CVE-2022-30190, aka Follina, was published by @nao_sec on Twitter on May 27, 2022 — the start of Memorial Day weekend in the U.S. — highlighting once again the need for round-the-clock cybersecurity coverage. Threat hunting in particular is critical in these instances, as it provides organizations with the surge support needed to combat adversaries and thwart their objectives.Hunting for Follina
As with previous zero-day disclosures, OverWatch’s approach to hunting remains unchanged. OverWatch hunts specifically for hands-on-keyboard activity — not initial access vectors. Laser-focusing resources on post-exploitation behavior is a proven strategy that has effectively and efficiently uncovered sophisticated adversaries leveraging prior zero-day vulnerabilities, such as the Log4j vulnerability.
Over Memorial Day weekend, OverWatch analysts were on high-alert, actively monitoring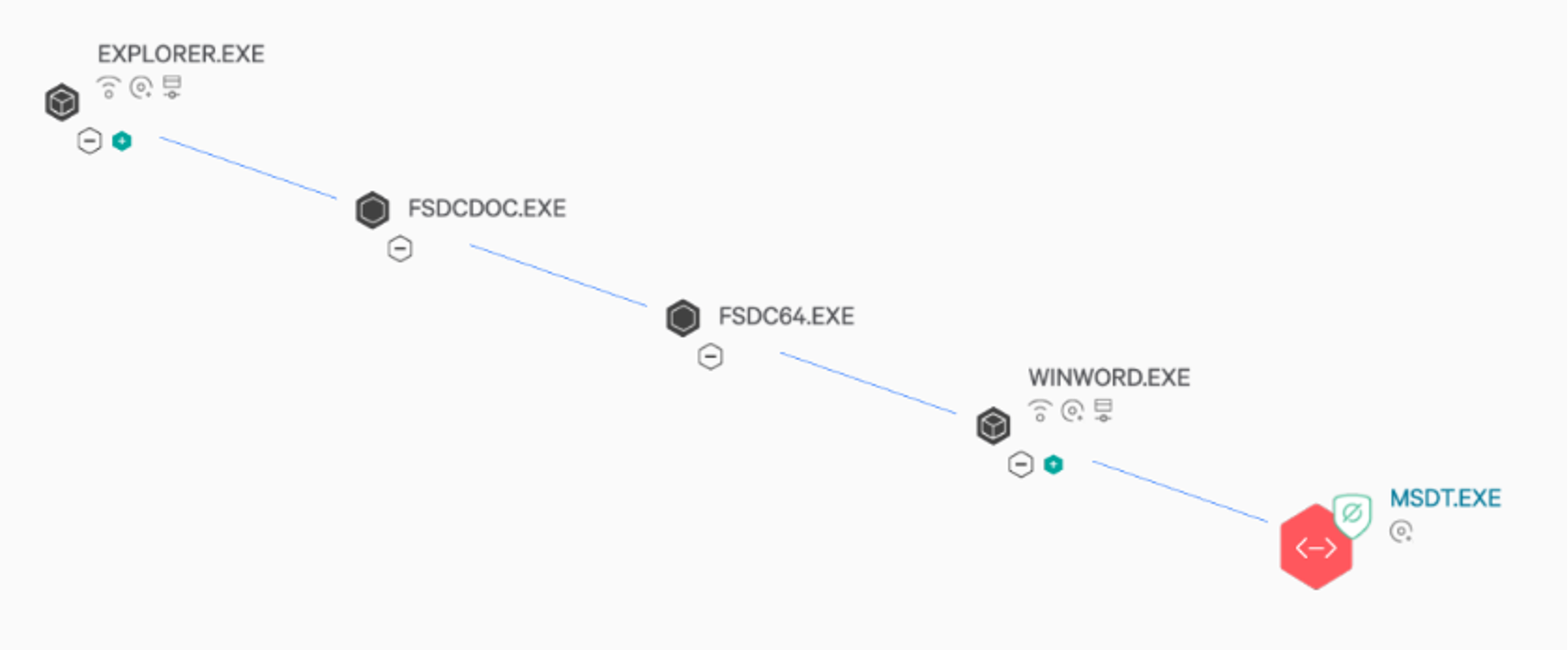 Figure 1. A process tree showing execution of arbitrary PowerShell via Microsoft Diagnostic Tool through a URI directive in a carefully crafted Word document.
Looking at the commands run as part of this adversary emulation, OverWatch observed an attempt to use
Figure 1. A process tree showing execution of arbitrary PowerShell via Microsoft Diagnostic Tool through a URI directive in a carefully crafted Word document.
Looking at the commands run as part of this adversary emulation, OverWatch observed an attempt to use 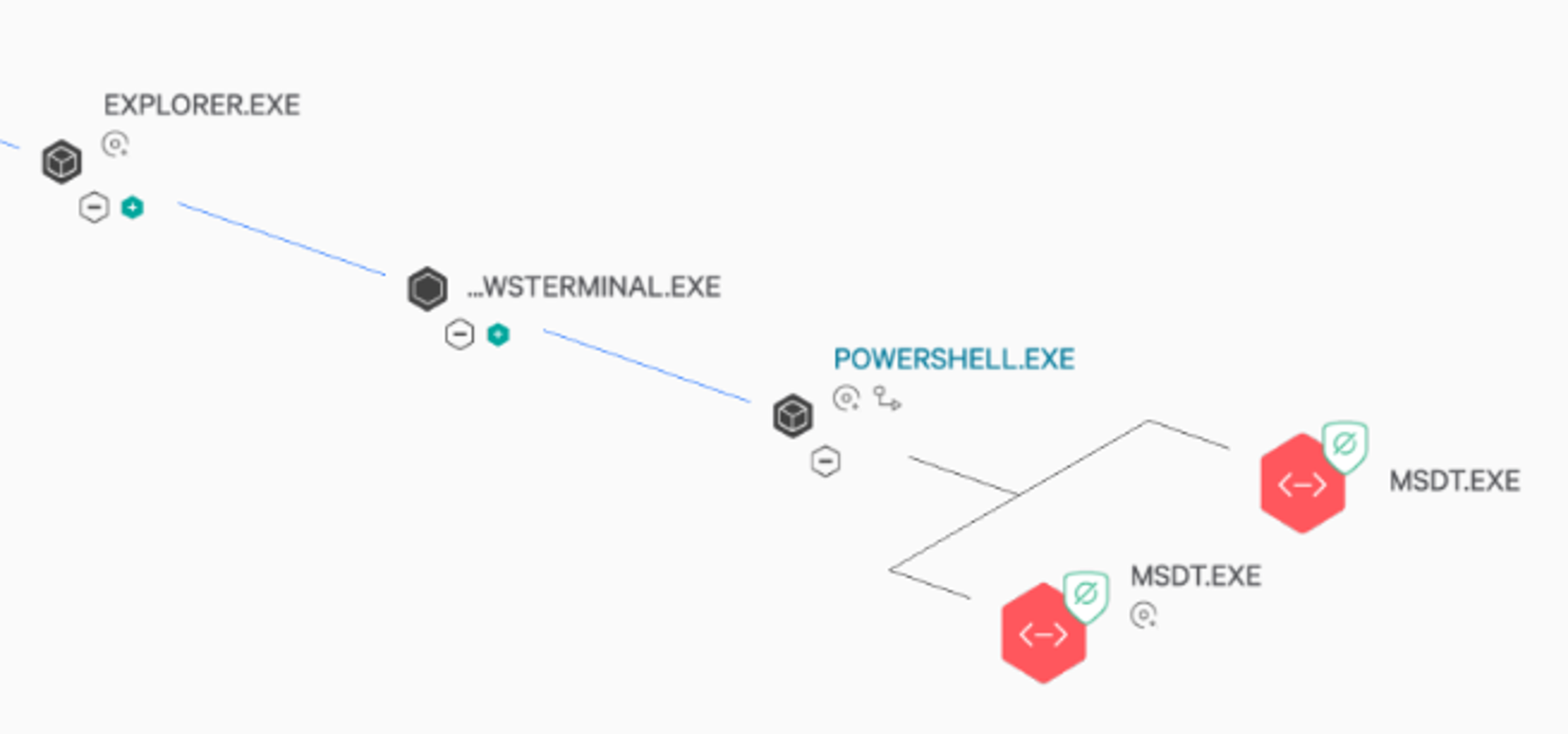 Figure 2. In this example, the vulnerability is abused via an interactive PowerShell session, showing how Follina may be abused to obfuscate further action on objectives once initial access has already been obtained.
Figure 2. In this example, the vulnerability is abused via an interactive PowerShell session, showing how Follina may be abused to obfuscate further action on objectives once initial access has already been obtained.
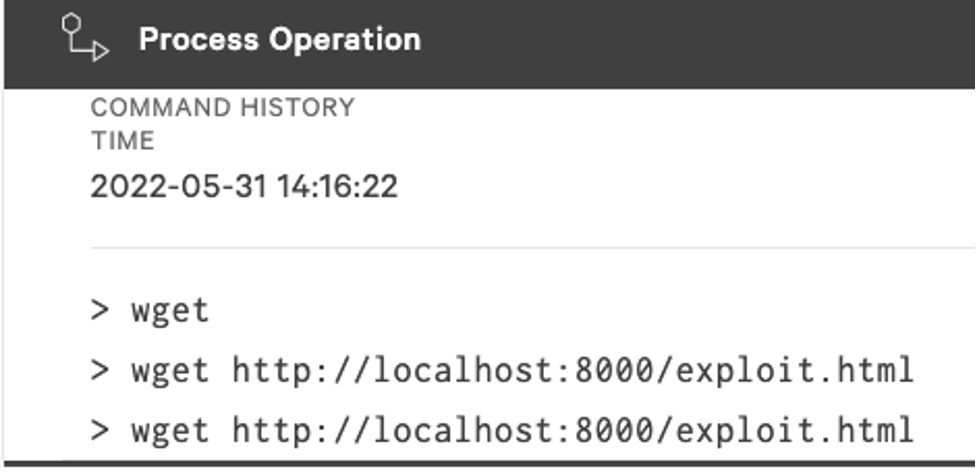 Figure 3. While Falcon will show wget as a captured process operation, all web requests will take place entirely within PowerShell, using the Invoke-WebRequest cmdlet.
Utilizing an Event Search query developed by the OverWatch team, you can search for abuse of
Figure 3. While Falcon will show wget as a captured process operation, all web requests will take place entirely within PowerShell, using the Invoke-WebRequest cmdlet.
Utilizing an Event Search query developed by the OverWatch team, you can search for abuse of
The Follina vulnerability, classified as a zero-day, can be invoked via weaponized Office documents, Rich Text Format (RTF) files, XML files and HTML files. Moreover, there are a variety of ways this vulnerability can be used in the wild. As always, OverWatch threat hunters are casting a wide net in hunting for this activity — protecting customers against both known and unknown threats.
The CrowdStrike Falcon®® platform protects customers from current Follina exploitation attempts using behavior-based indicators of attack (IOAs). As described in depth in this CrowdStrike blog about Follina, the Falcon sensor has detection and prevention logic that addresses exploitation of this vulnerability. With "Suspicious Process Blocking" enabled, Falcon will block code execution attempts from
msdt.exe. Even without "Suspicious Process Blocking" enabled, the Falcon sensor will still generate a detection in the Falcon console.
Today’s determined adversaries, however, are known to be persistent and agile in their attempts to circumvent automated detections. OverWatch remains vigilant in tracking this new threat as it evolves to provide a strong last line of defense.
Hunting for Follina
As with previous zero-day disclosures, OverWatch’s approach to hunting remains unchanged. OverWatch hunts specifically for hands-on-keyboard activity — not initial access vectors. Laser-focusing resources on post-exploitation behavior is a proven strategy that has effectively and efficiently uncovered sophisticated adversaries leveraging prior zero-day vulnerabilities, such as the Log4j vulnerability.
Over Memorial Day weekend, OverWatch analysts were on high-alert, actively monitoringvarious open source intelligence outlets that showed early signs of an influx in
ms-msdt usage.
Initial publications demonstrated a successful proof-of-concept utilizing Microsoft Word (winword.exe) as the parent process to msdt.exe. While OverWatch has also observed winword.exe as the predominant parent process leveraged for exploitation of Follina, threat hunters have also seen cmd.exe, explorer.exe and powershell.exe used as parent processes. The process tree below illustrates an attempted Follina exploitation as part of likely adversary emulation activity observed by OverWatch:
 Figure 1. A process tree showing execution of arbitrary PowerShell via Microsoft Diagnostic Tool through a URI directive in a carefully crafted Word document.
Figure 1. A process tree showing execution of arbitrary PowerShell via Microsoft Diagnostic Tool through a URI directive in a carefully crafted Word document.regsvr32.exe to execute a malicious DLL file:
C:\Windows\SysWOW64\msdt.exe ms-msdt:/id PCWDiagnostic /skip force /param "IT_RebrowseForFile=cal?c IT_LaunchMethod=ContextMenu IT_SelectProgram=NotListed IT_BrowseForFile=h$(start-process('powershell')(@('regsvr32.exe','-u','C:\Users\Public\Documents\customDLL_stageless64.dll')))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe IT_AutoTroubleshoot=ts_AUTO"winword.exe(Microsoft Word Binary)msdt.exe(Microsoft System Diagnostic Tool)regsvr32.exe(DLL Registration Service Binary)
 Figure 2. In this example, the vulnerability is abused via an interactive PowerShell session, showing how Follina may be abused to obfuscate further action on objectives once initial access has already been obtained.
Figure 2. In this example, the vulnerability is abused via an interactive PowerShell session, showing how Follina may be abused to obfuscate further action on objectives once initial access has already been obtained.Advanced Exploitation Technique Hunting
In addition to Microsoft Office products utilizingms-msdt, PowerShell also executes any code via msdt.exe as it trusts Microsoft Protocol URIs. Therefore, adversaries can leverage the built-in web parsing capabilities of PowerShell to download malicious HTML containing ms-msdt directives. This allows the adversary to obfuscate any further commands by leveraging msdt.exe to execute arbitrary code as opposed to using Command and Scripting Interpreter (T1059) directly. Since adversaries can use wget to facilitate further action on objectives within the environment, OverWatch continues to hunt for malicious instances or anomalies surrounding the use of PowerShell’s built-in web request capabilities.
When hunting for Follina exploitation strings utilizing wget, curl or iwr, it is important to remember that they are aliases for the PowerShell cmdlet Invoke-WebRequest and as a result, the alias will not appear in the process tree.
 Figure 3. While Falcon will show wget as a captured process operation, all web requests will take place entirely within PowerShell, using the Invoke-WebRequest cmdlet.
Figure 3. While Falcon will show wget as a captured process operation, all web requests will take place entirely within PowerShell, using the Invoke-WebRequest cmdlet.msdt.exe in your environment:
event_simpleName=ProcessRollup2 event_platform=win FileName=msdt.exe
| search (PCWDiagnostic AND ms-msdt:)
| eval ProcessExplorer="https://falcon.crowdstrike.com/investigate/process-explorer"
| strcat ProcessExplorer ".html" aid ".html" TargetProcessId_decimal "?_cid=" cid ProcessExplorerURL
| table _time ParentBaseFileName CommandLine ComputerName UserName ProcessExplorerURL
| sort + _timemsdt.exe where the process event contains two keywords that are known to be present in successful exploitation attempts within the process command line. The third and fourth lines construct a Process Explorer link to the relevant msdt.exe process, which can be useful for triaging the executions. The final two lines format the results in a table, and sort them chronologically.
Please note that depending on which Falcon cloud you reside in, you may need to adjust the second line of the query which is used to generate a Process Explorer link:
| Cloud | PrEx URL String |
| US-1 | https://falcon.crowdstrike.com/investigate/process-explorer |
| US-2 | https://falcon.us-2.crowdstrike.com/investigate/process-explorer |
| EU | https://falcon.eu-1.crowdstrike.com/investigate/process-explorer |
| Gov | https://falcon.laggar.gcw.crowdstrike.com/investigate/process-explorer |
Conclusion
The announcement of Follina follows a trend that OverWatch has observed in which zero-day exploits are released leading up to or on a long weekend. Holiday weekends are an opportune time for adversaries to exploit zero-days as organizations tend to have reduced resources available and respond slower to threats. OverWatch, armed with the power of CrowdStrike Security Cloud, leverages statistical-, hypothesis- and intelligence-driven threat hunting 24/7/365 to discover malicious artifacts and detection methods not accounted for in automated, passive monitoring. As new vulnerabilities like Follina hit the news, OverWatch immediately begins analyzing customer environments for threat activity and alerts them to risks. OverWatch’s hunting methodology moves beyond the zero-day, protecting customers against all threats regardless of the initial access vector. OverWatch Elite builds on the 24/7 threat hunting operations provided as a part of OverWatch standard and includes additional services, such as: 60-minute call escalation for critical threats, quarterly threat briefings, tailored threat hunting and more. OverWatch Elite customers are also invited to a private Slack channel where they can reach an OverWatch Elite analyst to respond with speed and confidence.Additional Resources
- Learn more about Falcon OverWatch’s proactive managed threat hunting.
- Discover the power of tailored threat hunting OverWatch Elite provides customers in this blog post.
- Watch how Falcon OverWatch proactively hunts for threats in your environment.
- Read more about how part-time threat hunting is simply not enough in this blog post.
- Learn more about the CrowdStrike Falcon®® platform.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































