A new, significant vulnerability was recently discovered, hiding in plain sight. CVE 2021-3156, also known as Baron Samedit, is considered potentially serious. The Cybersecurity & Infrastructure Security Agency (CISA) is encouraging users and administrators to review this vulnerability and patch it as quickly as possible. With this CVE, a threat actor could gain unprivileged root access and exploit Linux and Unix-based operating systems.
Since this vulnerability utilizes a default utility within most Linux systems, the potential for exploitation could be dangerous to many organizations. Recognizing the need for IT staff to quickly identify which Linux systems are at risk and track remediation progress, CrowdStrike has developed a custom threat dashboard.
About CVE-2021-3156
The disclosure for this vulnerability occurred on Jan. 26, 2021. It’s a heap-based overflow vulnerability identified in sudo, a utility that allows users to run programs with another user’s security privileges. The exploitation of this vulnerability would allow an unprivileged user to gain root-level privileges. It was first introduced in July 2011 and had been hiding in plain sight for almost 10 years. When combined with a remote code execution exploit, an attacker could gain access to a system and elevate its privileges.
Why Baron Samedit Is a Serious Risk
CVE-2021-3156 is listed in the National Vulnerability Database with a 7.8 score. This is considered a “high” score, and one to consider prioritizing. CrowdStrike researchers have moderate confidence that attackers could weaponize this vulnerability because of the access to root-based privileges, along with the fact that sudo is a default utility that is available in most Unix distributions. It’s especially dangerous, as the user does not need any type of special privileges to use this exploit. At the time of this publication, CrowdStrike has not observed in-the-wild exploitation of this vulnerability.
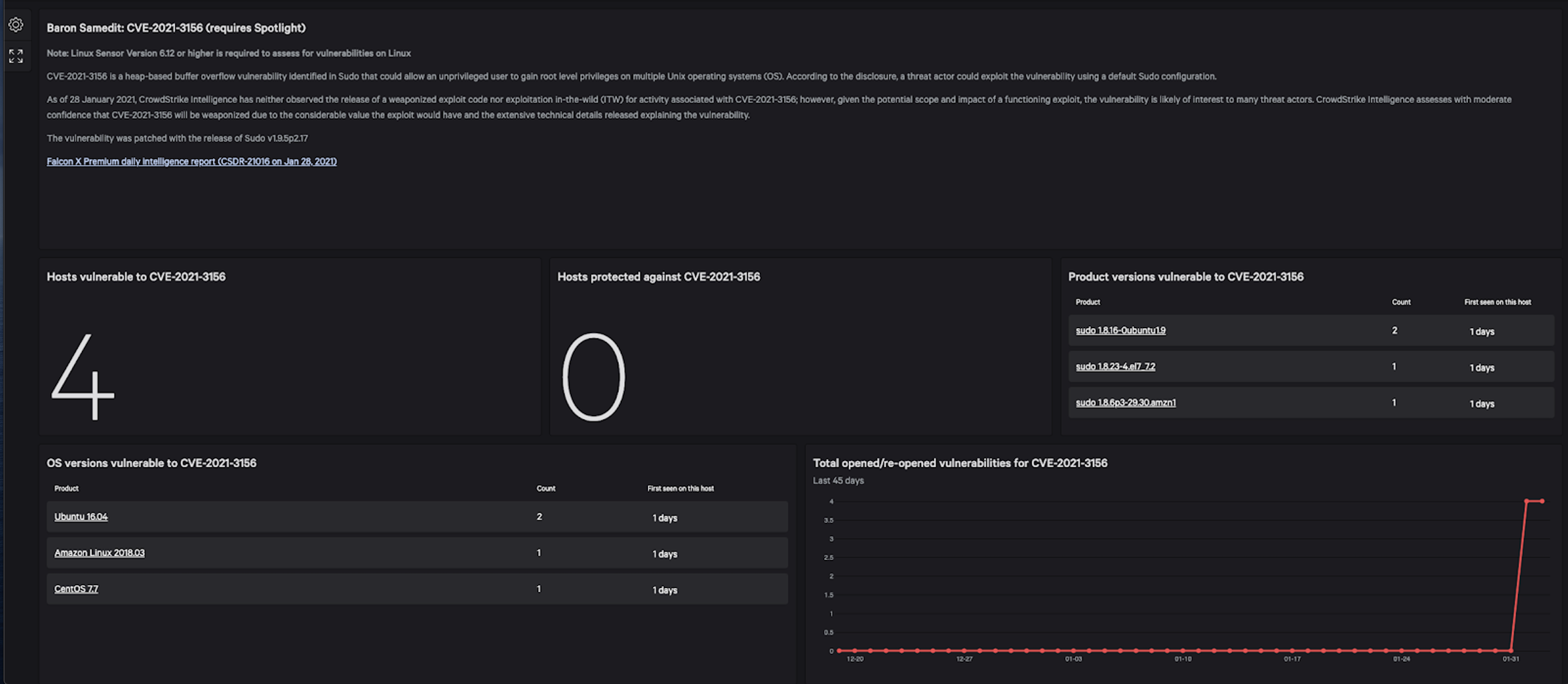 CrowdStrike custom dashboard enables customers to identify which systems are vulnerable to CVE-2021-3156 quickly. (Click to enlarge)
CrowdStrike custom dashboard enables customers to identify which systems are vulnerable to CVE-2021-3156 quickly. (Click to enlarge)CrowdStrike Provides Customers with Custom Threat Dashboard for Linux Vulnerability
To enable customers to quickly see which Linux hosts are vulnerable, CrowdStrike has developed a custom dashboard specific for Falcon Spotlight™ customers. The dashboard offers details on the threat analysis provided by researchers and includes at-a-glance views of detailed information on hosts and systems vulnerable to CVE-2021-3156, as well as the count of vulnerable product versions. CrowdStrike also released a detection for exploiting this vulnerability for Falcon Insight™ customers. IT can patch hosts with sudo v1.9.5.p.2.17 or higher. As with other custom dashboard releases, Spotlight customers can access these predefined dashboards by navigating to Dashboards > Trending Threat.
Because the CrowdStrike Falcon® platform operates in the cloud via a single lightweight agent, it can provide constant and immediate visibility to vulnerabilities such as CVE-2021-3156. To see how Falcon Spotlight works in action, watch this Falcon use case video and learn how you can quickly see and resolve any vulnerabilities in your environment.
Additional Resources
- Learn more about Falcon Spotlight.
- Read about the custom CrowdStrike dashboard for CVE-2020-1472 ZeroLogon Vulnerability.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































