New CrowdStrike Falcon Fusion Features Refine Workflow Automation for CrowdStrike Customers
CrowdStrike Falcon® Fusion is a cloud-scale, extensible security orchestration, automation and response (SOAR) framework that’s natively integrated with the CrowdStrike Falcon® platform and available to CrowdStrike customers at no added cost.
From within the Falcon console, Falcon Fusion enables security operations center (SOC) analysts to define end-to-end automated workflows with ease using an intuitive UI, pre-built workflow templates and customized scripts to execute almost any action directly on the endpoint.
Two new capabilities have recently been added to Falcon Fusion to further simplify incident investigation, response and remediation: workflow scheduling and human input requesting.
The industry-leading CrowdStrike Falcon platform sets the new standard in cybersecurity. Watch this demo to see the Falcon platform in action.
Scheduled Workflows: A New Way to Trigger Automation
With Falcon Fusion, CrowdStrike users can now create workflows that execute on a defined schedule, enabling automated tasks to run regularly rather than only when a trigger event occurs. This new capability broadens the ways in which Falcon Fusion workflows can be applied to IT and security use cases.
Use Case
A large school system’s IT department wants to schedule a nightly workflow to execute a Falcon Real Time Response (RTR) script that clears browser cookies, the cache and the temp file directory across all their Windows devices in their library.
Typically, this workflow would be accomplished using a traditional security orchestration, automation and response (SOAR) or IT service management (ITSM) platform. While these tools include scheduling, they require additional configuration by the user to allow the Falcon RTR action to complete across a fleet of endpoints. This may include configuring and managing a jumpbox that can connect to each endpoint, and modifying firewall rules, service accounts and other configurations — not a trivial amount of work to do when endpoints number in the tens or hundreds of thousands or more.
Using Falcon Fusion’s Scheduled Workflows in conjunction with Falcon RTR eliminates the complexity and burden of applying actions to a large endpoint estate in a highly automated way. Users can focus on identifying the use case to schedule and writing the Falcon RTR script to complete the action, not coordinating action across endpoints.
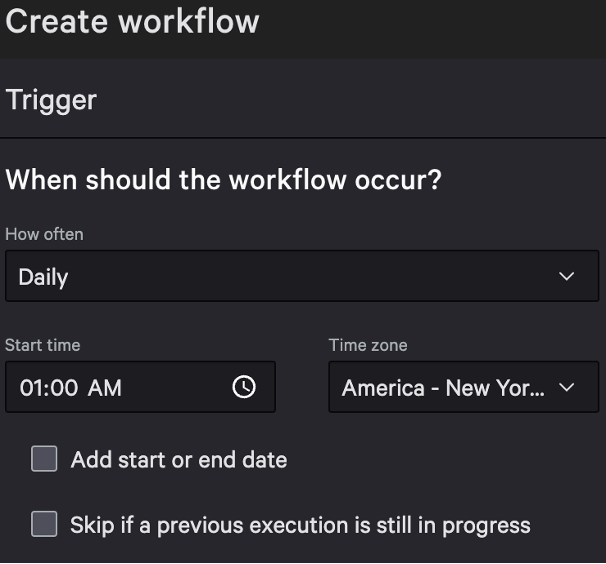
To build a workflow to solve for our use case, the user must specify when the workflow is to occur and then add the corresponding actions, as shown in Figures 1 and 2.
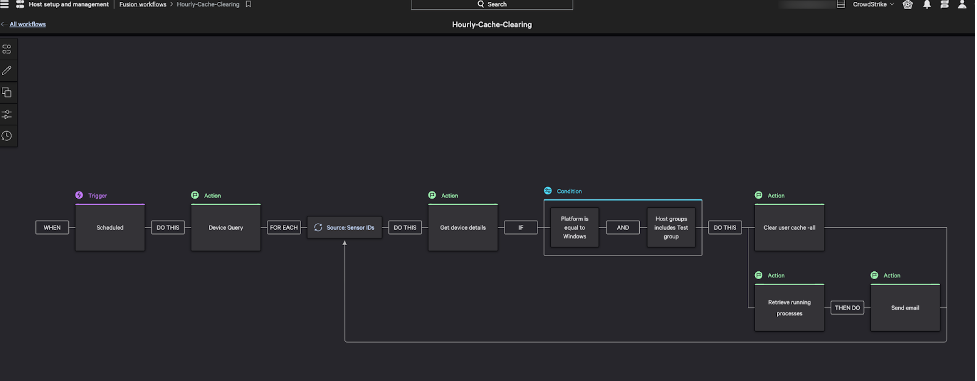
Figure 2. Falcon Fusion “Scheduled Workflows” definition for clearing browser cookies, cache and temp file directory (click to enlarge)
In this example, our intent is to run a Falcon RTR script daily at 1:00 a.m. ET across all of the devices in host group: library. Using the Device Query action, we can query for hosts in the library host group and then loop through the results of the query and execute the Falcon Custom RTR script for all Windows machines in this host group. Lastly, the Jira action will create a ticket for the IT team to review the results of the scheduled workflow, which includes a list of all of the host names the Falcon RTR script was executed on.
Other use cases in which Falcon Fusion workflows can be used with Falcon RTR scripts include:
- Sweep an environment and check if a registry key/value exists, change it if it doesn’t and is desired, or delete it if undesired
- Run a cloud-hosted executable (e.g., a patch or a software installer) on a fleet
- Run a script to make a configuration change to a fleet (e.g., change a setting that prevents a zero-day worm from spreading)
Request for Human Input: A New Action for Reviewing Workflow Execution
Many security teams are reluctant to automate their response workflows, either because of the potential negative impact on their operations as a result of false positives or a general lack of trust in automation.
Because automated response workflows can take high-impact actions that may cause service interruptions or irreversible consequences, a Falcon Fusion workflow can now include an action that pauses the workflow and requires human input (e.g., review and approval) before executing or stopping the remainder of the workflow.
This is accomplished using the new “Request Human Input” action, which allows the workflow creator to select response options, such as Approve, Decline or Escalate. There is also an option to set a timeout if there is an SLA related to the approval.
Use Case
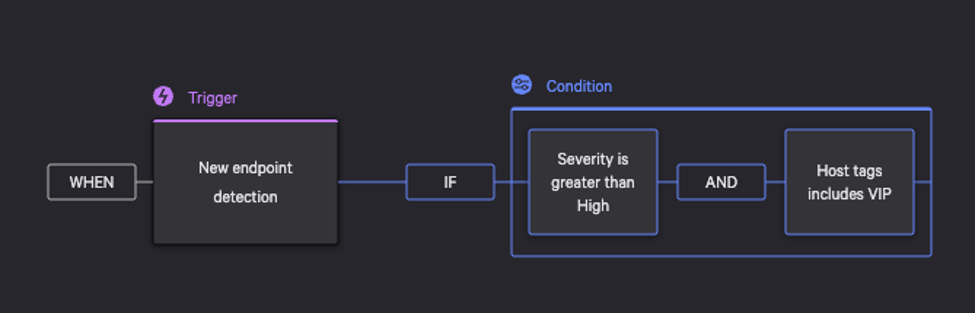
Let’s consider a use case in which a CIO has asked their organization’s security team not to automatically network-contain devices used by the executive leadership team in case a related alert may be a false positive. Because the security team wants to continue to use automation to respond to critical and high severity alerts, they decide any devices tagged “VIP” require a human approval before they are auto-contained, with a SLA of 50 minutes in accordance with what CrowdStrike refers to as the 1-10-60 rule: detect an intrusion within 1 minute, investigate within 10 minutes, and isolate or remediate the problem within 60 minutes (see Figure 3).
Using Falcon Fusion, the workflow creator can create a new workflow or modify an existing workflow by adding a condition to check if a “VIP” host tag is included (see Figure 4).
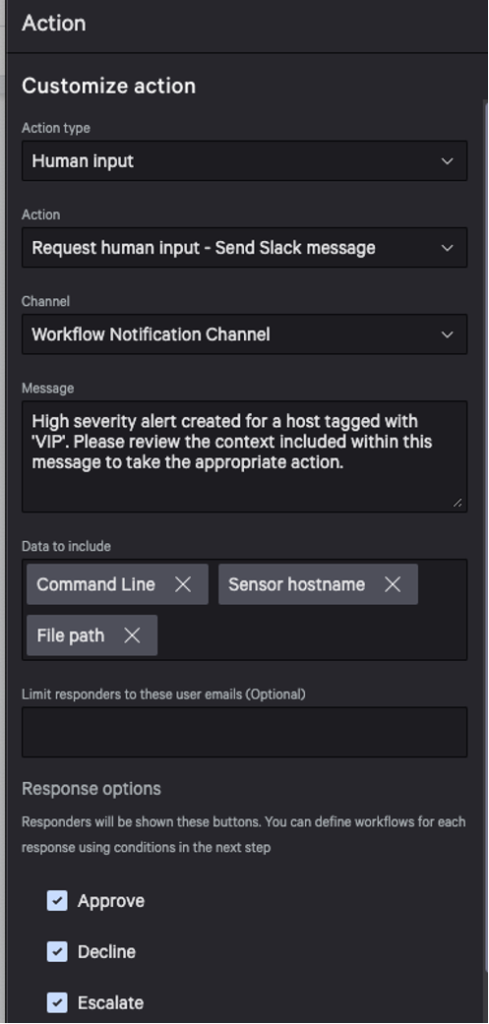
Once the condition is added, then the user can add the Request Human Input action. Within the action, the user should include the relevant context required for the approver to make a decision, such as the command line arguments, VirusTotal score, host name, file path, etc. Typically, one should include the context an analyst would gather manually in the workflow to eliminate redundant manual tasks for the analysts. For this example, we’ll use the following options: Approve, Decline, Escalate.
- If approved, the device will be contained and a comment will be added to the detection.
- If declined, a comment will be added to the detection.
- If escalated, then the approver is indicating they are unsure and escalating to Tier 2 support to make the decision. The recipient of the notification will have a shorter SLA time and only two options: Approve or Decline.
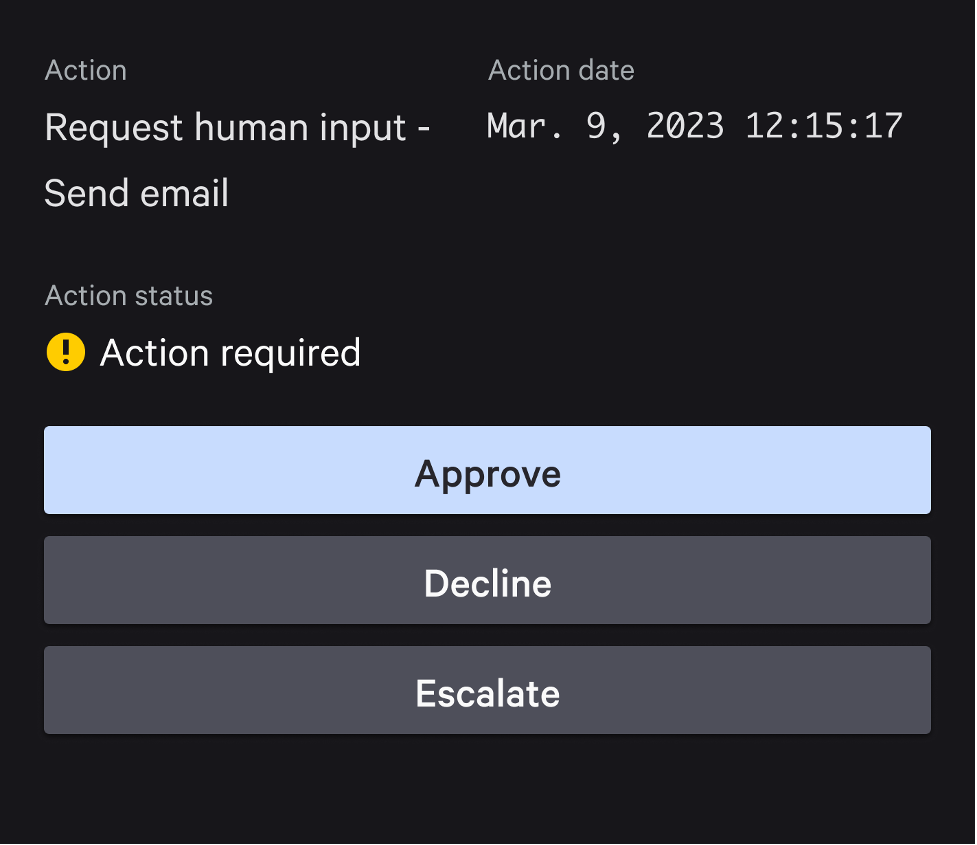
Once the workflow has been created and turned on, the workflow will execute once the conditions are met. Upon execution, the approvers will get a notification (in this example, in Slack), and the notification will include context and a link to respond (see Figure 5).
The user can then select Approve, Decline or Escalate, and the response will be stored in the Execution log.
Learn More
To learn more about using Falcon Fusion with your Falcon platform deployment, download the Falcon Fusion data sheet. If you’re not yet a CrowdStrike customer, request a free trial.
Additional Resources
- Learn more about the Falcon Fusion integrated cloud-scale framework.
- Get technical details about Falcon Fusion in the data sheet.
- Learn how the powerful CrowdStrike Falcon platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon Prevent and see for yourself how true next-gen AV performs against today’s most sophisticated threats.