An adversary’s ability to live off the land — relying on the operating system’s built-in tooling and user-installed legitimate software rather than tooling that must be brought in — may allow them to navigate through a victim organization’s network relatively undetected. CrowdStrike Falcon® OverWatch™ threat hunters are acutely aware of adversaries' love of these living off the land binaries (LOLBins) and build their hunts accordingly. In recent months, OverWatch Elite, a part of CrowdStrike’s Falcon OverWatch managed threat hunting service, has seen an increase in the use of JScript in hands-on-keyboard intrusions.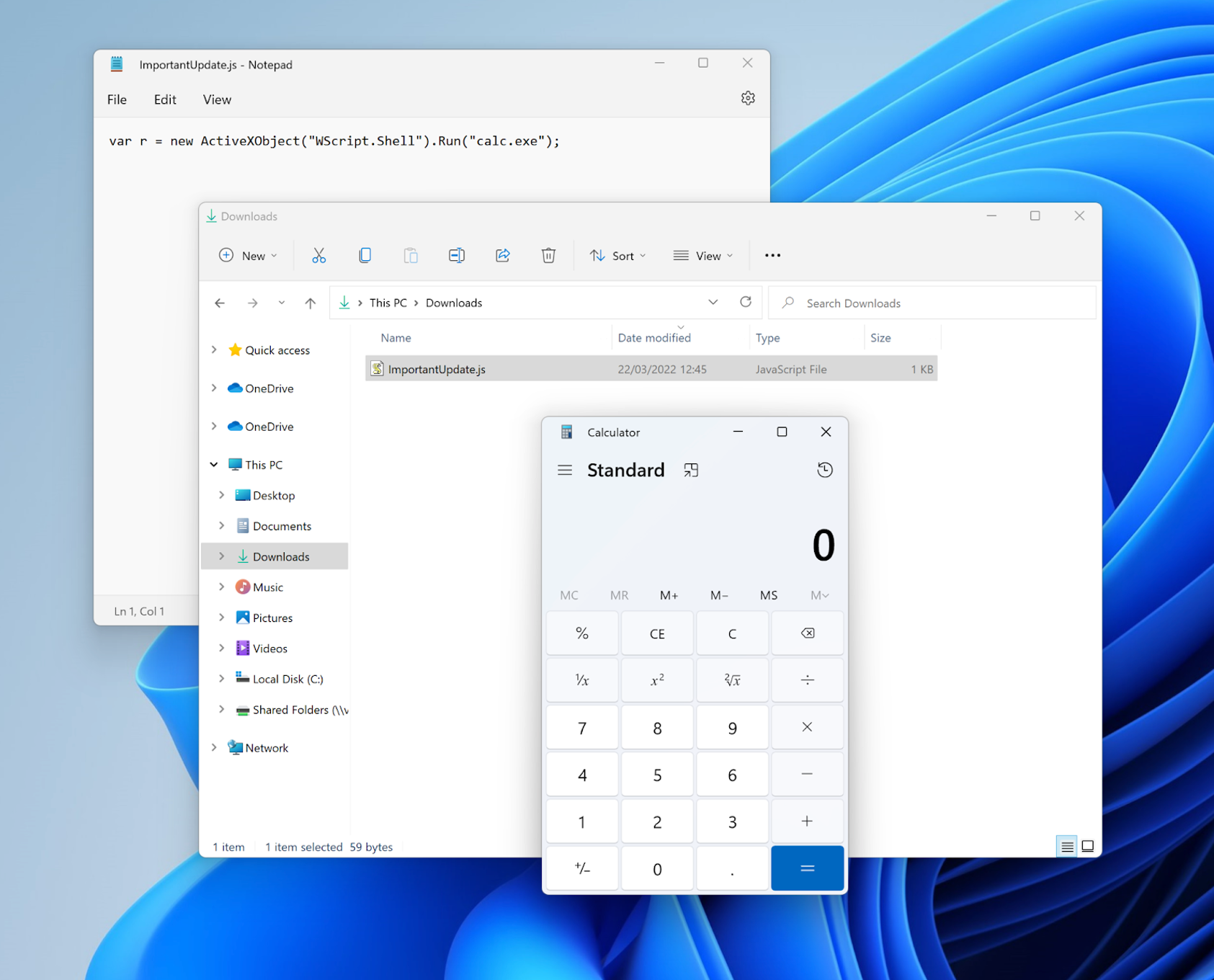 Figure 1: A proof-of-concept JScript execution that upon double clicking spawns
Figure 1: A proof-of-concept JScript execution that upon double clicking spawns
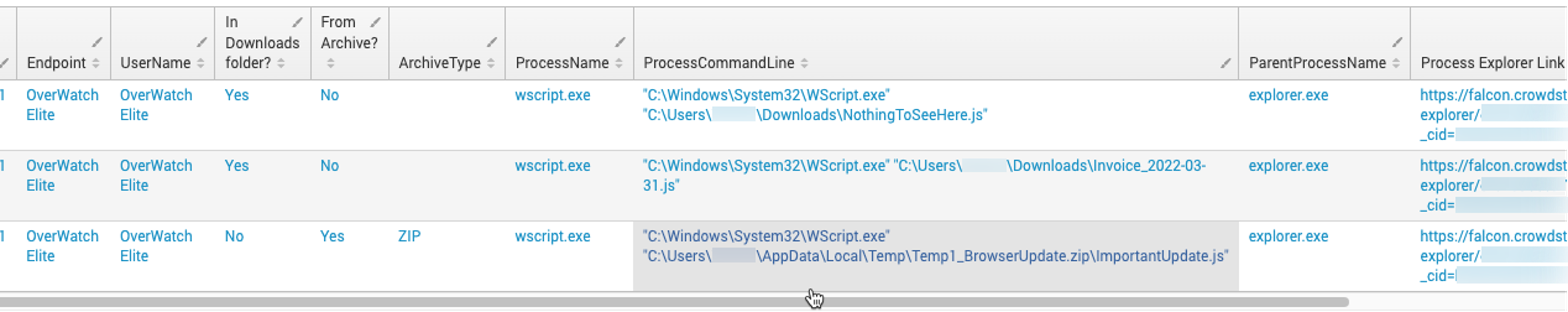 Figure 2: Sample output of the above Event Search query, surfacing suspicious JScript executions. (Click to enlarge)
A next step would be to use the Process Explorer Link to see the process execution and dive deeper into what actions were performed by the JScript file.
Figure 2: Sample output of the above Event Search query, surfacing suspicious JScript executions. (Click to enlarge)
A next step would be to use the Process Explorer Link to see the process execution and dive deeper into what actions were performed by the JScript file.
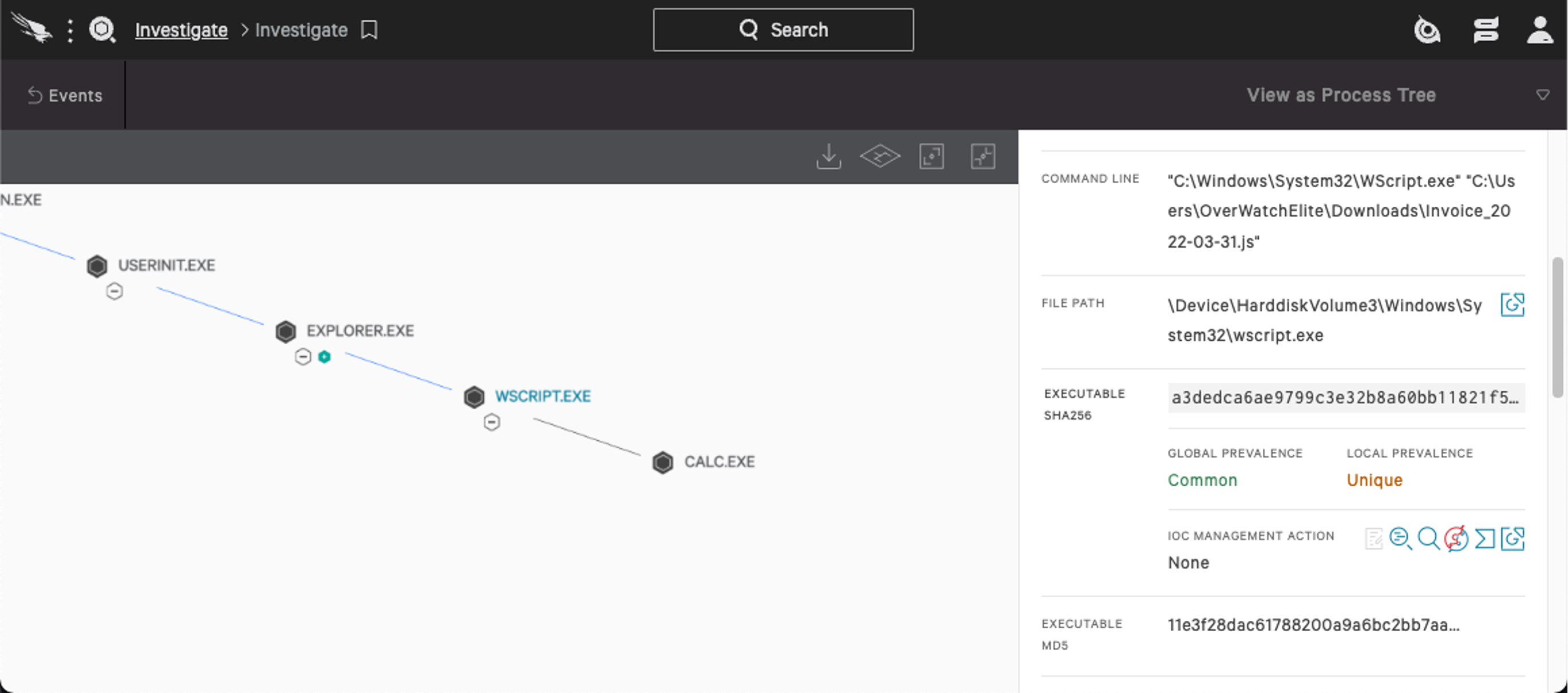 Figure 3: Falcon’s Process Explorer reveals the suspiciously-named
The above example shows the execution of
Figure 3: Falcon’s Process Explorer reveals the suspiciously-named
The above example shows the execution of
JScript vs JavaScript
JScript is a Microsoft-dialect of standard JavaScript, a scripting language that can be used in a web browser setting to add custom functionality to web pages. JScript, however, is an Active Scripting language, meaning it is more integrated into the operating system. JScript can be executed as a standalone file. It is often used to write files to disk, make registry changes, make network connections, execute commands and more.While JScript and JavaScript are distinct scripting mechanisms, they both use the same file extension:
.js. By default, double-clicking on a .js file in Windows Explorer will cause it to open the file with Windows Script Host executable wscript.exe, which will execute the code. Because wscript.exe is signed by Microsoft and is included in every Windows installation, it is often considered trusted by more traditional security solutions. Although when a .js file is downloaded from the internet an extra warning dialog is displayed prior to execution, our telemetry shows that this does not stop users from proceeding with the execution.The relative ease with which
.js files can be opened provides attackers with an attractive initial access vector, as tricking a user into executing their malicious scripts can be easy. Moreover, the limited logging that is provided by Windows Script Host (WSH) allows adversaries using malicious JScript files to evade some defense mechanisms and go unnoticed for longer.
 Figure 1: A proof-of-concept JScript execution that upon double clicking spawns
Figure 1: A proof-of-concept JScript execution that upon double clicking spawns calc.exe. (Click to enlarge)JScript as an Entry Point for Hands-on-Keyboard Activity
Unsurprisingly, OverWatch threat hunters regularly see intrusions that involve, or even start with, malicious JScript executions. In the first quarter of 2022, OverWatch identified several Fake Browser Update (FBU) infections — two of which led to the delivery of Cobalt Strike beacons followed by hands-on-keyboard activity. The actor likely used hijacked WordPress websites to host fake warnings about outdated browsers or plugins, asking the user to click a button to download the latest version. A malicious.js payload was then packed in a .zip archive, which the user was lured into opening by giving it names such as ChromeUpdate.js. This file connected to a command-and-control (C2) channel, executing various reconnaissance commands (e.g., leveraging whoami, net, nltest and cmdkey) before dropping and running a Cobalt Strike beacon. The actor was then observed using this beacon for hands-on-keyboard activity.In another instance, OverWatch observed the use of malicious
.js files in financial services-themed phishing lures. The victim organization was sent an email with a .zip file containinga file called
agreement.js. Upon opening, the JScript file reached out to an attacker-controlled domain, setting up a PowerShell implant that allowed the actor to perform further hands-on-keyboard activity. This activity included creating persistence, running various discovery commands and executing BloodHound. OverWatch quickly alerted the victim organization about the malicious activity, enabling them to contain the affected machines.
Detecting and Preventing Malicious JScript Executions in Your Environment
Because of how JScript works, there is not a straightforward way to detect malicious executions. While JScript is considered a legacy technology, it is still relied upon by a vast array of software and admin automation solutions. This can make distinguishing benign behavior from potentially malicious behavior challenging. As seen in the examples above, to abuse JScript for initial access means, the attacker need only convince a user to open a malicious.js file, which is often provided to the user in an archive file. One approach for hunting in your environment for this malicious needle in your environment’s haystack is to hunt for JScript executions that originate from a user’s download folder or temporary archive locations (e.g., ZIP, RAR or 7Zip files).In the CrowdStrike Falcon®® platform’s Event Search function, the following query will surface such executions:
event_simpleName=ProcessRollup2 FileName IN ("cscript.exe", "wscript.exe")
| search CommandLine = "*.js*" (CommandLine="*\\downloads\\*" OR (CommandLine="*\\Appdata\\Local\\Temp\\*" AND (CommandLine="*.zip\\*" OR CommandLine="*\\7z*" OR CommandLine="*\\Rar*")))
| rex field=CommandLine "(?i)(?<ArchiveType>\.zip\\\|\\\7z|\\\Rar)"
| eval ArchiveType=case(ArchiveType=".zip\\", "ZIP", ArchiveType="\\7z", "7Z", ArchiveType="\\Rar", "RAR")
| eval isFromArchive=if(ArchiveType!="","Yes", "No")
| eval isInDownloads=if(match(CommandLine, ".*\\\Downloads\\\.*"),"Yes", "No")
| eval ProcExplorer="https://falcon.crowdstrike.com/investigate/process-explorer.html" .aid. ".html" . TargetProcessId_decimal . "?_cid=" . cid
| convert ctime(_time)
| table _time aid ComputerName UserName isInDownloads isFromArchive ArchiveType FileName CommandLine ParentBaseFileName ProcExplorer
| sort + _time
| rename _time as Time, aid as "Falcon AID", ComputerName as Endpoint, isInDownloads as "In Downloads folder?", isFromArchive as "From Archive?", FileName as ProcessName, CommandLine as ProcessCommandLine, ParentBaseFileName as ParentProcessName, ProcExplorer as "Process Explorer Link" Figure 2: Sample output of the above Event Search query, surfacing suspicious JScript executions. (Click to enlarge)
Figure 2: Sample output of the above Event Search query, surfacing suspicious JScript executions. (Click to enlarge) Figure 3: Falcon’s Process Explorer reveals the suspiciously-named
Figure 3: Falcon’s Process Explorer reveals the suspiciously-named invoice_2022-03-21.js spawned calc.exe. (Click to enlarge)calc.exe, which may be considered unusual in a given environment. This would provide for further hunting opportunities, such as analyzing unusual children spawned by wscript.exe.If the given hunting query produces too many results, it is possible to narrow the search further — for example, by limiting it to
wscript.exe executions that involve spawning new processes, writing certain file types to disk, or manipulating sensitive registry locations.
From a prevention perspective, there are a few things that can be done. A key weakness in how JScript is set up in Windows is that double clicking a .js file quickly leads to execution. Removing the file association of .js files with wscript.exe may reduce the chances of success. Without the file association, a user would have to use the command line prompt to execute the file. Thus, an unsuspecting user double clicking a link in a phish would not result in a successful phish. Further, partially disabling JScript could reduce the attack surface. Microsoft also offers an option to completely disable Windows Script Host (although in most corporate environments this would not be a feasible option).
The Value of OverWatch Elite
Hunting for malicious.js executions can prove difficult due to high data volumes, legitimate use of JScript files and the variety of ways in which attackers can abuse JScript. To effectively defend against this requires deep knowledge of your environment, insights as to how attackers operate and experience with regards to detecting follow-on behavior. Managing this and other day-to-day responsibilities can easily overwhelm an in-house security team.OverWatch’s preeminent managed threat hunting service protects customer environments on a 24/7/365 basis. OverWatch’s primary mission is to pinpoint malicious activities at the earliest possible stage, providing customers with timely, high-fidelity and, most importantly, actionable notifications and context that inform a swift and decisive response. OverWatch Elite builds on the 24/7/365 threat hunting operations provided as a part of OverWatch standard and includes additional services, such as: 60-minute call escalation for critical threats, quarterly threat briefings, tailored threat hunting and more. OverWatch Elite customers are also invited to a private Slack channel where they can reach an OverWatch Elite analyst to respond with speed and confidence. For more information, please visit the OverWatch Elite page on CrowdStrike’s website.
Additional Resources
- Read the 2021 Threat Hunting Report blog or download the report now.
- Learn more about Falcon OverWatch’s proactive managed threat hunting.
- Discover the power of tailored threat hunting OverWatch Elite provides customers in this blog post.
- Watch how Falcon OverWatch proactively hunts for threats in your environment.
- Read more about how part-time threat hunting is simply not enough in this blog post.
- Learn more about the CrowdStrike Falcon®® platform.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)



















































