This week we announced the general availability of CrowdStrike’s newest innovation, CROWDSTRIKE FALCON® XDR, and I couldn't be more excited. Using our same single, lightweight agent architecture, CROWDSTRIKE FALCON® XDR enables security teams to bring in third-party data sources for a fully unified solution to rapidly and efficiently hunt and eliminate threats across multiple security domains.
As George outlined in his blog post today, our goal isn’t just to launch a new product into the market, it’s to help bring clarity to the growing confusion around what XDR is and what it’s not.So What Is XDR?
XDR is the evolution of EDR. XDR must start with EDR technology and build upon that foundation. Forrester says it best: “Good XDR lives and dies by the foundation of good EDR.” If you don’t start with the endpoint, there’s nothing for XDR to “extend.”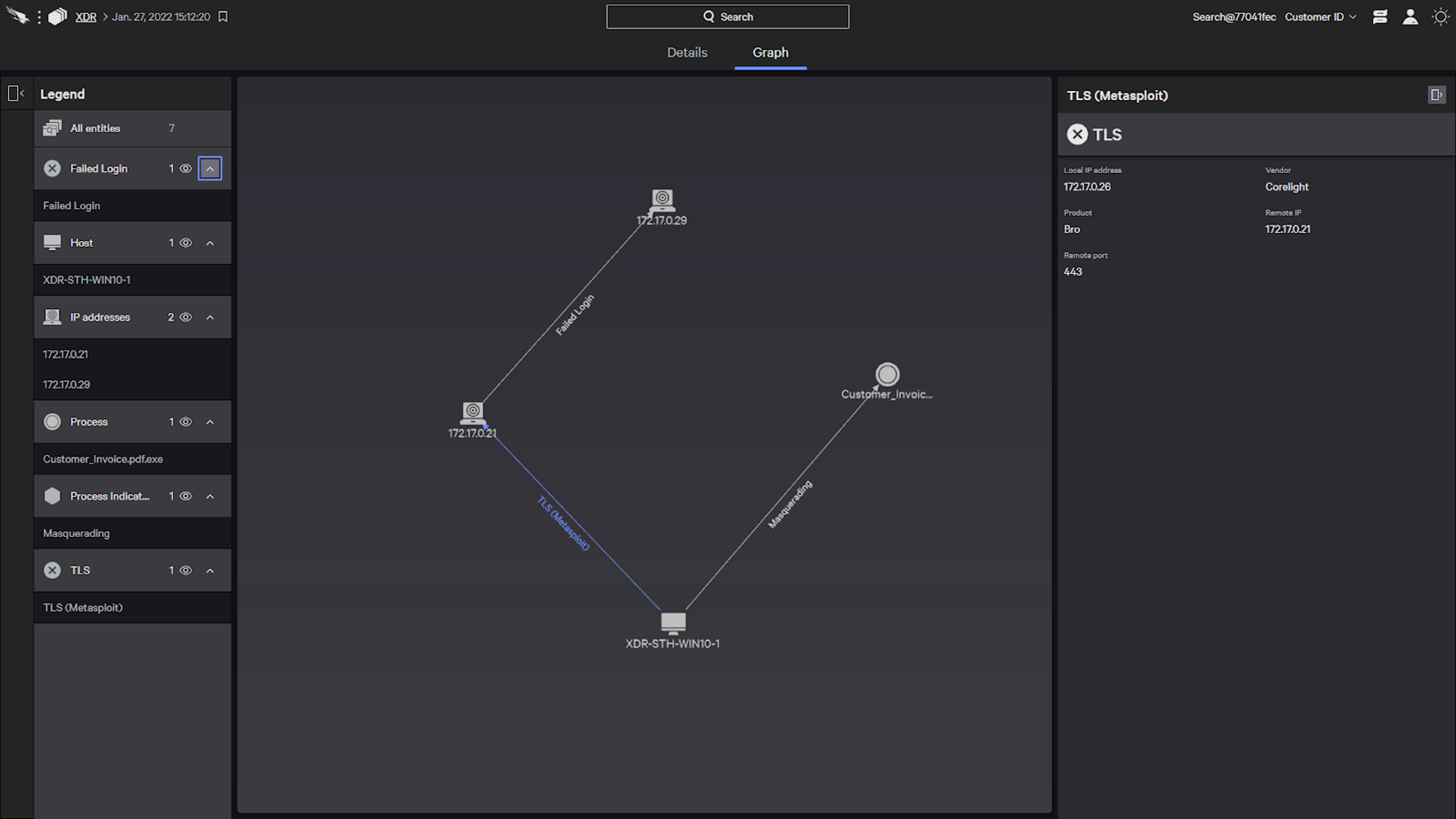 CROWDSTRIKE FALCON® XDR Graph Explorer: CrowdStrike also includes the option to visualize the attack in a graph view. The graph details the Metasploit connection between the adversary and system 1, and illustrates that a malicious file was successfully dropped and run. The adversary then tried and failed to login to a second host. Using the legend, we can highlight certain aspects of the graph by behaviors and traits like CrowdStrike managed systems. (Click to enlarge)
Understanding a given XDR detection can be difficult and time consuming, particularly when there’s disparate information from across data domains and log sources. The graph explorer’s visual representation of a suspected attack helps analysts much more rapidly orient and explore connections in cross-domain data, so they can quickly make a determination and decide on an appropriate response.
CROWDSTRIKE FALCON® XDR Graph Explorer: CrowdStrike also includes the option to visualize the attack in a graph view. The graph details the Metasploit connection between the adversary and system 1, and illustrates that a malicious file was successfully dropped and run. The adversary then tried and failed to login to a second host. Using the legend, we can highlight certain aspects of the graph by behaviors and traits like CrowdStrike managed systems. (Click to enlarge)
Understanding a given XDR detection can be difficult and time consuming, particularly when there’s disparate information from across data domains and log sources. The graph explorer’s visual representation of a suspected attack helps analysts much more rapidly orient and explore connections in cross-domain data, so they can quickly make a determination and decide on an appropriate response.
Right now, if you ask five people to define XDR, you’ll get five different answers. It’s understandable why someone could be confused with more than 30 SIEM, legacy and next-gen endpoint, network security and security service vendors claiming products in the space. Even analysts still debate the meaning of XDR and the definitions are growing divergent.
My biggest issue with the confusion in the market is that it does nothing to serve the customer and can actually create more work for security teams and make them less efficient. Just step back and think about everything an organization has to do just to run their business over the past two years. Now add on top of that the fact that a cyberattack could grind everything to a halt and cause massive capital and brand damages. The customer wants a better way to stay ahead of attacks and stop threats. So they look to the cybersecurity community for guidance, to be a source of truth in the best way to stop attacks. But what the market has done with XDR is add more complexity in their lives, making it hard to figure out what is truly XDR and what’s rehashed and repackaged technology.
I believe in the promise of XDR and the positive impact it can have for security teams. But to realize the massive benefits, it has to be implemented correctly, it has to be more than just monitoring or analyzing events, and it absolutely has to be more than superficial integrations we’ve seen before. Otherwise, XDR is nothing but a buzzword. This is why we’ve approached XDR the CrowdStrike way, purposefully and focused on the customer. We spend a lot of time working with customers to understand their problems and how technology can solve them. With XDR, what we’ve heard is the repeated struggle to make sense of log data and telemetry. It takes deep domain expertise to produce useful detections from a wide variety of sources, and then contextualize them for investigations and response.
CROWDSTRIKE FALCON® XDR was purpose-built to solve this problem, bringing together the best of both the native XDR and hybrid XDR approaches.
Why Now? XDR Before It Was Called XDR
One of the questions I frequently am asked is “Why now? Why join the fray?” It’s a fair question that I believe is best answered in two fundamental ways.First, the industry hype around XDR has reached the point where it can negatively impact security teams. Distorting the concept isn’t victimless; if a customer makes the wrong XDR choice based on confusing marketing, they could actually amplify the exact issues they’re trying to solve.
The second part of this is that CrowdStrike could have been claiming XDR from Day One. CrowdStrike pioneered EDR, and our customers have been leveraging our EDR platform for XDR-style use cases for years. We’ve spent the past decade enriching endpoint data by adding network visibility and telemetry from all workloads, regardless of where they are: on premises, in the cloud or even deployed in a container. We have integrated threat intelligence in everything we do. Today, we also correlate VirusTotal, DomainTools, Sixgill, RiskIQ, OPSWAT and more. We moved beyond traditional telemetry to correlate asset information and user identity and the services and infrastructure we use every day, to expand our scope and enrich our existing knowledge. We also made it easy for customers to enrich telemetry in the CrowdStrike Falcon®® platform with third-party apps at the click of a button with the launch of the CrowdStrike Store.
This is why early on Forrester referred to CrowdStrike as a mature vendor in the XDR space, despite us purposely not banging the hype drum. Our strategy has been clear: to bring important information into the Falcon platform at the right time to enrich our EDR telemetry. This allows us to make actionable decisions about real-world scenarios. We believe XDR is an extension of that existing strategy that has served our customers so well. In this post, I want to share my thoughts on what XDR should be and why CrowdStrike is embracing XDR from a customer-centric perspective, and show a few examples of the power of XDR in action.
So What Is XDR?
XDR is the evolution of EDR. XDR must start with EDR technology and build upon that foundation. Forrester says it best: “Good XDR lives and dies by the foundation of good EDR.” If you don’t start with the endpoint, there’s nothing for XDR to “extend.”XDR must give security teams relevant telemetry from systems and applications across an organization’s entire IT security ecosystem to enhance and accelerate visibility, and XDR must also provide detection and response actions beyond the endpoint to enable security teams to stop breaches faster. While EDR performs many of the same functions at its core, XDR builds on EDR. It makes all telemetry accessible — from endpoints, cloud workloads, identity, email, network traffic, virtual containers, sensors (from operational technology, or OT) and more.
Why CROWDSTRIKE FALCON XDR Is Not Just Another SIEM
CROWDSTRIKE FALCON® XDR is not just about integrating all data into one console. We can do that easily enough with Humio, our powerful log management platform. Humio generates new insights from data contained in logs by providing customizable dashboards to view and explore them — for any data source. Humio is amazing and impactful, but this capability alone is not XDR. XDR isn’t about aggregation, it’s about results. CROWDSTRIKE FALCON® XDR is designed to incorporate security-relevant third-party data sets into the Falcon platform and generate XDR detections. It makes real-time threat detection easier by bringing together world-class threat hunting, machine learning (ML), artificial intelligence (AI) and indicators of attack (IOAs) with third-party data sources from other vendors. Our strategy is clear: to bring important information into the platform at the right time to enrich our EDR telemetry to allow us to make actionable decisions about real-world scenarios.CROWDSTRIKE FALCON® XDR delivers sharper and more impactful remediation strategies by intelligently and efficiently consolidating all of the valuable telemetry from the Falcon platform and third-party vendor solutions, while orchestrating and automating analysis. It’s more than just gathering all network and endpoint related data, it’s about understanding how your data is generated and what that means to your security environment. More on this topic > XDR vs. SIEM
It’s All About Detections and Response
CROWDSTRIKE FALCON® XDR delivers CrowdStrike-generated detections that span a broad range of data sources, along with an investigation capability that allows analysts to view related indicators, affected entities and events.The analyst can explore the data through an event timeline and a new “graph explorer” while pivoting, investigating and coordinating responses from within the Falcon console. Flexibility is key. Customers won’t be limited to our detections and analysts can generate their own custom XDR detections that are relevant to their own environment. But as I alluded to earlier, the data makes the difference, which is why we’re using a native/hybrid XDR approach. From a native perspective, CROWDSTRIKE FALCON® XDR collects telemetry from across the entire platform of Falcon modules. We correlate this with third-party security sources (aka Hybrid) such as email, web, cloud access security broker (CASB), network threat detection, identity and firewall data. This data will, of course, be available for search and alerts. Yet by itself, that doesn’t really solve the customer problem that I mentioned above.CROWDSTRIKE FALCON® XDR consolidates telemetry from relevant security and IT systems that hold meaningful threat data. It also accelerates response and remediation for security teams through coordinated, multi-platform automation. With consolidated, multi-platform telemetry, CROWDSTRIKE FALCON® XDR improves threat detection and correlation for security teams, surfacing hidden, lateral-moving threats that traditionally siloed security systems typically miss or identify too late. XDR detections have an XDR-focused UI in the Falcon console that enables customers to efficiently triage, investigate and respond to cross-domain alerts. Once CROWDSTRIKE FALCON® XDR correlates and analyzes data in real time upon ingestion and automatically generates XDR detections when suspicious activity is discovered, XDR detections appear in the new UI. The workflow will enable you to:
- Triage: Filter XDR detections by data domain and data source alongside more familiar parameters like status and severity for more efficient triage. Assign, update status and comment on XDR detections.
- Investigate: Review detection details in the detection summary, including the indicators that triggered the detection. Pivot from the summary into event search to view event data associated with the alert. Pivot to the Falcon XDR graph explorer to visualize the detection and explore connections between events.
- Respond: Network contain hosts involved in the XDR detection.
Visualizing the Data
One of the unique capabilities of the CROWDSTRIKE FALCON® XDR solution is data visualization. CROWDSTRIKE FALCON® XDR's graph explorer allows analysts to visualize all elements of an XDR detection. Within the graph view, analysts can see how the various indicators, events and entities relate to each other. Analysts can click into each indicator to expand the graph, view the specific events and entities associated with the indicator, and identify the connections between them. Clicking into an indicator, event or entity opens an information panel with security-relevant contextual data from Falcon and other XDR log sources. CROWDSTRIKE FALCON® XDR Graph Explorer: CrowdStrike also includes the option to visualize the attack in a graph view. The graph details the Metasploit connection between the adversary and system 1, and illustrates that a malicious file was successfully dropped and run. The adversary then tried and failed to login to a second host. Using the legend, we can highlight certain aspects of the graph by behaviors and traits like CrowdStrike managed systems. (Click to enlarge)
CROWDSTRIKE FALCON® XDR Graph Explorer: CrowdStrike also includes the option to visualize the attack in a graph view. The graph details the Metasploit connection between the adversary and system 1, and illustrates that a malicious file was successfully dropped and run. The adversary then tried and failed to login to a second host. Using the legend, we can highlight certain aspects of the graph by behaviors and traits like CrowdStrike managed systems. (Click to enlarge)Threat Hunting with CROWDSTRIKE FALCON® XDR
A key benefit of XDR is the ability to hunt for suspicious activity or further investigate detections against cross-domain data. CROWDSTRIKE FALCON® XDR extends threat hunting across all telemetry through the use of Humio Query Language. You can create XDR event searches that run automatically and recur on a schedule that you set. Search results can easily be shared, and your specified recipients can receive notifications each time a scheduled search completes.To streamline threat hunting and triage, threat hunters can generate a custom XDR detection from recurring searches that indicate suspicious activity. You can assign severity and tactic and technique to these custom detections. These custom XDR detections will appear alongside CrowdStrike generated XDR detections for triage.
Automating Response with Falcon Fusion
A key benefit of XDR is response, and we do this a number of ways with CROWDSTRIKE FALCON® XDR. Falcon Fusion powers the “Response” in CROWDSTRIKE FALCON® XDR and orchestrates and automates any security workflow. We’ve built this natively into the Falcon platform, which means that CROWDSTRIKE FALCON® XDR will inherit all of the benefits and enable customers to orchestrate and automate multi-platform notification and response workflows. Additionally, Falcon Real Time Response (RTR) provides a robust remote access tool that goes beyond remediation and works across Windows, MacOS and Linux. RTR gives powerful and dynamic response capabilities to responders. Using predefined commands and customizable scripts that responders can execute, RTR enables teams to respond to incidents and remediate any issues with speed and decisiveness.Accessed directly from the CrowdStrike Falcon® console, it is easy to connect to a host directly and can carry out a comprehensive list of commands to complete key remediation tasks. RTR is not limited to Falcon-centric actions and has limitless applications. It can also be used to deploy a patch, revert to a system snapshot, acquire file artifacts, acquire memory snapshots and dumps, and even make configuration changes to a system. Bringing together Falcon Fusion and Real Time Response, incident responders can easily automate many investigation and response activities. Falcon XDR detections show a “connect to host” information panel, which launches RTR. If you can script it or run the executable, CROWDSTRIKE FALCON® XDR supports it. This video is a good example of what you can achieve with the power and flexibility of Falcon Fusion and RTR.
The Right Ecosystem
Finally, for XDR to truly work, you need a purpose-built partner ecosystem in place in which data and workflows are structured for cross-system detection, analysis and multi-system response. Be sure to invest in a solution that will better protect your enterprise, understand and digest all data, streamline your security operations and lower risk. XDR drives productivity gains and saves security professionals time by allowing them to understand and trust the data they gather. It is about piecing together those disparate pieces of information to form a holistic picture that can detect and remediate intrusions much more easily. For today’s rapidly evolving data environments, XDR just might be the ticket.CrowdStrike: Doing the Hard Work on Data so Customers Don’t Have To
Third-party data ingestion is critical to XDR outcomes. CROWDSTRIKE FALCON® XDR supports ingestion of data from third-party vendors in the CrowdXDR Alliance. We continue to announce and expand support to include more CrowdXDR Alliance partners as well as other security vendors. We’re continuing to develop mapping of each vendor’s telemetry to our XDR Data Schema, which provides a common language for correlation and analysis across telemetry from any source. When ingested, relevant data is automatically parsed and mapped into the XDR Data Schema, and stored in a common repository where it is available for XDR search and detections.
The data ingestion process can vary by vendor and each customer’s environment and configuration, and can be complex — which many vendors don't mention. We announced the CrowdXDR Alliance and we have been working on the XDR Data Schema so you don't have to! As George said in his blog, this is just the beginning for us. I couldn’t agree more. We believe this is a pivotal point in the XDR journey for every organization. For more than a year, you’ve heard various definitions and promises of XDR and what it can do for your organization. I believe in the power of XDR, but I also believe that it has to be done the right way, built on EDR technology and focused on solving the hard problems that every company faces today.
We’re going to continue to do the hard work to deliver the solutions that our customers need to stay ahead of adversaries and stop breaches.
Additional Resources
- Read the CROWDSTRIKE FALCON® XDR GA press release and learn more about
CROWDSTRIKE FALCON® XDR and the CrowdXDR Alliance. - Learn more about Falcon Fusion by visiting the webpage
- Read the blog “Modernize Your SOC with Falcon Fusion, CrowdStrike’s Integrated SOAR Framework.”
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































