In this blog you will:
- Learn how to leverage the CrowdStrike Falcon® Spotlight™ integrated threat and vulnerability management module to fuse your endpoint telemetry with CISA's Known Exploited Vulnerabilities Catalog
- Learn how to use the CrowdStrike Falcon®® console to further investigate and take action
The U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Agency (CISA) has been quite busy this year. It recently issued a “Shields Up” advisory, highlighting that “Russia’s invasion of Ukraine could impact organizations both within and beyond the region,” including the threat of malicious activity against U.S. interests and companies. CISA selected CrowdStrike to be a founding partner of its Joint Cyber Defense Collaborative (JCDC) in order to help develop proactive and rapid responses in the face of cyber threats and intrusions. This led to the announcement of the Critical Infrastructure and Defense Program, a joint partnership between CrowdStrike, Cloudflare and Ping Identity.
Most recently, CISA today published a Cybersecurity Advisory (CSA) jointly with the UK, Canada, Australia and New Zealand, warning of Russian state-sponsored and criminal threats to critical infrastructure. This latest CSA builds on the earlier “Shields Up” advisory while demonstrating that the JCDC is working and already effective.
CrowdStrike’s commitment to threat intelligence, finding adversaries in the wild, and making use of this data to enable us and our customers to defend themselves is second to none. In some cases, this threat intelligence and industry and government collaboration can lead to identifying new vulnerabilities or increasing the priority of previously disclosed common vulnerabilities and exposures (CVEs).
Somewhat less talked about in all this progress is CISA’s Known Exploited Vulnerabilities Catalog, a list of CVEs that CISA has prioritized based on observed active exploitation in the wild. This indicates a much greater relevance and urgency in mitigating, as these CVEs could indicate a nation-state-level attack. Although CISA mandates the patching of these vulnerabilities for the federal executive branch, all organizations should consider following this guidance. This is especially true for those in the Defense Industrial Base (DIB), healthcare, water, energy and other sectors that are part of critical infrastructure.
Thanks to Falcon Spotlight’s Expert Prediction Rating Artificial Intelligence (ExPRT.AI) feature, which we will double-click on shortly, all CVEs in CISA’s Known Exploited Vulnerabilities Catalog are prioritized and assigned a critical rating This data source is one of many that CrowdStrike taps into, including its own threat intelligence.
Enter CrowdStrike Falcon® Spotlight
As CrowdStrike expands its customer base within the U.S. government, accelerated by new authorizations of its cloud services, customers have been asking how they can assess against the CISA Known Exploited Vulnerabilities Catalog. With Falcon Spotlight, CrowdStrike’s integrated threat and vulnerability management solution, we can easily assess an environment’s exposure to vulnerabilities in CISA’s catalog, both in the Falcon console as well as programmatically via APIs.
Falcon Spotlight's CVE data integrates the CISA Known Exploited Vulnerabilities Catalog out of the box, requiring no extra configuration or manual effort. Spotlight collects endpoint vulnerability data through the same single lightweight agent that powers CrowdStrike's entire suite of endpoint security offerings, allowing customers to reap the benefits without any additional software deployment, overhead, reboots or scans. This scanfree solution provides visibility in near real time and also takes in data from additional data sources, prioritizing vulnerabilities via Falcon Spotlight ExPRT.AI, an advanced artificial intelligence (AI) model that produces greater accuracy and value by prioritizing what’s most important to customers.
CrowdStrike’s impressive database of threat and exploit intelligence is what makes ExPRT.AI possible. Other vendors’ solutions can apply data science to vulnerability prioritization, but they lack the data that CrowdStrike has across endpoint detection and response (EDR), vulnerability management, intelligence and threat hunting services. This constantly adapting model uses historical and new data to predict the likelihood of vulnerability exploitation. The beauty of the ExPRT.AI model is that by using the inputs, the AI provides a probability adjustment, offering a dynamic score that changes over time, giving Falcon Spotlight customers the ability to proactively respond to vulnerabilities before they become an issue. And because ExPRT.AI is always learning, it predicts what might happen ahead of time so patching teams can proactively address their risk. ExPRT.AI allows SecOps the ability to focus on what truly matters while deprioritizing those vulnerabilities that pose little to no risk.
Accessing the CISA Known Exploited Vulnerabilities Catalog via Falcon Spotlight APIs
CrowdStrike has two major API clients: PsFalcon, a PowerShell-based client, and Falconpy, a Python-based client. We are happy to announce that we have leveraged Falconpy to provide a new publicly available sample on GitHub. This sample allows Falcon Spotlight customers to quickly: 1) authenticate to the CrowdStrike Security Cloud, 2) consume the current CISA Known Exploited Vulnerabilities Catalog and 3) leverage APIs to compare Falcon Spotlight data against this catalog, providing a comma separated value (CSV) list of results. You’ll need Python to get started. The readme provides instructions on how to get started, including setting up the Python environment with the right dependencies. After pulling the code from GitHub, you’ll need to first ensure, in the CrowdStrike API page, that the right Client ID is given the correct privileges. The APIs leveraged require Spotlight vulnerabilities read-access: ![]() Without this, you won't be able to grab the data you need. Using that Client ID and Client Secret, we can quickly launch the Python code, fusing Falcon Spotlight data with that of CISA’s Known Exploited Vulnerabilities Catalog: ./python main.py --client_id <client_id> --client_secret <secret> If you’re using CrowdStrike's GovCloud-1 environment, which as of this writing is FedRAMP Moderate authorized, add the --base_url usgov1 tag: ./python main.py --client_id <client_id> --client_secret <secret> --base_url usgov1 Note that this code can take some time to execute since it's actively assessing your environment against every CVE on the CISA list against every asset with Falcon Spotlight installed. Upon completion, the sample Python code will generate CSV files that can help prioritize what to do next.
Without this, you won't be able to grab the data you need. Using that Client ID and Client Secret, we can quickly launch the Python code, fusing Falcon Spotlight data with that of CISA’s Known Exploited Vulnerabilities Catalog: ./python main.py --client_id <client_id> --client_secret <secret> If you’re using CrowdStrike's GovCloud-1 environment, which as of this writing is FedRAMP Moderate authorized, add the --base_url usgov1 tag: ./python main.py --client_id <client_id> --client_secret <secret> --base_url usgov1 Note that this code can take some time to execute since it's actively assessing your environment against every CVE on the CISA list against every asset with Falcon Spotlight installed. Upon completion, the sample Python code will generate CSV files that can help prioritize what to do next.
 Figure 1. CrowdStrike Falcon® Spotlight Most Urgent CSVs, sorted by when CISA requires it to be patched within the U.S. Federal Government
Figure 1. CrowdStrike Falcon® Spotlight Most Urgent CSVs, sorted by when CISA requires it to be patched within the U.S. Federal GovernmentFor example, you will see the most pressing CISA known exploited vulnerabilities in your environment based on the date CISA requires the specific CVE to be patched. These dates are a “minimum,” meaning the recommendation for any actively exploited CVE is to patch it as soon as possible. It also produces a list of top offending assets.
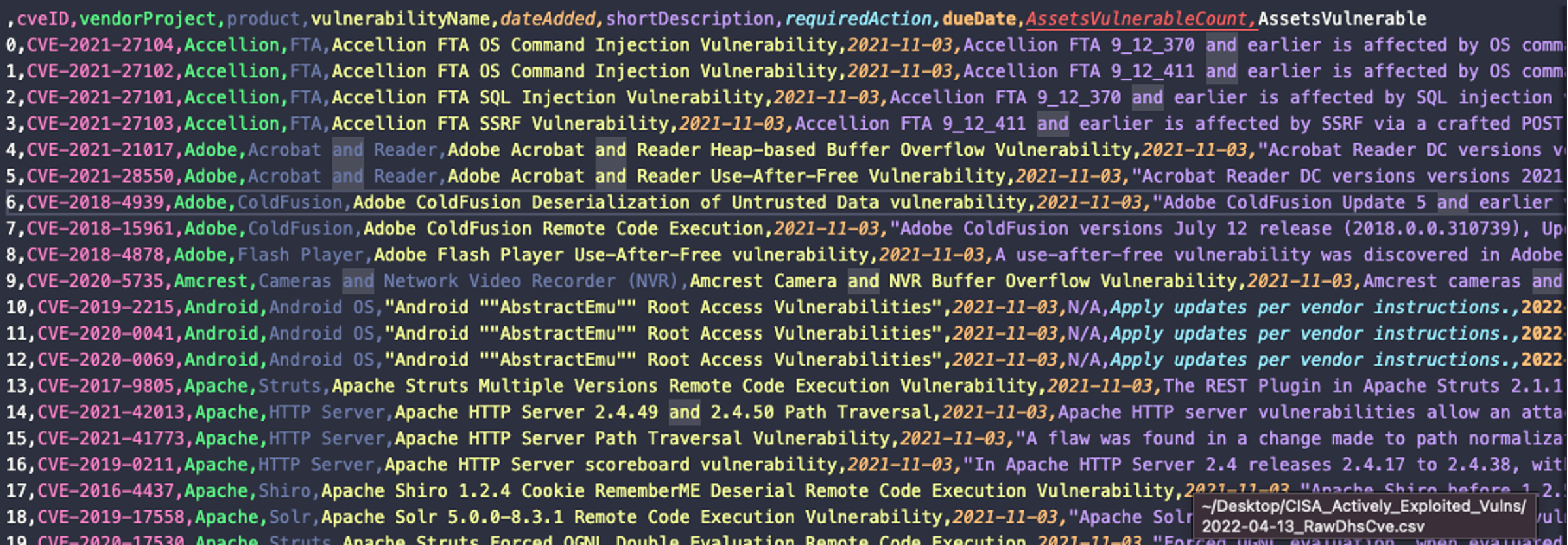 Figure 2. CVEs identified by Falcon Spotlight to prioritize (based on numerous data sources) (Click to enlarge)
Figure 2. CVEs identified by Falcon Spotlight to prioritize (based on numerous data sources) (Click to enlarge)As shown in Figure 2, Falcon Spotlight includes all of the CVEs, the details of each CVE, the date by which CISA requires each vulnerability to be patched, the total assets impacted by that CVE, and the specific CrowdStrike Agent ID (AID) exhibiting the issues. Importing this into a spreadsheet, we can quickly adjust and reorder this data to prioritize it to our liking. This is very helpful when coordinating across teams, sharing via email and automating workflows on top of this data.
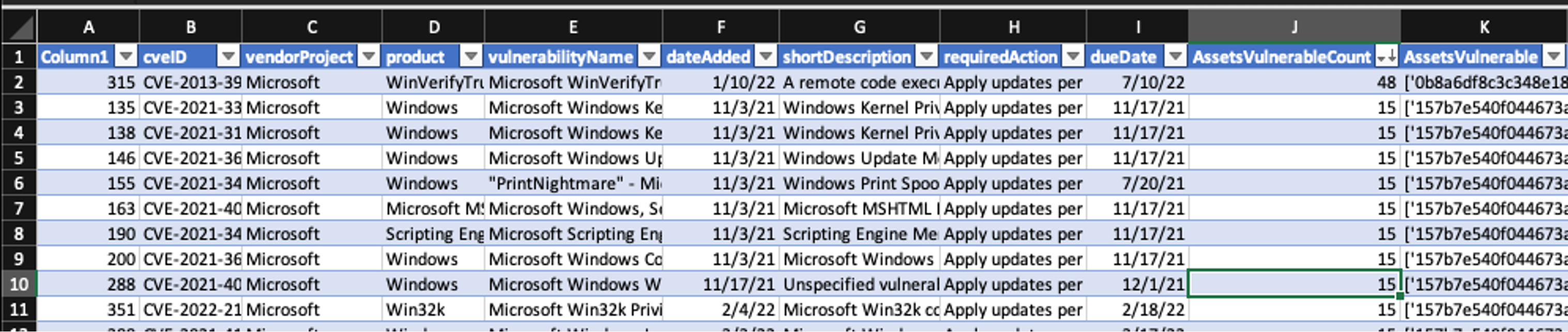 Figure 3. Falcon Spotlight data imported into a spreadsheet to prioritize patching (Click to enlarge)
Figure 3. Falcon Spotlight data imported into a spreadsheet to prioritize patching (Click to enlarge)In Figure 3, you’ll see that the list is in ascending order based on the total number of assets impacted by the given vulnerability. This helps identify the most offending and vulnerable assets based on their CrowdStrike AID.
Accessing the CISA Known Exploited Vulnerabilities Catalog via Spotlight User Interface (UI)
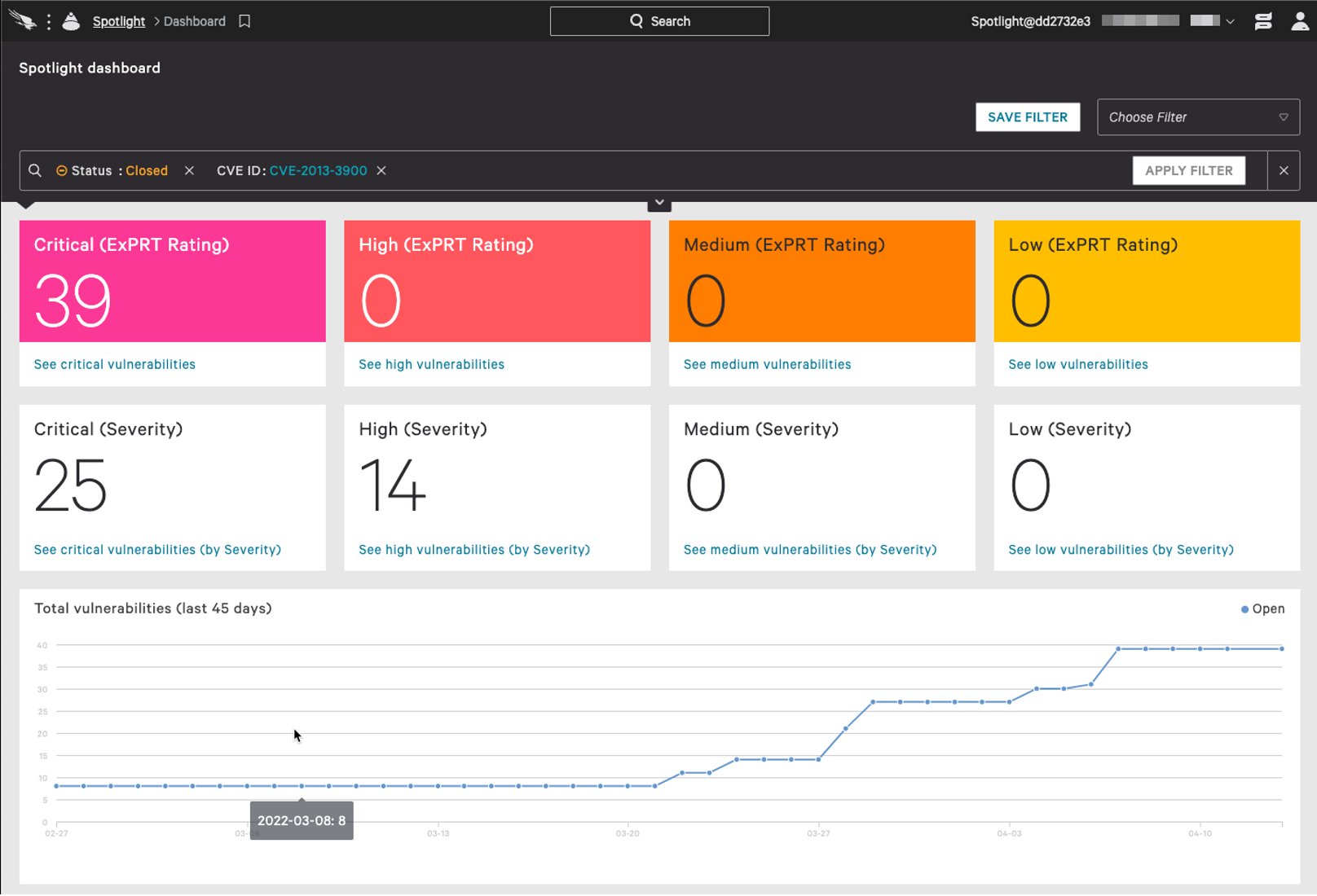
Note that the Python code above does not provide you with the applications causing the issue or exposure. This is where the Falcon Spotlight UI can come in on top to augment the workflow. Knowing the vulnerable application is helpful if you have a Program of Record (PoR) where applications are maintained by an outside team. It also can help prioritize which applications to patch across the fleet. For example, let's look at one of the CVEs we have a finding for in our environment: CVE-2013-3900, classified as a critical vulnerability.
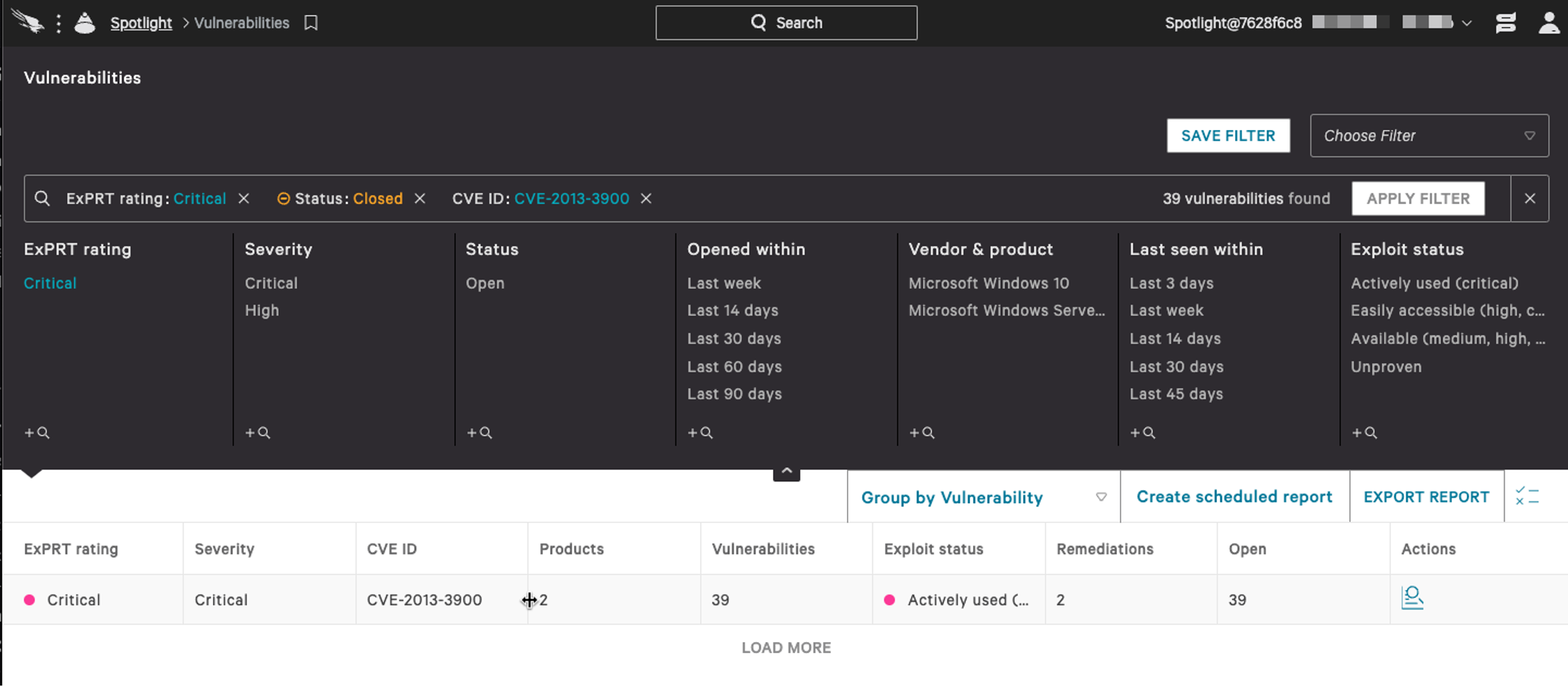
If we click on the Falcon Spotlight ExPRT rating (top left), we can filter based on the priority of the finding, and we see there are two products causing 39 distinct vulnerabilities across our endpoints.
| Why Falcon Spotlight ExPRT.AI? |
| Organizations relying on CVSS scoring often struggle, as severity scoring leaves IT staff with large quantities of severely ranked vulnerabilities. Falcon Spotlight’s Expert Prediction Rating Artificial Intelligence (ExPRT.AI) addresses that challenge by offering an ever-adapting AI model that rates the vulnerabilities posing the most relevant risk to an organization. Static ratings don’t offer the context needed by IT staff — and still leave staff with a large quantity of vulnerabilities that need further manual analysis to determine if they are critical to their organization. ExPRT.AI offers a rich output of data formulated through the dynamic ExPRT Rating, streamlining and simplifying the vulnerability management process. |
Clicking on the “Vendor & product” value, we can further drill in and see that CrowdStrike Falcon® has near real-time visibility that this CVE is being actively exploited in the wild. Falcon Spotlight ExPRT.AI is fed data from multiple sources in addition to CISA’s Known Exploited Vulnerabilities Catalog including other vulnerability catalogs, CrowdStrike’s threat intelligence, dark web intelligence and what is being seen in the wild through incident response engagements. This essentially means anything CISA pushes to its Known Exploited Vulnerabilities Catalog will automatically trigger CrowdStrike to tag that respective CVE as “Actively used,” raising its priority, if it wasn’t already flagged via other means. CrowdStrike Falcon® data includes additional relevance and context, like the date when it was first seen being actively exploited in the wild. 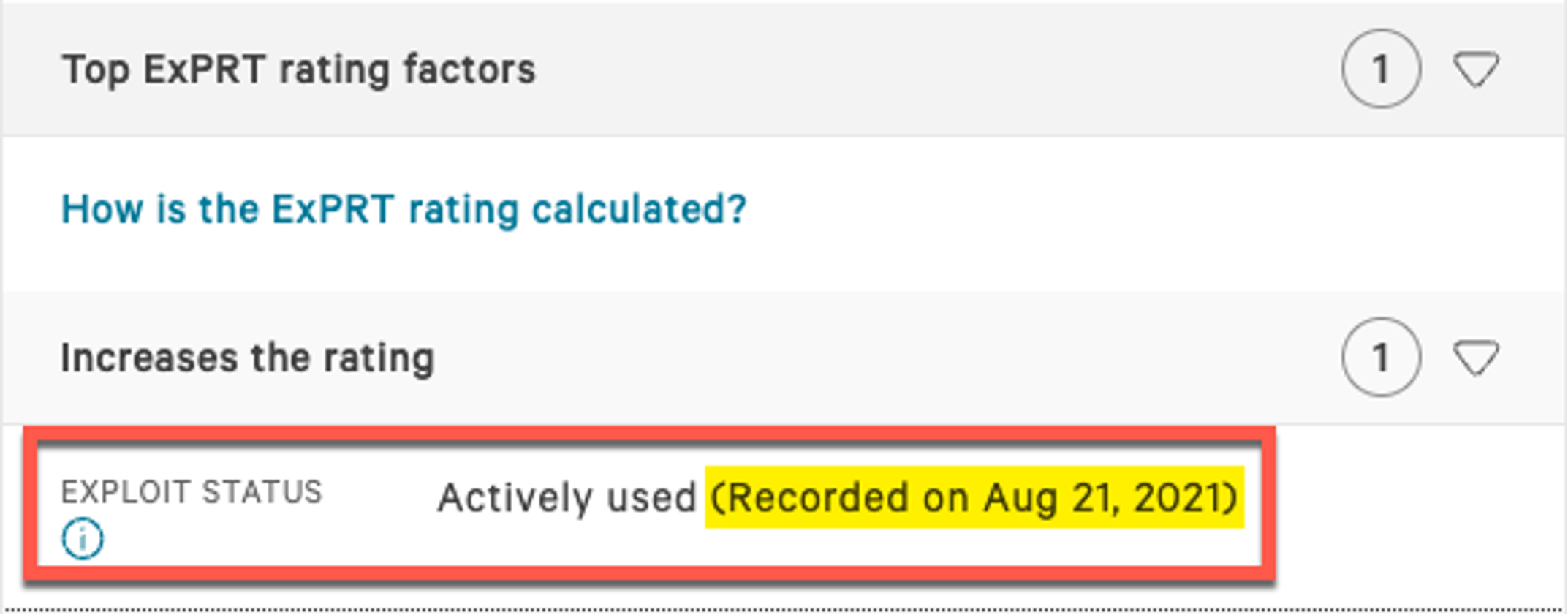 We can see in this example that the reason we tag this as actively used is due to the CISA Known Exploited Vulnerabilities Catalog, which is noted as the source.
We can see in this example that the reason we tag this as actively used is due to the CISA Known Exploited Vulnerabilities Catalog, which is noted as the source. 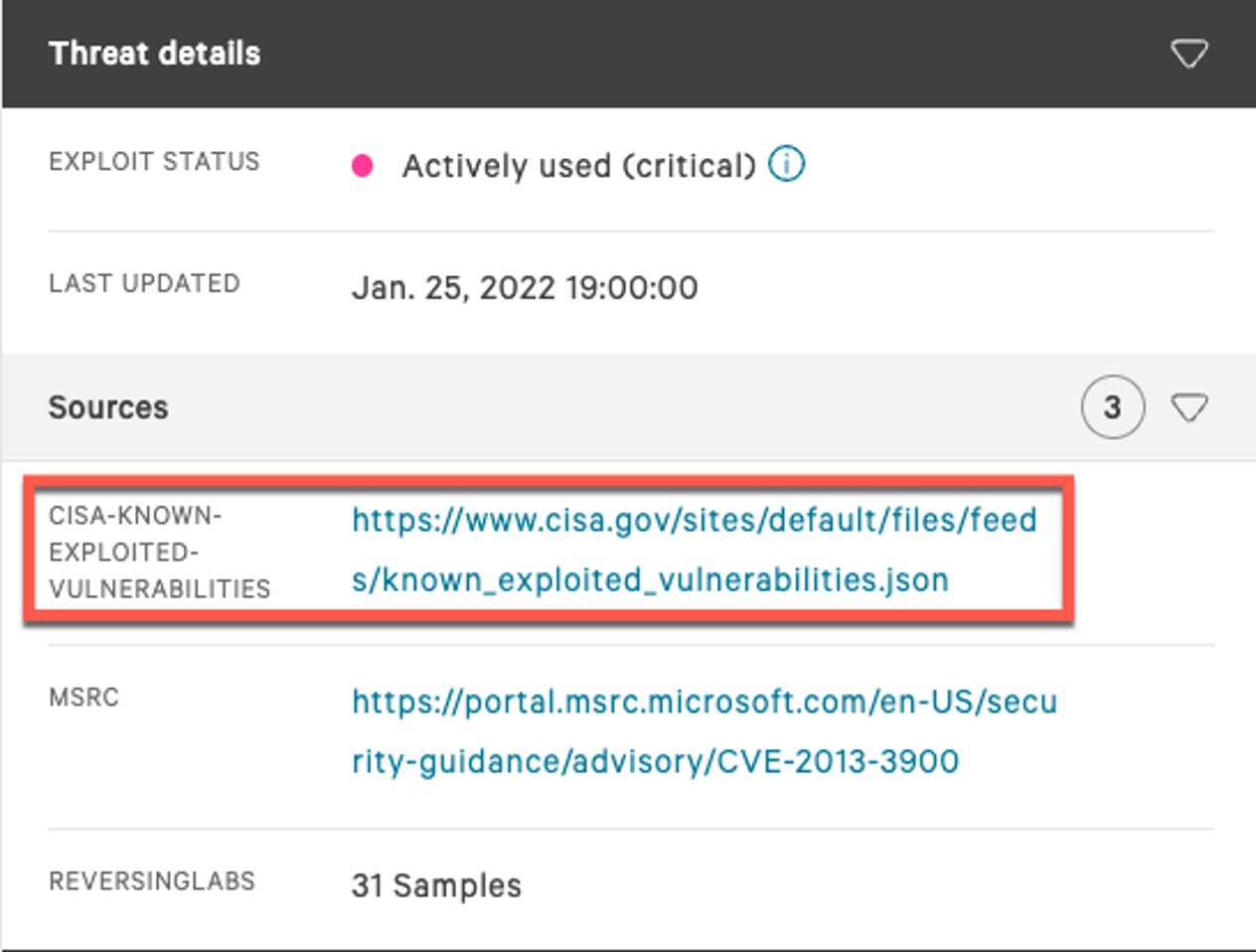 And we are presented with attributing artifacts, such as Microsoft's Security Response Center (MSRC) link on the exploit itself. This is helpful information when reviewing the vendor’s notes on the vulnerability and their recommended mitigation, which may often involve additional steps beyond simply deploying a patch or hotfix.
And we are presented with attributing artifacts, such as Microsoft's Security Response Center (MSRC) link on the exploit itself. This is helpful information when reviewing the vendor’s notes on the vulnerability and their recommended mitigation, which may often involve additional steps beyond simply deploying a patch or hotfix. 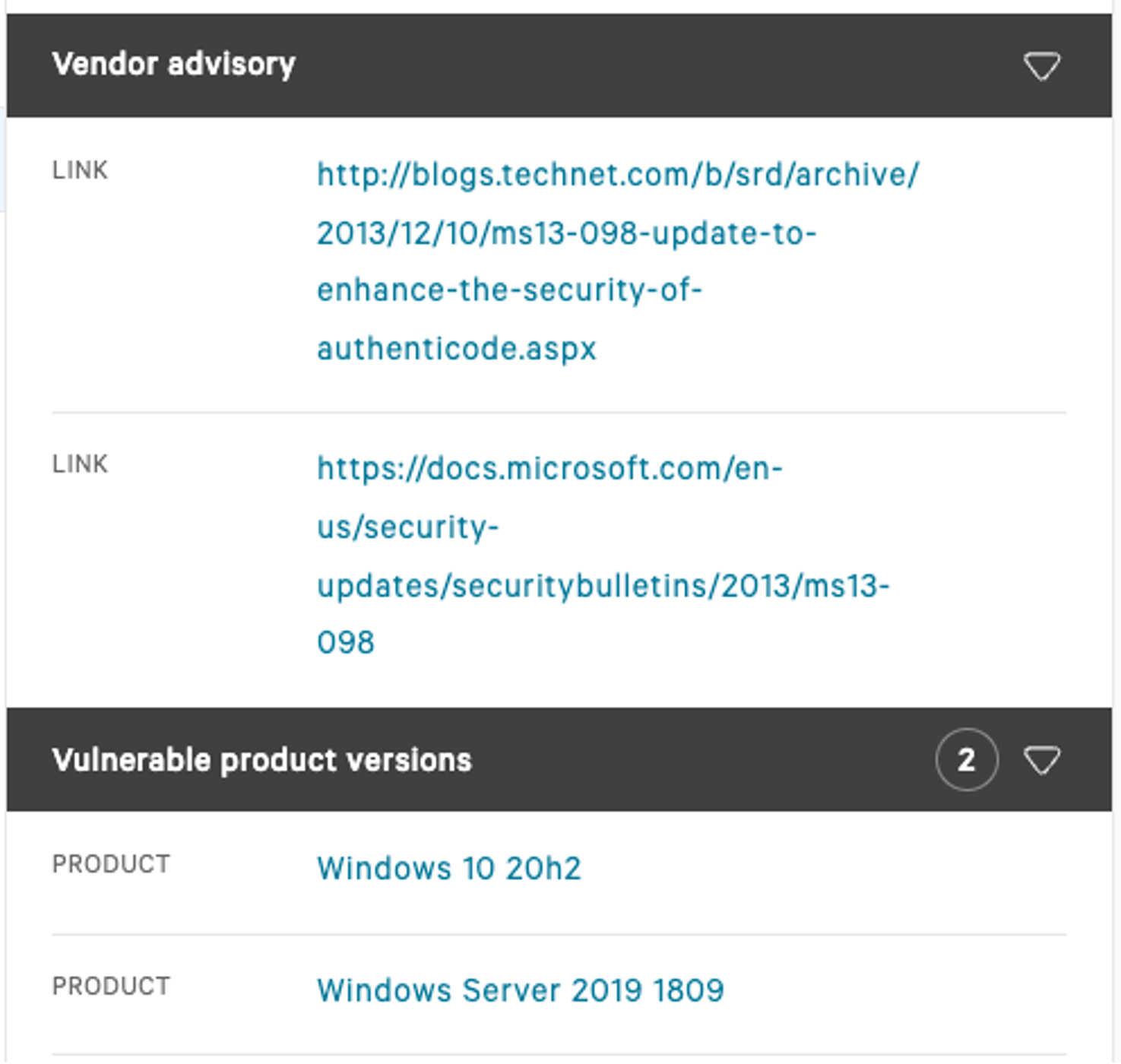 There you have it. In addition, it’s worth highlighting two other Falcon Spotlight Features: 1) real-time notifications — we recommend setting up Falcon Spotlight Scheduled Reports, alerting you any time a CVE is actively being used in your technology environment, and 2) Falcon Spotlight’s Emergency Patching feature, which provides one-click patching for Windows Updates against hosts. These two capabilities increase operational tempo and aid in the discovery of critical vulnerabilities, prioritizing them appropriately and helping resolve exposures quickly. This blog introduced CISA's Known Exploited Vulnerabilities Catalog and demonstrated how to compare it with Falcon Spotlight’s data for near real-time situational awareness via APIs and the Falcon UI. We were able to grab additional context on the vulnerability, see how it's tagged as an “actively used” exploit, and grab additional data to aid our prioritization and remediation phases.
There you have it. In addition, it’s worth highlighting two other Falcon Spotlight Features: 1) real-time notifications — we recommend setting up Falcon Spotlight Scheduled Reports, alerting you any time a CVE is actively being used in your technology environment, and 2) Falcon Spotlight’s Emergency Patching feature, which provides one-click patching for Windows Updates against hosts. These two capabilities increase operational tempo and aid in the discovery of critical vulnerabilities, prioritizing them appropriately and helping resolve exposures quickly. This blog introduced CISA's Known Exploited Vulnerabilities Catalog and demonstrated how to compare it with Falcon Spotlight’s data for near real-time situational awareness via APIs and the Falcon UI. We were able to grab additional context on the vulnerability, see how it's tagged as an “actively used” exploit, and grab additional data to aid our prioritization and remediation phases.
Conclusion
Between CISA’s ever-growing list of known exploited vulnerabilities and the increasing advisories from various government agencies, the alert fatigue and time spent researching the right vulnerabilities to patch can become daunting, even for the most robust team within SecOps. To successfully manage the profusion of vulnerabilities and to maintain your organization’s security posture, you need to utilize a robust vulnerability management program and couple that with the right solutions that will help you accurately identify those vulnerabilities that pose the most critical risk. Vulnerability management is a game of timing — patching vulnerabilities before an attacker can gain access to your environment’s systems could make a dramatic difference in business operations.
Additional Resources
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environment
- Learn more about which Microsoft vulnerability updates your staff should prioritize in the monthly Patch Tuesday analysis.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)