By integrating Amazon EventBridge with CrowdStrike Falcon® Horizon™ cloud security posture management, CrowdStrike has developed a cloud-based solution that allows you to detect threats in real time. This solution uses AWS CloudTrail and EventBridge — CloudTrail allows governance, compliance, operational auditing and risk auditing of your AWS account, and EventBridge is a serverless event bus that makes it easier to build event-driven applications at scale. In this blog post, we’ll cover the challenges presented by using traditional log file-based security monitoring. We will also discuss how CrowdStrike used EventBridge to create an innovative cloud security solution that enables high-speed, event-driven alerts detecting malicious actors in real time.
Challenge of Log File-based Security Monitoring
Being able to detect malicious actors in your environment is a necessity to stay secure in the cloud. With the growing volume, velocity, and variety of cloud logs, log file-based monitoring makes it difficult to reveal adverse behaviors in time to stop breaches. When an attack is in progress, a security operations center (SOC) analyst has an average of one minute to detect the threat, 10 minutes to understand it and 60 minutes to contain it. If you cannot meet this 1/10/60 minute rule, you may have a costly breach that may move laterally and explode exponentially across the cloud estate.
A Real-life Example
Let’s look at a real-life scenario. When a malicious actor attempts a ransom attack that targets high-value data in an Amazon S3 bucket, it can involve activities in various parts of the cloud services in a brief time window. These example activities can involve:
- IAM: account enumeration, disabling multifactor authentication (MFA), account hijacking, privilege escalation, etc.
- Amazon Elastic Compute Cloud (Amazon EC2): instance profile privilege escalation, file exchange tool installs, etc.
- Amazon S3: bucket and object enumeration; impair bucket encryption and versioning; bucket policy manipulation; getObject, putObject, and deleteObject APIs, etc.
With siloed log file-based monitoring, detecting, understanding, and containing ransom attack while still meeting the 1/10/60 rule is difficult. This is because log files are written in batches and files are typically only created every five minutes. Once the log file is written, it still needs to be fetched and processed. This means that you lose the ability to dynamically correlate disparate activities.
To summarize, top-level challenges of log file-based monitoring are:
- Lag time between the breach and the detection
- Inability to correlate disparate activities to reveal sophisticated attack patterns
- Frequent false positive alarms that obscure true positives
- High operational cost of log file synchronizations and reprocessing
- Log analysis tool maintenance for fast-growing log volume
Indicators of Attack by CrowdStrike with Amazon EventBridge
In real-world cloud breach scenarios, timeliness of observation, detection and remediation is critical. CrowdStrike Falcon® Horizon IOAs, with their event-driven architecture based on EventBridge, are able to operate at a velocity where they can outpace attackers. IOAs from CrowdStrike Falcon® Horizon perform the following core actions:
- Observe: EventBridge streams CloudTrail log files across accounts to the CrowdStrike Falcon® platform as the activity occurs. Parallelism is enabled via event bus rules, which enables CrowdStrike to avoid the five-minute lag in fetching the log files and dynamically correlate disparate activities. The Falcon platform observes end-to-end activities from AWS services and infrastructure hosted in the accounts protected by CrowdStrike.
- Detect: Falcon Horizon invokes IOA detection algorithms that reveal adversarial or anomalous activities from the log file streams. It correlates new and historical events in real time while enriching the events with CrowdStrike threat intelligence data. Each IOA is prioritized by the likelihood of activity being malicious via scoring and mapped to the MITRE ATT&CK® framework.
- Remediate: The detected IOA is presented with remediation steps. Depending on the score, applying the remediations in a timely manner can be critical before the attack spreads.
- Prevent: Unremediated insecure configurations are revealed via indicators of misconfiguration (IOMs) in Falcon Horizon. Applying the remediation steps from IOMs can prevent future breaches.
Key differentiators of IOAs from Falcon Horizon are:
- Observability of wider attack surfaces with heterogeneous event sources
- Detection of sophisticated tactics, techniques and procedures (TTPs) with dynamic event correlation
- Event enrichment with threat intel that aids prioritization and reduces alert fatigue
- Low latency between malicious activity occurrence and corresponding detection
- Insight into attacks for each adversarial event from MITRE ATT&CK framework
High-level Architecture
Event-driven architectures provide advantages for integrating varied systems over legacy log file-based approaches. For securing cloud attack surfaces against the ever-evolving TTPs, a robust event-driven architecture at scale becomes a key differentiator. CrowdStrike maximizes the advantages of event-driven architecture by integrating with EventBridge. EventBridge allows observing CloudTrail logs in event streams. It also simplifies log centralization from a number of accounts with its direct source-to-target integration across accounts.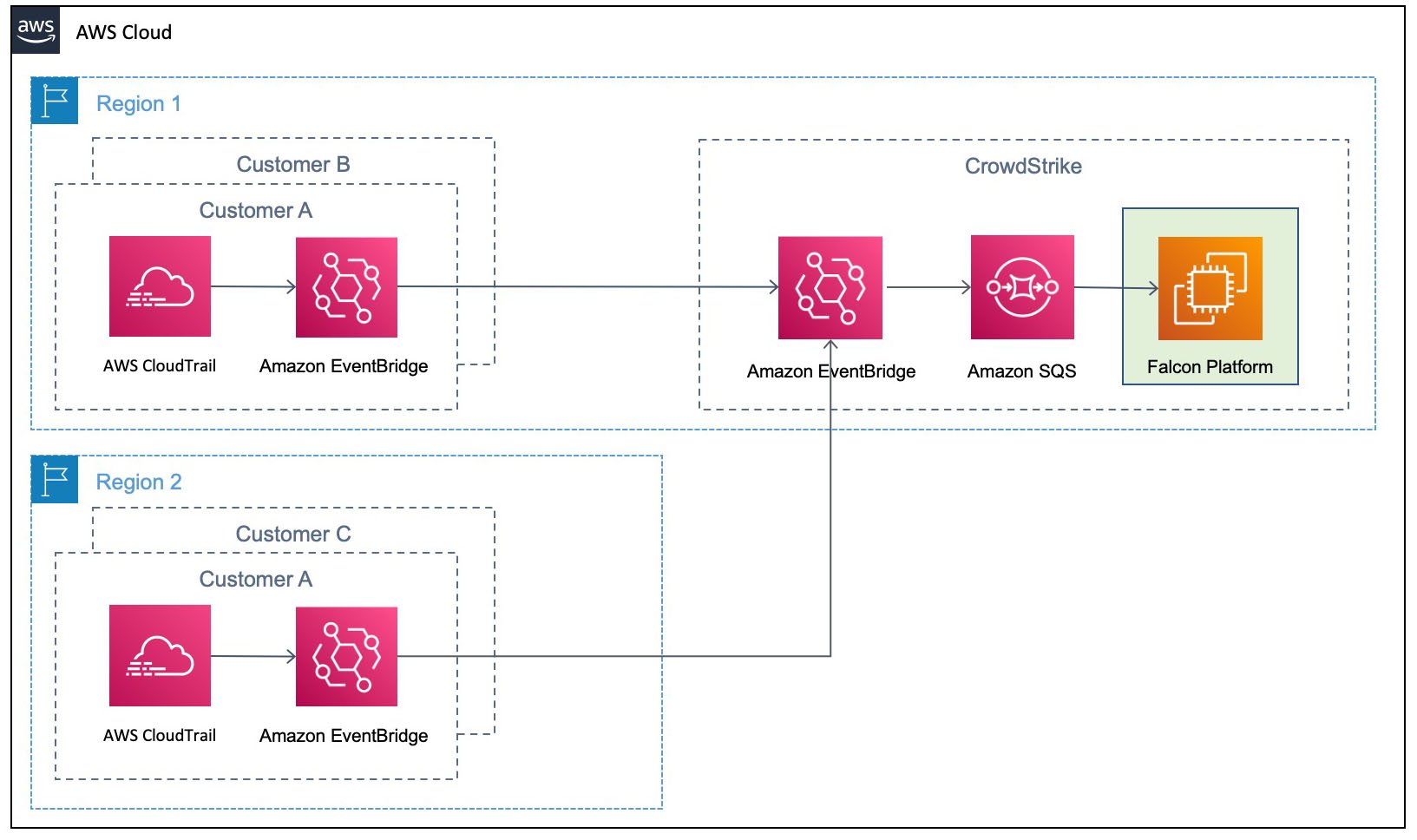
- CrowdStrike hosts an EventBridge with central event buses that consume the stream of CloudTrail log events from a multitude of customer AWS accounts.
- Within customer accounts, EventBridge rules listen to the local CloudTrail and stream each activity as an event to the centralized EventBridge hosted by CrowdStrike.
- CrowdStrike’s event-driven Falcon platform detects adversarial behaviors from the event streams in real time. The detection is performed against incoming events in conjunction with historical events. The context that comes from connecting new and historical events minimizes false positives and improves alert efficacy.
- Events are enriched with CrowdStrike threat intelligence data that provides additional insight of the attack to SOC analysts and incident responders.
As data is received by the centralized EventBridge, CrowdStrike relies on unique customer ID and region in each event to provide integrity and isolation. EventBridge allows hassle-free customer onboarding by using cross-account rules to allow the transfer of customer CloudTrail data into one common event bus that can then be used to filter and selectively forward the data into the Falcon Horizon platform for real-time IOA detections and remediations.
Conclusion
As your organization’s cloud footprint grows, visibility into end-to-end activities in a timely manner is critical for maintaining a safe environment for your business to operate. EventBridge allows event-driven monitoring of CloudTrail logs at scale. CrowdStrike Falcon® Horizon IOAs powered by Amazon EventBridge observe end-to-end cloud activities at high speeds at scale. Paired with targeted detection algorithms from in-house threat detection experts and threat intelligence data, Falcon Horizon IOAs combat emerging threats against the cloud control plane with a cutting-edge event-driven architecture.
Additional Resources
- Learn more about Falcon Horizon cloud security posture management.
- Learn more about Amazon EventBridge and AWS CloudTrail.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.
About the Authors
Arlene Watson is a CrowdStrike technology leader for cloud security, including Falcon Horizon and Falcon Discover™ for Cloud. She has extensive experience and background in cloud security, threat intelligence, IR and vulnerability detections. Arlene is an active advocate of digital transformation, providing strategic direction and thought leadership on public cloud security and stopping breaches in the cloud. Joby Bett is a Sr. Technical Account Manager at AWS based in Orange County, CA. He works with ISV Enterprise customers, providing advocacy and strategic technical guidance to help plan and build solutions using AWS best practices. Outside of work, he likes to spend time with his family, go camping and explore the undersea world scuba diving. Vinodh Krishnamoorthy is a Sr. Technical Account Manager currently supporting AWS Enterprise customers’ creative and transformative spirit of innovation across all technologies —
including Compute, Storage, Database, BigData, Application-level services, Networking, Serverless and more — providing advocacy and strategic technical guidance to help plan and build solutions using best practices, and proactively keep customers’ AWS environments operationally healthy.
 Arlene Watson (CrowdStrike), Joby Bett (AWS), Vinodh Krishnamoorthy (AWS)
Arlene Watson (CrowdStrike), Joby Bett (AWS), Vinodh Krishnamoorthy (AWS)




![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
















































