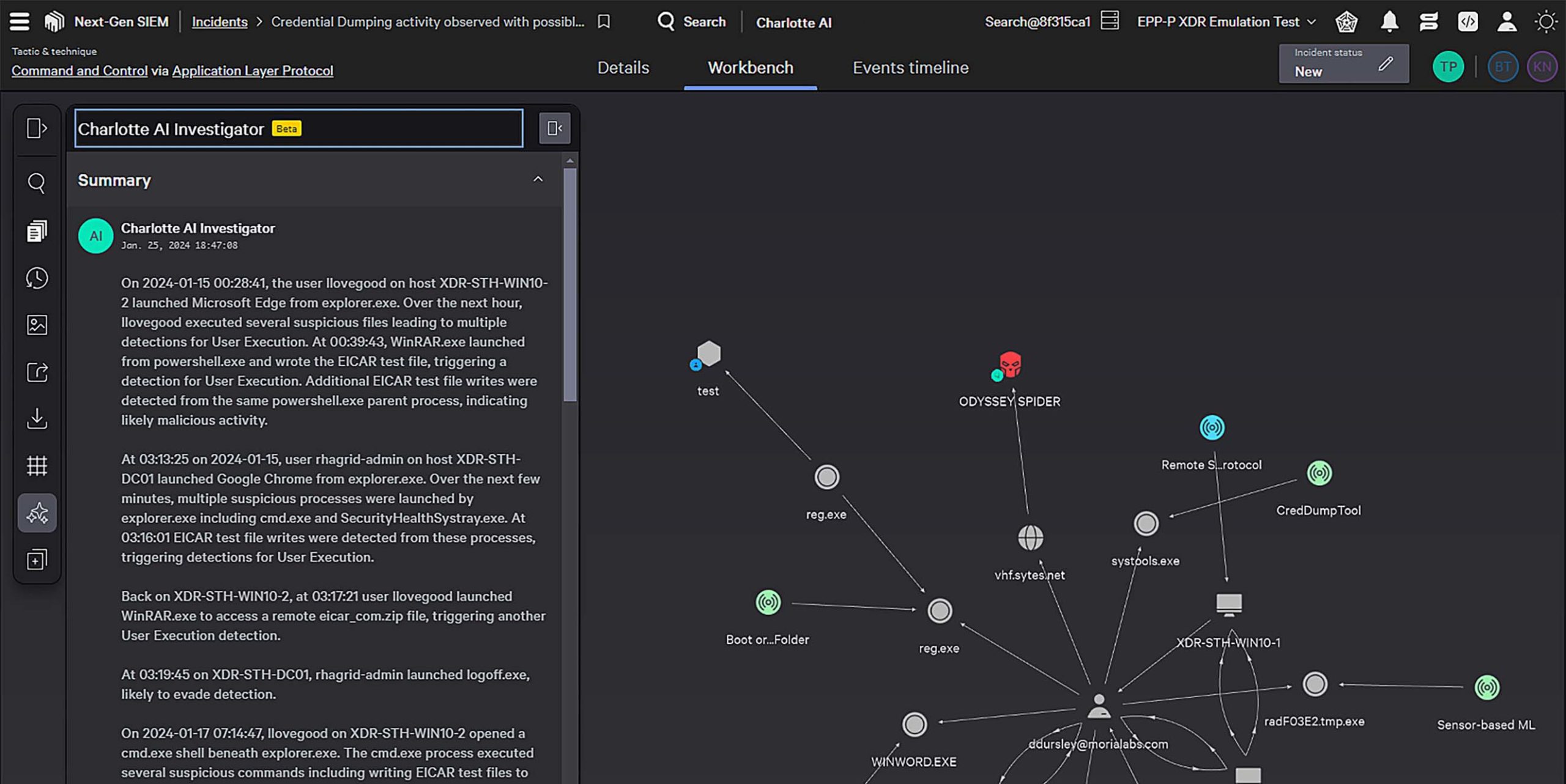
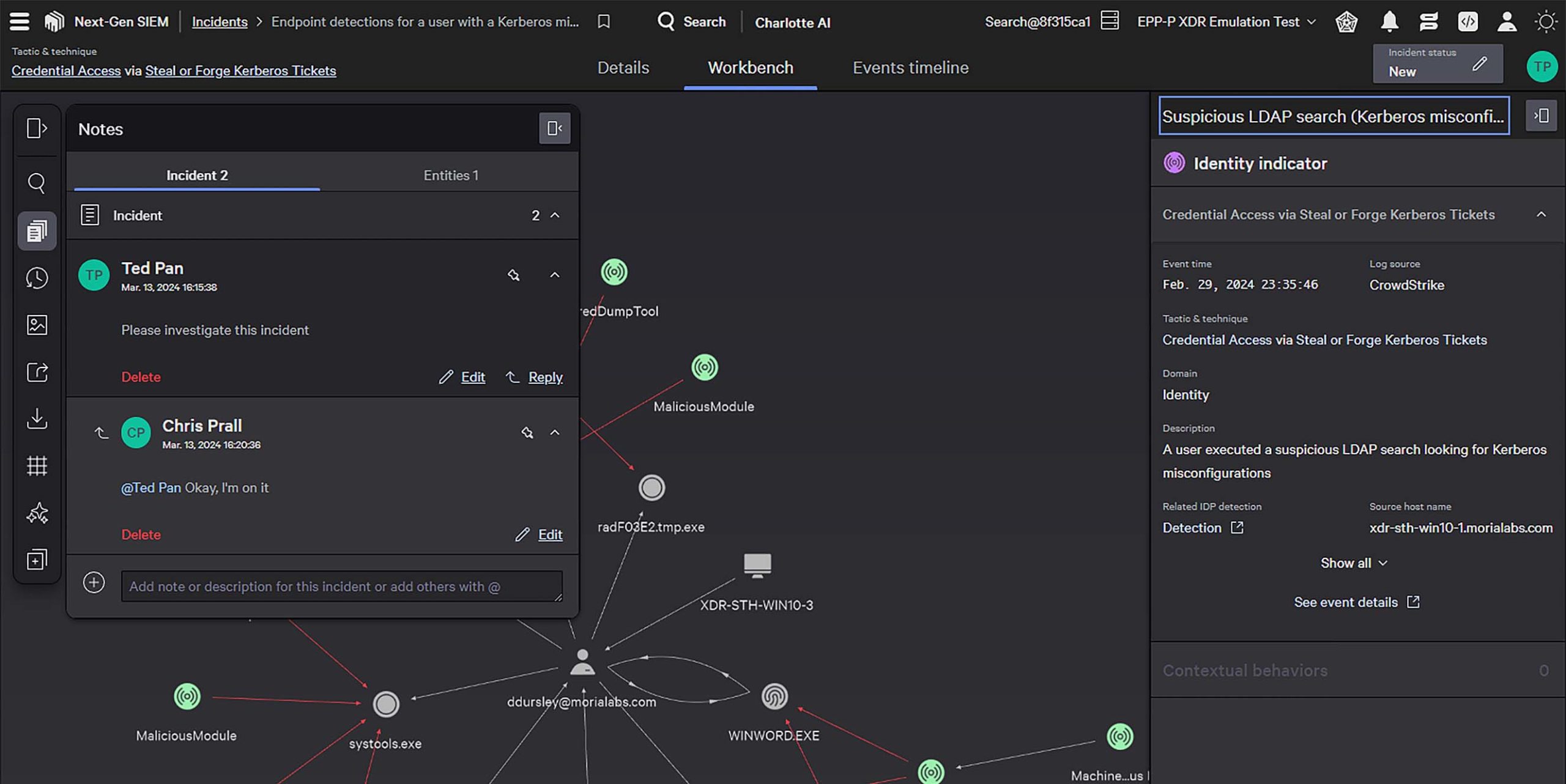
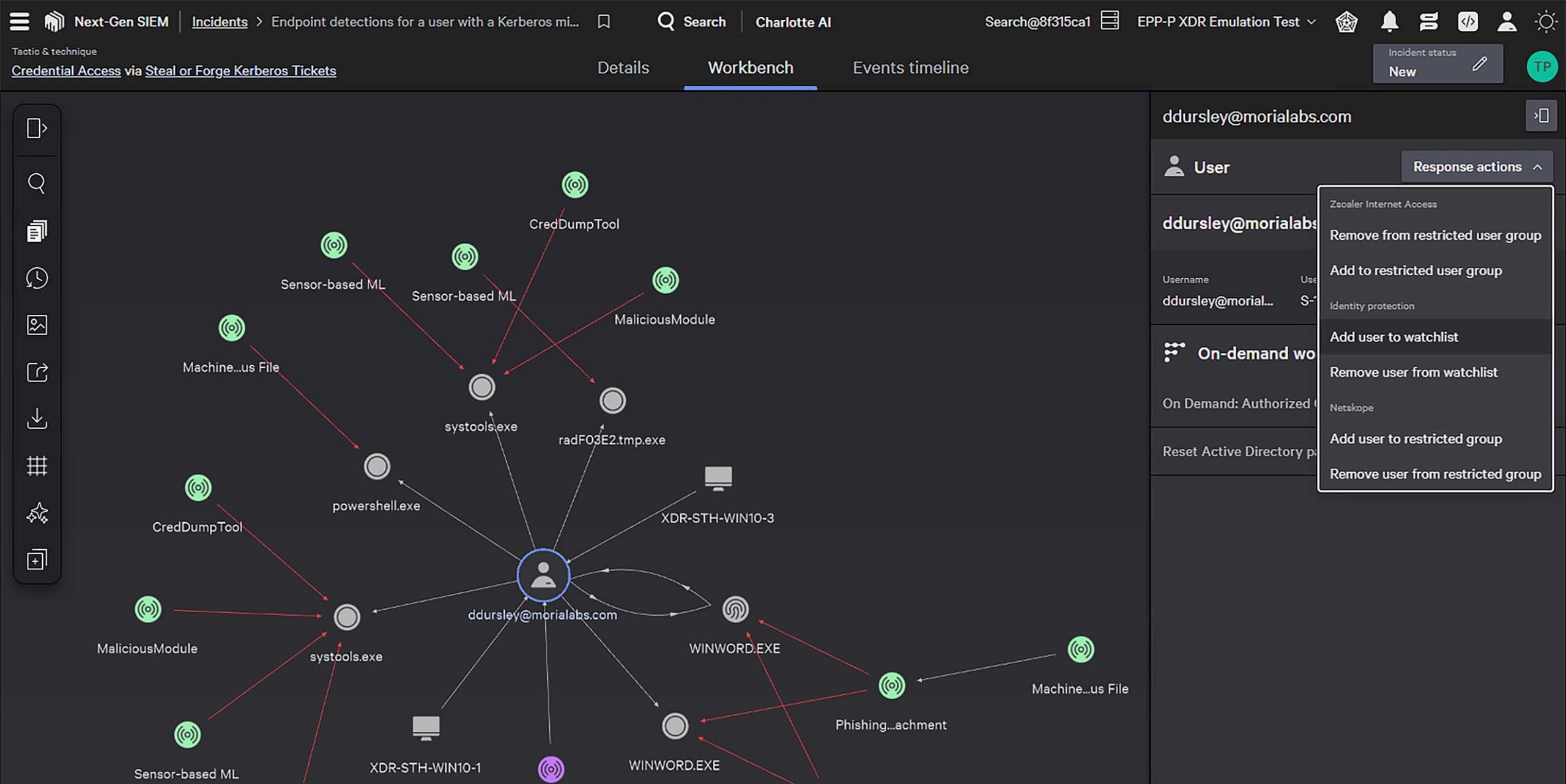
Automate rapid response
Elevate threat response with the world’s best threat intelligence on 230+ adversaries and their tradecraft at your fingertips. Automatic sandboxing and detailed adversary profiles provide unmatched insights for swift, and decisive remediation from indicators to root cause.
Eradicate even the most sophisticated threats with Real Time Response (RTR) for direct system access to contain threats. Kill processes and run commands, executables, and scripts to shut down threats from anywhere in the world.
Streamline and automate complex tasks at scale with native Falcon Fusion security orchestration automation and response (SOAR) to dramatically improve SOC team efficiency and shut down attacks.
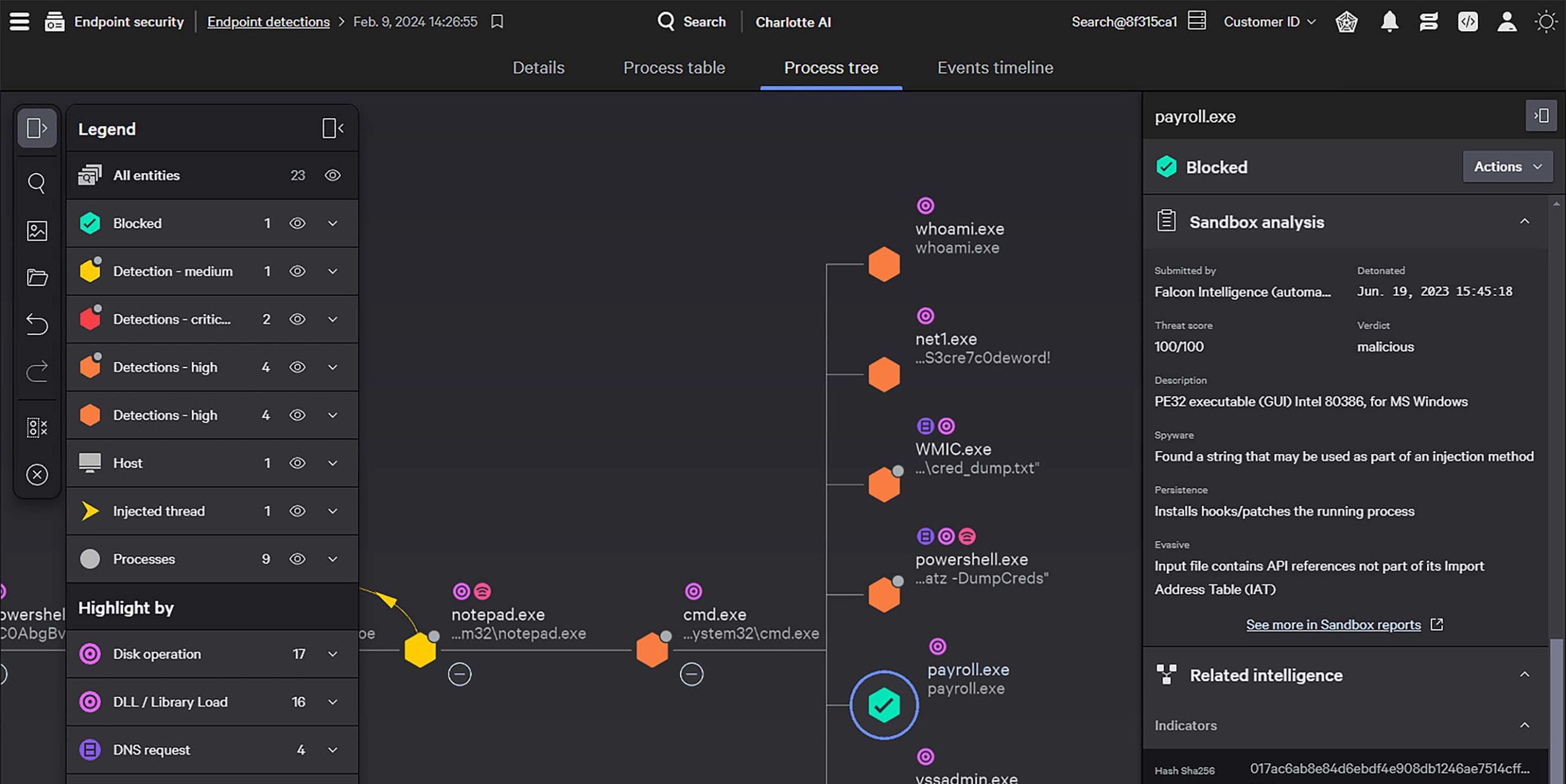
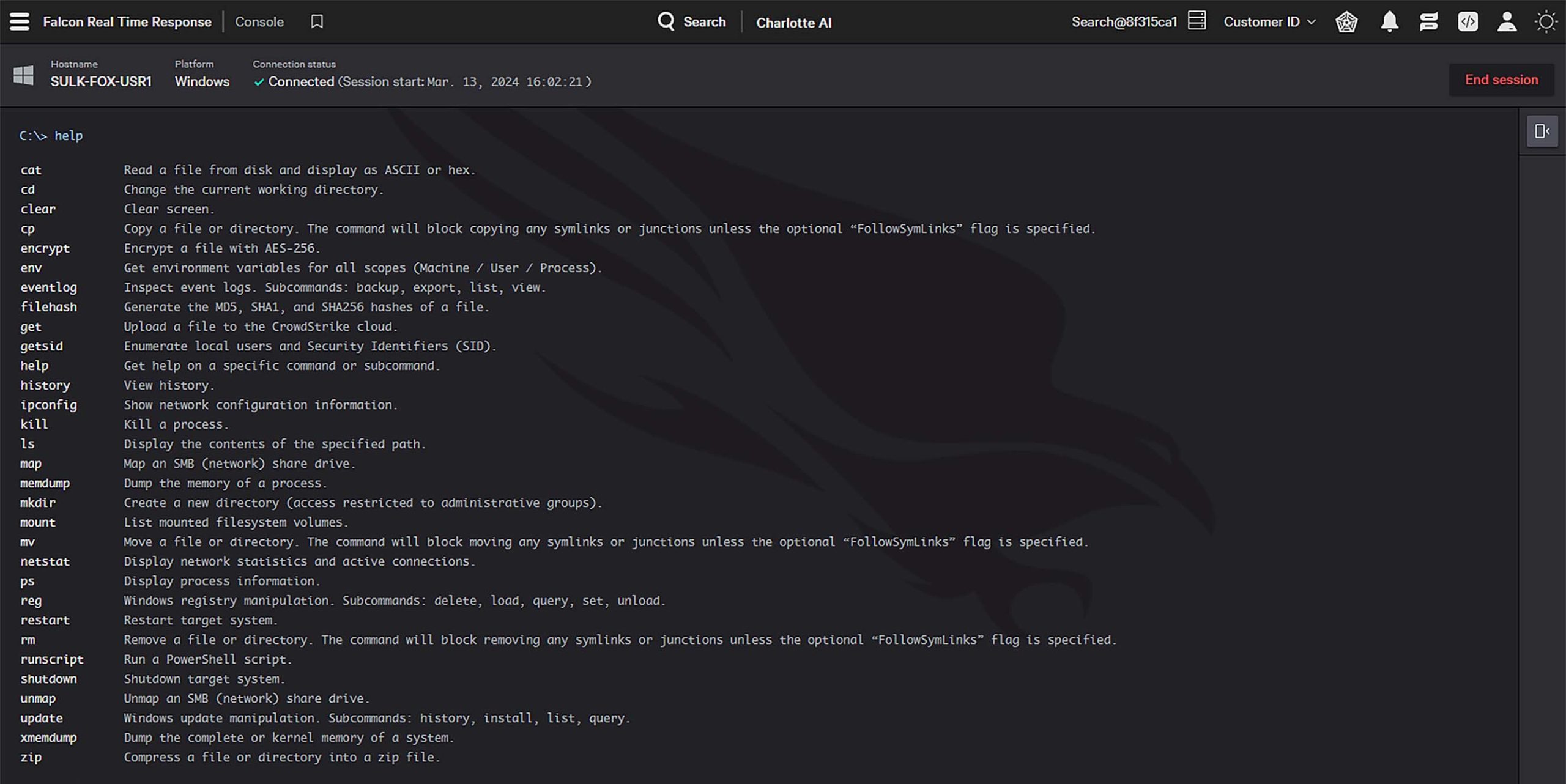
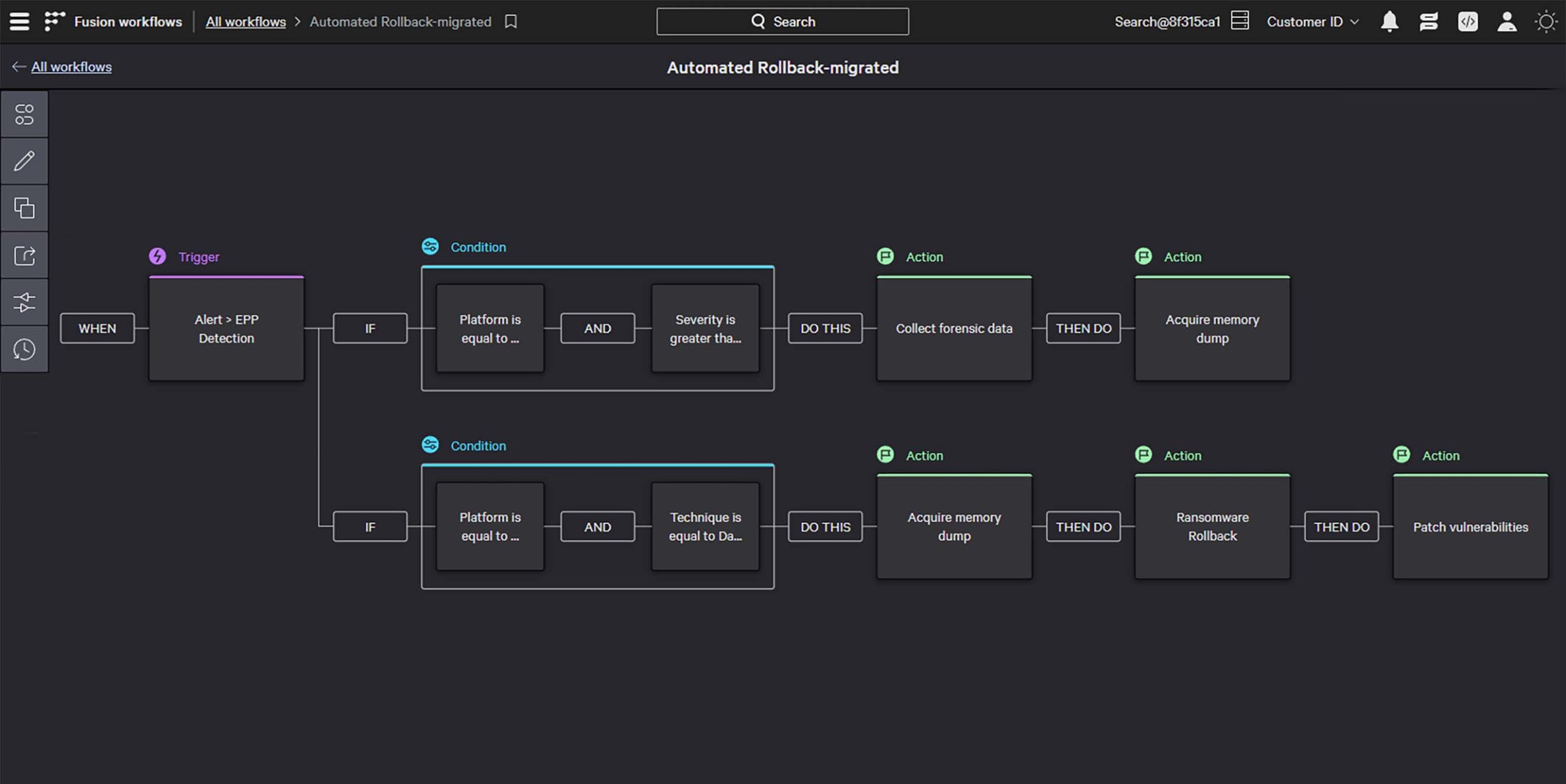
Stop the breach with industry-leading managed services
Our expertise is your expertise, with Falcon Insight XDR continuously strengthened by a world-class team that works night and day to stop adversaries.
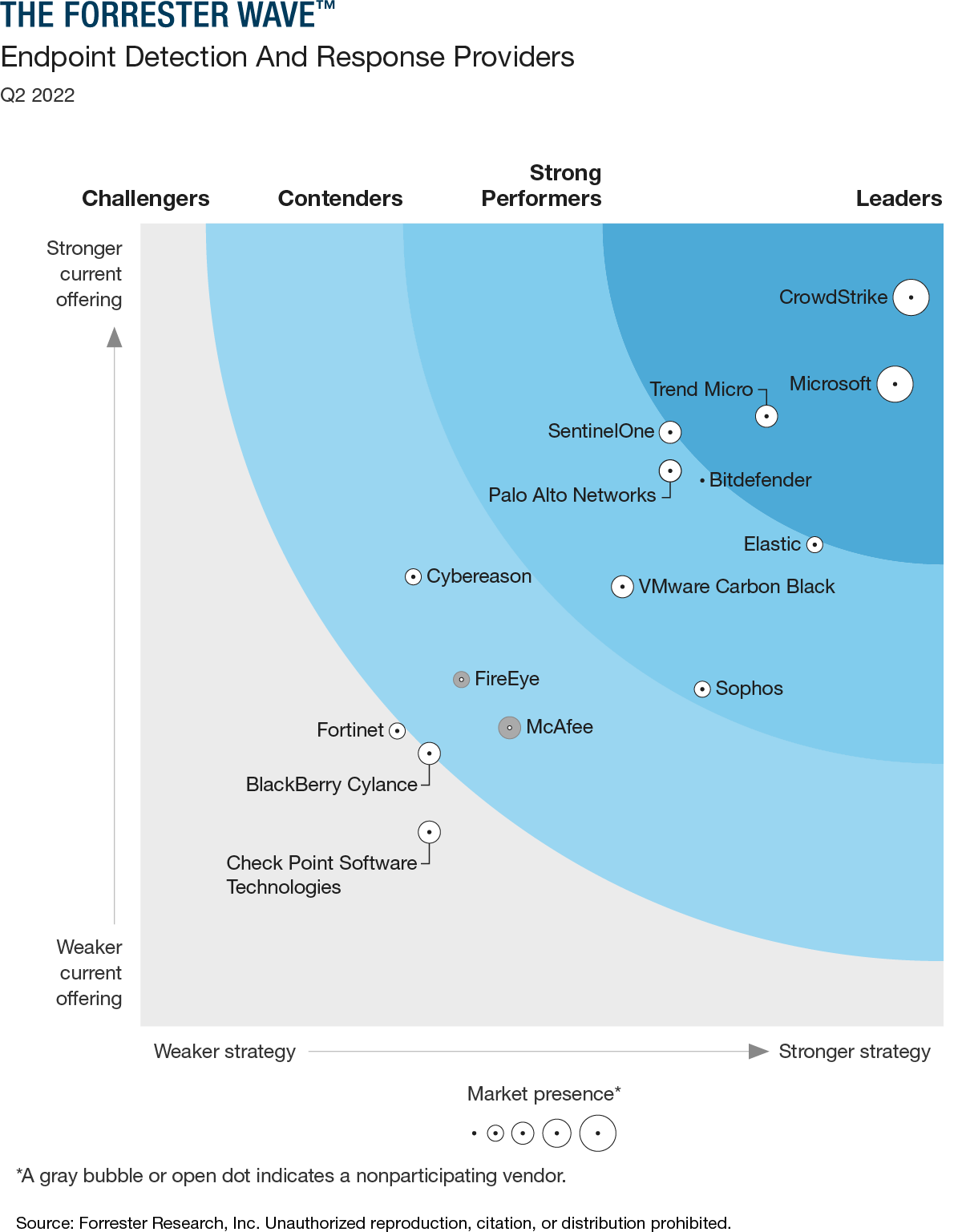
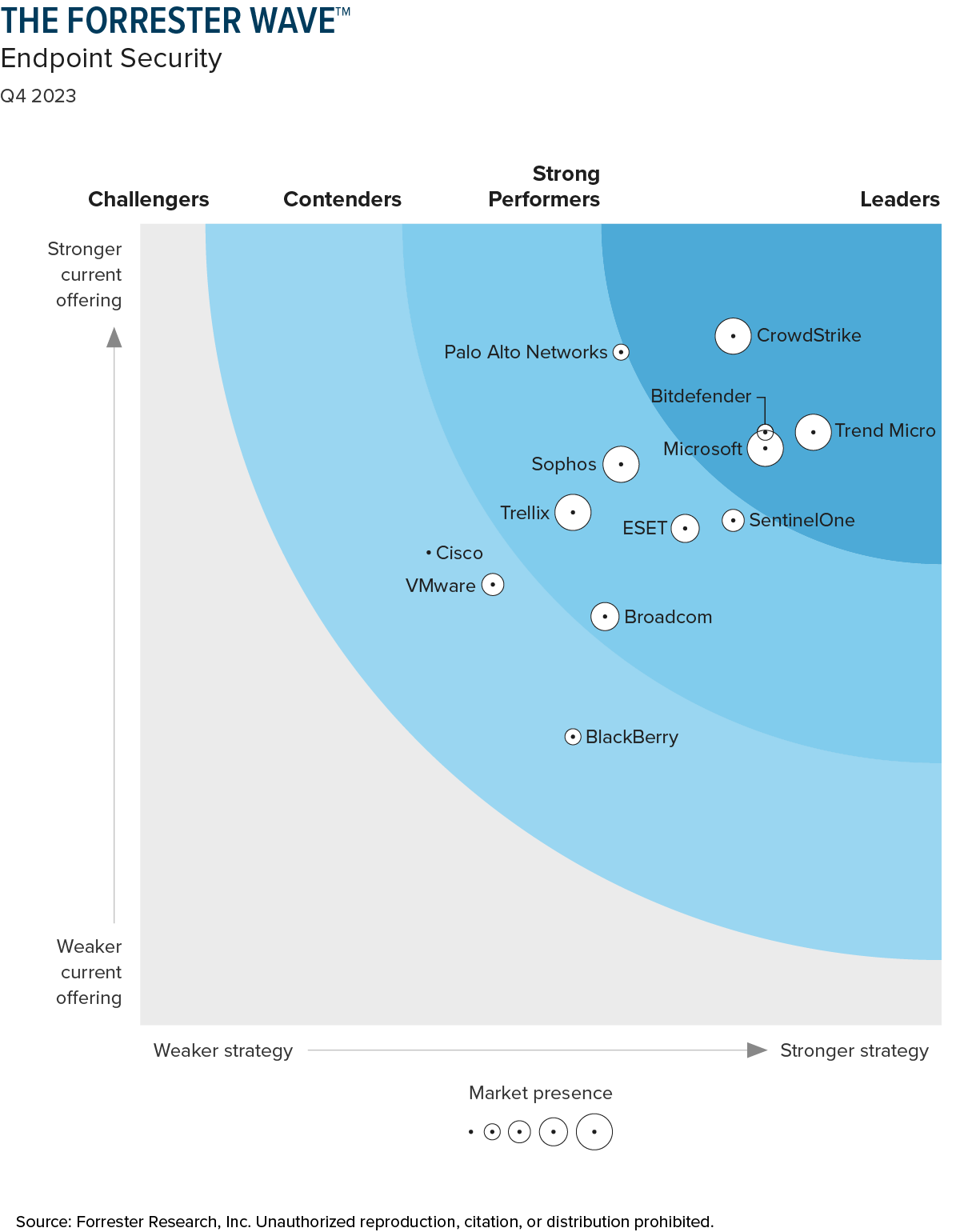
Market leader validated by every
third-party analyst
Customers love CrowdStrike:
EPP Customers’ Choice 2023
See the power of Falcon Insight XDR in three minutes
Related products
Try CrowdStrike free for 15 days
Total protection has never been easier. Enjoy a free trial of the CrowdStrike Falcon platform in just a few simple clicks. Once initiated, head over to the CrowdStrike Store within the console to enable your trial of Falcon Insight XDR.
Start a free trialFeatured resources
1 MITRE Engenuity ATT&CK® Evaluations: Enterprise – Round 5
2 These numbers are projected estimates of average benefits based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.
3 SE Labs Test