Alert overload is practically a given for security teams today. Analysts are inundated with new detections and events to triage, all spread across a growing set of disparate, disconnected security tools. In fact, they’ve burgeoned to such an extent that the average enterprise now has 45 cybersecurity-related tools deployed across its environment.
As attacks grow in scale and sophistication, even more painstaking work is needed on the backend for SOC analysts to piece together the full scope of incidents and their protracted trails of lateral movement across every vector and touchpoint. Siloed detections simply don’t cut it any more.
If we haven’t hit a breaking point yet, it’s clear that we’re rapidly approaching one. In the CrowdStrike 2021 Global Security Attitude survey, close to half (47%) of the 2,200 surveyed IT security practitioners reported that one of their primary challenges in carrying out effective detection and response is the growing number of siloed security tools in their environments (see Figure 1). Ultimately, security teams feel these adverse effects as their visibility gaps widen, and triage and remediation workflows ebb in efficiency.
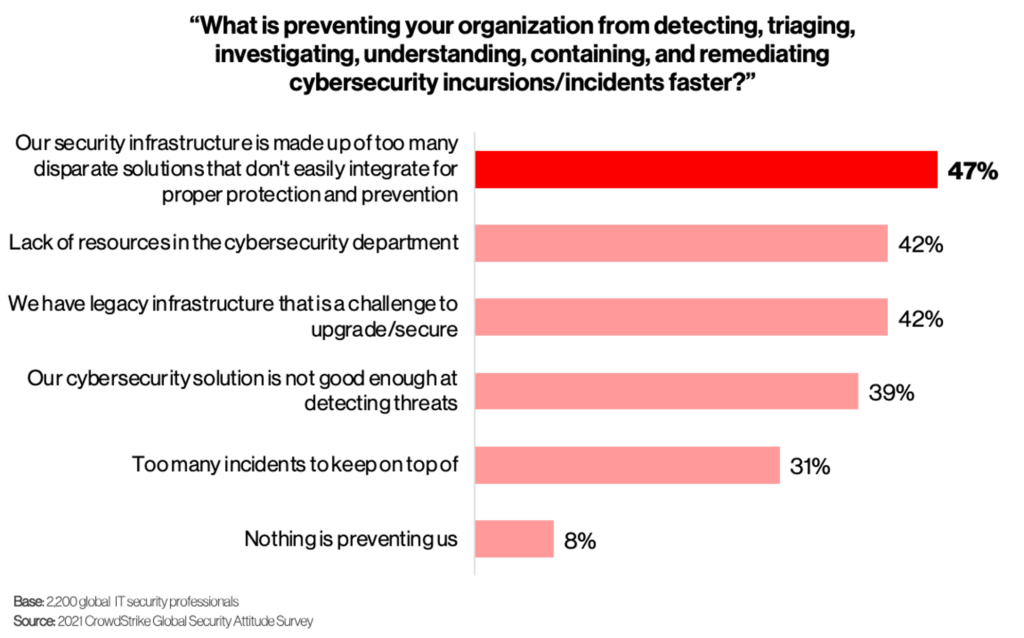 Figure 1. Too many disparate security tools hamper detection and response
Figure 1. Too many disparate security tools hamper detection and responseFive Steps to Kick-start Your Move to XDR
Transitioning to XDR is not as easy as a snap of the fingers — but it shouldn’t be too far removed from that either. Whether you’re just starting out with endpoint detection and response (EDR) or already operate a highly mature security organization, there are practical steps you can take right now to begin your transition to XDR. We lay out five of these below.
Step #1: Recognize You’re Not Starting from Scratch
Unlike many other new security technologies, XDR is additive. Security teams that have (or plan to build) a strong security foundation through EDR have already taken their first step to XDR. This is because XDR is an extension of EDR — i.e., XDR leverages and expands on existing EDR concepts, processes and best practices — and uses it as an efficient starting place with much of the extraneous noise that you’d typically expect from massive data aggregation already natively filtered out.
As a result, EDR data becomes the primary focal point to coalesce additional security telemetry and workflows from systems and applications across an organization’s technology ecosystem.
The simplicity XDR brings to your security operations is how easily it unifies threat detection and response workflows across your security and IT systems. Even if you’re a brand-new CISO running a newly formed security program, you can still approach and plan for XDR as part of your endpoint security strategy—baking in XDR as the underlying, connective framework that links together all things detection and response.
Step #2: Demystify XDR with Concrete Use Cases
XDR is still a new and ambitious security concept. Before you pull the XDR cart too far ahead of the horse, make sure your team and influential business stakeholders are all onboard as well. To make XDR more real for them, illustrate the possibilities that XDR brings in terms of the new and improved security use cases that it will enable, including the following examples:
- Improve the fidelity of alerts with correlated, cross-domain data
- Detect advanced threats that siloed security systems can often miss
- Execute response actions without having to pivot across products
Step #3: Prioritize Plans That Streamline Analyst Workflows
Do you notice a common trend in the three example use-cases listed above? It’s that the primary security value they deliver all stems back to operational efficiency and speed. Though XDR can generate business value in many ways, prioritize the XDR initiatives that most dramatically accelerate and improve the quality of your team’s day-to-day work.
This approach pays several dividends. Not only do operational efficiency improvements lead to some of the largest ROI gains of technology adoption projects, they’re also some of the most tangible for your team. The faster and more efficient work they produce can lead to tertiary benefits, such as higher job satisfaction, reduced analyst burnout and improved staff retention.
Step #4: Take Advantage of Your Existing Security Stack
Extensibility is the fundamental value driver for XDR. XDR shouldn’t require you to replace or add a number of additional tools to your security stack. In fact, quite the opposite. XDR should enable you to keep your existing tools and extend their value through tighter integration, automation and analytics with the endpoint security work you already perform.
With the massive — and still growing — set of systems, applications, networks and identities that exists across every organization, prioritization and elevation of the most important domains is critical for XDR to succeed. For this specific reason, CrowdStrike established the CrowdXDR Alliance to ensure that XDR is architected right and with the right outcomes across the most relevant and critical domains.
Identify the security solutions that are primed to take advantage of an XDR integration, and stagger your approach. You may have many security solutions that fit the bill. But whether you opt to extend XDR first to your secure email gateway or to your cloud workload protection platform (CWPP), focus on bringing in the right supplemental data that will add rich context to your EDR correlations and that will align nicely with the operational priorities outlined in earlier steps.
Step #5: Prioritize Fidelity from the Get-Go
XDR should solve for the alert fatigue problem plaguing security teams today — and it should do so starting from Day One. The primary purpose of XDR is to cut down on alert noise and simplify overly complex and resource-intensive alert configuration processes. If XDR cannot accomplish either without significant time and expertise allocated to tailor detections properly, why even pursue it? You’re right back at square one with a legacy SIEM tool attempting to boil the ocean of security data.
This is why XDR must tip the detection and response efficiency scale back in your favor. It’s simple: You send the data to your XDR solution, it handles the rest — including all initial and ongoing data mapping, correlation and automation necessary to operate it. With this approach in place, you elevate the value of fidelity and minimal tuning to XDR, making them core requirements as opposed to long-term objectives that may or may not ever be achieved.
Kick-start Your Journey to XDR
Download our XDR white paper, Making the Move to Extended Detection and Response (XDR), and prepare your team for the move from EDR to XDR.
Additional Resources
- Get more clarity to XDR market confusion by reading this blog from CrowdStrike CEO George Kurtz: CROWDSTRIKE FALCON® XDR: Why You Must Start With EDR to Get XDR.
- Learn how to do XDR the right way in this blog from CrowdStrike CTO Michael Sentonis: CROWDSTRIKE FALCON® XDR: Extending Detection and Response – The Right Way.
- Discover the benefits and strengths of CrowdStrike CROWDSTRIKE FALCON® XDR.
- Learn what XDR is, and what it isn’t, from our “Exactly What is XDR?” infographic.
- Experience the powerful, cloud-native CrowdStrike Falcon® platform and everything it can deliver to your team.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































