DLL Side-Loading: How to Combat Threat Actor Evasion Techniques
Threat actors constantly evolve their tactics and techniques to circumvent security solutions. Working at the cutting-edge of detection engineering, CrowdStrike rapidly tracks and observes these evolutions in tactics to deliver timely, effective detections that protect customers. In this blog, we explore DLL side-loading and learn how CrowdStrike has expanded protections with Advanced Memory Scanning.
| Learn More About CrowdStrike’s Advanced Memory Scanning |
| Watch this webcast to see how the CrowdStrike Falcon platform’s Advanced Memory Scanning feature accelerates protection earlier in the kill chain. |
Enter the DLL Side-Loading Evasion Technique
DLL side-loading is the proxy execution of a malicious DLL via a benign executable planted in the same directory, similar to DLL search-order hijacking. This abuses the Windows behavior of loading the DLL from where the application (e.g. the benign, planted binary) was loaded prior to other locations such as system directories.1 DLL side-loading is a frequently seen technique that CrowdStrike has developed extensive protections against.
Advantages of DLL Side-Loading for Threat Actors
The advantages of DLL side-loading is the executables used are often trusted, signed and in use within an organization. As such they may face less scrutiny by security appliances or teams. In reality, the payload is embedded within the DLL and may often be encrypted or obfuscated to defeat anti-virus or basic scanning.
DLL side-loading is not a new technique and has been observed by the CrowdStrike® Falcon OverWatch™ and CrowdStrike Intelligence teams for years.2 It is one of the most prevalent techniques amongst attackers spanning targeted intrusions, eCrime (including big game hunting) and commodity RATs.
DLL side-loading is used not only in post-exploitation, but also for lateral movement and persistence where the files are copied to another endpoint and remotely executed, or placed in a startup location or registry path to maintain or expand access.
Understanding the DLL Side-loading Technique
The technique is mapped to MITRE under Hijack Execution Flow (T1574.002).
An example chain of malicious activity might appear similar to these steps:
- A threat actor obtains initial access to an endpoint, either via an application vulnerability, compromised credentials, successful phish, trojanized installer or even a trusted insider.
- Once an initial foothold has been gained, the threat actor needs to potentially upgrade their access to a more capable command and control (C2) such as Cobalt Strike or similar C2 frameworks.
- To do this, the threat actor copies both a benign, often signed executable and a malicious DLL to disk into the same directory.
- Upon launching the benign executable, the dropped DLL is loaded with its malicious payload. The application either fails to run any further, or the DLL proxies legitimate function calls to the real DLL to avoid any crash or suspicious behavior.
- Once the payload has been executed it will call back to the threat actor controlled remote C2.
- The process tree will show the execution of the binary rather than any malicious program.
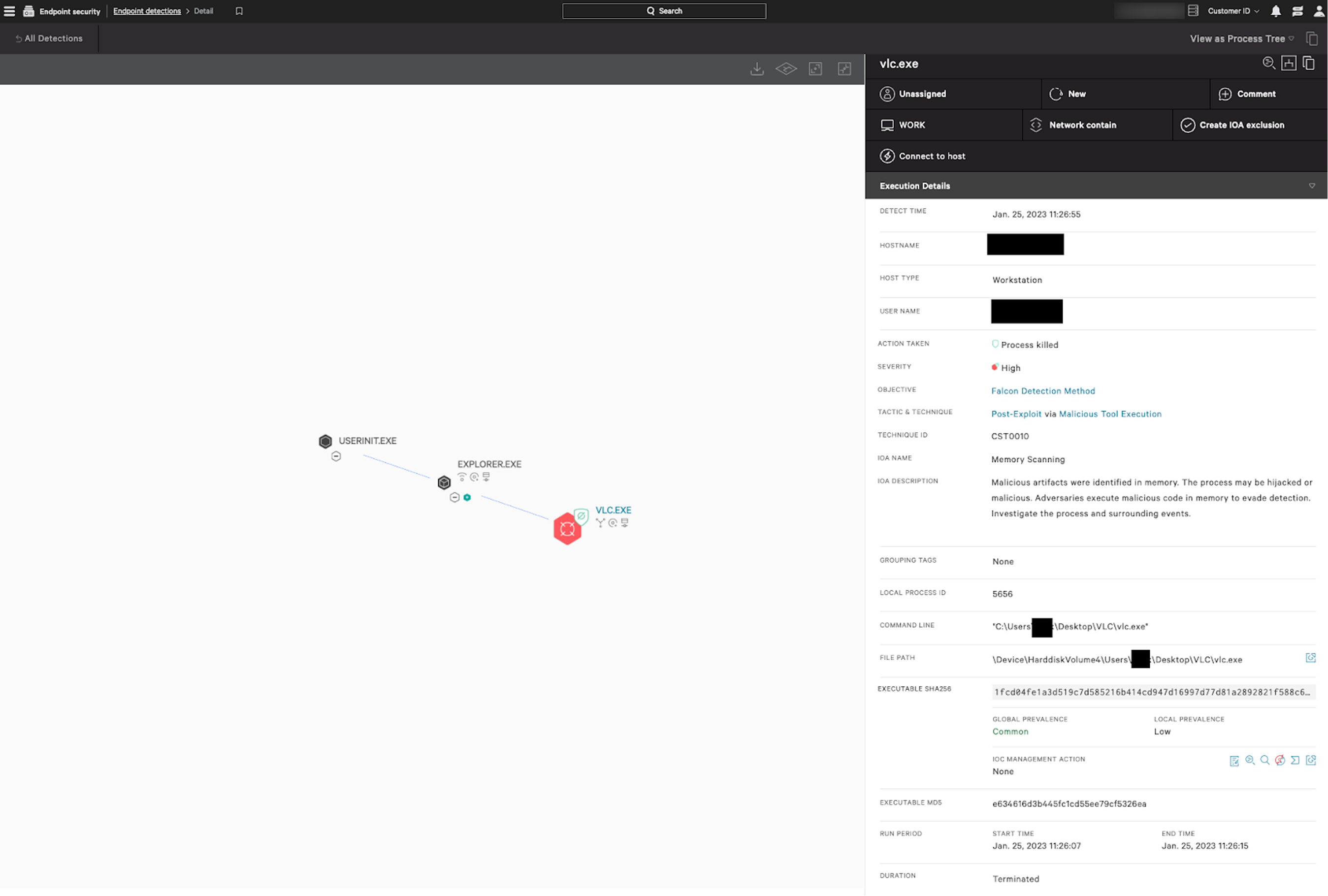
Definitely Not Just Vlc.exe
Since October 2022, CrowdStrike Intelligence has observed abuse of particular DLL side-loading to further various intrusions.3 In November and early December 2022, CrowdStrike identified a number of ransomware intrusions targeting the health sector which also had similar TTPs. In these cases, The threat actors used a copy of vlc.exe masquerading as the Windows binary msdtc.exe (Microsoft Distributed Transaction Coordinator). This file normally resides in C:\Windows\System32 whereas these executions were often from user-related folders such as C:\Users\<username>\Documents. The renamed vlc.exe would load a malicious DLL, libvlc.dll, which contained a Cobalt Strike payload.
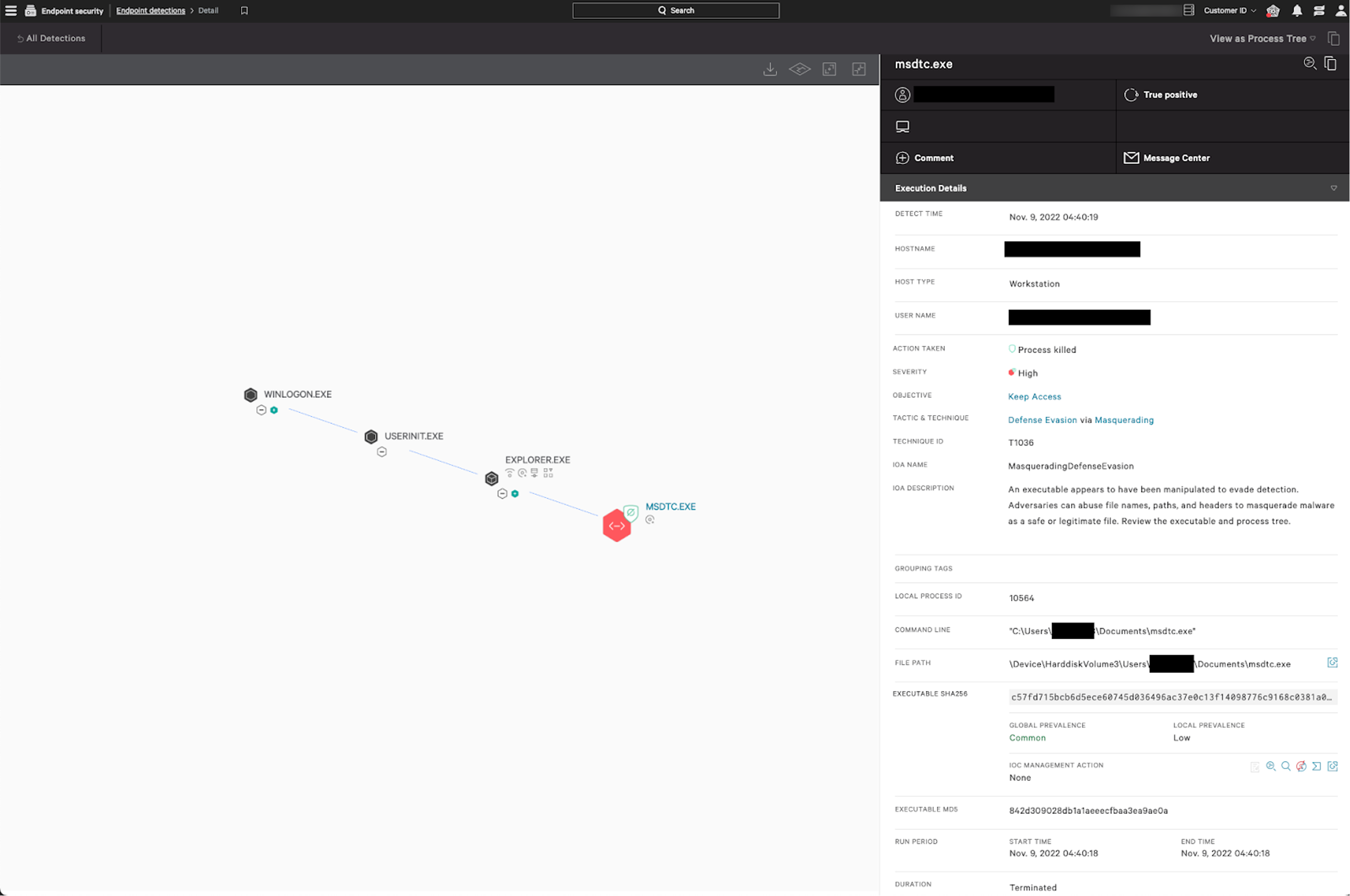
Figure 1. The Falcon platform prevents malicious execution of the binary used in this DLL side-loading example (click to enlarge)
Advantage: The CrowdStrike Falcon Platform
The Falcon platform has significant capabilities when dealing with DLL side-loading. This is due to the platform’s overlapping set of detections, which include:
- Detect on-Write (DoW), which will trigger when a malicious DLL is written to disk
- CrowdStrike behavioral indicators of attack (IOAs) alerting on malicious execution
- Sensor and cloud machine learning constantly scanning executed files
- Falcon OverWatch and CrowdStrike Intelligence teams add a layer of human expertise to look for suspicious clusters of activity across trillions of daily events.
Building on this coverage is a new evolution for Falcon detection: Advanced Memory Scanning (AMS). Advanced Memory Scanning adds another layer of protection to stop threats like malicious DLL side-loading techniques and fileless threats earlier in the kill chain to deliver on CrowdStrike’s mission to stop breaches.
Part of the role of the Endpoint Protection (EPP) Content team is to analyze intrusions and anticipate any changes in TTPs threat actors might use, and to ensure continued coverage against the latest threats. While the execution in the aforementioned intrusions was prevented, the basic IOCs for DLL side loading can be endlessly changed: hashes, filenames, execution paths or network indicators.
To add another layer of protection for CrowdStrike customers, the EPP Content team dove into the malicious DLL and extracted a set of artifacts for AMS. The team also developed customized “triggers” based on suspicious behaviors. By pairing the artifacts with the triggers, CrowdStrike can ensure that AMS performs targeted scans against real threats and remains highly performant.
Further, the memory scan specifications built from these behavioral triggers are delivered to Falcon customer endpoints in real time, ensuring the most up-to-date protection without sensor updates.
The below animation demonstrates AMS preventing this DLL side-loading technique. It replicates the abuse of vlc.exe loading a malicious version of libvlc.dll. As AMS is looking for malicious artifacts in memory, the detection is more robust than relying on other indicators that can be modified.

From the Falcon console, analysts can see the process that triggered the scan, confirm that it was killed by the sensor, and view the explanatory text noting that malicious artifacts were found in memory.
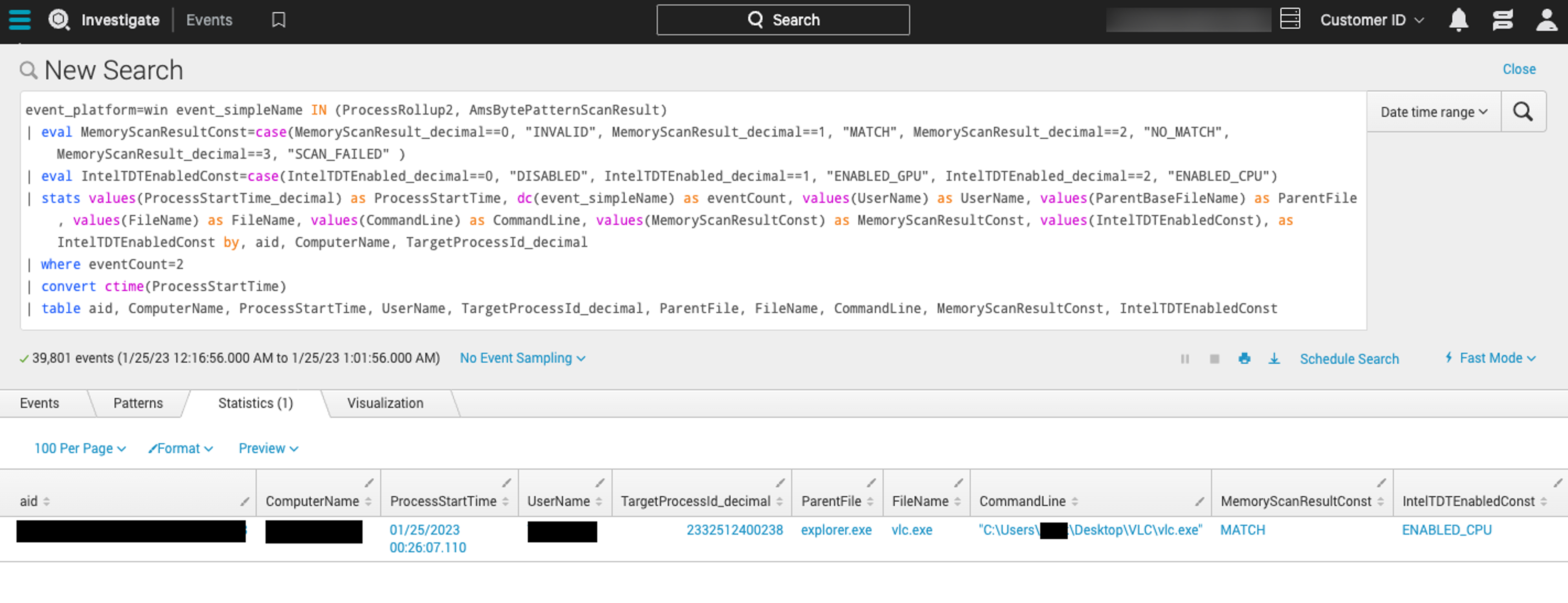
Analysts can also review AMS events in the Event Viewer and review the results of memory scans with the following example Splunk syntax:
event_platform=win event_simpleName IN (ProcessRollup2, AmsBytePatternScanResult)
| eval MemoryScanResultConst=case(MemoryScanResult_decimal==0, "INVALID", MemoryScanResult_decimal==1, "MATCH", MemoryScanResult_decimal==2, "NO_MATCH", MemoryScanResult_decimal==3, "SCAN_FAILED" )
| eval IntelTDTEnabledConst=case(IntelTDTEnabled_decimal==0, "DISABLED", IntelTDTEnabled_decimal==1, "ENABLED_GPU", IntelTDTEnabled_decimal==2, "ENABLED_CPU")
| stats values(ProcessStartTime_decimal) as ProcessStartTime, dc(event_simpleName) as eventCount, values(UserName) as UserName, values(ParentBaseFileName) as ParentFile, values(FileName) as FileName, values(CommandLine) as CommandLine, values(MemoryScanResultConst) as MemoryScanResultConst, values(IntelTDTEnabledConst), as IntelTDTEnabledConst by, aid, ComputerName, TargetProcessId_decimal
| where eventCount=2
| convert ctime(ProcessStartTime)
| table aid, ComputerName, ProcessStartTime, UserName, TargetProcessId_decimal, ParentFile, FileName, CommandLine, MemoryScanResultConst, IntelTDTEnabledConst
Not Your Average Memory Scan
When we think of “traditional” memory scanning, we often think of legacy antivirus applications constantly thrashing hard disk drives as it scans the entire memory of a system. Even on high-end systems, this was a drain on resources and significantly impacted performance.
CrowdStrike partnered with Intel Corp to reimagine memory scanning, enabling fast, high-performance scans by integrating Intel’s Threat Detection Technology (TDT) with the Falcon platform’s Advanced Memory Scanning algorithms.
To break free of traditional memory scanning constraints, the EPP Content engineering team minimized resource consumption through targeted hardware optimizations, such as GPU offloading and innovative algorithms optimized for Intel processors. To limit a memory scan’s size and duration vs traditional approaches, memory can be logically down-selected to limit scans appropriately to the artifact type. Effective guardrails on scan size and CPU limits minimize performance disruption, as should be expected for enterprise environments. These innovations result in surgical scans, more often, with minimal impact.
These highly performant scans are automated with high-fidelity behavioral triggers, leveraging the Falcon platform’s indicators of attack instead of initiating on arbitrary intervals. Automation and behavioral triggers help Advanced Memory Scanning stop fileless attacks in real time, not after a breach. Furthermore, new memory scan specifications are delivered to customer endpoints from the cloud in minutes, so customer endpoints are protected from the newest and most sophisticated fileless attacks.
Endnotes
- Learn more about dynamic-link library search order.
- Some examples over the years include:
- CSA-14023 VIXEN PANDA Activity Using Mirage Malware Leverages DLL Side-Loading Technique Previously Only Seen with PlugX, April 23, 2014
- CSIT-16115 PREDATOR PANDA Uses HexRAT Malware to Target Asian Entities, October 19, 2016
- CSA-221165 New Falha Banking Trojan Campaign Observed; Continued Use of MSI Files and C2 Dead-Drop Pastebin URLs, November 05, 2022
- CSIT-22180 Logsupport: A China-Nexus Implant Targeting Eastern Europe, December 15, 2022.
- See CSA-230012 HIVE SPIDER Affiliate Targets Telecommunications Sector Entity; Affiliate Utilized HalfAndHalf and SolarMarker for Initial Access and Persistence, January 5, 2023.
Additional Resources
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.