Microsoft has released 48 security patches for its February Patch Tuesday rollout. None are considered Critical or known to have been actively exploited. CVE-2022-21989, a publicly known zero-day vulnerability in the Windows Kernel, should be closely monitored as the situation continues to unfold.
Separate from the patches offered this month, Microsoft has strongly suggested an update in the servicing stack. Failure to apply this update could result in serious implications for organizations using Windows Server 2008 and Windows 7/Server 2008 R2.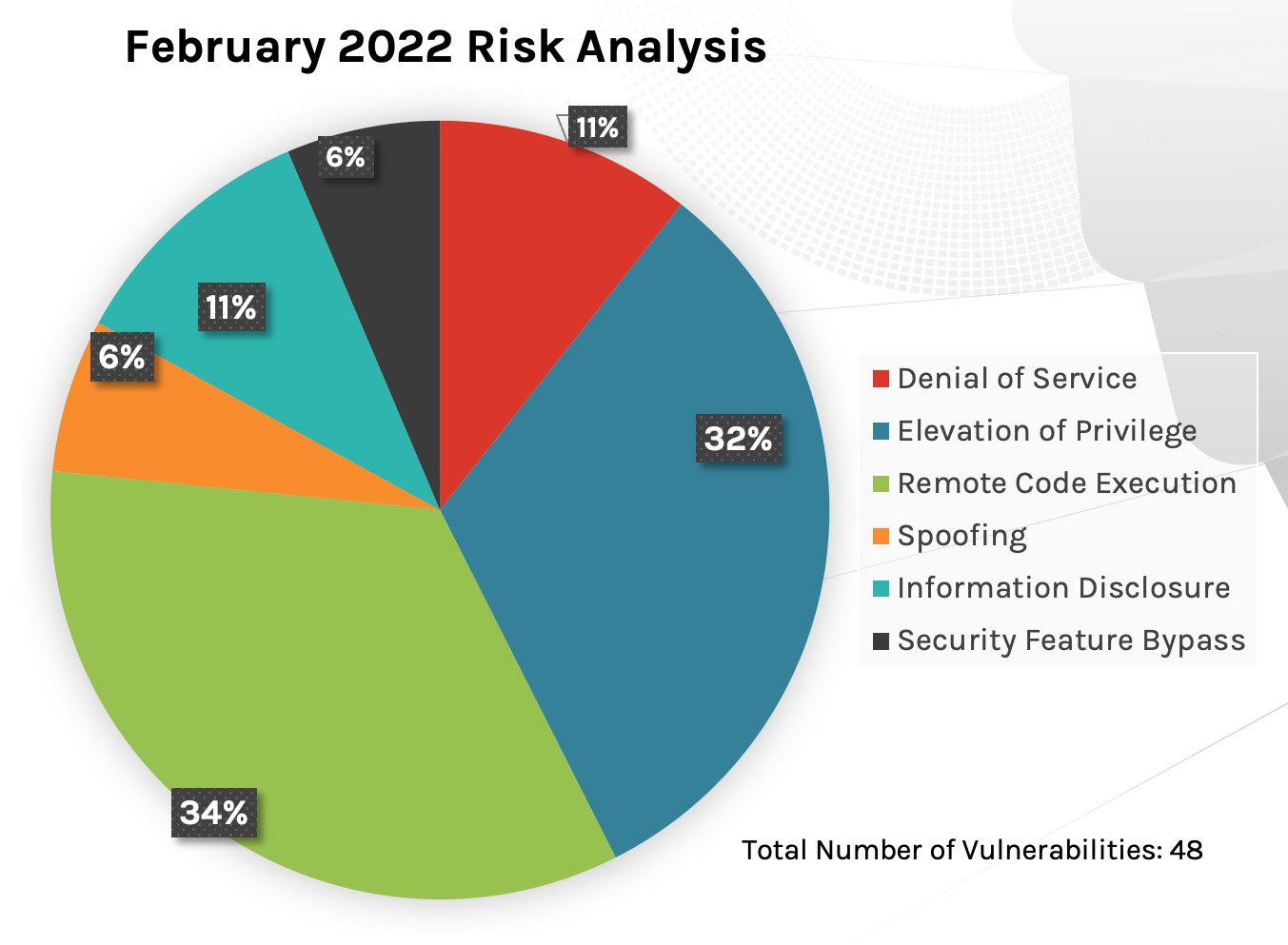 Figure 1. Breakdown of February 2022 Patch Tuesday attack types
Figure 1. Breakdown of February 2022 Patch Tuesday attack types
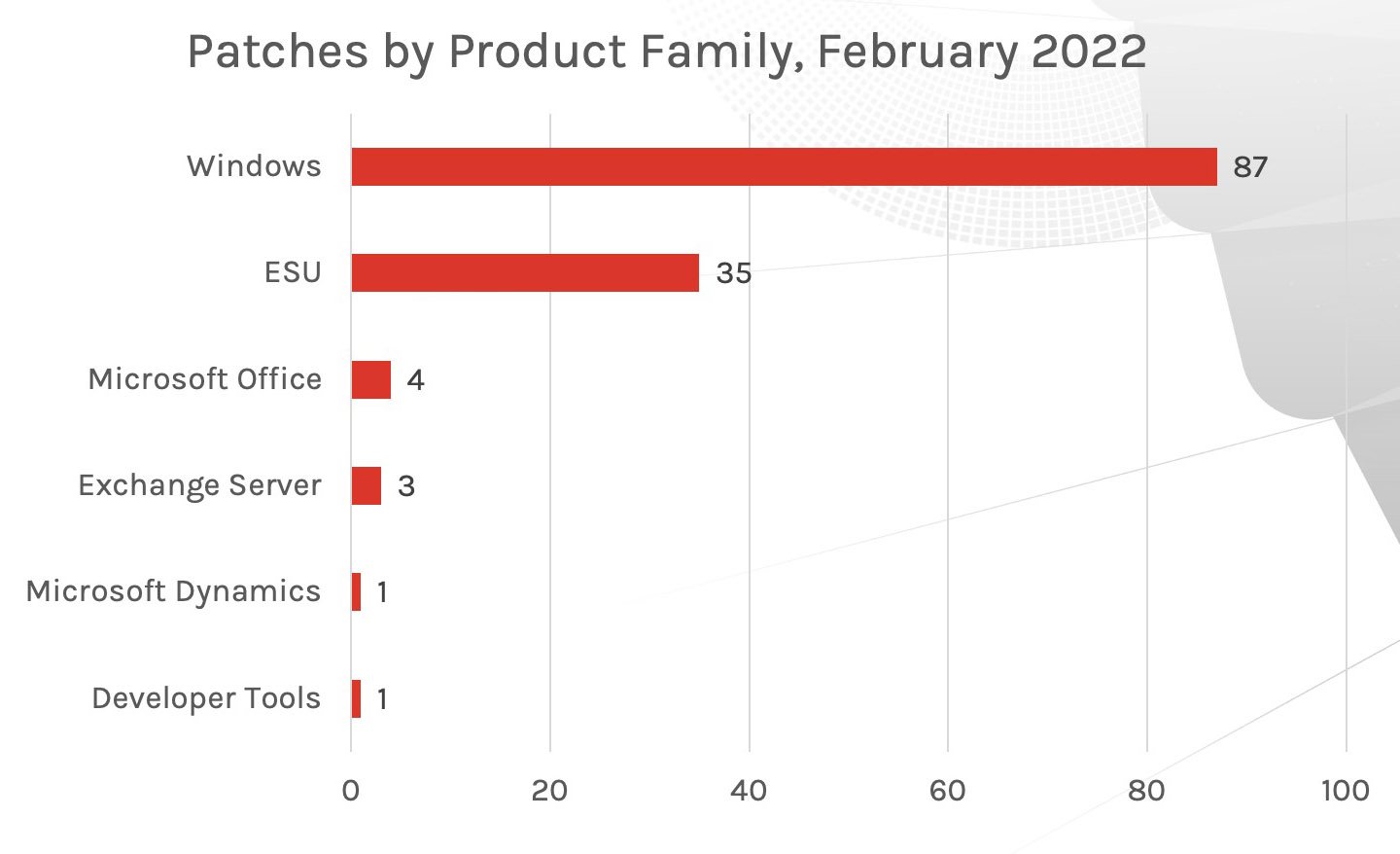 Figure 2. Breakdown of February 2022 Patch Tuesday affected product families
Last month we saw most of the patches affecting Windows and Extended Security Updates (ESU) products, but this month the coverage across multiple Microsoft products has returned. While the bulk of patches are going to the Microsoft Office suite, there is a fair quantity of patches for other product families, with Windows and Developer Tools receiving the most coverage behind Office products.
Figure 2. Breakdown of February 2022 Patch Tuesday affected product families
Last month we saw most of the patches affecting Windows and Extended Security Updates (ESU) products, but this month the coverage across multiple Microsoft products has returned. While the bulk of patches are going to the Microsoft Office suite, there is a fair quantity of patches for other product families, with Windows and Developer Tools receiving the most coverage behind Office products.
Regularly Patch and Review Your Mitigation Strategy
A layered security approach with heavy emphasis on tools, programs and solutions that create efficiency and quicken response time is key to organizations’ security posture. Vulnerabilities are found in a wide variety of Microsoft products and platforms, with attackers diligently working on creative ways to access valuable systems and information. Security teams only have so much time in a given day, and the proper use of security solutions and programs can dramatically increase efficiency and responsiveness.Additional Resources
CrowdStrike continues to provide research and analysis regarding critically rated vulnerabilities and the subsequent patches offered by Microsoft. We will discuss three vulnerabilities with the highest CVSS scores reported for this month and what they could mean for your organization.
New Patches for 48 Vulnerabilities
This month’s Patch Tuesday update includes fixes for 48 vulnerabilities, a relatively low number compared with previous months.While none of the vulnerabilities patched this month are rated as Critical, one CVE that was publicly disclosed this month (CVE-2022-21989) has a CVSS score of 7.1. We see the leading attack types continue to be remote code execution and privilege elevation. Information disclosure and denial of service have increased slightly — something we also saw in December 2021 — with each method comprising 11% of attack types this month.
In the CrowdStrike 2021 Global Threat Report, CrowdStrike Intelligence assessed remote service and privilege escalation as a viable method for credential-based attacks.
As with all parts of the vulnerability management lifecycle, the saying still holds true: “if you can’t see it, you can’t protect it.” Visibility into all areas of your organization and which vulnerabilities are affecting critical systems is essential to a consistent and secure posture.
 Figure 1. Breakdown of February 2022 Patch Tuesday attack types
Figure 1. Breakdown of February 2022 Patch Tuesday attack types Figure 2. Breakdown of February 2022 Patch Tuesday affected product families
Figure 2. Breakdown of February 2022 Patch Tuesday affected product families
Important Vulnerabilities in Windows DNS Server, SharePoint and Windows Kernel
Because no Critical vulnerabilities have been addressed this month, CrowdStrike is calling out some of those classified as Important. While the rank and score of these CVEs are necessary pieces of information for SecOps teams to understand how severity is given, please remember that these vulnerabilities are given a one-time score. As more information is disclosed and other attack information surfaces, the ranking of these vulnerabilities could change and might have a dramatic impact on security teams’ prioritization schedules.Falcon Spotlight ExPRT. AI can help staff identify which vulnerabilities are truly relevant for their organizations to address immediately. Falcon Spotlight, coupled with Falcon Identity Protection, offers robust visibility to stop threats in their tracks. The following updates cover two remote code execution vulnerabilities and one elevation of privilege vulnerability. It is worth noting that CVE-2022-21984 and CVE-2022-22005 are on critical systems and even a short exposure for an organization may yield severe outcomes if not mitigated or patched promptly. CVE-2022-21984: This Windows DNS Server vulnerability utilizes remote code execution as an attack type. A server is only affected if dynamic updates are enabled—a relatively common configuration for many organizations. In this environment, an attacker could take over an organization’s DNS and execute code with elevated privileges. Since dynamic updates aren’t enabled by default, this vulnerability doesn’t receive a Critical rating. An attack type like this could put an entire domain at risk because all accounts can possibly be harvested and thus compromised. If your DNS servers use dynamic updates, your team should treat this bug as Critical. CVE-2022-22005: This remote code execution vulnerability exists in Microsoft SharePoint Server. The update fixes a bug that could allow an authenticated user to execute arbitrary .NET code on the server under the context and permissions of the service account of the SharePoint Web Application. It’s common for SharePoint servers to be exposed on the internet, and this exposure can be used to access an internal network. An attacker would need “Manage Lists” permissions in order to exploit this vulnerability. By default, authenticated users are able to create their own sites and, in this case, the user will be the owner of this site and have all necessary permissions. CVE-2022-21989: This Windows Kernel vulnerability became public prior to Microsoft releasing a patch. Attackers can use privilege elevation to take advantage of this vulnerability. It should be noted that for an attacker to achieve a successful exploitation, they would need to take additional actions prior to exploitation to prepare the target environment. According to Vendor Information, an exploit for this vulnerability is likely to become available in the upcoming days or weeks. Spotlight customers should definitely refer to this vulnerability’s ExPRT rating to see a live, accurate update on how the criticality of this vulnerability could change.
| Rank | CVSS Score | CVE | Description |
| Important | 7.1 | CVE-2022-21989 | Windows Kernel Elevation of Privilege Vulnerability |
| Important | 8.8 | CVE-2022-21984 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 8.1 | CVE-2022-23272 | Microsoft Dynamics GP Elevation Of Privilege Vulnerability |
| Important | 8.3 | CVE-2022-23274 | Microsoft Dynamics GP Remote Code Execution Vulnerability |
Microsoft Office Affected by Multiple Vulnerabilities
As previously stated, the Microsoft Office suite received the most patches this month. Products including Microsoft Excel, Outlook for Mac, Sharepoint and Click to Run are all affected by remote code execution vulnerabilities. Refer to the table below to identify the rank and CVSS score for each CVE.| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-22005 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important | 8.0 | CVE-2022-21987 | Microsoft SharePoint Server Spoofing Vulnerability |
| Important | 7.8 | CVE-2022-21988 | Microsoft Office Visio Remote Code Execution Vulnerability |
| Important | 5.3 | CVE-2022-23280 | Microsoft Outlook for Mac Security Feature Bypass Vulnerability |
Microsoft Servicing Stack Updates
In addition to their monthly patch release, Microsoft has added a new update within the Microsoft servicing stack and advises security teams to install this update on most or all operating systems. While none of the CVEs patched this month have been deemed Critical, it is Microsoft’s view that updating this system is considered Critical. CrowdStrike urges teams to update these operating systems where applicable.
What is a Servicing Stack Update?
Servicing stack updates are shipped separately from the cumulative patches offered because they modify the component that installs Windows updates — essentially updating the updater. The servicing stack is released separately because the servicing stack itself requires an update, and updating it will provide a more secure posture for these servers. This update applies to Windows Server 2008 and Windows 7/Server 2008 R2. It’s recommended that teams running these versions apply them at their earliest convenience. CrowdStrike covered the challenges surrounding the types and installation of updates around the servicing stack in a Fal.Con 2021 webinar.
Regularly Patch and Review Your Mitigation Strategy
A layered security approach with heavy emphasis on tools, programs and solutions that create efficiency and quicken response time is key to organizations’ security posture. Vulnerabilities are found in a wide variety of Microsoft products and platforms, with attackers diligently working on creative ways to access valuable systems and information. Security teams only have so much time in a given day, and the proper use of security solutions and programs can dramatically increase efficiency and responsiveness.This month’s focus on Windows and ESU products underscores the value of a robust mitigation strategy for vulnerabilities that affect organizations’ critical systems where patches are not available.
Security and operations teams need layered security and tools that help prevent, detect and identify vulnerabilities and guide them through their patching and assessment process. A robust mitigation strategy will help reduce areas of opportunity for attackers, helping companies to remain as secure as possible and prevent any potential breach.
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn more about Falcon Identity Protection products and stop workforce identity threats faster.
- Download a copy of the 2021 Global Threat report to learn who and what is affecting your environment.
- Learn about the latest trending threat in Linux and how you can find it.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
















































