Quadrant Knowledge Solutions Names CrowdStrike a Leader in the 2022 SPARK Matrix for Digital Threat Intelligence Management

“CrowdStrike is capable of catering to the diverse customer needs across industry verticals, with its comprehensive capabilities, compelling customer references, comprehensive roadmap and vision, cloud-native platform, and product suite with high scalability, have received strong ratings across technology excellence and customer impact.” – Quadrant Knowledge Solutions: 2022 SPARK MatrixTM for Digital Threat Intelligence Management
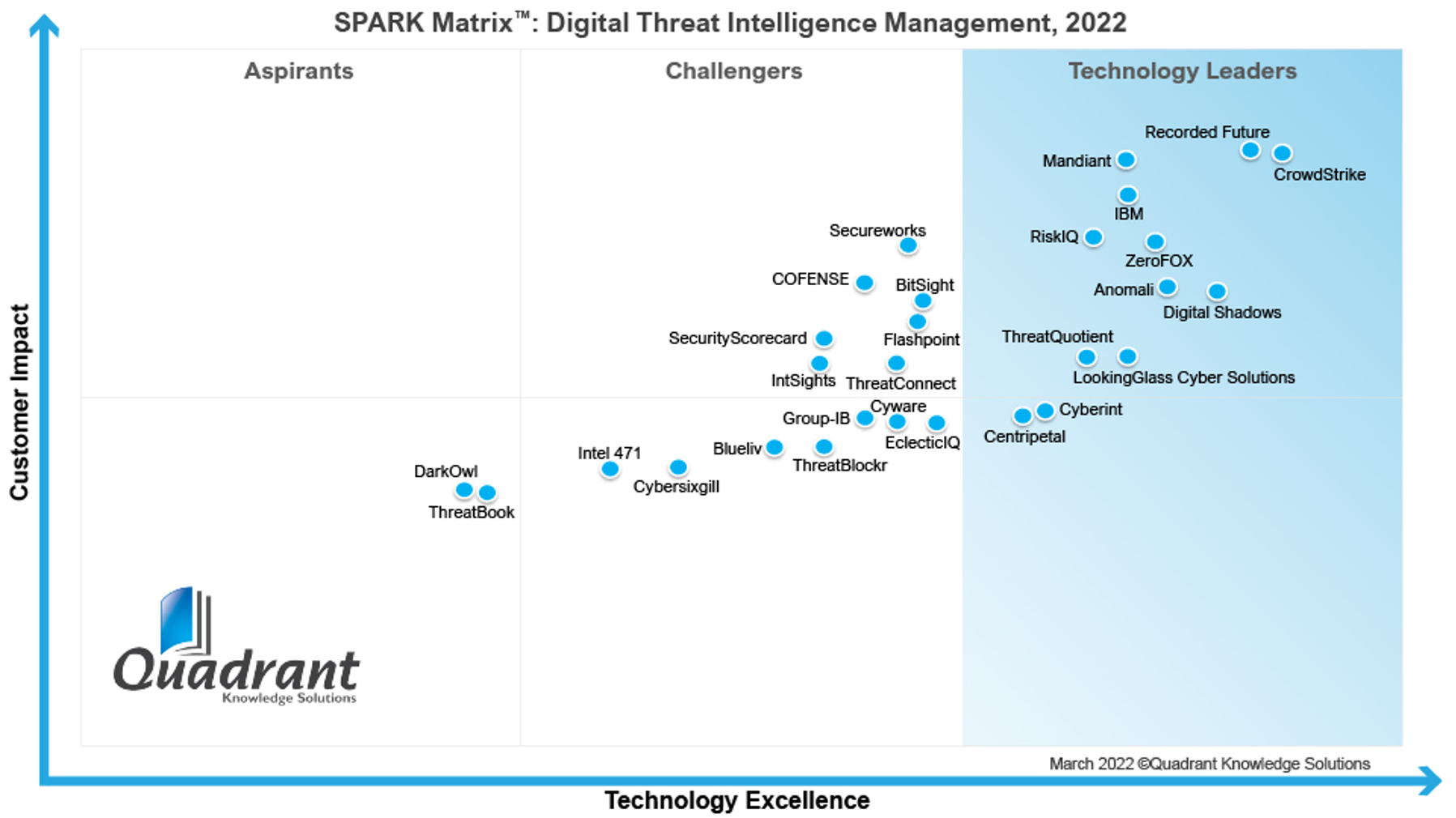
We are excited to announce Quadrant Knowledge Solutions has named CrowdStrike as a 2022 technology leader in the SPARK Matrix analysis of the global Digital Threat Intelligence Management market. Among all 28 vendors in the report, CrowdStrike received the highest score in the Technology Excellence category.
The SPARK Matrix evaluates top vendors in the Digital Threat Intelligence Management space on a variety of criteria and groups them into Leaders, Challengers and Aspirants. The criteria are broken down into two categories:
- Technical Excellence: Sophistication of Technology, Competitive Differentiation Strategy, Application Diversity, Scalability, Integration & Interoperability, and Vision & Roadmap
- Customer Impact: Product Strategy & Performance, Market Presence, Proven Record, Ease of Deployment & Use, Customer Service Excellence and Unique Value Proposition
How CrowdStrike Falcon® Intelligence Stands Apart
The SPARK Matrix analysis takes a deep look into the 28 most significant threat intelligence providers. This broad set of vendors illustrates the diversity of the threat intelligence market and the many use cases customers demand — including dark web monitoring, intelligence automation, machine-readable intelligence, finished intelligence, threat research and threat intelligence platforms.
CrowdStrike joins only a few select vendors in this report that provide a comprehensive solution to address all of these use cases. Our customers benefit from access to intelligence using a single workflow with the ability to pivot into intelligence across all use cases — leading to smarter, faster decision making.
You may know CrowdStrike as a leader in cloud-delivered protection of endpoints, cloud workloads, identity and data, but you may not know the full extent of how our offerings differ from those of pure-play threat intelligence companies. Here, we take a closer look at the capabilities that set CrowdStrike’s technology apart.
Raw Intelligence Collection to Bolster Defense
CrowdStrike’s raw intelligence collection strategy is a critical differentiator. Each vendor’s collection plan forms the foundation that determines the intelligence solutions they can deliver. If a collection plan is too narrow — for example, if it only pulls data from the dark web — it will only address a limited number of customer use cases. If it only collects low-fidelity data, such as publicly available information, the resulting intelligence will be similar across vendors because open-source data is the easiest to obtain. (This isn’t to say the data isn’t valuable, or there aren’t valuable solutions built in these areas.)
We can deliver across multiple use cases and provide unique intelligence due to our comprehensive collection strategy. This starts with the trillions of events per week collected by the CrowdStrike Security Cloud, which powers the protection of millions of endpoints across the globe and provides visibility into real-time and zero-day attacks. In addition, CrowdStrike Intelligence collects raw intelligence from several other sources including:
- CrowdStrike Services engagements for incident response and compromise assessments, which drive visibility into adversary activity in victims across the globe
- Open-source intelligence, which is collected in dozens of languages using linguistically capable collectors and analysts to ensure proper comprehension and analysis of the collected material
- Billions of objects collected from the deep and dark webs, criminal forums and markets, and social media and messaging apps
- Processing millions of malware samples per day that are interrogated for actionable information such as command and control, persistence, campaign identification and other indicators, which are instantly published to our customers
- Maintaining honeypots across the internet, which provide visibility into threats propagating via remote exploitation as well as early warning for things that may affect customers
- Operating freely available sandbox technology, which is utilized by tens of thousands of security personnel and researchers
- Maintaining a special collection of data that enables visibility into botnet command and control payloads, spam email and distributed denial of service (DDoS) activity
This comprehensive collection strategy, with the Falcon platform at its core, underscores CrowdStrike’s ability to collect data that no one else can, resulting in threat intelligence that no other vendor can provide.
An Adversary-Focused Approach to Security
Behind every attack is a human being with motivation and intent. As pioneers in actor profiling and attribution, CrowdStrike uses an adversary-focused approach to threat intelligence. We track more than 180 nation-state, cybercrime and hacktivism adversaries to expose their activities and tradecraft and then enable customers to take proactive steps to protect their organization.
CrowdStrike Falcon® Intelligence provides information on the malware adversaries use, vulnerabilities they exploit, tactics for accessing systems and indicators of compromise (IOCs) that identify them. An adversary-focused approach shrinks the problem set for you to manage. By filtering adversaries to those most likely to target your business (e.g., by region or business sector) you can focus on the most likely attacks, expose attacker tradecraft, degrade their ability to attack, increase the cost to the adversary and deploy your resources more effectively.
Threat Intelligence for Everyone
“Threat intelligence for everyone” was one of our core principles when going to market with the CrowdStrike Falcon Intelligence solution. Threat intelligence has different meanings to different organizations, typically based on the size and skills of their security team. For many organizations early in their intelligence journey, “threat intelligence” may simply describe IOCs to block or open-source news alerts when a new cyberattack happens. As organizations mature, intelligence morphs to include enriched context for detections, help in hunting and investigating threats, then dark web monitoring and malware sandboxing. As intelligence becomes more strategic, it may mean access to finished intelligence or threat research.
It is critical to find a vendor that meets your definition of intelligence, supports where you are, and provides room for your team to grow. Further, it should challenge you to take the next step into a new use case so you can better protect your business and gain an advantage on today’s sophisticated cyberattacks. CrowdStrike Falcon Intelligence threat intelligence solutions are designed to meet you where you are in your threat intelligence journey. Thousands of our customers are implementing intelligence for the first time, and many of the most advanced Global 2000 and government entities rely on the superior collection, tradecraft and analysis of CrowdStrike Falcon Intelligence.
If you are a CrowdStrike Falcon customer, or would like to become one, CrowdStrike Falcon Intelligence threat intelligence is built directly into the platform, supporting your daily workflow by providing additional detection context and defensive strategies at your fingertips. If you are not a Falcon platform customer, our CrowdStrike Falcon Intelligence solutions are available separately, cloud-delivered and operational on Day One.
We believe we met our goal to provide “intelligence for everyone.” For the first time, all organizations, regardless of size or expertise, can easily operationalize intelligence within the security operations center (SOC), gain visibility into the cybercriminal underground to protect their brand and executives, and receive best-of-breed intelligence reporting and technical analysis backed by a dedicated team of intelligence professionals.
Defend Against Threats with CrowdStrike Falcon Intelligence
CrowdStrike Falcon Intelligence solutions include:
- CrowdStrike Falcon® Intelligence: Enriches the events and incidents detected by the CrowdStrike Falcon® platform, automating intelligence so security operations teams can make better, faster decisions
- CrowdStrike Falcon® Intelligence Recon: Provides visibility into the cybercriminal underground so customers can effectively mitigate threats to their brands, employees and sensitive data
- CrowdStrike Falcon® Intelligence Premium: Delivers world-class intelligence reporting, technical analysis, malware analysis and threat hunting capabilities; CrowdStrike Falcon Intelligence Premium enables organizations to build cyber resiliency and more effectively defend against sophisticated nation-state, eCrime and hacktivist adversaries
- CrowdStrike Falcon® Intelligence Elite: Expands your team with access to an intelligence analyst with the expertise to help you better defend against threats targeting your organization
Additional Resources
- Read the press release.
- Download the report: 2022 SPARK Matrix™ for Digital Threat Intelligence Management.
- To find out more about how to incorporate intelligence on threat actors into your security strategy, visit the CrowdStrike Falcon® Intelligence™ Threat Intelligence page.
- Read about adversaries tracked by CrowdStrike Intelligence in 2021 in the CrowdStrike 2022 Global Threat Report.
- Learn more about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.
- Get a full-featured free trial of CrowdStrike Prevent and CrowdStrike Falcon Intelligence™ and learn how true next-gen AV performs against today’s most sophisticated threats.