Credentials, Authentications and Hygiene: Supercharging Incident Response with Falcon Identity Threat Detection
CrowdStrike Incident Response teams leverage the new Falcon Identity Threat Detection (ITD) module to gain visibility and control within Microsoft Active Directory and Azure AD in eCrime and nation-state investigations
- CrowdStrike Incident Response teams leverage Falcon Identity Threat Detection (ITD) for Microsoft Active Directory (AD) and Azure AD account authentication visibility, credential hygiene and multifactor authentication implementation
- Falcon ITD is integrated into the CrowdStrike Falcon®® platform and provides alerts, dashboards and custom templates to identify compromised accounts and areas to reduce the attack surface and implement additional security measures
- Falcon ITD allows our Incident Response teams to quickly identify malicious activity that would have previously only been visible through retroactive log review and audits, helping organizations eradicate threats faster and more efficiently
Incident responders and internal security teams have historically had limited visibility into Microsoft AD and Azure AD during an investigation, which has made containment and remediation more difficult and reliant on the victim organization to provide historical logs for retrospective analysis and perform manual authentication and hygiene audits. Since CrowdStrike acquired Preempt in 2020, the Services team has leveraged a new module in the Falcon platform, Falcon Identity Threat Detection (ITD), to gain timely and rich visibility throughout incident response investigations related to Activity Directory, specifically account authentication visibility, credential hygiene and multifactor authentication implementation. This blog highlights the importance of Falcon ITD in incident response and how our incident response teams use Falcon ITD today.
How Falcon ITD Is Leveraged During Incident Response
It’s no secret that one of CrowdStrike’s key differentiators in delivering high-quality, lower-cost investigations to victim organizations is the Falcon platform. Throughout 2021, we have included Falcon ITD in the arsenal of Falcon modules when performing incident response. This new module provides both clients and responders with the following critical data points during a response:
- Suspicious logins/authentication activity
- Failed login activity, including password spraying and brute force attempts
- Inventory of all identities across the enterprise, including stale accounts, with password hygiene scores
- Identity store (e.g., Active Directory, LDAP/S) verification and assessment to discover any vulnerabilities across multiple domains
- Consolidated events around user, device, activity and more for improved visibility and pattern identification
- Creation of a “Watch List” of specific accounts of interest
In a typical incident response investigation, our teams work with clients to understand the high-level Active Directory topology numbers (e.g., domains, accounts, endpoints and domain controllers). Once the domain controllers are identified, the Falcon ITD sensor is installed to begin baselining and assessing accounts, privileges, authentications and AD hygiene, which typically completes within five to 24 hours. Once complete, Falcon ITD telemetry and results are displayed in the Falcon platform for our responders and clients to analyze.
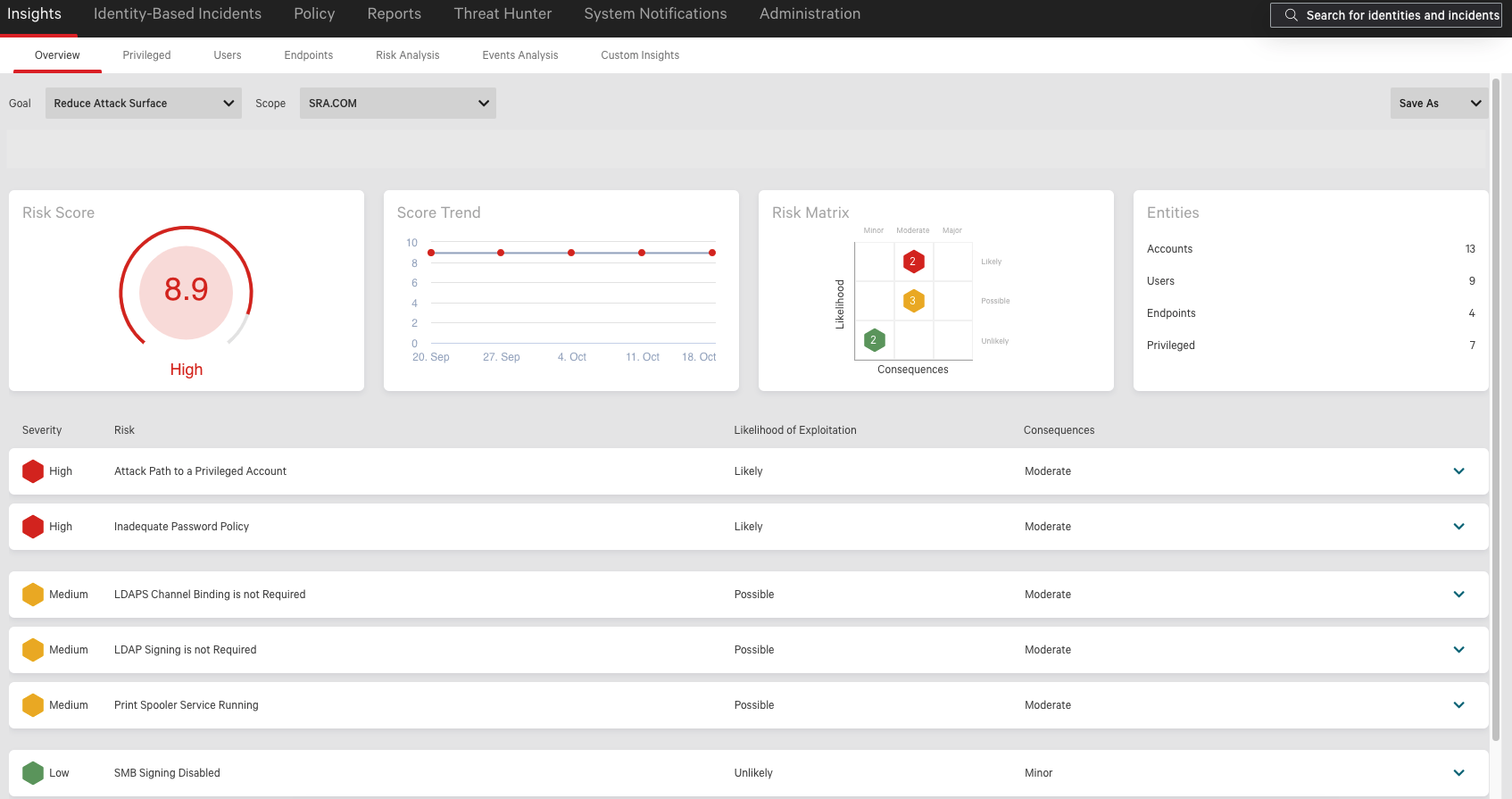
Figure 1 shows the Falcon ITD Overview dashboard, which features attack surface risk categories and assesses the severity as Low, Medium or High. CrowdStrike responders use this data to understand highly exploitable ways an attacker could escalate privileges, such as non-privileged accounts that have attack paths to privileged accounts, accounts that can be traversed to compromise the privileged accounts’ credentials, or if the current password policies allow accounts with passwords that can be easily cracked.
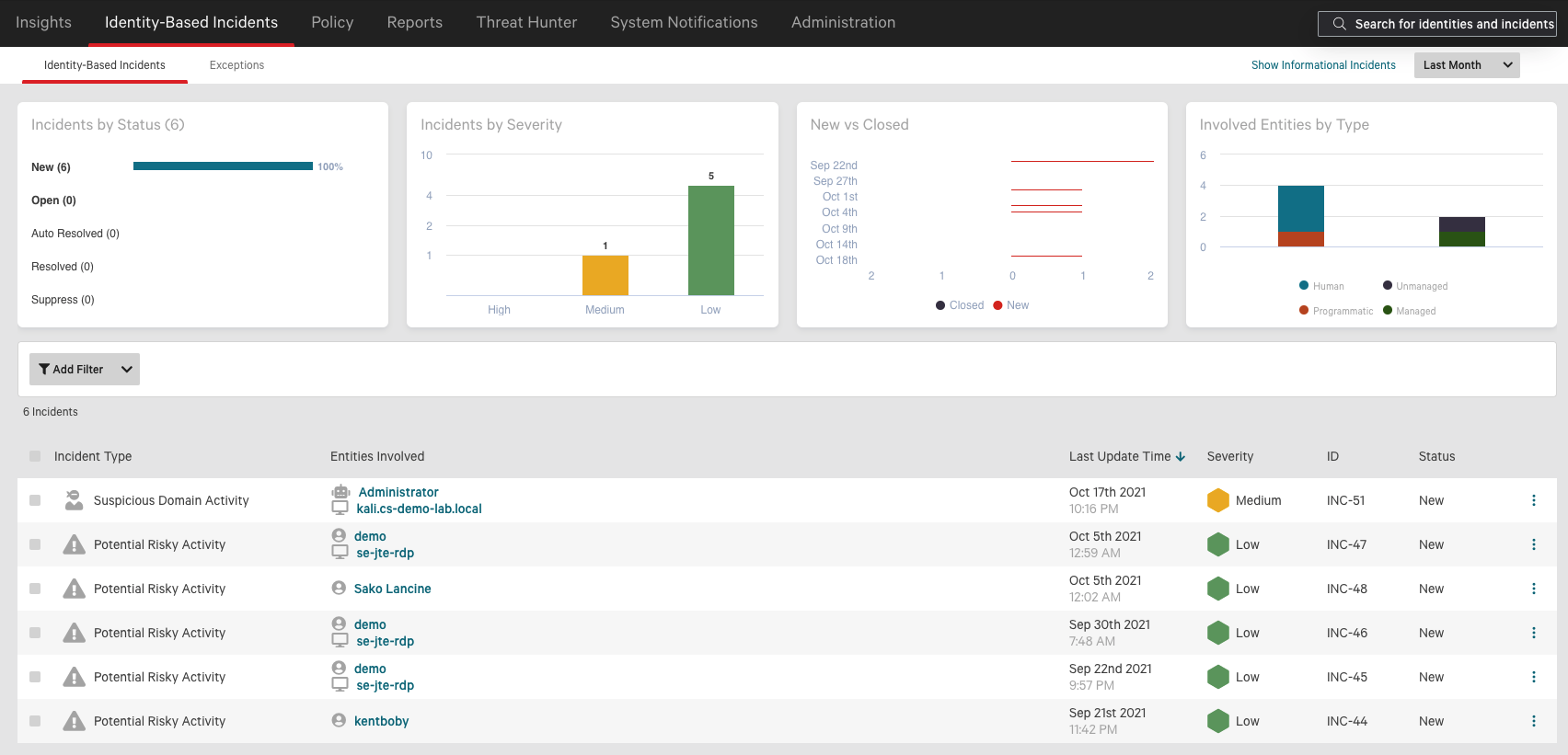
Figure 2 shows the main Incidents dashboard. This dashboard highlights suspicious events based on baseline patterns and indicators of authentication activity, and also includes any custom detection patterns the CrowdStrike incident response teams have configured, such as alerting when an account authenticates to a specific system.
CrowdStrike responders leverage this information to understand and confirm findings such as the following scenarios:
- Credentials were used to perform unusual LDAP activity that fits Service Principal Name (SPN) enumeration patterns
- An account entered the wrong two-factor verification code or the identity verification timeout was reached
- Credentials used are consistent with “pass the hash” (PtH) techniques
- Unusual LDAP search queries known to be used by the BloodHound reconnaissance tool were performed by an account
In addition to the above built-in policies, CrowdStrike responders, in consultation with clients, may also configure custom rules that will trigger alerts and even enforce controls within Falcon ITD, such as the following:
- Alert if a specific account or group of accounts authenticates to any system or specific ones
- Enforce a block for specific accounts from authenticating to any system or specific ones
- Enforce a block for specific authentication protocols being used
- Implement identity verification from a 2FA provider such as Google, Duo or Azure for any account or for a specific one attempting to authenticate via Kerberos, LDAP or NTLM protocols
- Implement a password reset for any account that has a compromised password
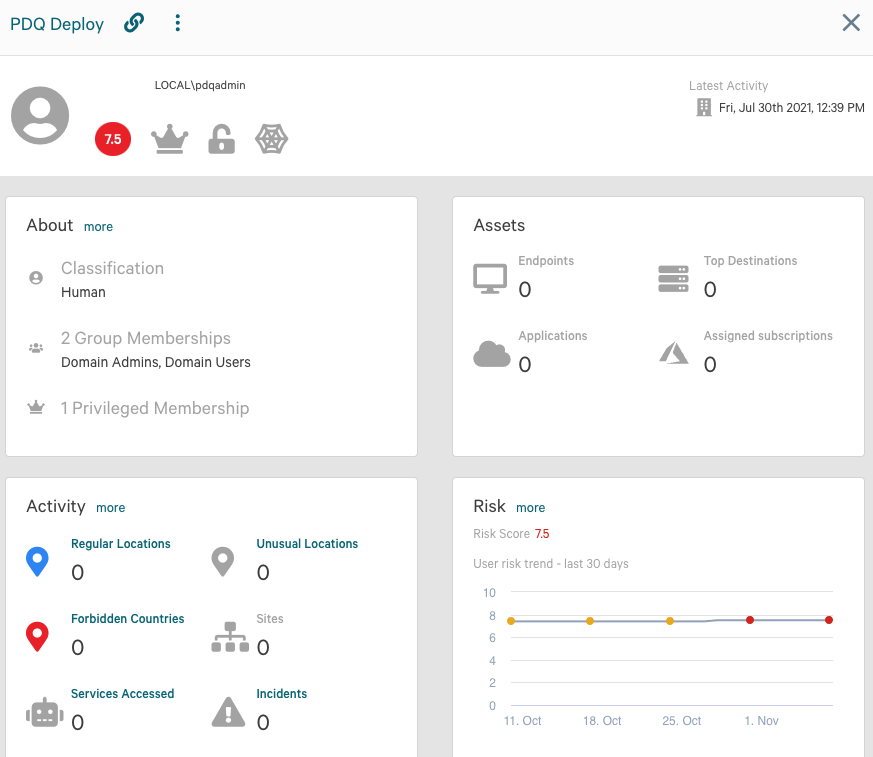
In other cases, responders are looking for additional information on accounts of interest that were observed performing suspicious activity. Typically, incident responders would have to coordinate with the client and have the client’s team provide information about that account (e.g., what group memberships it belongs to, what privileges the account has, and if it is a service or human account). Figure 3 shows how Falcon ITD displays this information and more, including password last change date, password strength and historical account activity. This is another example of how CrowdStrike responders are able to streamline the investigation, allowing our client to focus on getting back to business in a safe and secure manner.
Hygiene and Reconnaissance Case Study
During a recent incident response investigation, CrowdStrike Services identified an eCrime threat actor that maintained intermittent access to the victim’s environment for years. The threat actor leveraged multiple privileged accounts and created a domain administrator account — undetected — to perform reconnaissance, move laterally and gather information from the environment.
CrowdStrike incident responders leveraged Falcon ITD to quickly map out permissions associated with the accounts compromised by the threat actor, and identify password hygiene issues that aided the threat actor. By importing a custom password list into Falcon ITD, incident responders were able to identify accounts that were likely leveraged by the threat actor with the same organizational default or easily guessed password.
Falcon ITD also allowed CrowdStrike’s incident response teams to track the threat actor’s reconnaissance of SMB shares across the victim environment. The threat actor leveraged a legitimate administrative account on a system that did not have Falcon installed. Fortunately, the visibility provided by Falcon ITD still alerted incident responders to this reconnaissance activity, and we coordinated with the client to implement remediations to eradicate the threat actor.
Multifactor Authentication and Domain Replication Case Study
During another investigation, CrowdStrike incident responders identified a nation-state threat actor that compromised an environment and had remained persistent for multiple years. With this level of sophisticated threat actor and the knowledge they had of the victim environment’s network, Active Directory structure and privileged credential usage, no malware was needed to be able to achieve their objectives.
In light of the multiyear undetected access, CrowdStrike incident responders leveraged Falcon ITD to aid in limiting the threat actor’s mobility by enforcing MFA validation for two scenarios, vastly reducing unauthorized lateral movement capabilities:
- Enforce MFA (via Duo) for administrator usage of RDP to servers
- Enforce MFA (via Duo) for any user to RDP from any server to a workstation
Falcon ITD’s detection capabilities were also paramount in identifying the threat actor’s resurgence in the victim network by alerting defenders to a domain replication attack. This allowed defenders to swiftly identify the source of the replication attack, which emanated from the victim’s VPN pool, and take corrective action on the VPN, impacted accounts and remote resources that were accessed by the threat actor.
Conclusion
Falcon Identity Threat Detection provides CrowdStrike incident response teams with another advantage when performing investigations into eCrime or nation-state attacks by providing increased visibility and control in Active Directory, which had previously been unachievable at speed and scale.
Additional Resources
- For more information on Falcon ITD, see the overview page and the data sheet.
- For more information on CrowdStrike Services, please visit the overview page.