This blog was originally published on September 18, 2020.
On August 11, 2020 Microsoft released a security update including a patch for a critical vulnerability in the NETLOGON protocol (CVE-2020-1472) discovered by Secura researchers. Since no initial technical details were published, the CVE in the security update failed to receive much attention, even though it received a maximum CVSS score of 10. After analyzing Secura’s vulnerability whitepaper and the exploit that was released, we believe this is the most critical Active Directory vulnerability discovered this year. Its severity is equivalent to that of MS-14-068 (Forged-PAC). This vulnerability allows an unauthenticated attacker with network access to a domain controller, to establish a vulnerable Netlogon session and eventually gain domain administrator privileges. The vulnerability is especially severe since the only requirement for a successful exploit is the ability to establish a connection with a domain controller.
Technical Details Overview
The core of the vulnerability lies in a poor implementation of the ComputeNetlogonCredential call of the Netlogon Remote Protocol (MS-NRPC). The ComputeNetlogonCredential takes an 8-byte challenge as an input, performs a cryptographic transformation using a session key (which proves knowledge of the computer secret), and outputs an 8-byte result. The issue lies in an implementation flaw in the newer method AES-CFB8 (which is also the only one allowed in newer Windows versions) which is used to perform this transformation.
In order to use AES-CFB8 securely, a random initialization vector (IV) needs to be generated for every plaintext to be encrypted using the same key. However, the ComputeNetlogonCredential function sets the IV to a fixed value of 16 zero bytes. This results in a cryptographic flaw in which encryption of 8-bytes of zeros could yield a ciphertext of zeros with a probability of 1 in 256. Another implementation issue that allows this attack is that unencrypted Netlogon sessions aren’t rejected by servers (by default). The combination of these two flaws could allow an attacker to completely compromise the authentication, and thus to impersonate a server of their choice.
Exploit Steps Overview
Here is a summary of the exploitation steps:
- Establish an unsecure Netlogon channel against a domain controller by performing a brute-force attack using an 8 zero-bytes challenge and ciphertext, while spoofing the identity of that same domain controller. This would require an average of 256 attempts (given the probability of success being 1 in 256).
- Use the NetrServerPasswordSet2 call to set the domain controller account’s password, as stored in Active Directory, to an empty one. This breaks some of the domain controller functionality, since the password stored in the domain controller’s registry does not change (this is the reason step four noted below is taken).
- Use the empty password to connect to that same domain controller and dump additional hashes using the Domain Replication Service (DRS) protocol.
- Revert the domain controller password to the original one as stored in the local registry to avoid detection.
- Use the hashes dumped from stage 3 to perform any desired attack such as Golden Ticket or pass the hash using domain administrator credentials.
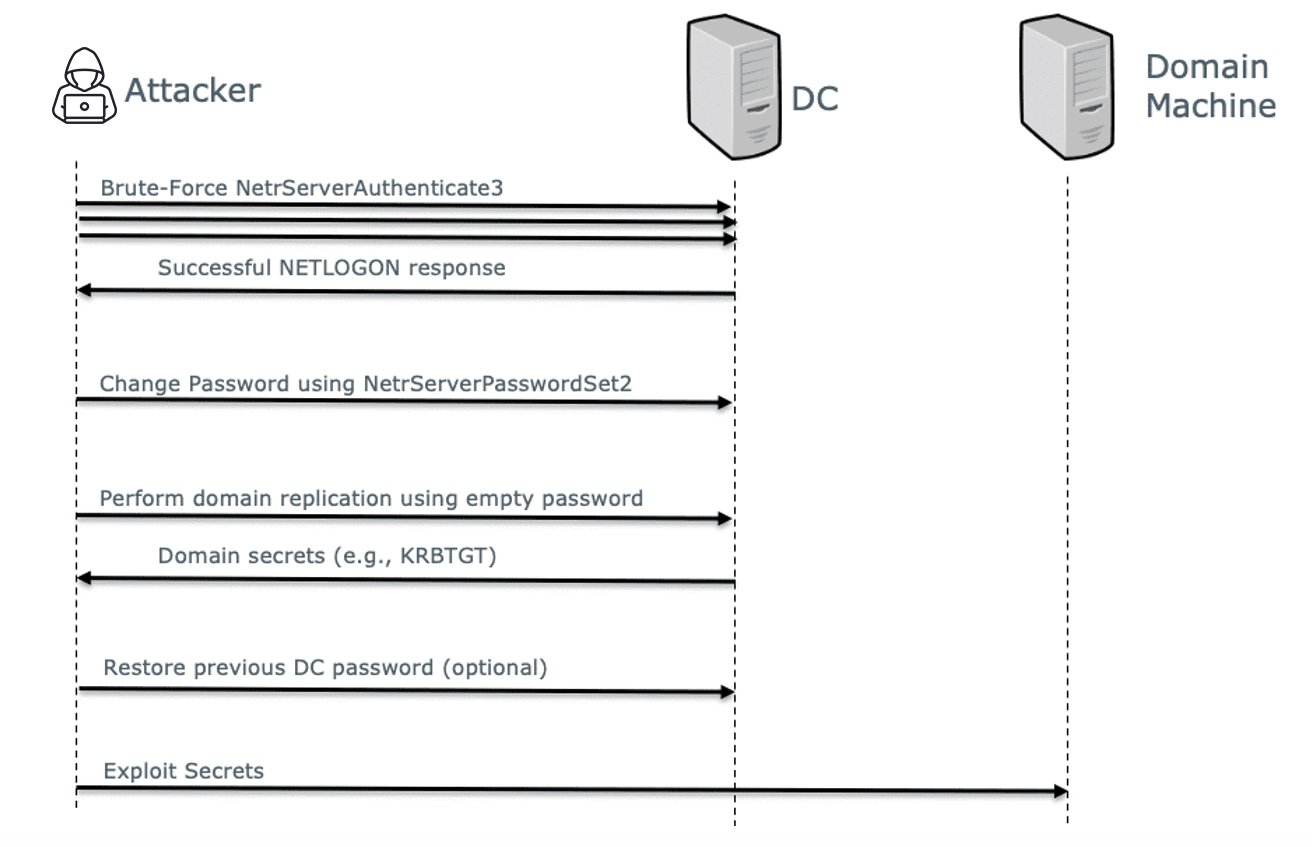 Figure 1 – Flow of ZeroLogon (CVE-20120-1472) Attack
Figure 1 – Flow of ZeroLogon (CVE-20120-1472) AttackThere are various scripts online which can be used to detect and exploit this vulnerability, including:
- https://github.com/SecuraBV/CVE-2020-1472 – this script discovers vulnerable domain controllers without modifying the password.
- https://github.com/dirkjanm/CVE-2020-1472 by @dirkjan – which includes an actual exploit to change (and revert) the domain controller password.
The CrowdStrike Falcon®® Zero Trust and Falcon Identity Threat Detection products can both detect Zerologon traffic. Both products involve placing a sensor on the Domain Controller and viewing live authentication traffic. Additionally, Zerologon can be wrapped into the Mimikatz toolkit, which is also detected. Falcon Zero Trust offers the ability to challenge these attacks via step-up authentication.
Patch Details and Remaining Issues
Microsoft has applied two fixes to mitigate this attack. The first mitigation is to reject NetrServerAuthenticate3 requests in which the first five bytes are identical. Our analysis shows that this still allows for longer brute-force attacks (requiring an average of 2^32 attempts). The second mitigation is to reject Netlogon channels that are not signed/sealed for all Windows computer accounts. This will completely mitigate the attack even if brute force is possible. Since, Windows Netlogon clients always seal Netlogon messages there shouldn’t be any problem. But, Microsoft took the conservative approach and still allowed unsigned Netlogon sessions for non-Windows computer accounts. This means that, in theory, non-Windows computer accounts are still vulnerable. Microsoft is planning an additional patch in February that will also reject insecure Netlogon sessions from non-Windows devices.
How to Protect Your Network
- Patch. Apply the relevant Microsoft patch as quickly as possible!
- Proactively close patch gaps. Non-Windows machines are still somewhat unprotected from ZeroLogon. Search your network for non-Windows computer accounts with elevated privileges (e.g. domain replication privileges) as these could be used to launch a successful ZeroLogon attack even on patched domain controllers. (Falcon Zero Trust can provide you with a complete list of privileged accounts.)
- If you cannot patch for any reason:
- An attacker exploiting the vulnerability effectively gets privileged access to a domain controller. Using this access, the attacker can harvest credentials and then perform one of the following attacks:
- Golden Ticket attack
- Pass-the-Hash attack
- Silver Ticket attack
- Falcon Zero Trust can prevent these attacks via enforced step-up authentication.
- To mitigate further damage, ensure you are monitoring your environment against such attacks:
- Enable multi-factor authentication (MFA) for all accounts or at least privileged accounts. In that case, even if a privileged account is compromised, the access attempt would still be denied.
- Monitor for possible exploitation attempts with the open-source tool released by CrowdStrike (formerly Preempt).
How CrowdStrike Can Help
- CrowdStrike monitors the network and detects (via CrowdStrike Falcon® identity threat detection) and mitigates (via Falcon Zero Trust) various attacks against the domain controller such as Golden Ticket and Pass-the-Hash.
- CrowdStrike Falcon® Zero Trust can apply MFA to service accounts (including the domain controller admin account) using a comprehensive policy engine. Any user with MFA enabled on the Falcon platform will not be compromised even if the attacker was able to exploit ZeroLogon and steal the user account credentials from the DC.
- Falcon Zero Trust uses advanced analytics and patented machine learning technology to uncover reconnaissance (e.g. LDAP, BloodHound, SharpHound, credential scanning), lateral movement (e.g. RDP, mimikatz tool/Zerologon exploits, unusual endpoint usage, unusual service logins, etc), and persistence (e.g. Golden Ticket attack, hidden objects, privilege escalations).
Additional Resources
- Learn more by reading a white paper, “Disrupting the Cyber Kill Chain: How to Contain Use of Tools and Protocols.”
- Request a demo of CrowdStrike Falcon® Zero Trust or Falcon Identity Threat Detection products.
- Visit the CrowdStrike Falcon® Identity Protection solutions webpage.
- Read expert insights and analysis on other complex threats — download the CrowdStrike 2020 Global Threat Report.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































