XDR Definition
Extended detection and response (XDR) collects threat data from previously siloed security tools across an organization’s technology stack for easier and faster investigation, threat hunting, and response. An XDR platform can collect security telemetry from endpoints, cloud workloads, network email, and more.
Gartner defines XDR as a "unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components."
With all of this enriched threat data filtered and condensed into a single console, XDR enables security teams to rapidly and efficiently hunt and eliminate security threats across multiple domains from one unified solution.
How XDR Works
XDR connects data from siloed security solutions so they can work together to improve threat visibility and reduce the length of time required to identify and respond to an attack. XDR enables advanced forensic investigation and threat hunting capabilities across multiple domains from a single console.
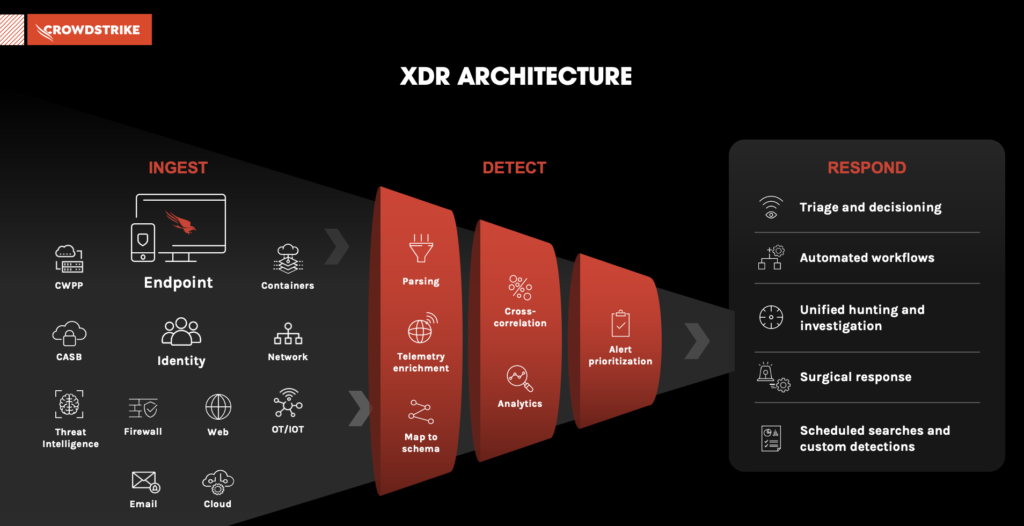
Here's a simple step-by-step of how XDR works:
- Step 1. Ingest: Ingest and normalize volumes of data from endpoints, cloud workloads, identity, email, network traffic, virtual containers and more.
- Step 2. Detect: Parse and correlate data to automatically detect stealthy threats with advanced artificial intelligence (AI) and machine learning (ML).
- Step 3 Respond: Prioritize threat data by severity so that threat hunters can quickly analyze and triage new events, and automate investigation and response activities.
3 Benefits of XDR Security
XDR coordinates and extends the value of siloed security tools, unifying and streamlining security analysis, investigation and remediation. As a result, XDR provides the following benefits:
- Consolidated threat visibility: XDR delivers granular visibility by working across multiple layers, collecting and correlating data from email, endpoints, servers, cloud workloads and networks.
- Hassle-free detections and investigation: Analysts and threat hunters can focus on high-priority threats because XDR weeds out anomalies determined to be insignificant from the alert stream. And with advanced analytics and correlation content prebuilt in the tool, XDR automatically detects stealthy threats — all but eliminating the need for security teams to spend time constantly writing, tuning, and managing detection rules.
- End-to-end orchestration and response: Detailed, cross-domain threat context and telemetry — from impacted hosts and root cause to indicators and timelines — guides the entire investigation and remediation process. Automated alerts and powerful response actions can trigger complex, multi-tool workflows for dramatic SOC efficiency gains and surgical threat neutralization.

SOC MODERNIZATION AND THE ROLE OF XDR
Download now to get insights into the key benefits XDR lends to SOC optimization efforts.
Download NowXDR vs Other Detection and Response Technologies
XDR often gets confused with similar “detect and respond” acronyms that make up the alphabet soup of cybersecurity technology. Below is a quick explanation of the differences between XDR and other detection and response technologies:
- Endpoint detection and response (EDR): Monitors end-user devices — desktops, laptops, tablets and phones — for threats that antivirus software can’t detect
- Managed Detection and Response (MDR): Essentially EDR purchased as a service.
- Network Detection and Response (NDR): Monitors communications within the network to detect, investigate and respond to threats that might otherwise remain hidden in unmanaged devices across on-premises, cloud and hybrid environments.
- Identity Threat Detection and Response (ITDR): Detects threats to all Service and Privileged accounts on your network and cloud.
- Extended Detection and Response (XDR): Uses EDR capabilities to extend protection beyond endpoints to also monitor data from networks, cloud workloads, servers, email, and more.
- Managed Extended Detection and Response (MXDR): Delivers managed multi-domain protection with 24/7 dedicated support, expertise, and response.
CrowdStrike's XDR Solution
CrowdStrike Falcon® Insight XDR unifies detection and response across your security stack to take CrowdStrike’s EDR technologies to the next level. Falcon and non-Falcon telemetry are integrated into one single command console for unified detection and response. CrowdStrike Falcon® Insight XDR turns cryptic signals trapped in siloed solutions into high-efficacy, real-time detections and deep investigation context. Equipped with CrowdStrike Falcon® Insight XDR, security professionals can more quickly and intuitively investigate, threat hunt and respond.
Looking for Managed XDR (MXDR)?
CrowdStrike Falcon® Complete XDR provides 24/7 expert-driven management, threat hunting, monitoring, investigation and response across customers’ attack surface to stop breaches. With native and third-party telemetry ingestion, organizations benefit from better cross-domain visibility and end-to-end remediation to eradicate threats holistically and efficiently.