The third round of the MITRE Engenuity ATT&CK® Evaluation program has been released, highlighting once again that CrowdStrike customers are protected in the face of adversaries operating in the real world. The CrowdStrike Falcon® platform provided actionable alerts on each of the 20 steps of the evaluation, intelligently identifying key attack activity while eliminating alert fatigue.Smart Prioritization and the Elimination of Alert Fatigue
Which product would you rather use? One that presents all of the key data with workflows at your fingertips to stop breaches, or one that makes you sift through hunting interfaces, raw events and spurious alerts in an effort to catch the attacker? Past solutions such as SIEM have shown large numbers of alerts do not drive sustainable security for an organization that sees hundreds of attacks each day. We’d much rather stop breaches.
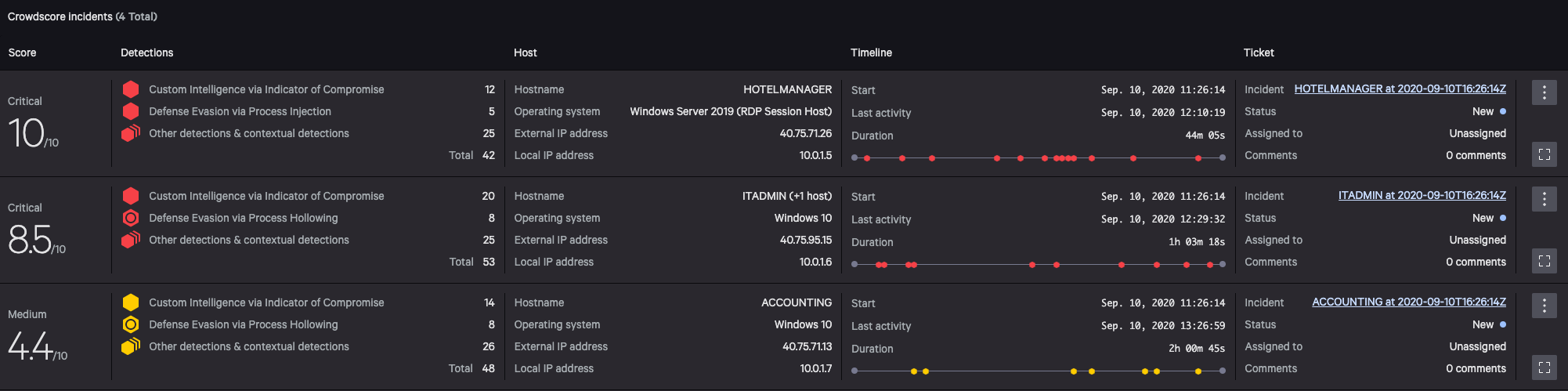
Working in the real world means finding the threat quickly, being able to identify and understand it in minutes and being able to contain the attack before the adversary can break out into your network and achieve their objectives. This means a SOC analyst doesn’t have valuable time to spend hunting through the data to see techniques and identify that a behavior is malicious. This is why Falcon’s CrowdScore™ detection engine is so revolutionary.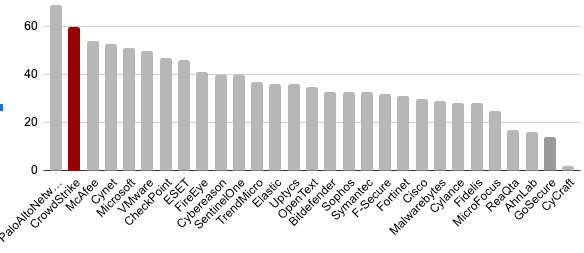 Figure 3. Number of detection steps where more than two data distinct sources were used
Comprehensive also means covering multiple platforms, and CrowdStrike Falcon® is effective for all of the platforms you use. This year, MITRE introduced Linux as an optional component of the test environment, giving participants an opportunity to showcase cross-platform capabilities. MITRE’s Evaluation results show that Falcon detected and prevented lateral movement techniques from Linux and Windows machines involving remote SSH connections to other network machines and services (T1021.004) and SMB protocol abuse (T1021.002), effectively negating bad actors from assessing other targets. MITRE’s Target Assessment is a key step in the attack chain, especially in the adversary emulations on Windows and Linux hosts.
Figure 3. Number of detection steps where more than two data distinct sources were used
Comprehensive also means covering multiple platforms, and CrowdStrike Falcon® is effective for all of the platforms you use. This year, MITRE introduced Linux as an optional component of the test environment, giving participants an opportunity to showcase cross-platform capabilities. MITRE’s Evaluation results show that Falcon detected and prevented lateral movement techniques from Linux and Windows machines involving remote SSH connections to other network machines and services (T1021.004) and SMB protocol abuse (T1021.002), effectively negating bad actors from assessing other targets. MITRE’s Target Assessment is a key step in the attack chain, especially in the adversary emulations on Windows and Linux hosts.
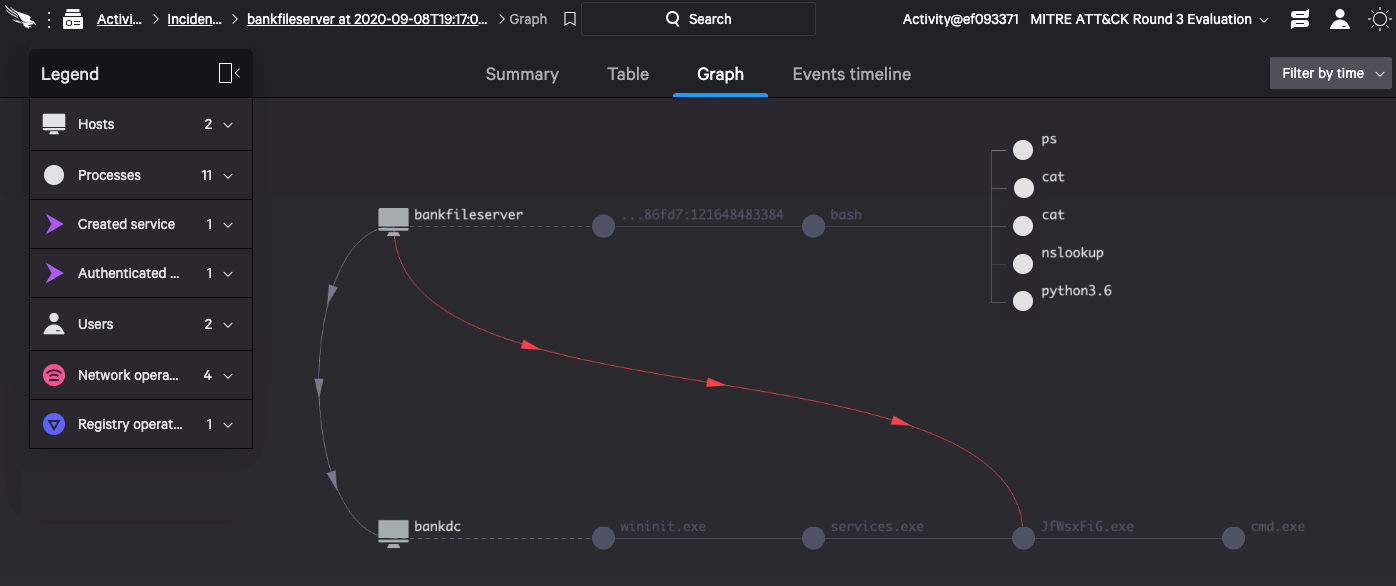 Figure 4. CrowdScore automatically detects and presents cross-platform incidents with lateral movement (Click to enlarge)
Having out-of-the-box capabilities, with no manual intervention, in blocking 100% of these attempts at this step in the attack chain is instrumental in ensuring a strong security posture across all infrastructure environments.
Figure 4. CrowdScore automatically detects and presents cross-platform incidents with lateral movement (Click to enlarge)
Having out-of-the-box capabilities, with no manual intervention, in blocking 100% of these attempts at this step in the attack chain is instrumental in ensuring a strong security posture across all infrastructure environments.
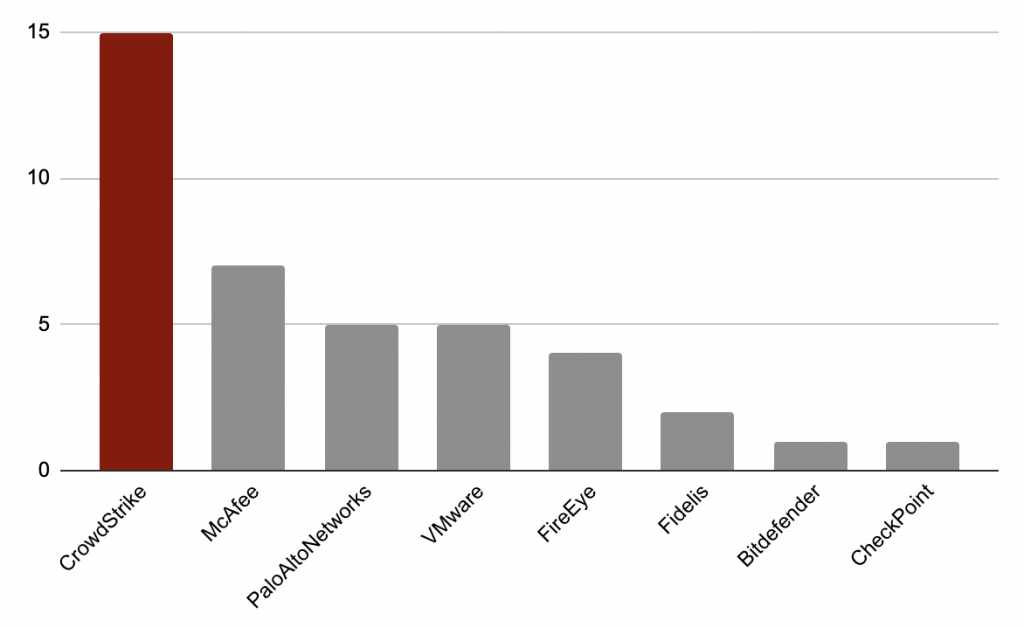 Figure 5. CrowdStrike Falcon® Sandbox™ provided automated intelligence, crucial to understanding current threats and preventing the next one
Figure 5. CrowdStrike Falcon® Sandbox™ provided automated intelligence, crucial to understanding current threats and preventing the next one
This iteration of the evaluation leveraged two sophisticated adversary emulations of Carbanak and FIN7 (CARBON SPIDER) and executed a series of attacks spanning the full ATT&CK matrix, covering 20 separate test steps and 174 test substeps on Linux and Windows operating systems. MITRE’s evaluation gives us a unique opportunity to showcase how CrowdStrike is pioneering solutions to our industry’s biggest challenges: the need for agility, comprehensive visibility and speed. CrowdStrike’s MITRE ATT&CK evaluation results show how the CrowdStrike Falcon® platform prevents breaches using a unique combination of prevention, detections and contextual telemetry, giving defenders full-spectrum protection while reducing the burden on overloaded security teams. CrowdStrike’s achievements in this year’s evaluation include:
- CrowdStrike Falcon® achieved 100% detection coverage across the intrusion stages by providing actionable alerts on each of the 20 steps of the evaluation and all MITRE ATT&CK tactics.
- The Falcon platform prevented simulated intrusions against both threat actors at multiple steps across the MITRE ATT&CK framework.
- The CrowdScore detection engine analyzed relevant indicators of compromise and telemetry, pulling together weak signals to detect highly sophisticated and stealthy adversary tradecraft.
- The Falcon Incident Workbench prioritized and visualized the detected attacks with rich contexts such as ATT&CK tactics and techniques, threat actor intelligence, devices and users. Results were presented as actionable security incidents enriched with deep contextual telemetry — reducing discrete security alerts by 90% and dramatically speeding time-to-respond in a manner that no other vendor could match.
- Falcon provided comprehensive detection by design with visibility into attack behaviors from multiple vantage points, virtually eliminating the adversary’s ability to remain undetected.
MITRE Engenuity’s evaluation methodology is not to pick a winner, it is designed to highlight “how product users could address specific ATT&CK Technique implementations under perfect circumstances with knowledge of what the adversary did and without environmental noise.” Despite MITRE’s methodology, vendors may claim a “win” using various criteria such as most detections or maximum visibility, using siloed test data as their proofpoint. In the real world, knowledge is highly imperfect, and environmental noise, spurious alerting and false positives are a constant drain on limited SOC and IT resources. Success in this challenging landscape is measured simply by the ability to stop real-world breaches. We approached this evaluation with this in mind, and I am proud to say that once again, the CrowdStrike Falcon® platform succeeded in doing just that.
Smart Prioritization and the Elimination of Alert Fatigue
Which product would you rather use? One that presents all of the key data with workflows at your fingertips to stop breaches, or one that makes you sift through hunting interfaces, raw events and spurious alerts in an effort to catch the attacker? Past solutions such as SIEM have shown large numbers of alerts do not drive sustainable security for an organization that sees hundreds of attacks each day. We’d much rather stop breaches.
Working in the real world means finding the threat quickly, being able to identify and understand it in minutes and being able to contain the attack before the adversary can break out into your network and achieve their objectives. This means a SOC analyst doesn’t have valuable time to spend hunting through the data to see techniques and identify that a behavior is malicious. This is why Falcon’s CrowdScore™ detection engine is so revolutionary.
The goal of CrowdScore is simple: Use machine intelligence to find signals in unalerted data and let the Falcon platform detect attackers hiding under the radar so you do not have to. It isn’t detecting a single process or a bad behavior in isolation, or doing simple time-based correlation;
it relies upon having petabytes of relevant behavior telemetry, customer-developed alerts, and strong and weak indicators of potentially malicious activity to accurately identify the probability of this data being a real attack. The proprietary CrowdStrike Threat Graph® is uniquely suited to address this challenge, allowing CrowdScore to detect and elevate unknown attacks in real time to the SOC that may have otherwise gone unnoticed.
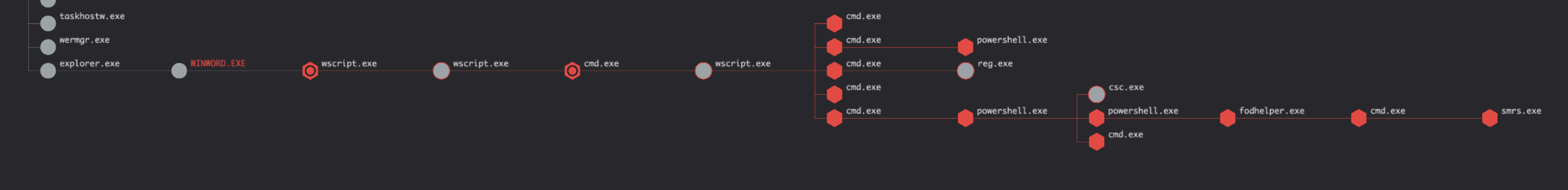
These CrowdScore detections represented a 90% decrease in alerts in the ATT&CK evaluation as well as in the real world. CrowdStrike is constantly pushing boundaries, detecting attackers in new and innovative ways that don’t always align with the tester's scoring methodology. CrowdScore is a great example of an innovative detection technology that changes the game for defenders. Were Falcon configured for prevention, the attack would have been stopped quickly. Configured for detection only (as per the test methodology), CrowdScore quickly identified that an attacker had successfully breached the system using Microsoft Word in a spear-phishing attack that relied on user execution and started building the incident in real time. With CrowdScore, defenders are not required to waste hours trolling through unprioritized data for the information they need to understand the components of a threat. CrowdScore Incident Workbench collects and presents key information to the SOC analyst that allows them to identify, understand and contain the attack quickly. CrowdScore does this so you don’t have to.
Comprehensive Detection by Design
Comprehensive detection starts with very robust data sources and visibility to see many vantage points. Data is not created equally when it comes to endpoint solutions, and the adversary is always trying to evade the defender and the security tools they bring to bear.CrowdStrike understands this, and it is why we leverage multiple sophisticated data sources and we harden them extensively both on the sensor and in the cloud. This makes it harder for the attacker to evade detection by simply renaming a file, changing a command line, performing a simple AMSI bypass, injecting behavior into a legitimate process, or restoring a hooked function. In the ATT&CK evaluation, the Falcon platform demonstrated leadership with most steps having more than two data sources, making Falcon’s detections more robust.
 Figure 3. Number of detection steps where more than two data distinct sources were used
Figure 3. Number of detection steps where more than two data distinct sources were used Figure 4. CrowdScore automatically detects and presents cross-platform incidents with lateral movement (Click to enlarge)
Figure 4. CrowdScore automatically detects and presents cross-platform incidents with lateral movement (Click to enlarge)The X Factor: CrowdStrike Falcon® Intelligence Empowers Teams with Automated Intelligence
The increased sophistication of adversary attack tactics, techniques and tools requires greater visibility and a more detailed analysis of advanced malware. Defeating evasive malware and expanding the effectiveness of the entire security infrastructure can help both empower security teams by having more visibility to make decisions better and faster, and help them drill into the technical details of the threat to understand how to effectively hunt for sophisticated adversaries in the future. During the evaluation, CrowdStrike CROWDSTRIKE FALCON® INTELLIGENCE™, and its powerful, automated sandbox analysis, provided comprehensive visibility and intelligence on adversary activities throughout the attack. CrowdStrike Falcon® Intelligence provided insights covering 15 separate test steps, identifying many techniques including privilege escalation via PowerShell scripts and lateral movement that adversaries look to leverage every day. The outcome of this analysis is not just visibility and detection, but deep intelligence and indicators on the adversary’s tradecraft. That gives defenders the critical intelligence they need to improve defenses, and not only detect but stop a persistent adversary tomorrow. Figure 5. CrowdStrike Falcon® Sandbox™ provided automated intelligence, crucial to understanding current threats and preventing the next one
Figure 5. CrowdStrike Falcon® Sandbox™ provided automated intelligence, crucial to understanding current threats and preventing the next onePower of the Platform
While this test focused on endpoint detection and response, a smart adversary will always try to span multiple attack domains to find the weakest point in the defense to achieve their outcomes. The cloud-native CrowdStrike Falcon® platform was built from Day One to provide defenders with comprehensive visibility across the endpoints and beyond. Falcon combines endpoint protection from Falcon Prevent™ next-gen antivirus and Falcon Insight™ endpoint detection and response with protection for identity (Falcon Identity Protection) and cloud workloads (Falcon Cloud Workload Protection) to empower security analysts with the capability they need to defend their organization against persistent adversaries. The story doesn’t end there. Once an attacker has been stopped, it is critical that the defender must review their security posture and attack surface to reduce the risk of similar attacks. Here the Falcon platform has an excellent capability, whether it is identifying users who need security training, highlighting vulnerabilities with Falcon Spotlight™ or software that could be exploited in the attack with Falcon Discover™, or using our leading intelligence data to understand how the attacker may try again.Relentless Focus on Stopping Breaches
CrowdStrike commits to testing the Falcon platform with a wide range of leading independent testing organizations to provide the necessary transparency on how our capabilities fare in close-to-real-world testing scenarios and provide confidence to our customers that we continue to deliver the best protection available. The results of this test highlight the consistent best-in-class threat detection capabilities of CrowdStrike Falcon®, which are continuously demonstrated in multiple SE Lab Breach Response tests and the AV-Comparatives Endpoint Protection and Response tests where we are named a strategic leader as well.Adversaries don’t stand still, and neither does CrowdStrike. CrowdStrike’s sophisticated detection techniques evolve continuously, as we innovate with new capabilities delivered to identify and stop new and emerging tradecraft. Since we participated in the MITRE ATT&CK evaluation in the summer of 2020, we have added a wide range of features and detection enhancements to protect against known and unknown threats. Through our participation in MITRE Center for Threat-Informed Defense, we remain committed to contributing to the community’s overall understanding of how to build a security program, including how to operationalize ATT&CK.
Through it all, Falcon’s proven agility, comprehensive visibility and speed remain key weapons in our shared battle against sophisticated adversaries. We are proud to once again demonstrate our indisputable leadership in protecting organizations from real-world breaches.
Additional Resources
- Read about recent trends in adversaries’ TTPs in the CrowdStrike 2021 Global Threat Report.
- Learn about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.
- To find out how to incorporate intelligence on threat actors into your security strategy, visit the CROWDSTRIKE FALCON® INTELLIGENCE™ Threat Intelligence page.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)