Today’s adversaries are moving faster than ever. With the quickest attacks happening in just 7 minutes, adversaries are compromising endpoints and moving laterally before security teams can respond.1 It’s critical for organizations to have the technology to stay ahead of them.
The mission of XDR is simple: Extend detection and response beyond the endpoint to deliver faster, more comprehensive visibility and response to stop breaches. The AI-native CrowdStrike Falcon® XDR platform has continually been on the forefront of defining XDR, and today marks one of the most significant moments since the introduction of the category itself: We are making native XDR available at no additional cost to all customers of CrowdStrike Falcon Insight XDR that have at least one additional supported Falcon module.*
We believe security teams deserve every edge possible in the fight to stop adversaries. Making native XDR available for free to over 23,000 customers is a significant step forward in our mission to deliver a unified, modern approach to cybersecurity that reduces complexity and cost, saves time and stops breaches.
How it works: Once upgraded to the Raptor platform release, Falcon Insight XDR customers with additional supported modules automatically gain access to native XDR and can dramatically accelerate investigations with unified context across CrowdStrike’s industry-leading endpoint, identity, cloud, mobile and data protection** offerings — without the need to buy or deploy anything else. It’s the same pioneering native XDR that CrowdStrike has always delivered, now available at no additional cost. Beyond CrowdStrike’s native data sources, customers can expand their visibility by ingesting third-party data as part of our open XDR and next-generation SIEM capabilities if they choose.
Extending detection and response beyond the endpoint is critical to stop today’s sophisticated adversaries. Advanced attackers seek to weaponize organizations’ technological complexity against them, moving laterally across environments and hiding within the cracks of IT infrastructure. Without comprehensive visibility across data sources, security teams are left with blind spots that attackers can exploit.
Modern attackers often harvest and use valid credentials to breach their targets, mask their activity and evade detection. In order to maximize protection, it's critical to have continuous visibility from EDR tools as well as other sources of telemetry, including identity data. Let’s see how native XDR helps broaden investigation and response across the CrowdStrike Falcon platform to stop an adversary.
Native XDR in Action
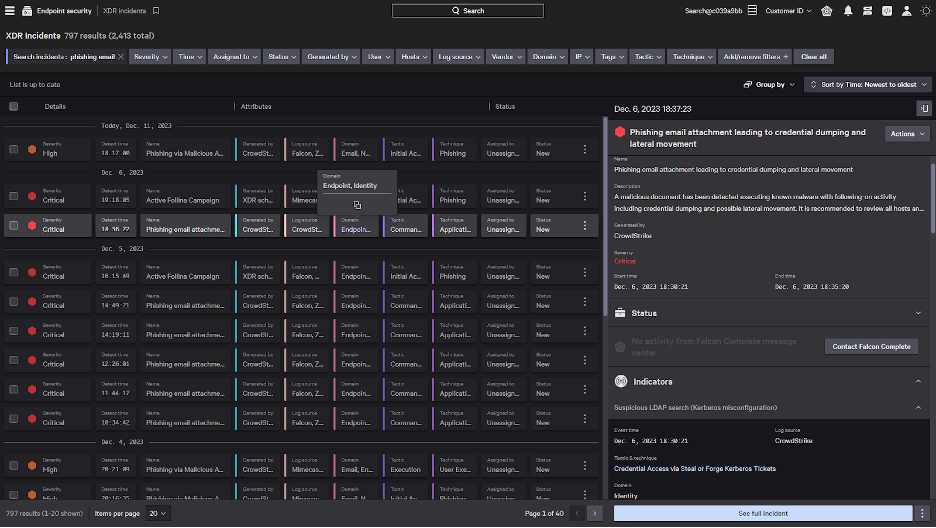
Native XDR detections can include data from endpoints and other Falcon modules across identity, cloud and data protection. For this example, we will focus on an XDR detection that extends our comprehensive endpoint visibility with data from CrowdStrike Falcon® Identity Protection. Rather than sift through individual endpoint or identity alerts, Falcon Insight XDR has unified this telemetry into a single XDR incident to accelerate investigations and provide greater context to a security analyst.
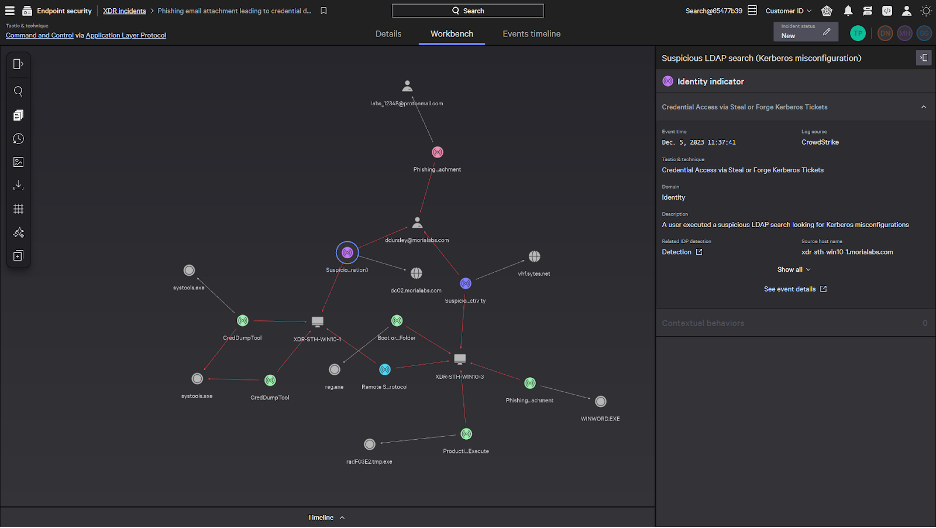
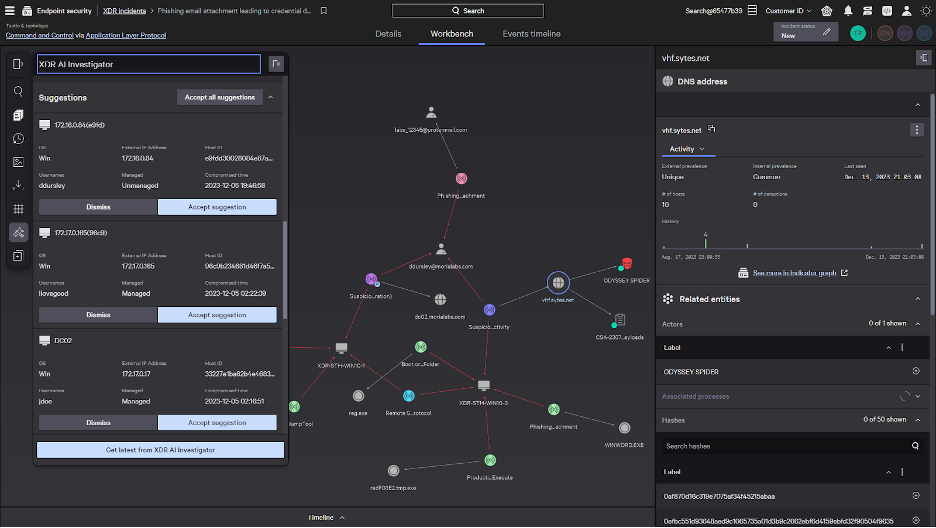
Selecting “See full incident” brings us to the all-new XDR Incident Workbench. Incident Workbench offers a unified investigation experience with simplified threat hunting workflows across the Falcon platform, including centralized insights from any data source, multi-user collaboration on incidents, and automated enrichment and remediation to simplify security operations. As part of Incident Workbench, analysts can use the XDR incident graph to easily see the full picture of an attack across every related entity, including information from all data sources across the Falcon platform — which can take hours to manually build with traditional approaches. From this view, it’s easy to see this incident began on the endpoint with a phishing email containing a malicious attachment.
In addition to this endpoint activity, the platform’s native XDR automatically correlates suspicious user behavior from Falcon Identity Protection, providing context needed to understand and respond across endpoint and identity. Not only did the user attempt to dump credentials, it’s also clear a suspicious search was executed to look for domain controller misconfigurations to exploit. This unusual behavior was automatically detected by Falcon Identity Protection, which is available as part of the unified XDR incident graph.
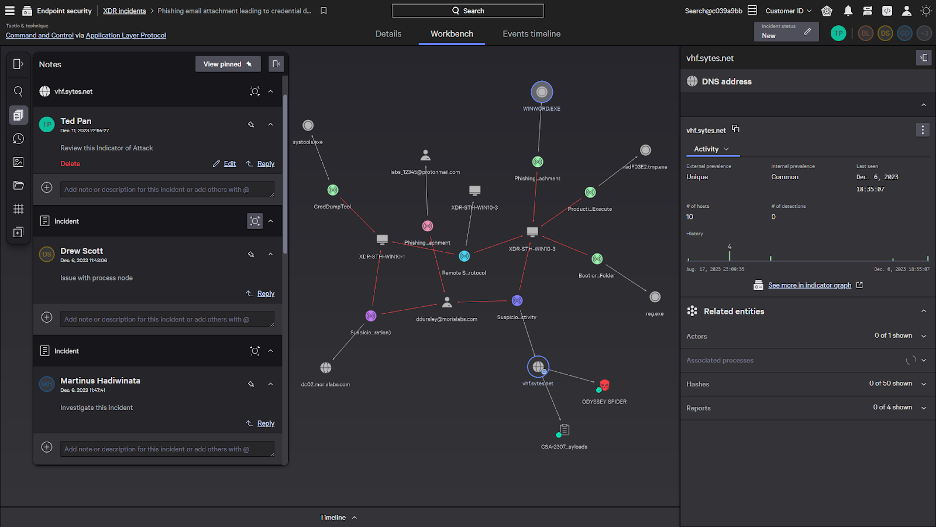
As part of the XDR Incident Workbench, customers can use the Collaborative Command Center to work together in real time from anywhere in the world to stop adversaries. Analysts can easily add a comment and tag a team member to review the incident and rapidly add context. All changes made by an analyst, such as adding or removing objects from the graph, are immediately visible to everyone collaborating on the incident to ensure a coordinated response.
Investigating Incidents with Integrated AI
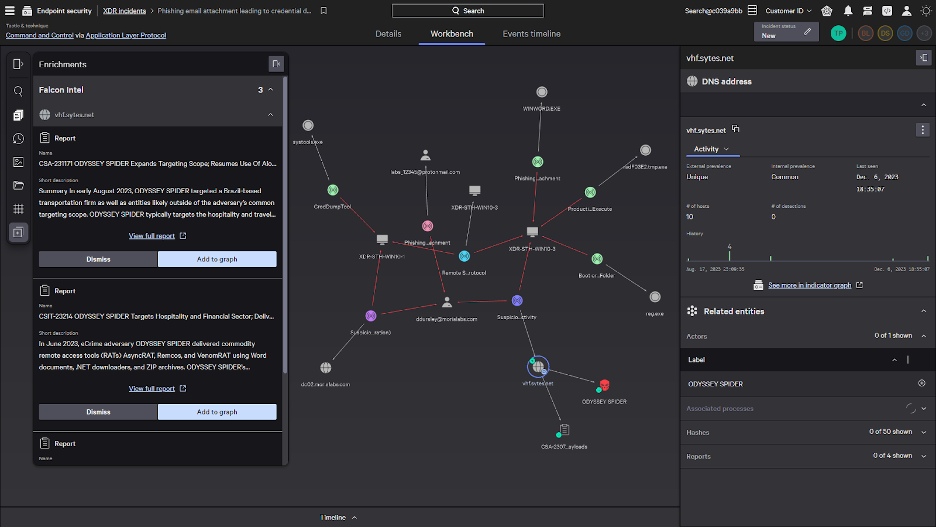
The Falcon platform offers world-class adversary intelligence at your fingertips, directly integrated throughout the console. To gain deeper insight into the attacker behind the threat, you can easily add recommended adversary context for an indicator of compromise (IOC) in the graph. With this, analysts can instantly identify the adversary and their tradecraft without requiring multiple consoles or third-party tools.
To ensure you understand the full scope of the incident, you can leverage the new XDR AI Investigator, which is part of the Raptor release and currently available in private customer preview. Starting with a single asset or event within an incident, XDR AI Investigator automatically correlates additional related context and generates an easy-to-understand summary. In this case, XDR AI Investigator has identified another unmanaged endpoint that has been accessed by the same suspicious user credentials. With one click, you can add this affected endpoint to the same incident. Analysts of all skill levels can harness the power of AI to accelerate workflows and reduce the time it takes to investigate and respond to incidents.
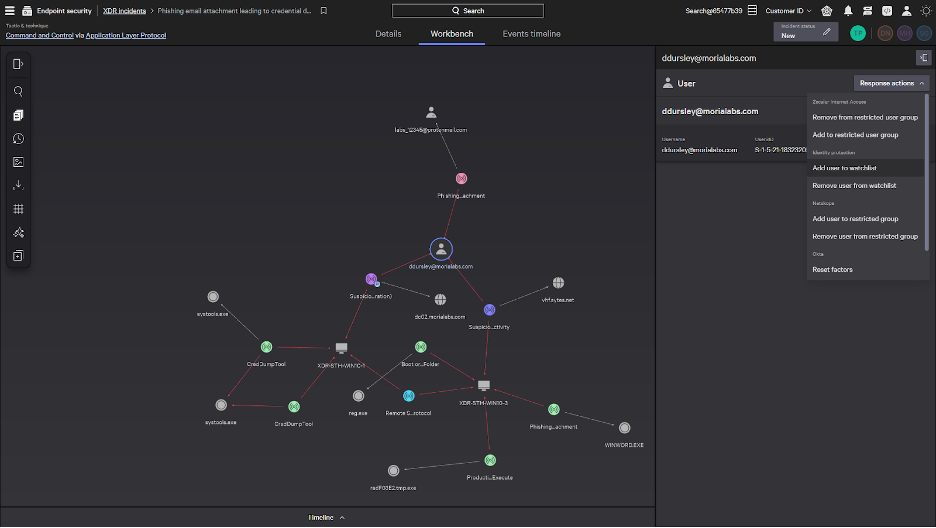
Now, it’s time to respond. With native XDR capabilities, you can quickly and easily implement unified response actions across endpoint and identity domains, directly from the Falcon Insight XDR console. Actions may include adding a user to a watchlist to enforce stronger authentication protocols, isolating affected endpoints from the network to contain the threat and prevent lateral movement, or remotely connecting to affected systems to collect additional information, kill processes or run custom scripts. Analysts can scale and automate response actions across even the largest environments with Falcon Fusion, CrowdStrike’s native security automation capabilities, which is available to all customers at no cost.
CrowdStrike is revolutionizing cybersecurity with faster and more comprehensive detections through native XDR, now available to all Falcon Insight XDR customers with an additional supported Falcon module, at no additional cost. By incorporating XDR as a fundamental capability of the Falcon platform, organizations of all sizes and across all industries can extend detection beyond the endpoint to include an expanding list of native data sources. Customers can use the full depth and breadth of CrowdStrike telemetry, together with innovative AI advancements, to achieve the speed needed to outpace today’s most sophisticated adversaries.
1CrowdStrike 2023 Threat Hunting Report
*Once upgraded to the Raptor release, all new and existing Falcon Insight XDR customers will be automatically provisioned with native XDR functionality if they have one or more of the following additional supported modules: Falcon Identity Protection, Falcon Cloud Security, Falcon for Mobile and/or Falcon Data Protection.
**Available Q1 2024
Additional Resources
- Stop breaches with pioneering detection and response across key attack surfaces.
- Read the white paper, “Designing XDR with Industry-Leading Solutions for Your Organization.”
- See the Raptor release in action.
- Get hands-on and test drive the Falcon platform now.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)