How Falcon Horizon Ensures Secure Authentication to Customer Clouds
One of the biggest challenges of the cloud today is properly configuring resources to prevent breaches. Various breaches have proven this, such as the LA Times breach in 2018, where an S3 bucket was misconfigured to allow public write access. This publicly accessible bucket was abused to perform a Coinhive cryptojacking attack on the LA Times website. One such solution to this problem is the emergence of cloud security posture management (CSPM) tools. CSPM tools typically scan environments for misconfigurations, offer secure remediations and provide information about the risk the misconfigurations pose to a cloud environment.
This blog will discuss the CrowdStrike® CSPM module, Falcon HorizonTM, and how it was designed to support best practices across all three clouds and securely integrate into customer environments.
Falcon Horizon
Falcon Horizon is a new CrowdStrike module that provides valuable security alerts for misconfigurations in a cloud environment while minimizing noise and unnecessary alerts. One primary goal of the product is to securely integrate with customer clouds, whichever cloud that may be. In the following, this blog outlines the different steps taken by the Horizon team to ensure this security.
Securing Cross-Account Authentication in the Cloud
AWS Cross-Account Roles and External IDs
In Amazon Web Services (AWS), the most secure way to grant a third-party product access to your cloud environment is through IAM roles that grant cross-account access and require a unique, unguessable external ID. An external ID can be thought of as a password, but it should not be considered a password because it can be viewed in cleartext in a variety of places, such as through IAM, CloudTrail, CloudFormation and potentially others. If set, it is required to be supplied when attempting to assume that role.
In line with best practices, Falcon Horizon utilizes cross-account IAM roles with an external ID. That external ID is a cryptographic UUID that is randomly generated and is unique across each customer of the product. Additionally, the customer is not able to configure this value themselves, removing the risk of a weak external ID that may be brute forced.
The following screenshot shows an example IAM role trust policy that is applied to the Horizon IAM role created in customer accounts.
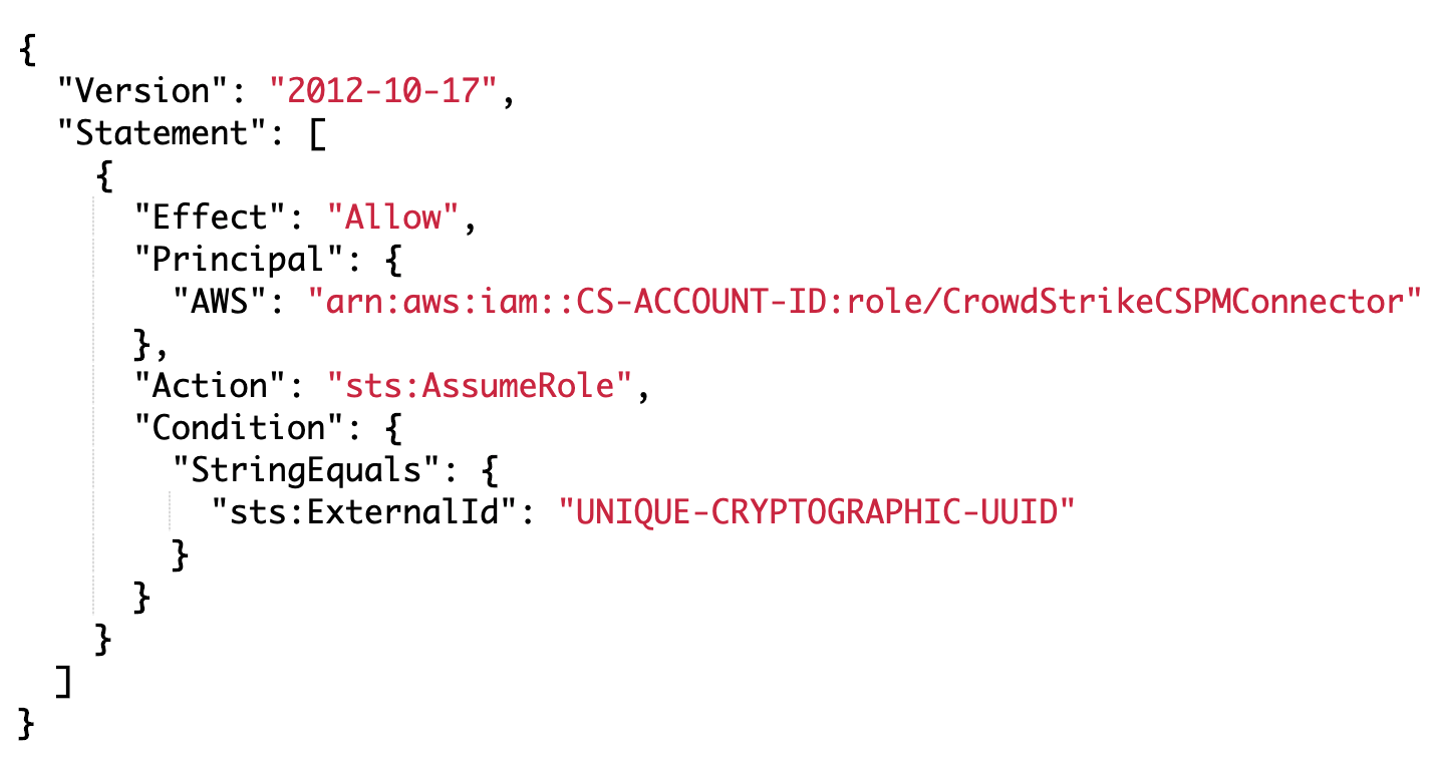
The permissions granted to the cross-account IAM role are also important. The role that gets created in Horizon customer accounts is only granted the necessary permissions to identify misconfigurations in the supported resources. This means that no write access is granted to the role and only the minimum read-access permissions are granted, reducing the blast radius of a compromise in a customer’s environment.
As a last step, the name of the IAM role contains a random string so that it is more difficult for an attacker to guess the name of the Horizon integration role across customer accounts if they were to discover a certain AWS account is using Falcon Horizon.
Azure Certificate Authentication, JWTs, and Proper Encryption
In Microsoft Azure, certificate authentication to a service principal in the customer’s account is used. This means that when a customer begins the onboarding process for Horizon, a public and private key pair is generated by CrowdStrike that is then stored along with the Azure Tenant ID and Subscription ID in a key management service (KMS) encrypted location. The public key is then applied to a service principal in the customer account. Using a Client_Assertion, a JSON Web Token (JWT) is requested through the OAuth client to receive credentials to authenticate as the service principal in question.
The service principal is only granted access to read APIs, meaning it is only supplied read access to the necessary resources that are required and does not require any write access permissions to the environment.
GCP Service Accounts, Key Files, and Proper Encryption
For the forthcoming Google Cloud Platform (GCP) integration, Horizon takes advantage of a cross-account service account and a key file for that service account. Prior to the onboarding process, CrowdStrike creates a GCP service account in their own environment, which is then provided to the customer through an onboarding script. A service account key file is created for that service account, where the private key is encoded and KMS encrypted to protect the contents. This removes the need for customers to create a service account for CrowdStrike in their GCP projects.
Once a customer begins onboarding Horizon to their GCP environment, they are provided a script that will allow the service account access to their GCP environment with low-level permissions. The only permissions required are read permissions, meaning read access is provided for resources that the product needs to access to identify security risks and does not provide any write access to the environment.
Conclusion
Secure integration into customer clouds follows the security-first principle of CrowdStrike, ensuring customers are provided the necessary tools to secure their environment and that those tools are securely integrated into those environments. Security is key, and you should never compromise. To learn more about how CrowdStrike can help you gain visibility, continuously monitor threats and ensure compliance in the cloud, enabling DevOps to deploy applications with greater speed and efficiency, visit crowdstrike.com.
Additional Resources
- Visit our website to learn more about the CrowdStrike Cloud Security suite of solutions.
- Learn more about the Falcon Horizon: CSPM, CrowdStrike’s new cloud security posture management solution.
- Learn more about the powerful CrowdStrike Falcon®® platform by visiting the webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.


