Microsoft has released 71 security patches for its March Patch Tuesday rollout. Of the 71 CVEs addressed, three are ranked as Important zero-days. This month the quantity of patches for Critical vulnerabilities remains low; however, the total number of updates is nearly double what was offered in February 2022.
As vulnerabilities and patches continue to be released, and as stories around patch updates change (see Log4j as an example), it’s vitally important for SecOps teams to maintain a careful remediation and mitigation plan around all vulnerabilities relating to their environments. CrowdStrike’s vulnerability research team offers details and analysis on the vulnerabilities affecting most organizations; however, your company may use a more particular set of Microsoft products. We recommend that you review the vendor’s research accordingly, along with your standard prioritization and remediation plan.
Multiple Zero-day Vulnerabilities
The three zero-day vulnerabilities reported and patched this month only garner CVSS scores between 6.3 and 8.8, or a rank of Important. Nonetheless, these vulnerabilities are relevant to any organization using the affected products. For a more accurate understanding of how these zero-day vulnerabilities could affect your organization, trial CrowdStrike Falcon® Spotlight™ ExPRT.AI. It will provide valuable data and insights, predicting when and how these vulnerabilities could affect your environment.
This month, the zero-days cover a broad range of Microsoft products:
CVE-2022-21990: Remote Desktop Client remote code execution (RCE) vulnerability. This client-side vulnerability should not impact organizations as much as a server-side RDP vulnerability, but its listing as publicly known warrants attention for SecOps teams, and it should be patched promptly. This CVE has the highest CVSS score (8.8) out of this month’s three publicly known flaws. In the case of a Remote Desktop connection, an attacker with control of a Remote Desktop Server could trigger a RCE attack on the RDP client machine when a victim connects to the attacking server with the vulnerable Remote Desktop Client.
CVE-2022-24512: .NET and Visual Studio remote code execution vulnerability. Rated as Important with a CVSS of 6.3, this vulnerability does not require any type of privileges to be exploited; however, successful exploitation of this vulnerability requires user interaction — in this case, a user triggering the payload in the application.
CVE-2022-24459: Windows Fax and Scan Service elevation of privilege vulnerability. This affects all versions of Microsoft Server and Windows 10 and does not require user interaction or privileges. Because this has a CVSS score of 7.8 and a proof-of-concept exploit code is available, CrowdStrike recommends careful consideration of this vulnerability.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-21990 | Remote Desktop Client Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2022-24459 | Windows Fax and Scan Service Elevation of Privilege Vulnerability |
| Important | 6.3 | CVE-2022-24512 | .NET and Visual Studio Remote Code Execution Vulnerability |
March 2022 Risk Analysis
The attack types favored by adversaries around Microsoft products are comparable with last month's Patch Tuesday report. The top three attack types — remote code execution, privilege elevation and information disclosure — continue to dominate, with denial of service following at only 5% (down from 11% in February).
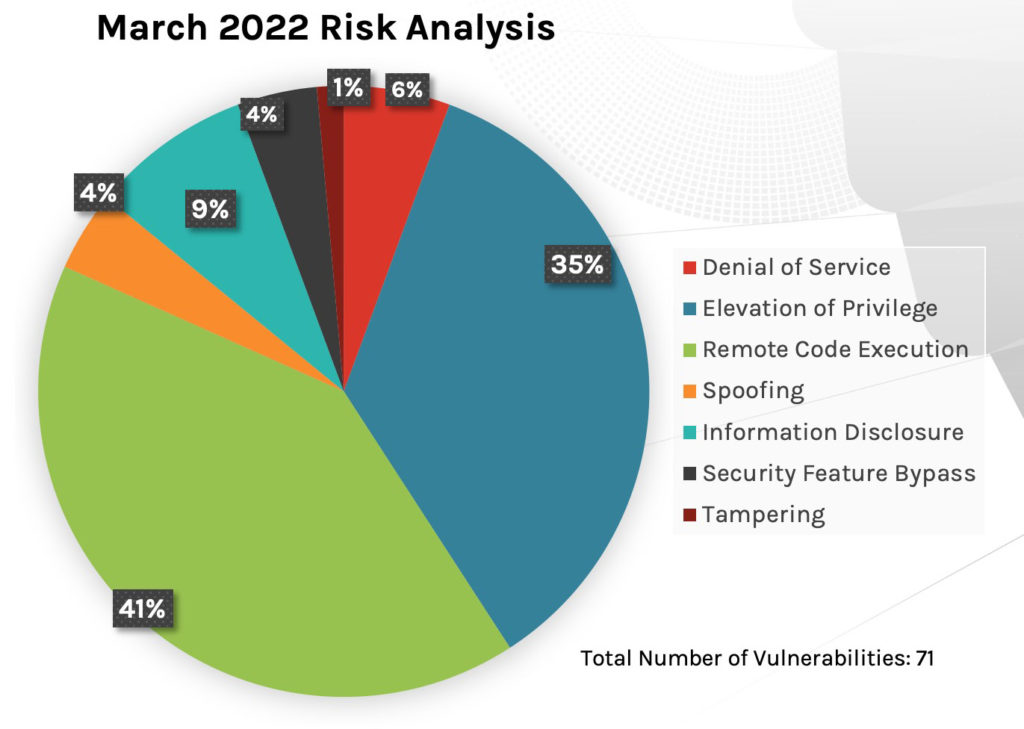 Figure 1. Breakdown of March 2022 Patch Tuesday attack types
Figure 1. Breakdown of March 2022 Patch Tuesday attack typesThe affected product families, however, have changed greatly since last month. While the dominating family is still Windows products, developer tools has taken second place in receiving the most patches, with system centers and Microsoft Office products following not far behind. You’ll recall that Extended Security Updates (ESU) took up the majority of updates in February.
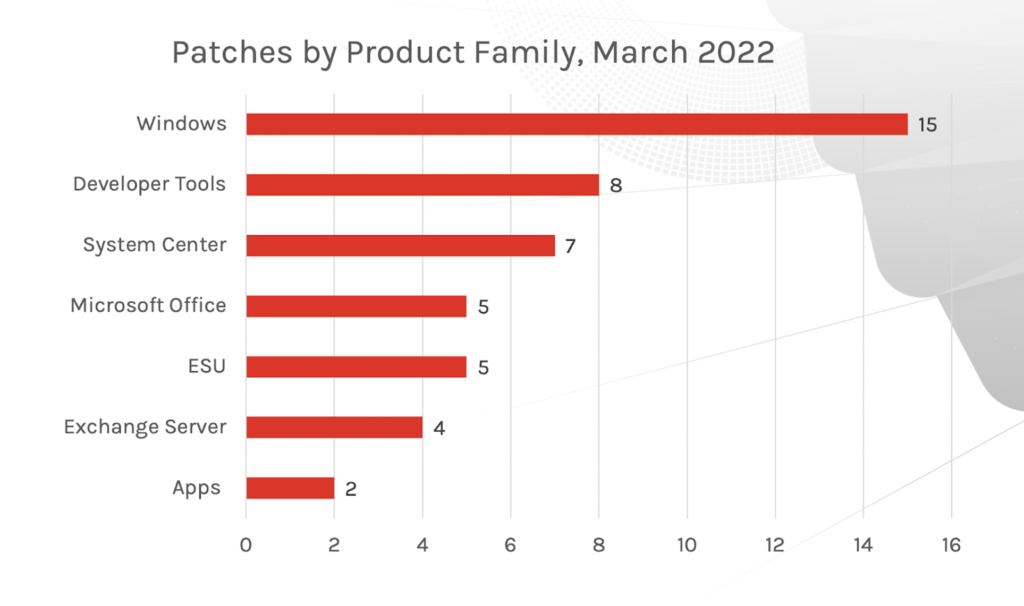 Figure 2. Breakdown of March 2022 Patch Tuesday affected product families
Figure 2. Breakdown of March 2022 Patch Tuesday affected product familiesMicrosoft Exchange Server RCE Vulnerability
CVE-2022-23277 occurs within Microsoft's Exchange Server and is ranked as Critical.
With this vulnerability, an attacker could target the server accounts using arbitrary or remote code execution. As an authenticated user, the attacker could attempt to trigger malicious code in the context of the server's account through a network call. The CVSS score for this CVE is 8.8, likely because of its low complexity of execution. It wouldn’t be surprising to see this vulnerability exploited in the wild in the coming months.
Another Exchange Server vulnerability, CVE-2022-24463, has a lower CVSS score of 6.5 and a rank of Important. This flaw could allow an authenticated attacker to view file content on an affected server. There is very little research offered by Microsoft around the spoofing bugs in Defender for Endpoint and Visual Studio — other than that the Defender bug needs information of the target environment and the Visual Studio bug requires a user to open a file.
For more on the depth and breadth of Critical vulnerabilities relating to Microsoft Exchange Server, read the Patch Tuesday Analysis release from March 2021.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-23277 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 6.5 | CVE-2022-24463 | Microsoft Exchange Server Spoofing Vulnerability |
Numerous Azure Site Recovery Vulnerabilities
Eleven CVEs impacting Azure Site Recovery stand out as possibly important to consider in your patching prioritization strategy this month. (Microsoft offers Azure Site Recovery as a native disaster recovery as a service, or DRaaS, which enables environments to continue to conduct business even during major IT outages).
An adversary can take advantage of Azure Site Recovery by calling the APIs provided by the configuration server and in turn get access to configuration data including credentials for the protected systems. Using the APIs, the attacker can also modify or delete configuration data, which in turn will impact the Site Recovery operation. This month’s release includes fixes for five elevation of privilege and six remote code execution vulnerabilities in the platform. These have CVSS scores ranging from 6.5 to 8.1, though CVE-2022-24469 has the highest severity score.
| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2022-24469 | Azure Site Recovery Elevation of Privilege Vulnerability |
| Important | 7.2 | CVE-2022-24520 | Azure Site Recovery Remote Code Execution Vulnerability |
| Important | 7.2 | CVE-2022-24517 | Azure Site Recovery Remote Code Execution Vulnerability |
| Important | 7.2 | CVE-2022-24471 | Azure Site Recovery Remote Code Execution Vulnerability |
| Important | 7.2 | CVE-2022-24470 | Azure Site Recovery Remote Code Execution Vulnerability |
| Important | 7.2 | CVE-2022-24468 | Azure Site Recovery Remote Code Execution Vulnerability |
| Important | 7.2 | CVE-2022-24467 | Azure Site Recovery Remote Code Execution Vulnerability |
| Important | 6.5 | CVE-2022-24519 | Azure Site Recovery Elevation of Privilege Vulnerability |
| Important | 6.5 | CVE-2022-24518 | Azure Site Recovery Elevation of Privilege Vulnerability |
| Important | 6.5 | CVE-2022-24515 | Azure Site Recovery Elevation of Privilege Vulnerability |
| Important | 6.5 | CVE-2022-24506 | Azure Site Recovery Elevation of Privilege Vulnerability |
Review Vendor Patch Updates and Layer in Your Mitigation Strategy
It may be obvious, but it’s crucial to check in with all of your organization's vendors for the patches they provide; doing so could make all the difference between spending a small amount of time shoring up defenses or potentially having a major incident. We’ve shared what we think are the most relevant patches that could affect organizations, but there are others to consider, including fixes rated Critical in both Microsoft’s HEVC and VP9 video extensions (updates can be found in the Microsoft Store). If you aren’t connected to the internet, your team will need to manually apply these patches.
Along with this approach, review the framework of your vulnerability mitigation plan regularly. If you haven’t reviewed it in a while, take the time to look at your action plan for implementing and prioritizing updates and mitigations. Review the solutions and tools your team utilizes to review and address vulnerabilities. Risk management can only come if there is regular management and maintenance — otherwise, you open your organization up to a variety of threats.
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environment
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Learn about the latest trending threat in Linux and how you can find it.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)








































