CrowdStrike Falcon® Identity Protection
Stop modern identity-based attacks in real-time
The industry’s only unified platform for identity threat detection and response (ITDR) and endpoint security.
From siloed point products that miss modern attacks to unified, real-time prevention
The Falcon Identity Protection difference
Customer assessment
$2M
savings over three years by consolidating endpoint and identity protection1
Customer assessment
85%
faster detection of identity attacks, offsetting ~5,000 investigation hours1
Commercial Bank of California
34%
reduction in cyber insurance premiums2
Mercedes-AMG Petronas F1 Team outpaces modern attacks with Falcon Identity Protection
The standard for unified identity protection
8 out of 10 attacks involve stolen or compromised credentials. Eliminate point products and stop modern threats in real-time with the world’s only unified platform for ITDR and endpoint security.
One platform. One console. One agent.
Falcon Identity Protection unifies endpoint and identity security with a single agent and console for immediate time-to-value. Extend your protection further and close the skills gap with industry-leading 24/7 MDR services when you need it.
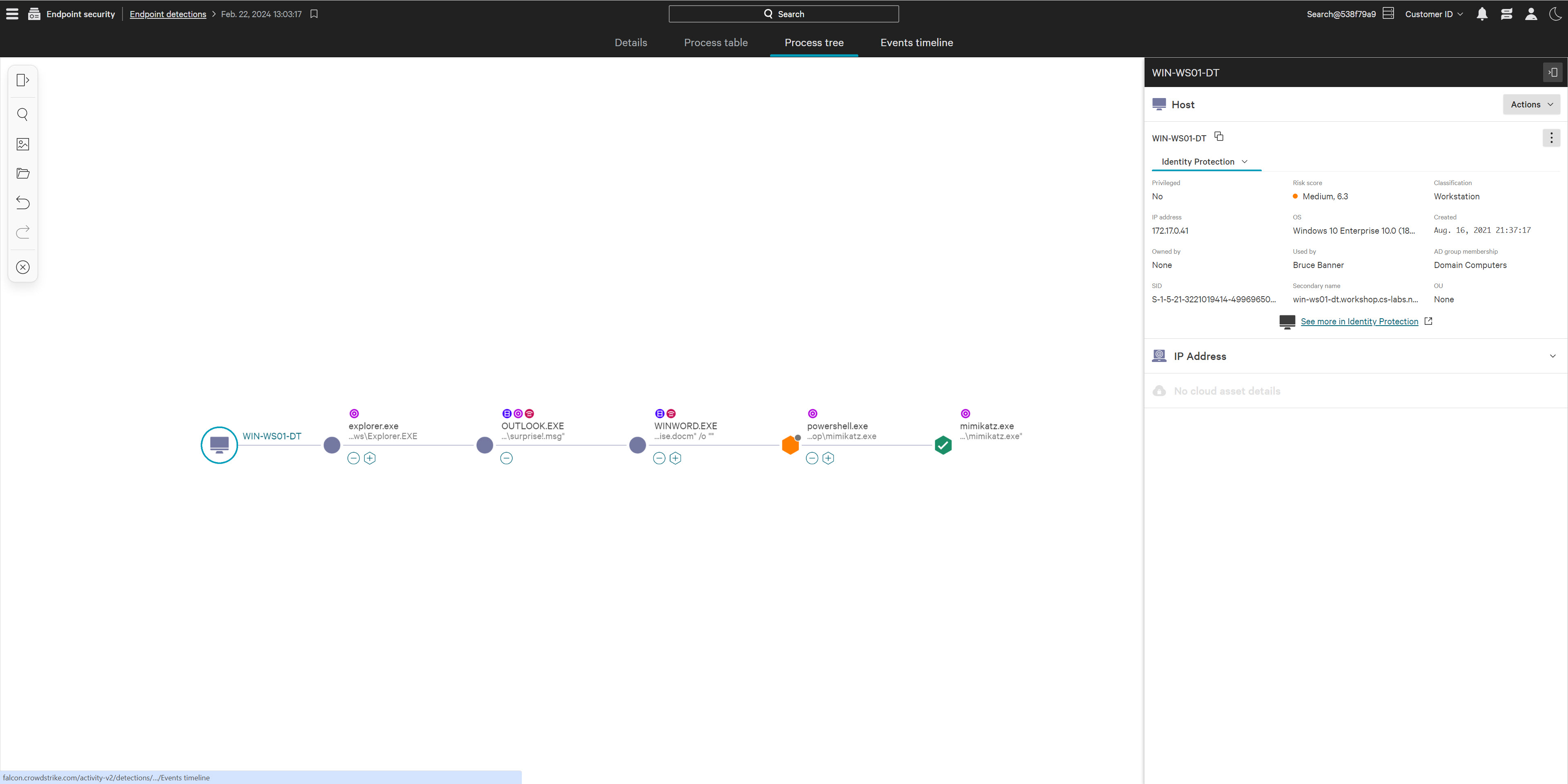
Unified identity protection for hybrid environments
Stop attacks from endpoint to cloud with complete visibility across traditional Active Directory (AD) and cloud identity providers such as Entra ID and Okta, empowered with industry-leading threat intelligence.
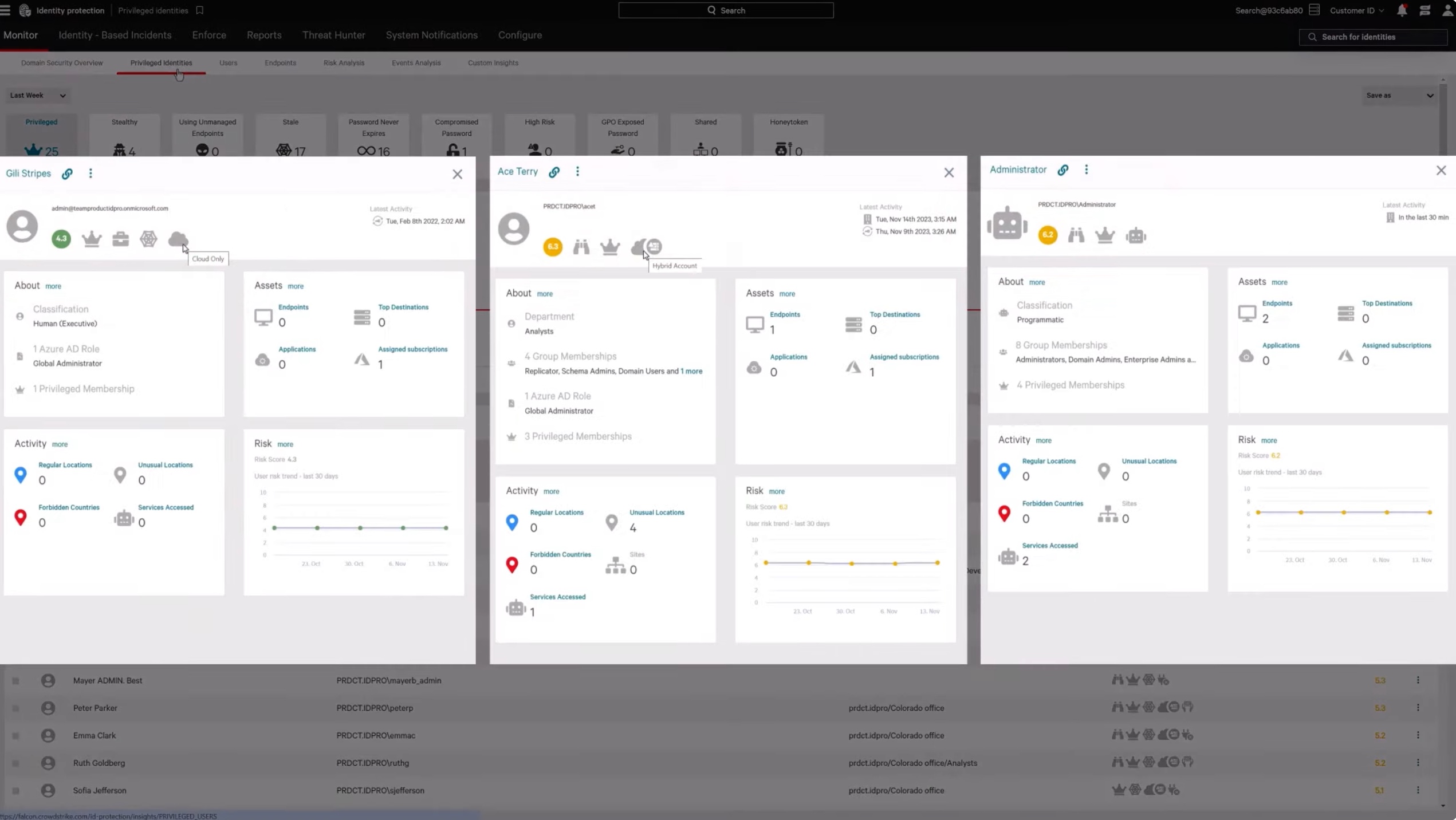
Find stealthy attacks with AI-powered detection
Get an automatic AI-driven baseline of normal user behavior to quickly find anomalies that reveal sophisticated threats as they attempt to move across endpoints and identities.
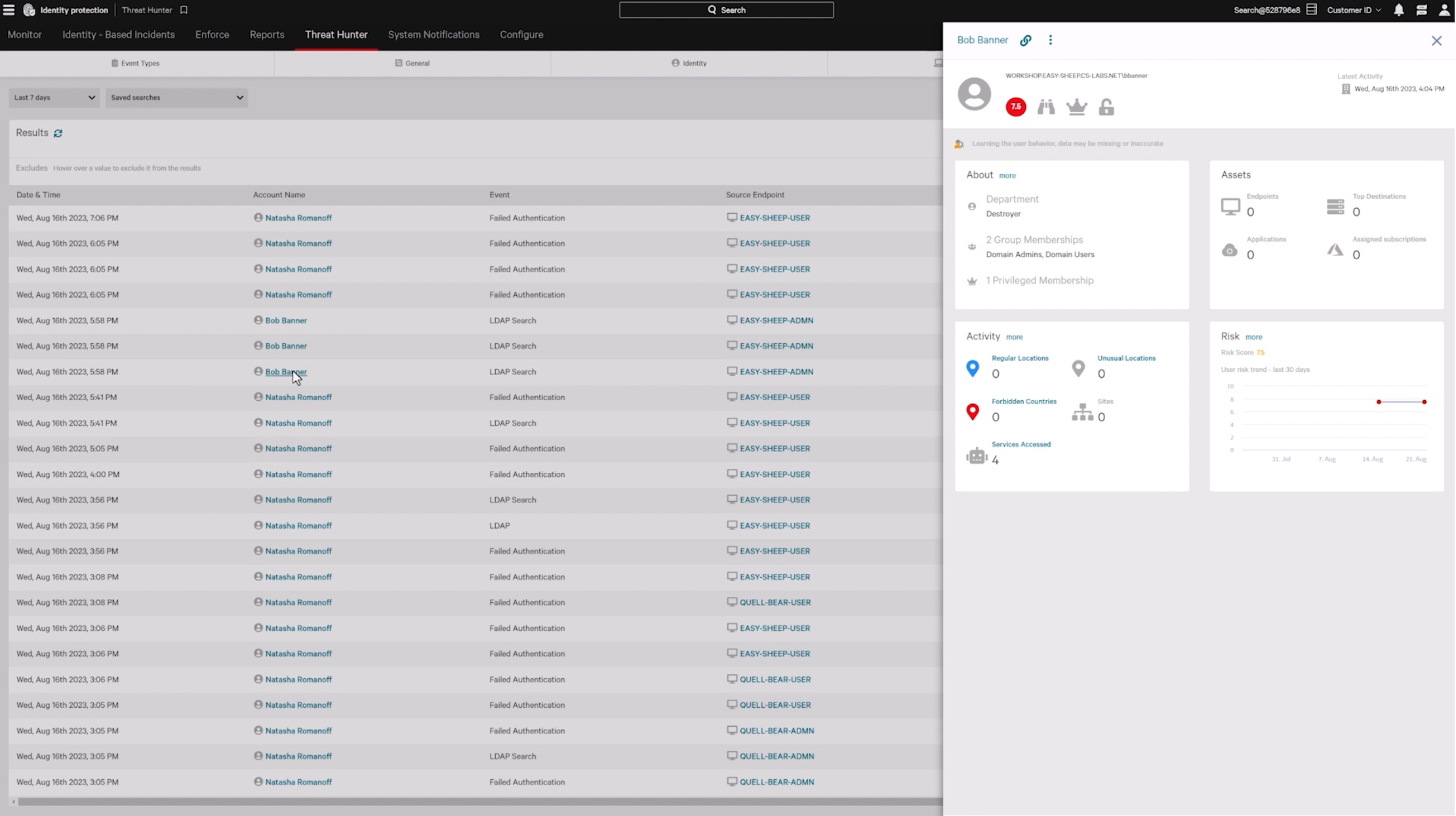
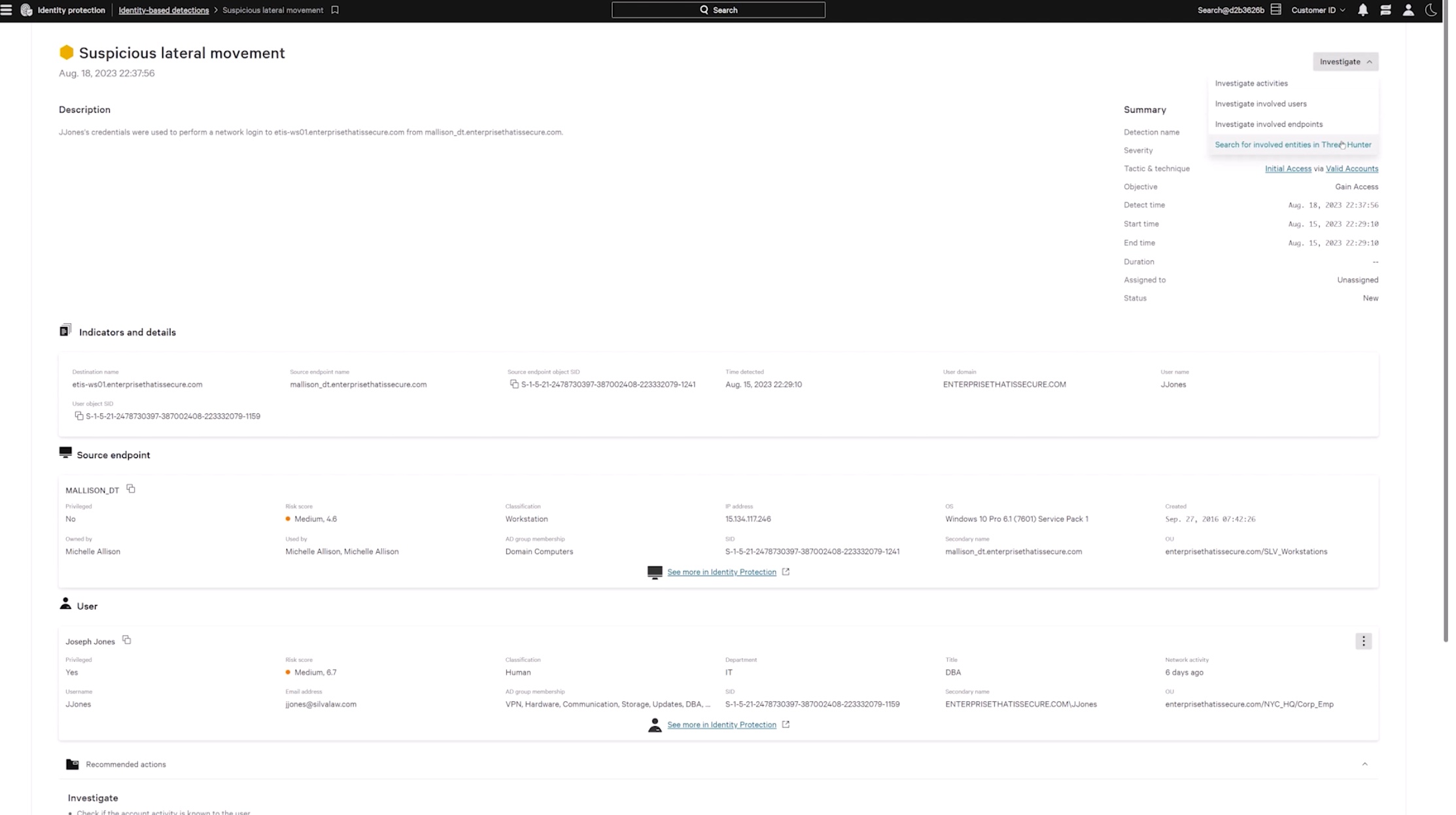
Stop lateral movement in real-time
Block threats in real time as soon as lateral movement is detected across both the authentication layer or endpoints. Improve your response times dramatically and eliminate the need to hunt through logs.
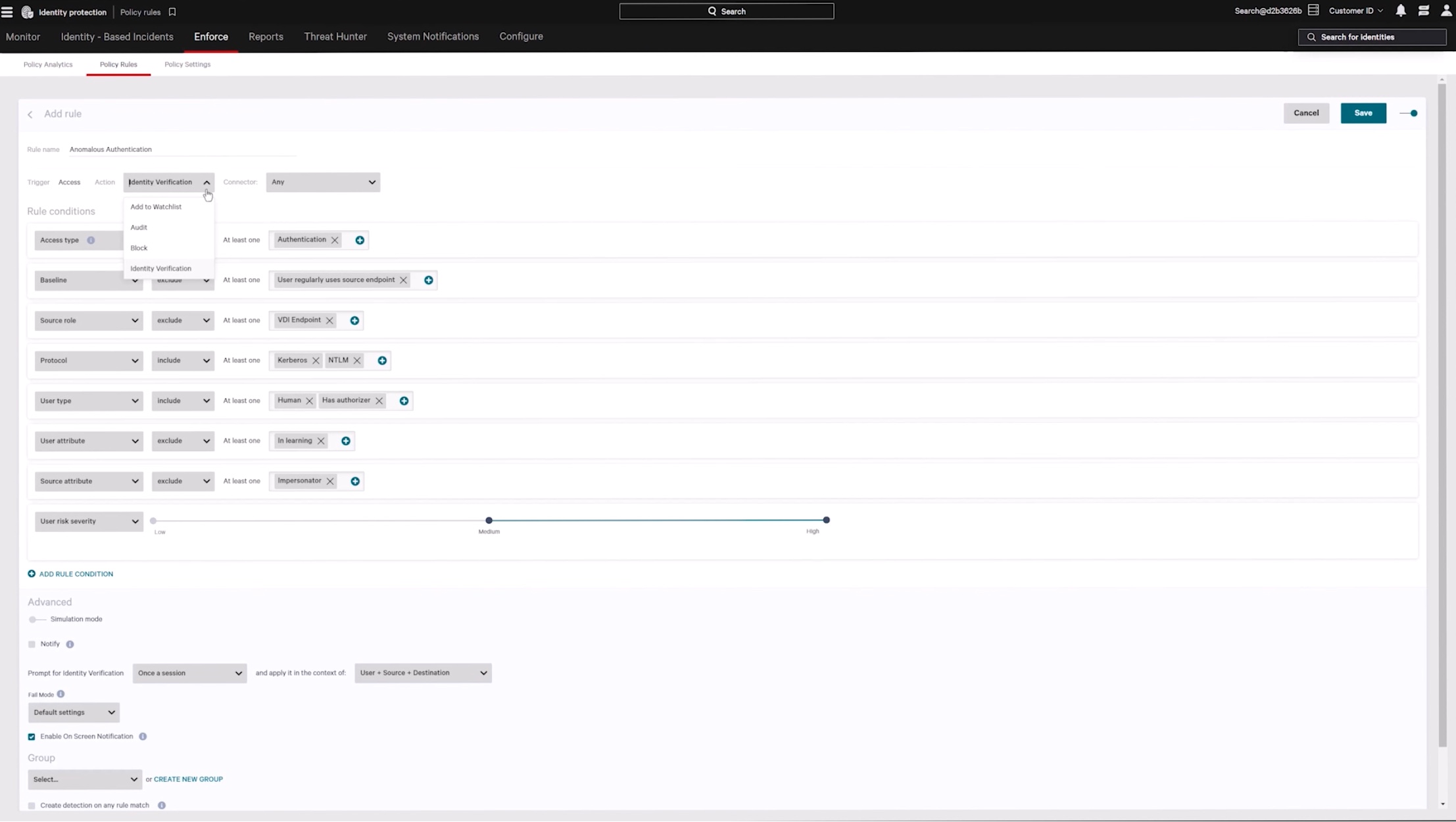
Enforce risk-based conditional access
Continuously monitor user behavior and risk context with dynamic enforcement of multi-factor authentication (MFA) when risk changes. Seamlessly extend MFA coverage to legacy systems and protocols that are likely to be exploited.
Trusted by industry leaders to
stop modern attacks
See the power of Falcon Identity Protection in under three minutes

Get an Identity Security Risk Review
Evaluate your current Microsoft Entra ID and Active Directory security posture with a detailed report and a 1:1 session with a CrowdStrike identity expert.
Schedule free reviewFeatured resources
1 These numbers are projected estimates of average benefit based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.
2 Results are from Commercial Bank of California Individual results may vary by customer.