A serious and potentially dire patch warning has been issued by the Department of Homeland Security (DHS) advisory team, the Cybersecurity and Infrastructure Security Agency (CISA). The alert, labeled “Emergency Directive 20-04,” is based on vulnerability CVE-2020-1472 and requires U.S. federal agencies to immediately patch Microsoft Windows servers.
Because of the severe nature of this vulnerability, CrowdStrike has recognized the immediate importance for IT staff to determine if their environment is susceptible to this threat and has developed a custom dashboard to address it. This preset dashboard provides detailed analysis from CrowdStrike® threat intelligence, an overview of vulnerable domain controllers and patching recommendations.
While some of the statements from DHS concerning vulnerabilities are recommendations, the CVE-2020-1472 vulnerability has been deemed an “unacceptable risk” to its agencies that “require an immediate and emergency action.” This vulnerability has been given the maximum base score of 10.0 under the Common Vulnerability Scoring System (CVSS) and proof-of-concept (POC) code is available — which means it is likely the vulnerability has also been incorporated in adversaries' framework or tooling. The following explains what makes this vulnerability so threatening.
What Is CVE-2020-1472?
This vulnerability is located in Microsoft Windows Netlogon Remote Protocol (MS-NRPC), an area that is responsible for the authentication of Active Directory. It’s named “Zerologon” because if an attacker can successfully deploy this exploit, it’s authenticated by submitting a string of zeros.If exploited, the vulnerability allows adversaries to compromise the Windows Server domain controllers. Once the attackers have gained access, it would allow them to compromise the rest of the environment that relies on Active Directory authentication services.
The Potential Danger for Zerologon Exploits
This vulnerability is considered critically severe because of the elevated privileges granted by successful exploitation. Once the adversary acquires admin access, they are able to change the domain controller password, allowing them unfettered access to the rest of the network.Because the Zerologon exploit can be automated, initial access can be achieved very quickly — sometimes in as little as three seconds.
Zerologon is becoming more popular with attackers after exploit code was recently added to Mimikatz. As of this publication, CrowdStrike has not seen threat actors actively exploiting this vulnerability, but the forceful language in the “Emergency Directive” from the DHS is indicative of a strong likelihood that exploitation of this vulnerability will increase.
CrowdStrike Extends Visibility for Customers
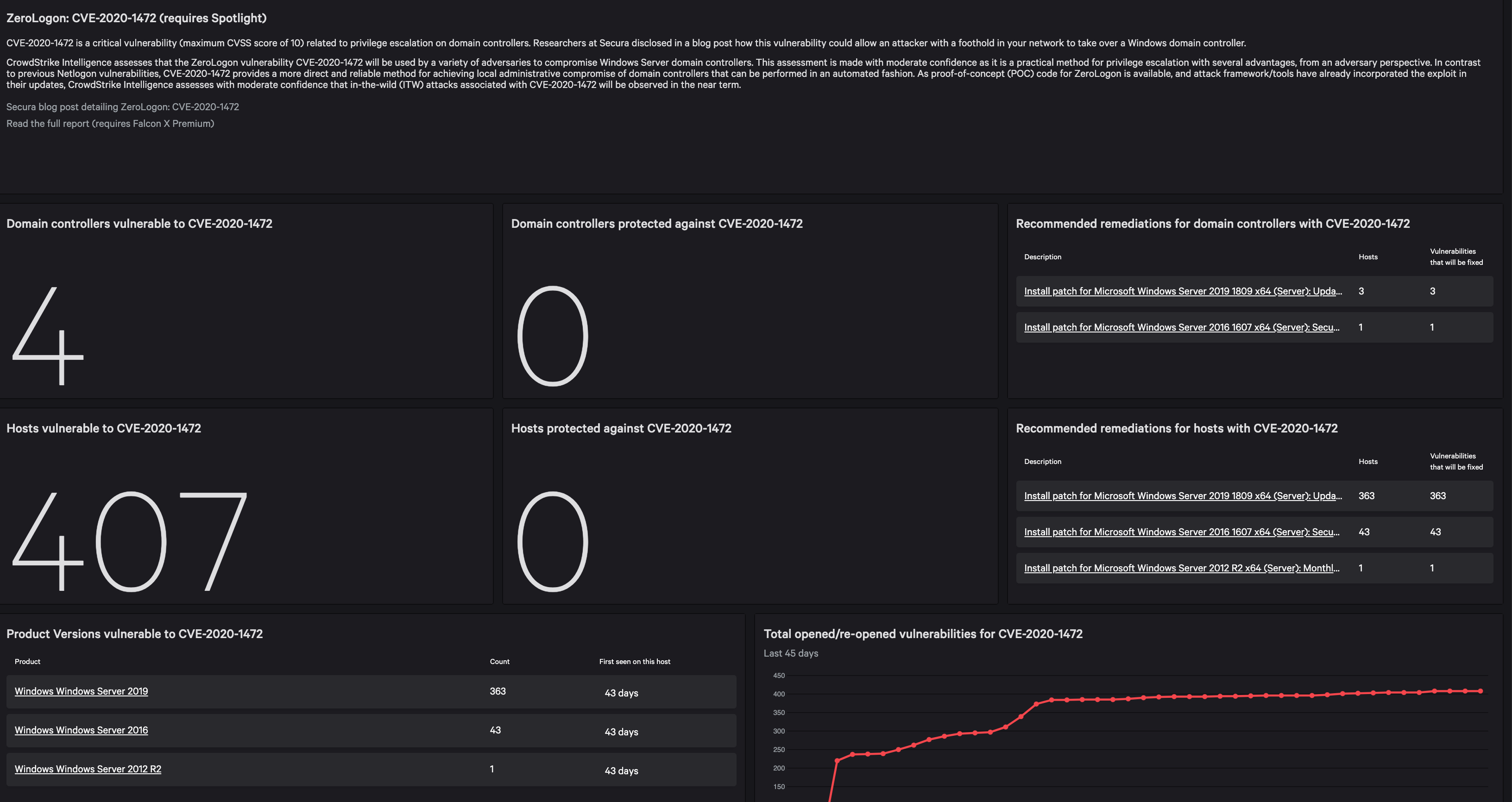
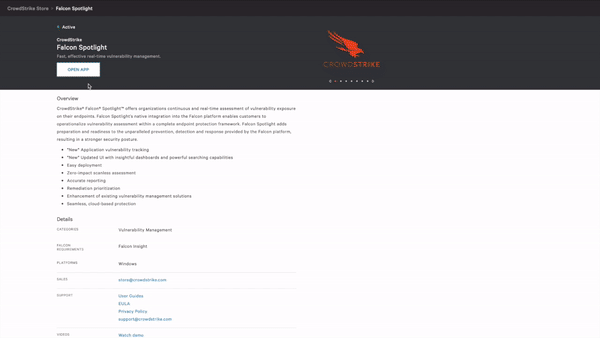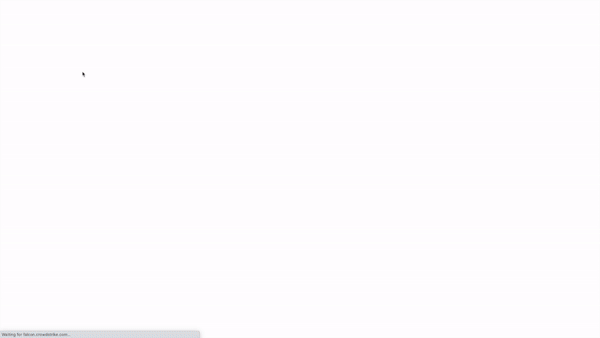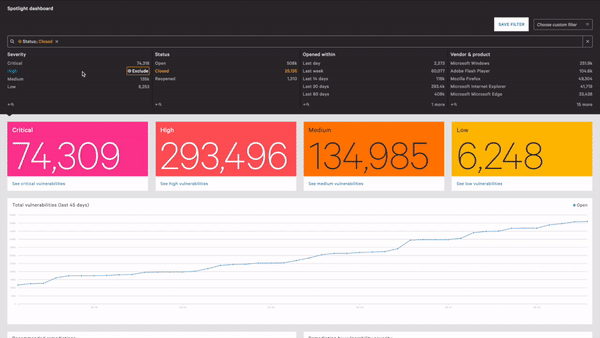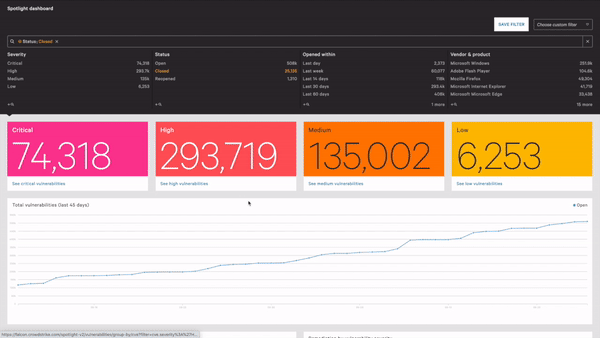
To enable customers to quickly see which servers are vulnerable to CVE-2020-1472, CrowdStrike has developed a specific dashboard for Falcon Spotlight™ customers. The dashboard also offers recommendations on which servers to remediate. By clicking into the recommendations chart, customers will find more information about vulnerable hosts.For customers that do not have Spotlight, CrowdStrike’s vulnerability management module, initiating a trial of Spotlight through the CrowdStrike Store will grant access to this dashboard: This dashboard also offers an overview of domain controllers and servers on your network, displaying how many of them are vulnerable to, or secure from, CVE-2020-1472. The dashboard includes additional charts on versions that are vulnerable and total opened/reopened vulnerabilities for CVE-2020-1472.
CrowdStrike has a new updated dashboard interface to make it easier to access module dashboards as well as to utilize preset ones. Customers can access the Zerologon dashboard by navigating to Dashboards > Preset.
To extend visibility, customers using Falcon Spotlight will have access to its comprehensive visibility and reporting capabilities that include vulnerability exposures.
Because the CrowdStrike Falcon®® platform operates in the cloud via a single lightweight agent, it is able to provide constant and immediate visibility to vulnerabilities such as CVE-2002-1472.
To see how Falcon Spotlight works in action, watch this Falcon use case video and learn how you can quickly see and resolve any vulnerabilities in your environment.
Additional Resources:
- Watch the Falcon Spotlight demo.
- Read about the Emergency Directive 20-02 from the Department of Homeland Security.
- Learn more about CrowdStrike vulnerability management by visiting the Falcon Spotlight webpage.
- Learn more about the powerful CrowdStrike Falcon® platform by visiting the product webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)