Solving the Complexity of Azure Identity: Horizon Identity Analyzer

There are a lot of complexities when managing identity in Microsoft Azure, primarily in gaining end-to-end visibility of what a user can do and what properties are applied to them to handle their access. For this reason, CrowdStrike is releasing two new features for Falcon HorizonTM, our cloud security posture management (CSPM) tool, to solve these problems and provide visibility where it is lacking in your Azure environment. A few example problems (of the many) we cover in this blog are multifactor authentication (MFA) for users, the application of roles in Azure and user consent for applications.
Multifactor Authentication
There are currently many different ways to enforce MFA for a specific user in an Azure environment.
- One way is through Conditional Access policies, where you can require the MFA condition to be met before the user can log in.
- Another way is on a per-user basis through Azure AD (login required), where MFA can be “disabled,” “enabled” or “enforced.”
- A third way is through the “Security Defaults” feature where you can enforce MFA across your organization.
There are also ways to enforce MFA through third-party IDPs or an Azure MFA server, but because those are external it’s not always possible to query enforcement of MFA through the Azure APIs.
When reviewing the MFA settings for your users, you may encounter “disabled” when you thought it was enforced, because these three mechanisms are separate from one another. Because of this, it is necessary to query each individual method to see if MFA is actually enabled for a specific user. This limits visibility and makes it difficult to quickly identify risks in the environment, such as when MFA is not enabled and/or not being enforced for users as expected. This is a problem we have solved with Falcon Horizon’s Identity Analyzer.
Roles
Another area of Azure that limits visibility and increases complexity is the multiple definitions of what a “role” is and how/where they are assigned. A role can be applied on a subscription basis, but also on an Azure AD basis, where they do different things and there are different sets of roles to apply in each case. Additionally, they must be queried independently to find out what permissions a specific user has, making it more difficult to get a unified view of what is and what is not allowed for a user. This is also a problem that we have solved with Falcon Horizon’s Identity Analyzer.
Some examples of Azure roles and permission grants include:
- Directory Role: Read, Write or Administrative permissions for Active Directory (AD), enterprise applications (Microsoft and third party), mail and more.
- Application Role: Read and Write permissions for directories, applications, data, etc., via the Azure API. Application roles are assigned to applications and their service principals.
- Delegated Permissions: Read and Write permissions for directories, applications, data, etc., via OAuth 2.0. Delegated permissions are assigned to applications and their service principals.
- Subscription Role: Read, Write or Administrative permissions for Azure cloud services; Azure has published built-in roles and users can create custom roles as needed.
User Consent for Applications
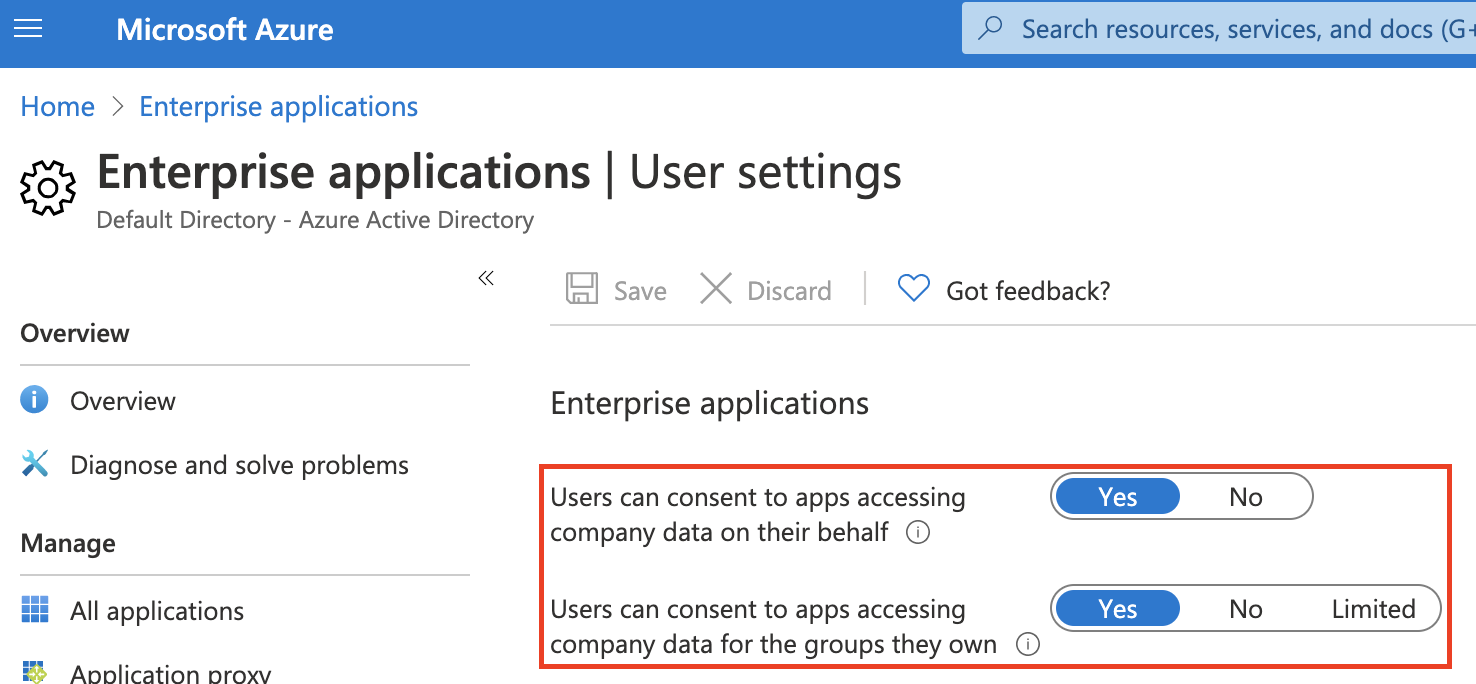
Another pain point in Azure is the default settings applied to an Azure AD, allowing users to consent on behalf of the company to grant applications access to company data. By default, this is allowed and does not require any type of approval from an administrator, as shown in the following screenshot.
Microsoft’s documentation itself warns of potential dangers with these settings, specifically noting the “risk of malicious applications attempting to trick users into granting them access to your organization’s data.” This could manifest as a targeted attack on an employee to trick him or her into granting access to company mailboxes through a malicious application. All of this could happen within your company without you even realizing it.
Falcon Horizon has recently added detections to identify when these two settings are set to “Yes” so you can properly configure your application consent settings for a safer environment. This, combined with Identity Analyzer, will help ensure users cannot freely consent and identify what applications have been granted access to data that may not have been intended.
Falcon Horizon’s Identity Analyzer
This new update brings two new features to Falcon Horizon under the umbrella of Identity Analyzer.
Application Registrations
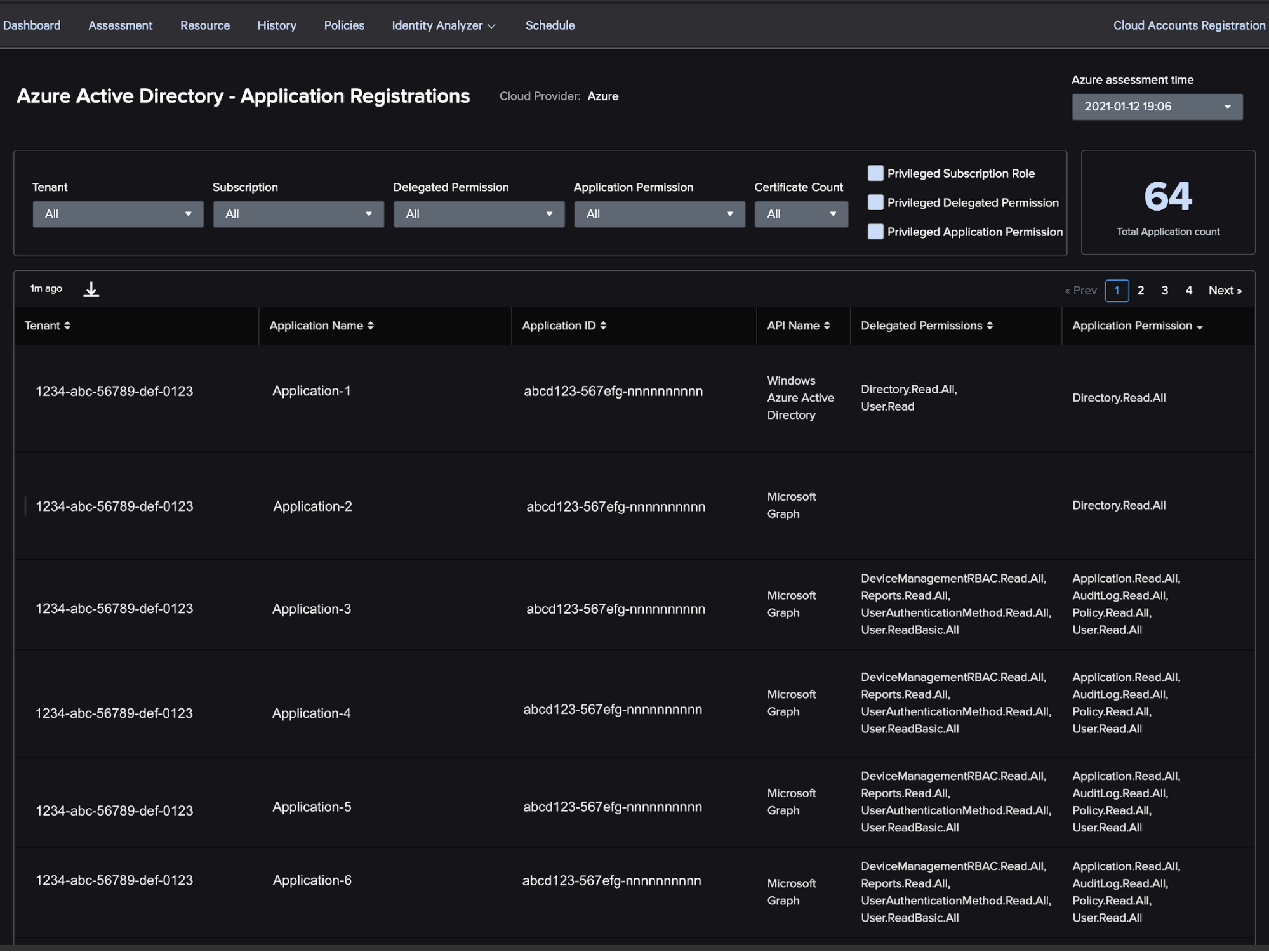
The first new feature brings a unified dashboard to review application registrations within your Azure environment. This allows you to search, filter and identify issues in the applications you have in your environment and may be used to identify overly permissive applications, old/unused applications, multiple secrets/certificates for the same application and much more.
One particularly useful feature is the “Privileged” filter checkboxes. These allow you to filter the applications by privileged subscriptions roles, privileged delegated permissions and privileged application permissions, all with a single click. This combined with Horizon’s “User Consent for Applications” checks referenced above can be very powerful.
It’s also good to know when applications have multiple secrets or certificates, which can be thought of basically as passwords. The credentials could be compromised, and this view would provide good insight into the information behind the secret/certificate, but they may also be added by a privileged user as a way to maintain persistent access to the environment without messing around with users or accounts. Try filtering by “Certificate Count” set to two or higher to identify potentially risky setups.
AD Users
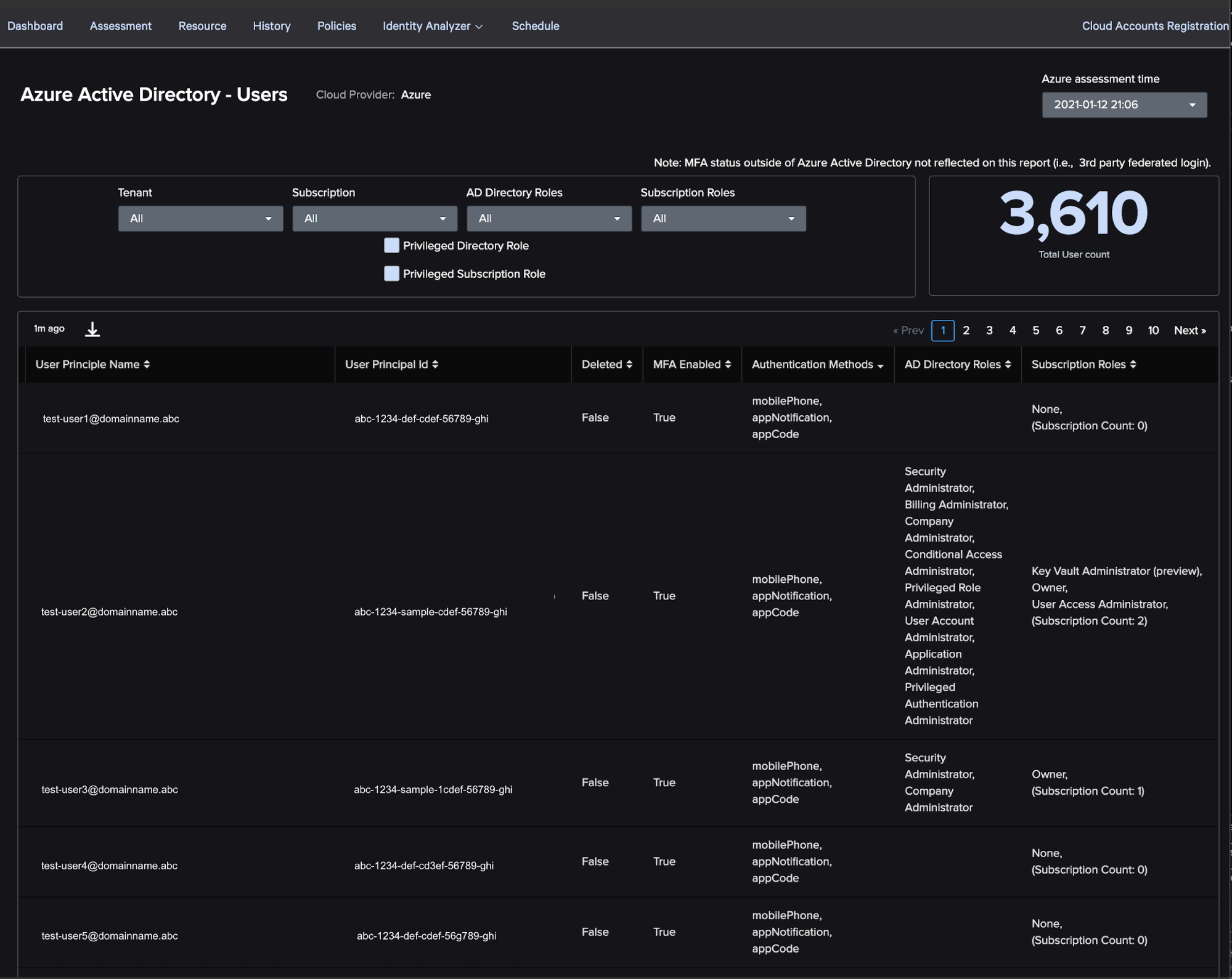
The AD Users feature is another unified dashboard that allows you to search and filter your Azure AD users, properties applied to them, and permissions applied to them in both Azure AD and at the subscription level. For example, the MFA Enabled column accounts for all three different types of MFA we discussed above to give you a single answer of whether or not MFA is required for that user. It also solves the problem of lack of visibility into a single user’s permissions through both AD roles and subscription roles by providing that information in one place.
Again, a useful feature of this dashboard is the “Privileged” filter checkboxes. These allow you to identify users who are granted high-privileged access to the environment through either Azure AD roles or through subscription roles applied to them.
Conclusion
Enjoy these new features now, which are already released to customers with the Falcon Horizon module.
Additional Resources
- Learn about CrowdStrike’s powerful cloud security solutions by visiting the webpage.
- Learn how CrowdStrike makes cloud security posture management simple — visit the Falcon Horizon product webpage.
- Learn more about comprehensive breach defense with CrowdStrike Falcon® Cloud Workload Protection.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.