CrowdStrike Falcon® Cloud Security
Cloud Security
Posture Management
CrowdStrike Falcon® Cloud Security
Cloud Security
Posture Management
Comprehensive security enforcement, visibility, and compliance across the entire hybrid and multi-cloud environment.
Visibility, security posture, and compliance in a single and unified platform
Unify visibility across clouds
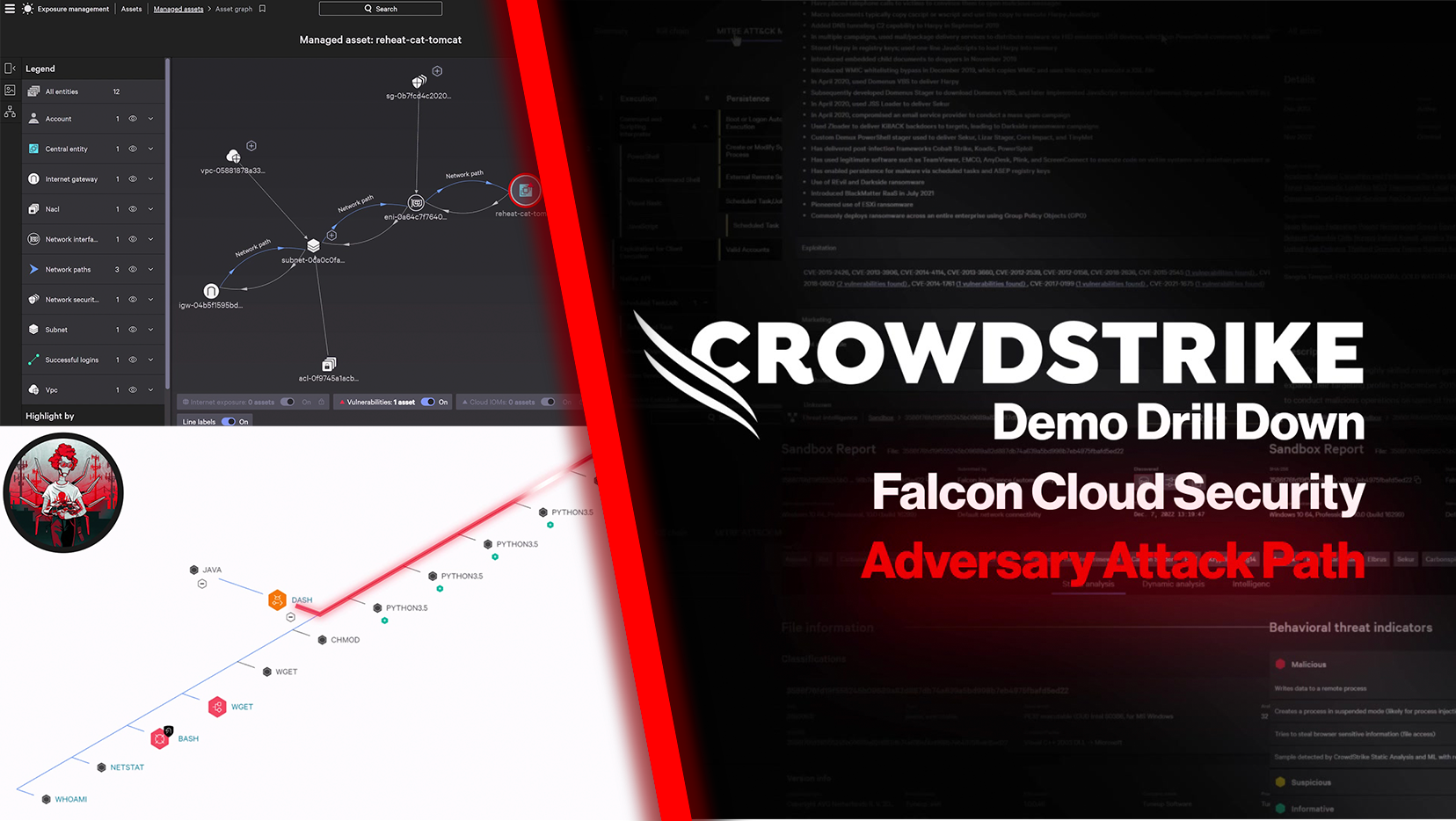
Falcon Cloud Security delivers continuous agentless discovery and visibility of cloud-native assets from the host to the cloud, providing valuable context and insights into the overall security posture and the actions required to prevent potential security incidents.
Prevent misconfigurations and stay compliant
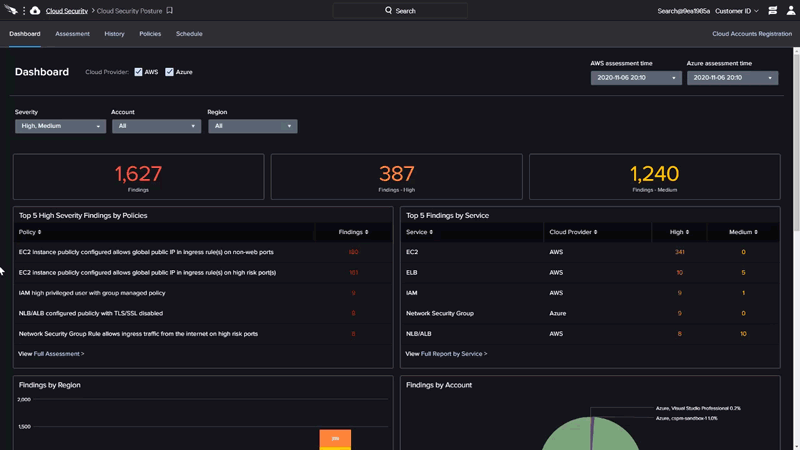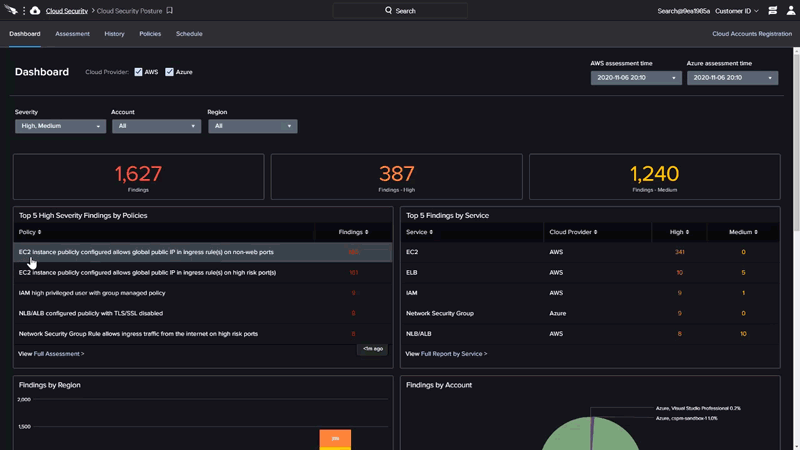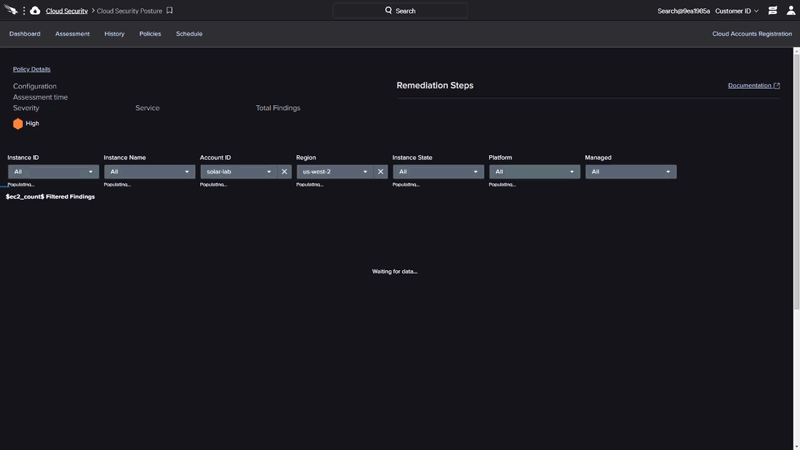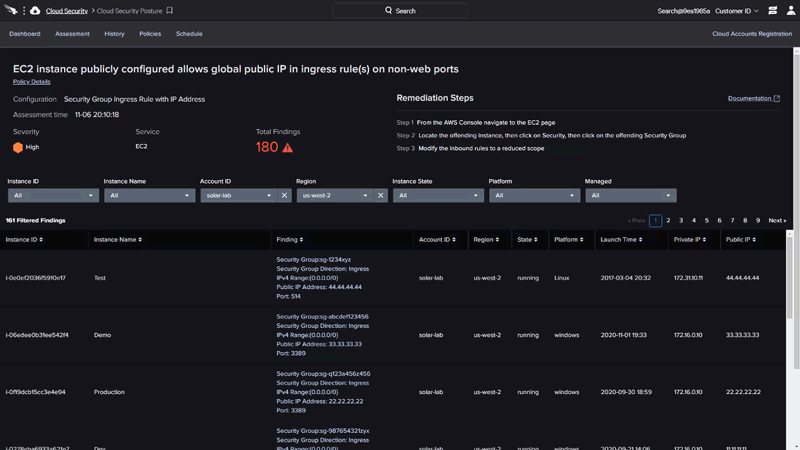
Falcon Cloud Security provides intelligent agentless monitoring of cloud resources to detect misconfigurations, vulnerabilities and threats to resolve security risks while enforcing compliance.
Detect and prevent threats in real time
Falcon Cloud Security's adversary-focused approach provides real-time threat intelligence on 230+ adversary groups, indicators of attack (IOA) and indicators of misconfiguration (IOMs), enabling teams to respond faster and stop breaches.
Cloud security made simple
Get complete visibility
Get complete visibility
- See everything: Visualize, investigate, and secure all cloud assets, identities, and applications in a single and unified cloud-native platform.
- Visualize the attack path: Stop supply chain attacks and reduce time to respond with automated context across endpoint, cloud workloads and runtime data.
- Enforce security posture: Manage and enforce security group policies across accounts, projects, regions and virtual networks from a single console.
- Simplify privileged access management: Secure all cloud identities and entitlements, predicting and preventing identity-based threats.
Manage, prevent and remediate misconfigurations
Manage, prevent and remediate misconfigurations
- Eliminate misconfigurations: Detect, prevent and remediate attacks (IOAs) and misconfigurations (IOMs) across multi and hybrid clouds, leveraging the industries best threat intelligence.
- Secure Identity and permissions: Ensure AzureAD and IAM users have the correct permission leveraging Identity Analyzer and attack path to stop identity based threats.
- Reduce alert fatigue: Remediate issues faster and reduce SOC costs with enhanced policy management and accurate alerts.
- Ensure resilience: Monitor database instances and verify that high availability, backups and encryption are enabled, and security groups set to limit exposure.
Detect and respond to threats in real time
Detect and respond to threats in real time
- Real-time threat detection: Leverage the largest threat intelligence database and behavior base TTP/IOA across the entire cloud estate to stop breaches.
- Accelerate response: Reduce the time it takes to remediate a breach with comprehensive policies, auto-remediation and accurate alerting and reporting.
- Confidence scoring and prioritization: Continuously aggregate, assess and score threats and configurations to accurately identify malicious activity, reducing the time to understand and respond.
- One-click remediation: Access security posture with agentless security and if necessary, deploy a single Falcon agent for containerized applications and full runtime protection.
Health Check
Try a free health check of your cloud security posture and infrastructure
Get my health check
Health Check
Try a free health check of your cloud security posture and infrastructure
Get my health check
Other Falcon Cloud Security Solutions
Cloud Workload Protection
Provides comprehensive breach protection across private, public, hybrid and multi-cloud environments, allowing customers to rapidly adopt and secure technology across any workload.
Container Security
Accelerates critical detection, investigation and threat hunting tasks performed on containers — even on ephemeral containers after they have been decommissioned — enabling security teams to secure containers at the speed of DevOps without adding friction.
Cloud Security Assessment
Test and evaluate your cloud infrastructure to determine if the appropriate levels of security and governance have been implemented to counter inherent security challenges.
Customers trust CrowdStrike





"Love the integrations with other companies allowing better visibility and security by leveraging other products in niche markets."
Security Manager, Medium Enterprise Banking Company
"CrowdStrike Cloud Security provides continuous and breach protection in my organization, as well as visibility and end-to-end protection from the host to the cloud."
Anulika Efobi, Cyber SOC Analyst, UBA PLC
"One of the best decisions we made moving to a cloud-based platform."
Joseph Daniels, CIO, Illinois State Treasurer
"Great products and support. I feel secure with CrowdStrike running in my environment."
Jason Grant, IT Manager, Diversified Conveyors Inc.
"CrowdStrike allows me to sleep at night."
System Administrator, State & Local Government
"It continues to delight and provides exactly what we need as part of our cyber defense strategy. "
Peter Locke, Senior Manager - Information Security, Partners Life
"We evaluate it very highly, as it provides the best protection for our investment."
Project Manager, Large Enterprise Telecommunications Services Company
"CrowdStrike provides visibility into cloud infrastructure and configuration. "
Engineer, Medium Enterprise Financial Services Company
"It catches things that are otherwise invisible to us."
IT Professional, Medium Enterprise Computer Services Company
"Ease of deployment, reliable detection, and capabilities."
Timothy Jee, Security Manager, New American Funding
Rated 4.7 by customers in
Gartner Peer Insights and G2
Gartner Peer Insights and G2
Tested and proven leader
CrowdStrike is proud to be recognized a leader by industry analyst and independent testing organizations.

Learn more about how CrowdStrike won the 2022 CRN Tech Innovator Award for Best Cloud Security.
Learn why Frost & Sullivan ranked CrowdStrike as a leader in Cloud-Native Application Security Platform (CNAPP).
CrowdStrike received the highest position of all vendors in the Strategy category, and received the highest scores possible in the Vision and Innovation criteria in The Forrester Wave™: Cloud Workload Security, Q1 2024.