Microsoft has released 55 security patches for its June 2022 Patch Tuesday rollout. Three of the 55 CVEs addressed are rated Critical severity, with CVE-2022-30136 having the highest CVSS score of 9.8. In this blog, the CrowdStrike Falcon® Spotlight™ team offers an analysis of this month’s vulnerabilities, as well as insights into the vulnerabilities and patches affecting Microsoft products in the first half of this year. We highlight the CVEs in this month’s update that are most severe and recommend how to prioritize patching. Additionally, we discuss a much-anticipated patch for the Follina vulnerability (CVE-2022-30190).
Official Fix for Windows MSDT Follina Zero-Day Vulnerability
Microsoft’s June 2022 patch update includes a fix for the widely exploited Windows Microsoft Diagnostic Tool (MSDT) zero-day vulnerability known as Follina. Last month, this Windows zero-day vulnerability was discovered in attacks that executed malicious PowerShell commands via MSDT. When it was first detected, the vulnerability bypassed all security protections, including Microsoft Office's Protected View, and executed the PowerShell scripts when a user simply opened a Word document. A brief timeline on this vulnerability:
- On May 27, 2022, a remote code execution vulnerability was reported affecting MSDT
- The vulnerability, which is classified as a zero-day, can be invoked via weaponized Microsoft Office documents, Rich Text Format (RTF) files, XML files and HTML files
- The CrowdStrike Falcon® platform protects customers from current Follina exploitation attempts using behavior-based indicators of attack (IOAs)
| Rank | CVSS Score | CVE | Description |
| Critical | 7.8 | CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability |
CrowdStrike recommends that you monitor your environment to see if it is affected by this vulnerability and apply the fix offered.
June 2022 Risk Analysis
The top three attack types — remote code execution (RCE), elevation of privilege and information disclosure — continue to dominate, with denial of service following at almost 6%.
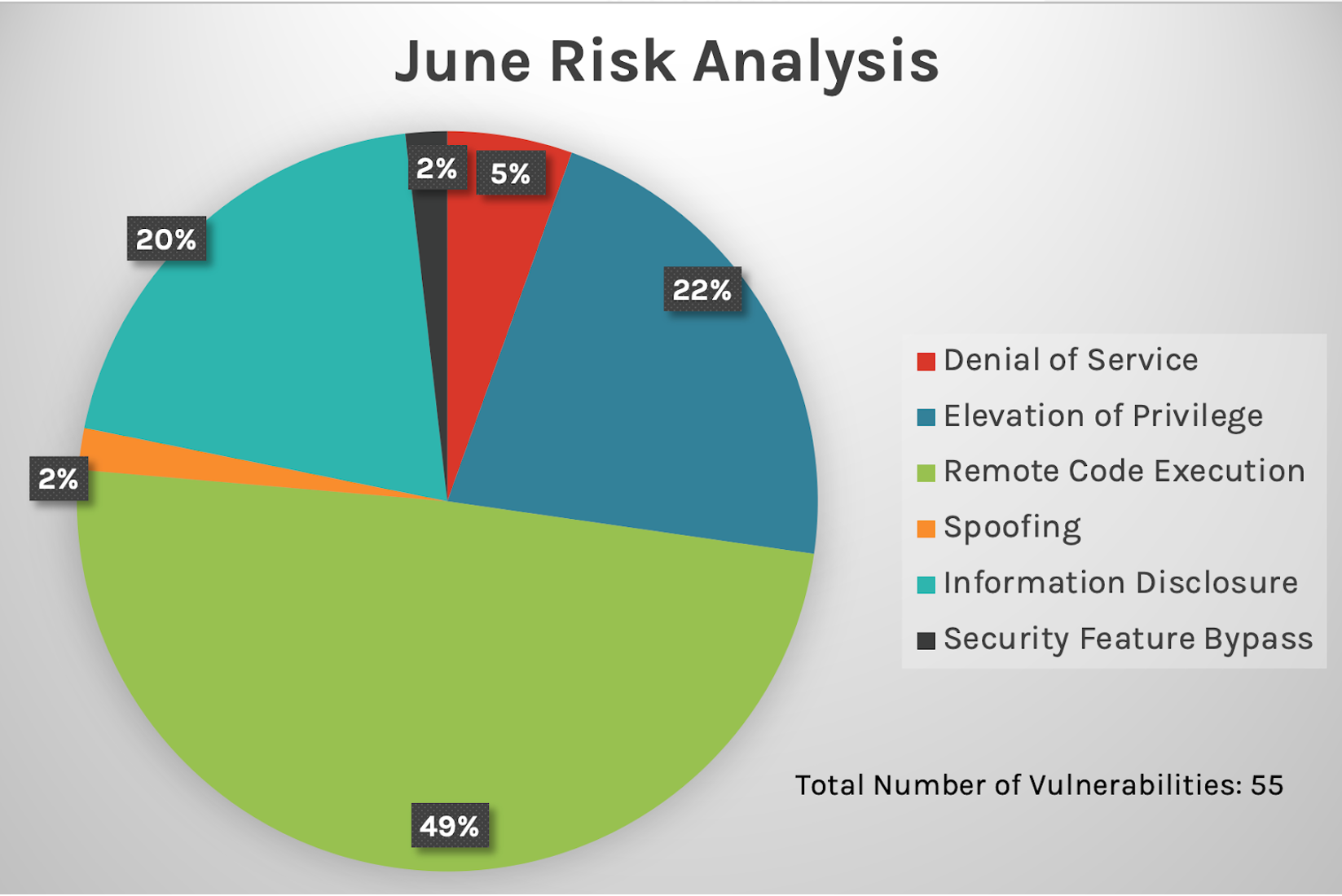 Figure 1. Breakdown of June 2022 Patch Tuesday attack types
Figure 1. Breakdown of June 2022 Patch Tuesday attack typesThe affected product families, however, differ greatly from last month. In May 2022, Developer Tools — including Visual Studio Code, Visual Studio 2019 and 2022, and Microsoft .NET Framework — saw a significant decrease in vulnerabilities patched. Microsoft Windows received the most patches this month, with Extended Security Updates (ESU) following close behind. A single Microsoft Exchange update was also included in this month’s patching list.
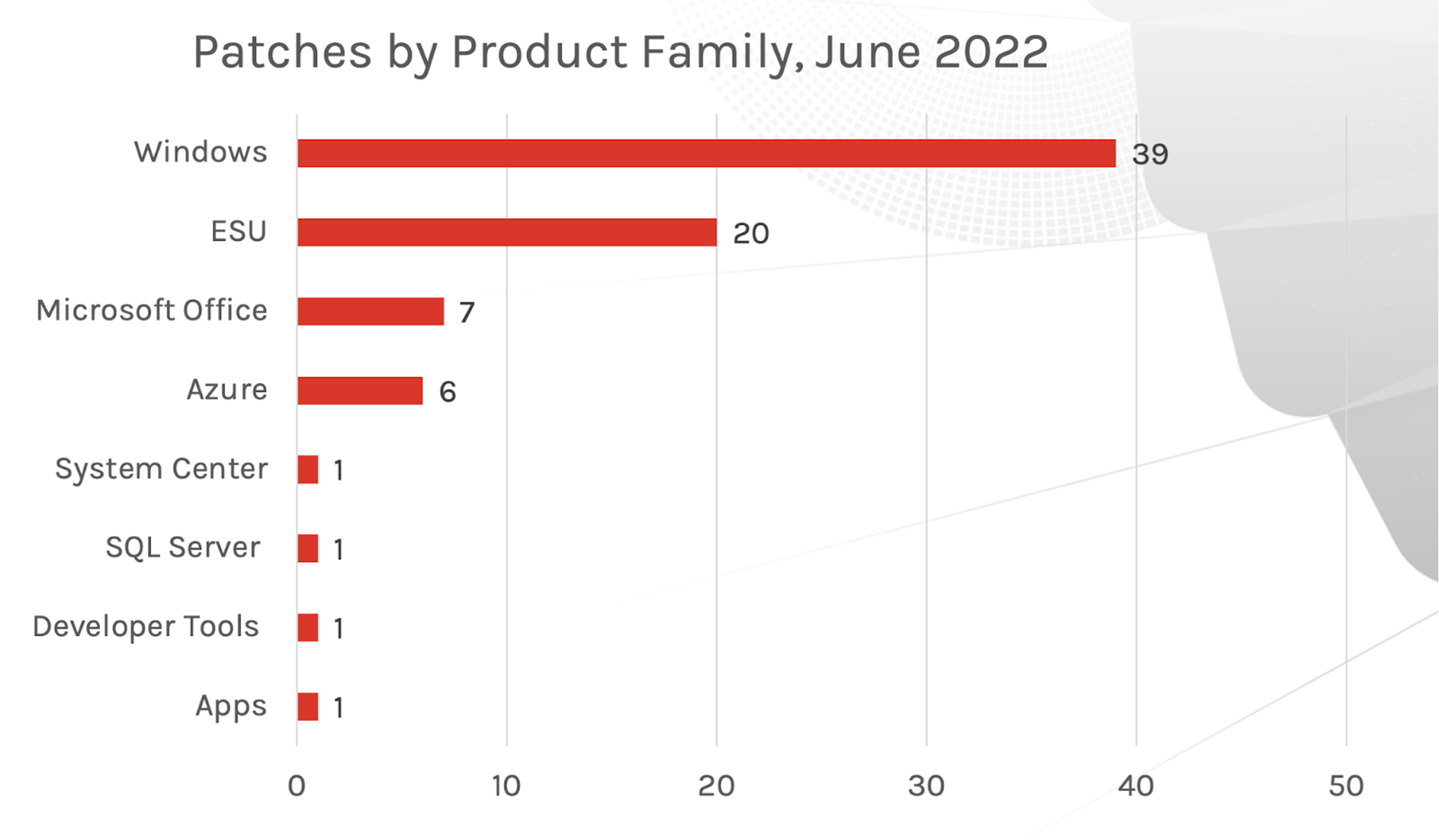 Figure 2. Breakdown of June 2022 Patch Tuesday affected product families
Figure 2. Breakdown of June 2022 Patch Tuesday affected product familiesCritical Vulnerabilities Affecting LDAP, NFS and Hyper-V
Three vulnerabilities ranked as Critical received patches this month. Affected products are Windows Lightweight Directory Access Protocol (LDAP), Windows Network File System (NFS) and Windows Hyper-V. Let’s review each of these vulnerabilities and how they could affect an organization’s environment.
CVE-2022-30136: This Windows Network File System remote code execution vulnerability with a CVSS of 9.8 is very similar to CVE-2022-26937, a Network File System (NFS) CVE patched last month. This vulnerability could allow a remote attacker to execute privileged code on affected systems running NFS. On the surface, the only difference between the patches is that this month’s update fixes a flaw in NFSV4.1, whereas the flaws found last month only affected versions NSFV2.0 and NSFV3.0. Enterprises running NFS should prioritize testing and deploying this fix.
CVE-2022-30163: This Windows Hyper-V remote code execution vulnerability with a CVSS of 8.5 could allow a user on a Hyper-V guest to run their code on the underlying Hyper-V host OS. The update doesn’t list the privileges the attacker’s code would run at, but any guest-to-host escape should be taken seriously. Microsoft notes that attack complexity is high since an attacker would need to win a race condition.
CVE-2022-30139: This Windows Lightweight Directory Access Protocol (LDAP) remote code execution vulnerability with a CVSS of 7.5 is one of the seven LDAP vulnerabilities fixed this month. The volume of CVEs in LDAP over the last couple of months could indicate a broad attack surface in the component.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2022-30136 | Windows Network File System Remote Code Execution Vulnerability |
| Critical | 8.5 | CVE-2022-30163 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2022-30139 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
Additional Windows LDAP Remote Code Execution Bugs
There are seven RCE vulnerabilities affecting Windows LDAP patched this month, a decrease from the 10 LDAP patches last month. One is rated as Critical (covered in the previous section), and six are ranked as Important. The most severe of these received a CVSS score of 8.8 but would require the MaxReceiveBuffer LDAP policy to be set to a value higher than the default value.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-30161 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-30153 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.1 | CVE-2022-30141 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 7.5 | CVE-2022-30143 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 7.5 | CVE-2022-30146 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 7.5 | CVE-2022-30149 | Windows LDAP Remote Code Execution Vulnerability |
Two Important Kerberos Vulnerabilities
Two vulnerabilities involving Windows Kerberos and Kerberos AppContainer received CVSS scores of 8.8 and 8.4, respectively, and a rank of Important. Nonetheless, these vulnerabilities are relevant to any organization using the affected products.
CVE-2022-30164: Kerberos AppContainer security feature bypass vulnerability. If exploited, an attacker could bypass the Kerberos service ticketing feature that performs user access control checks. According to Microsoft, no user interaction is required, and attack complexity is rated Low. For more details, click here.
CVE-2022-30165: Windows Kerberos elevation of privilege vulnerability. Ranked as Important with a CVSS of 8.8, this bug in Kerberos affects servers with both Credential Security Service Provider (CredSSP) and Remote Credential Guard (RCG) installed. An attacker could elevate privileges then spoof the Kerberos logon process when an RCG connection is made via CredSSP. According to Microsoft, no user interaction is required and attack complexity is rated Low. For more details, click here.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-30165 | Windows Kerberos Elevation of Privilege Vulnerability |
| Important | 8.4 | CVE-2022-30164 | Kerberos AppContainer Security Feature Bypass Vulnerability |
Falcon Spotlight provides the visibility SecOps teams need to quickly identify which vulnerabilities are prevalent in your organization’s environment. When it comes to additional detection capabilities, Falcon Spotlight is completely integrated within the CrowdStrike Falcon® platform that offers a host of other capabilities, including the ability to take swift and instantaneous action by isolating potentially compromised hosts from exploited vulnerabilities. Additionally, the Falcon platform mitigates the risk from vulnerabilities that can not be patched rapidly by detecting and automatically preventing exploitation attempts and post-exploitation activity.
H1 2022 Vulnerability Recap
There have been 461 CVEs affecting Microsoft products as of June 14, 2022. While this is markedly lower than the 612 vulnerabilities reported in H1 2021, what has remained consistent is the persistence of adversaries working to take advantage of vulnerabilities across myriad products. Out-of-band (OOB) patching and active exploitation continues to occur (such as Follina and Log4j), meaning a review of Patch Tuesday vulnerabilities should be a key component in your vulnerability management program.
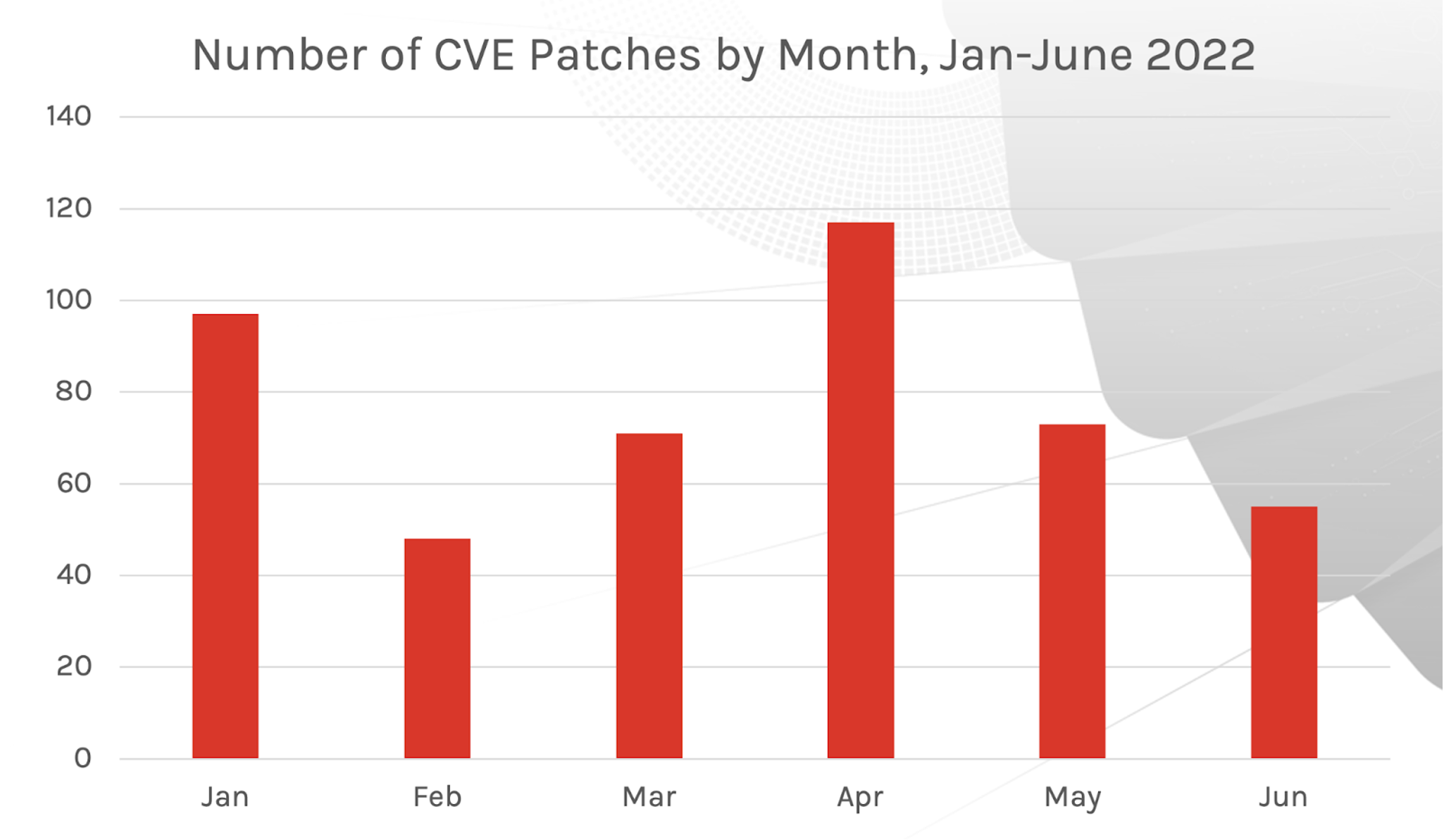 Figure 3. Number of CVEs that Microsoft released each month, January-June 2022
Figure 3. Number of CVEs that Microsoft released each month, January-June 2022While April saw the greatest number of vulnerabilities patched — it was the only month to exceed 100 in H1 2022 — the quantity of patches in a given month does not correlate with higher risk or indicate a higher rate of exploitation. It also does not signify an increase in eCriminal behavior for a particular product or service. In the latest Verizon Data Breach Investigations (DBIR) Report, vulnerability exploit analysis showed that organizations running a robust vulnerability management program were able to patch or remediate vulnerabilities and had no discernable security issues relating to vulnerabilities. However, organizations that did not regularly review vulnerability within their lifecycle ended up with more incidents, especially around internet-facing hosts.
What does all this mean for you in 2022? We have a few insights when it comes to maintaining your vulnerability management program:
- Adversaries are persistent and consistent; they have all the time in the world and will continue to look for access in whatever way possible. Remember, a small amount of access is still access.
- Vulnerabilities do not exist in a vacuum; assets, hosts and entities are all connected to each other in an environment, and many of them to the internet as well. It’s increasingly apparent that holistic visibility of all assets and how they relate to each other should be monitored in conjunction with your vulnerability management program. Security hygiene and attack surface visibility can offer valuable insights into how you prioritize and patch vulnerabilities within your environment.
- Patch Tuesday matters! If any part of your environment uses Microsoft products, or if other vendors conduct patching cycles, it’s important to review the patches released every month and take time to apply fixes or updates to products wherever applicable.
When It Comes to Vulnerabilities, It’s Not Just About Quantity
Adversaries will never go away. They will use any and every opportunity to take advantage of a flaw, weakness or vulnerability. If you have the big “holes” fixed in your organization’s environment, that’s a great start, but to stay on top of your vulnerability lifecycle program, SecOps staff must regularly maintain the program you’ve defined to determine which vulnerabilities are critical to your environment. Even if a vulnerability has a high CVSS score, that doesn’t necessarily mean it’s critical to your team. Context and prioritization matter, especially given that many SecOps teams have limited time to apply updates and patches.
CrowdStrike recommends relying on solutions that aid in speedy mitigation and remediation when it comes to all vulnerabilities, both in and out of Patch Tuesday cycles. CrowdStrike’s suite of SecOps solutions help provide deep-level context, including insights surrounding more advanced threats.
For vulnerability management specifically, Falcon Spotlight can help you dynamically rate and prioritize vulnerabilities that matter to your organization, and help you establish workflows to automate those CVEs that need to be scheduled for more regular maintenance. See how Falcon Spotlight operates via its game-changing AI with ExPRT.AI and workflows.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Learn about the latest trending threat in Linux and how you can find it.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
















































