CrowdStrike Falcon® Cloud Security
Cloud Workload Protection (CWP)
Unified workload visibility, protection and response to build, run, and secure your cloud environment
Complete protection from the host to the cloud and everywhere in between
See your entire cloud estate
Falcon Cloud Security provides complete visibility and breach protection across hybrid and multi-cloud environments. Rapidly adopt and secure virtual machines, containers, serverless functions, and Kubernetes on AWS, Google Cloud, and Azure.
Stop cloud attacks
With CrowdStrike’s world-class threat intelligence, we ensure you have the most accurate and fastest way to detect and stop adversaries across all workloads, containers and Kubernetes applications on any cloud.
Shift-left and automate DevSecOps
Seamlessly integrate with continuous integration/continuous delivery (CI/CD) workflows. Secure your workloads at the same speed as your DevOps processes, without compromising performance.
Complete visibility and protection for your cloud workloads
Stop cloud breaches with runtime and container security and compliance
- Comprehensive visibility and protection: Runtime visibility and protection for Linux and Windows hosts, containers and Kubernetes, as well as serverless compute like AWS Fargate.
- Stop zero-day threats in real time: The CrowdStrike Threat Graph® is the industry's most comprehensive set of endpoint and workload telemetry, threat intelligence, and AI-powered analytics built to stop adversaries in their tracks.
- Accelerate response with enriched threat intelligence: Visibility into relationships across account roles, workloads, and APIs to provide deeper context for faster more effective response.
Enhance business agility with CI/CD integration
- Accelerate Secure App delivery: Enhance operational security and accelerate production readiness by implementing predefined image and Infrastructure as Code (IaC) policies.
- Enable DevSecOps: Streamline visibility and drive alignment through reporting and dashboards. Access shared understanding across security operations, DevOps and infrastructure teams.
- Integrate with developer toolchains: Seamlessly integrate with Jenkins, Bamboo, GitLab, and more to respond and remediate faster within the DevOps tool sets you already use.

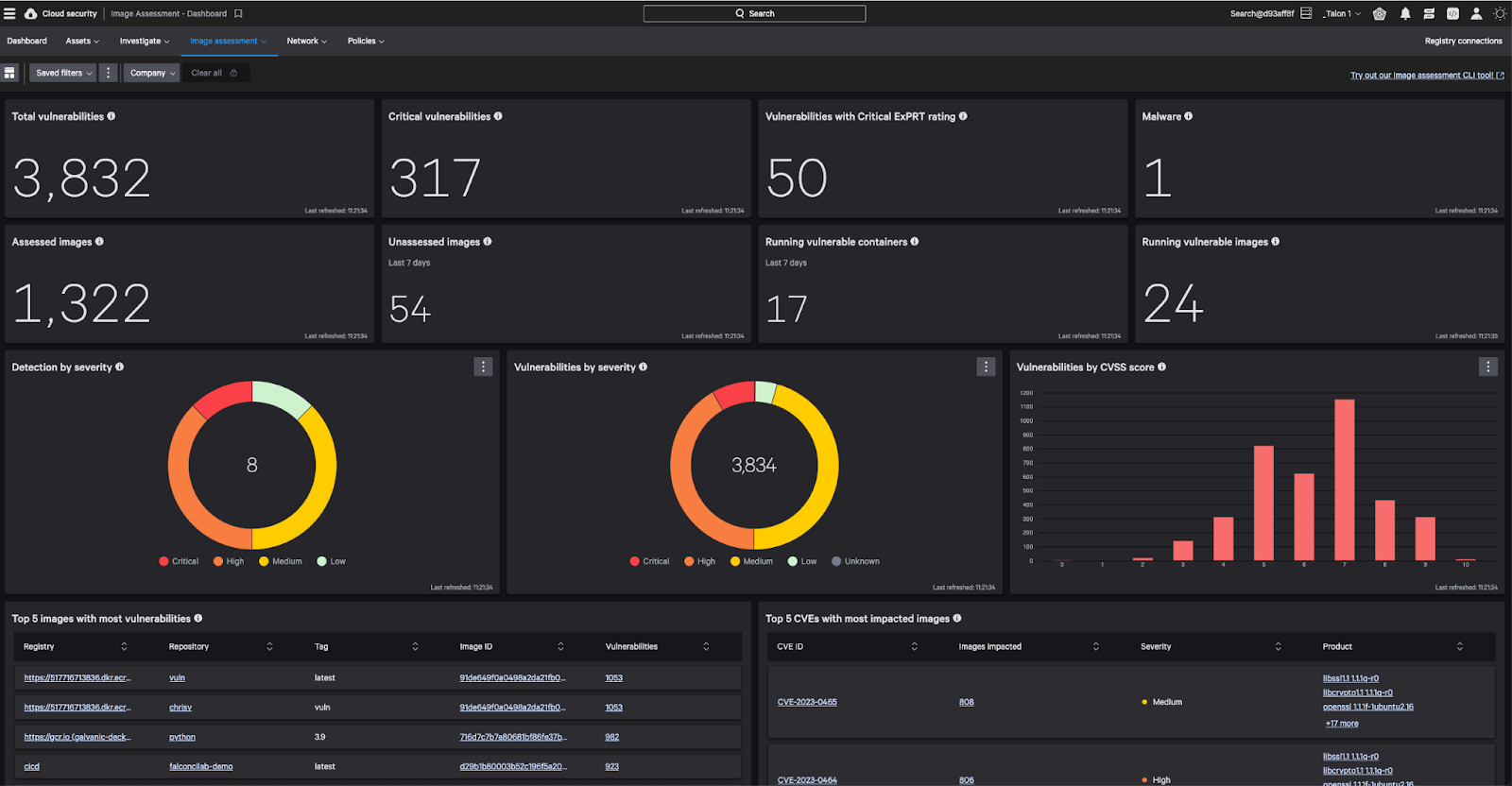
Rapidly detect and remediate vulnerabilities
- Visibility and risk management in a unified platform: Gain visibility into vulnerabilities and prioritize risk around your cloud workloads, containers, images, and registries.
- Identify vulnerabilities prior to production: Improve security and save time by assessing your images prior to production through supported registries or running local image assessment.
- Monitor continuously: Identify new vulnerabilities at runtime, alert and take action without having to rescan images.

The definitive cybersecurity platform for the cloud era
Trillions
of security events monitored weekly
140M+
of IOA protections every minute
Billions
of containers protected
Tested and proven leader
Frost & Sullivan has plotted the top companies in the Global Cloud Workload Protection Platform (CWPP) market in its 2023 Frost Radar™ analysis. CrowdStrike has been named a leader—excelling across both the innovation and growth indices.

Forrester evaluated the most significant cloud workload security (CWS) vendors based on three main categories — current offering, strategy, and market presence — and interviews with customers.

SC Media named the top 5 “Best Cloud Workload Protection Solutions”. CrowdStrike Falcon Cloud Security was included as part of those Top 5 named.
Falcon Cloud Security Customer Stories
"Cloud is a big part of our future. CrowdStrike has given us the security baseline patterns we need to have to make sure that as we move into the cloud, the infrastructure that we are setting up is secure from the outset."
Mick McHugh, CISO
@ Tabcorp
"CrowdStrike Falcon Cloud Security helps us swiftly assess our environment, address gaps, and respond in real-time."
Anthony Cunha, Deputy CISO
@ Mercury Financial