In this Microsoft Patch Tuesday update, we discuss several critical vulnerabilities, including a newly released zero-day targeting Internet Explorer that has already seen active exploitation in the wild, and five others that target the backbone of most organizations: DNS.
Organizations should take particular notice of the new Microsoft Exchange vulnerabilities revealed last week, which were so severe that Microsoft likely felt compelled to once again preempt its regular Patch Tuesday cycle to make them public. Mass exploitation in the wild, involving four remote code execution vulnerabilities used by an alleged state-sponsored adversary, should make patching these flaws a high priority for any affected organization. The risk may be higher for those that rely heavily on Microsoft Defender, which has recently been subject to numerous related critical vulnerabilities. In addition, Microsoft cites numerous AV exclusions that could further impact Exchange Server risk. Although the security fixes for older and out-of-support versions of Microsoft Exchange Server were released by Microsoft prior to the Patch Tuesday update, we’ll cover some important additional details in this roundup. Let's get started.
New Patches for 89 Vulnerabilities
This month’s Patch Tuesday updates include fixes for 82 vulnerabilities. Combined with the seven vulnerabilities patched for Microsoft Exchange Server released earlier this month, we have a total of 89 new CVEs with patch updates offered by Microsoft.
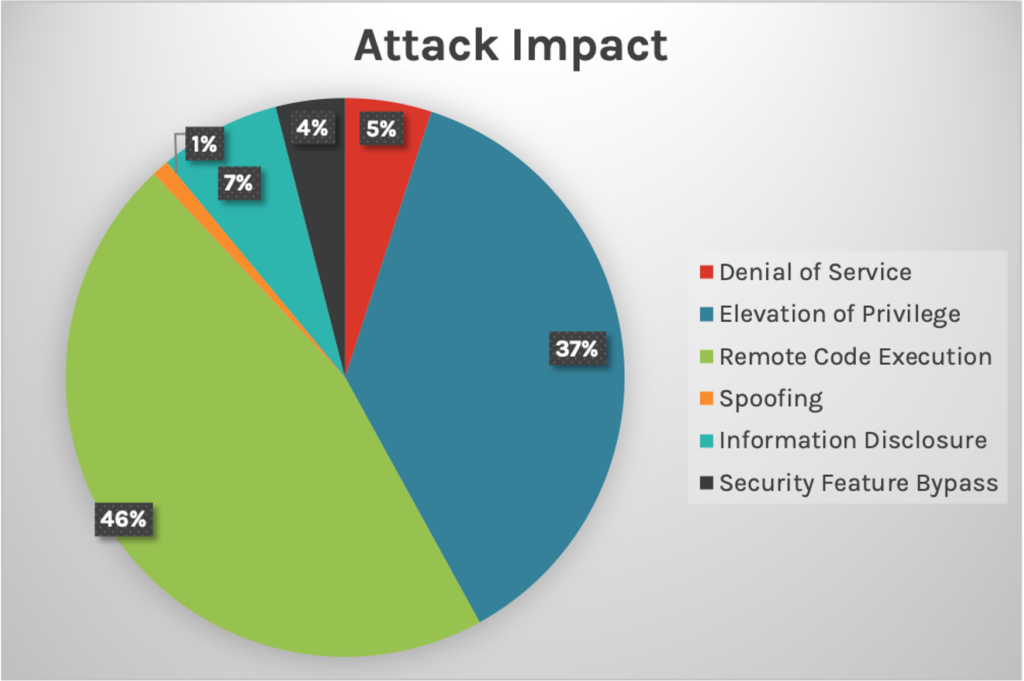 Figure 1. Breakdown of March’s Patch Tuesday attack impact
Figure 1. Breakdown of March’s Patch Tuesday attack impactZero-Day Vulnerability: Internet Explorer Memory Corruption Vulnerability Exploited in the Wild
CVE-2021-26411, a critical zero-day memory corruption vulnerability within Internet Explorer, has seen active exploitation in the wild. This vulnerability has a CVSS v3.0 base score of 8.8 out of 10, indicating high severity (for an explanation of CVSS scores, see the end of this blog post). The successful exploitation of this vulnerability would require user interaction after enticing the victim to visit a specially crafted website. Alternatively, the attacker could inject malicious code into a legitimate website. Once exploited, the attacker could gain the same operating system permissions as the user visiting the website. This attack method could be especially dangerous if you’re an admin browsing a website with malicious code — it would provide the attacker with admin-level privileges to files and operating systems.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2021-26411 | Internet Explorer Memory Corruption Vulnerability |
Windows DNS Server Remote Code Execution Vulnerability Updates
Remotely exploitable DNS vulnerabilities are an effective avenue for worms to spread quickly and effectively. Many organizations rely heavily on Windows-based DNS servers, so updating these vulnerabilities are critical in creating a safe environment.
Another five Windows DNS Server RCE vulnerabilities have been patched this month, including:
- CVE-2021-26897
- CVE-2021-26877
- CVE-2021-26893
- CVE-2021-26894
- CVE-2021-26895
These CVEs all have a high CVSS base score of 9.8. Another recent vulnerability that affected the Windows DNS server was known as SIGRED, referenced by CVE-2020-1350 and patched back in July 2020.
Please note that CVE-2021-24078 is only exploitable if the server is configured to be a DNS server.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2021-26897 | Windows DNS Server Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-26877 | Windows DNS Server Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-26893 | Windows DNS Server Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-26894 | Windows DNS Server Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-26895 | Windows DNS Server Remote Code Execution Vulnerability |
Other critical vulnerabilities to consider:
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2021-21300 | Git for Visual Studio Remote Code Execution Vulnerability |
| Critical | 9.9 | CVE-2021-26867 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-26876 | OpenType Font Parsing Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-26902 | HEVC Video Extensions Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-27061 | HEVC Video Extensions Remote Code Execution Vulnerability |
| Critical | 6.2 | CVE-2021-27074 | Azure Sphere Unsigned Code Execution Vulnerability |
| Critical | 6.8 | CVE-2021-27075 | Azure Virtual Machine Information Disclosure Vulnerability |
| Critical | 9.3 | CVE-2021-27080 | Azure Sphere Unsigned Code Execution Vulnerability |
More on Microsoft Exchange Server Critical Vulnerabilities
A total of seven remote code execution vulnerabilities affecting Microsoft Exchange server — including the four vulnerabilities being exploited actively by an alleged nation-state-sponsored actor — were disclosed before this month’s Microsoft Patch Tuesday update due to their impact and active exploitation. Learn what recommendations the Falcon Complete team offers to help stop a breach occurring from these vulnerabilities. Microsoft has recently released a guide with updated, temporary mitigation actions for those organizations that cannot fully patch and remediate the reported vulnerabilities. According to the information being shared by the Microsoft Security Response Center (MSRC) team, mitigations apply to Exchange server 2013, 2016, and 2019; however, these temporary measures might not prevent all potential avenues for attackers. The Microsoft Exchange team has released an out-of-band security update for an older and unsupported version of Microsoft Exchange server. Guidelines were provided along with recommendations for companies using older versions missing appropriate security fixes.
CrowdStrike enables organizations to protect themselves against attacks exploiting vulnerabilities like these.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.1 | CVE-2021-26412 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 6.6 | CVE-2021-26854 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 9.1 | CVE-2021-26855 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-26857 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-26858 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-27065 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 9.1 | CVE-2021-27078 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
















































