Falcon FileVantage: New CrowdStrike File Integrity Monitoring Solution Creates Total Efficiency for SecOps

This announcement is part of the Fal.Con 2021 CrowdStrike Cybersecurity Conference, Oct. 12-14. Register now for free to learn all about our other exciting new products and partnerships!
When it comes to SecOps staff defending an organization’s base — crown jewel files, folders and registries — they’re often faced with a dilemma: IT must monitor many assets for changes, and each one of these changes, at scale, can immediately create unachievable monitoring processes within an organization. As a result, SecOps can quickly get overwhelmed with alerts and notifications and can miss risky behaviors occurring around these assets.
Regulatory authorities require many organizations to monitor these important assets and systems, but the solutions available to SecOps staff are inefficient. Unfortunately, organizations often have to cobble together a complex solution stack to make a file integrity monitoring (FIM) solution that meets their needs — but it may not provide the required visibility and can also be prohibitively expensive.
CrowdStrike’s new Falcon FileVantage addresses these challenges, going beyond simply meeting compliance requirements — this FIM solution offers central visibility and increased efficiency by reducing alert fatigue for IT teams, all delivered within the CrowdStrike Falcon®® platform. And, unlike other FIM solutions, Falcon FileVantage gives staff the ability to quickly target file change data with relevant adversary activity, offering added insights with CrowdStrike’s threat intelligence data.
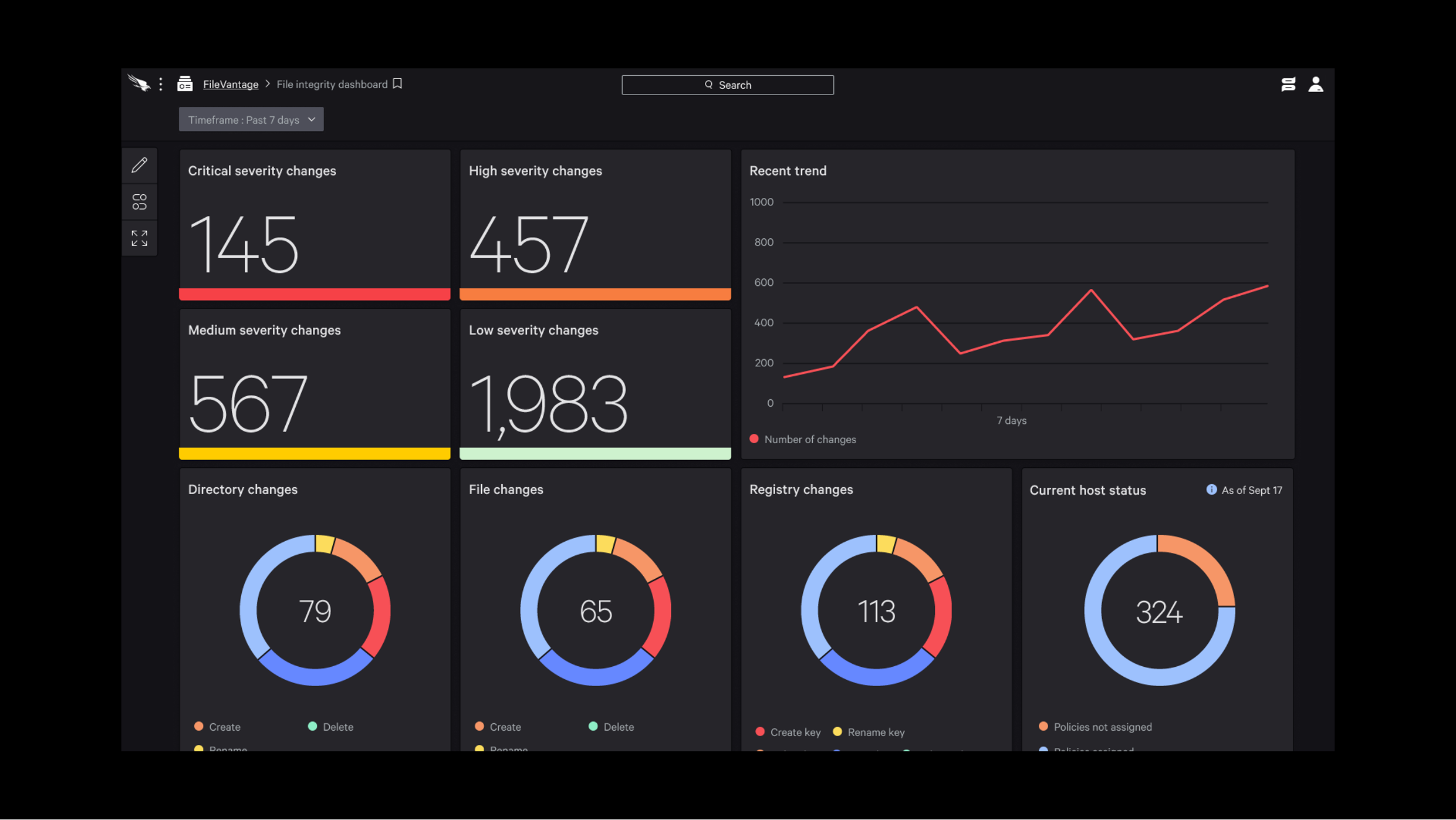
Figure 1. Falcon FileVantage offers central visibility and key insights with intuitive dashboards (Click to enlarge)
Providing Central Visibility and Increased Efficiency for SecOps
Falcon FileVantage provides real-time, comprehensive visibility for the creation, deletion and modification of all critical assets, files, registries and systems across an organization. Since many governing regulators — like the Payment Card Industry Data Security Standard (PCI DSS), National Institute of Standards and Technology (NIST), the Sarbanes-Oxley (SOX) Act of 2002, and others — require controls to monitor and prevent unauthorized access or changes to important data, it is critical for companies to have appropriate visibility into all harmful changes occurring within their environment.
Using a comprehensive set of Falcon FileVantage dashboards and valuable charts, SecOps can see everything relevant to their organization and can streamline that visibility to watch for systems with the most violations, for changes in file properties, and for many account-level and user-level behavior changes.
Added Context With Threat Intelligence Data at Your Team’s Fingertips
In addition to providing real-time visibility, Falcon FileVantage provides key context for research during or after an incident. For example, if a ransomware attack occurred within your organization, your staff can use the FileVantage console to identify which file/folder changes relating to the attack have occurred, and they can pivot into the detection directly from the FIM console. This data allows your teams to move fast, pinpointing the adversary’s activity within your environments and allowing for quick prioritization of remediation efforts around the affected files. Falcon FileVantage allows staff to quickly target file change data with any relevant adversary activity, and it relates that activity to the hash.
CrowdStrike’s threat intelligence offers groundbreaking information for security teams to stay abreast of the developments relating to threat actors and techniques, tracking over 130+ profiles relating to nation-state, eCrime and hacktivist adversaries. This threat intelligence combined with file monitoring is pivotal in creating a more secure posture.
Falcon FileVantage FIM Strengthens Your Organization’s Security Defenses
It’s time to put alert fatigue finally to rest. Give your SecOps the visibility they need to go beyond compliance — Falcon FileVantage enables them to connect the dots for risky behavior around assets and systems, with real-time monitoring and added threat intelligence context. Use Falcon FileVantage as one of your first lines of defense to protect crown jewel files and folders that matter the most to your organization. For more information about Falcon FileVantage, see the Fal.Con 2021 session File Integrity Monitoring for Falcon and read more in the press release.
Additional Resources
- Read the press release about Falcon FileVantage.
- Register for Fal.Con and watch sessions relating to SecOps.
- Request a 1:1 demo to see the Falcon platform in action.


