Blog updated: May 14th
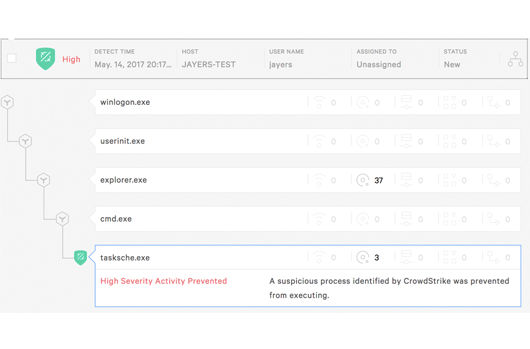
In this screenshot example from the Falcon UI, the detection process tree shows that the malicious file associated with WannaCryptor was launched from explorer.exe.
The global ransomware attack that hit multiple countries on Friday, May 12, 2017 continued to spread over the weekend
with new attacks in Japan, South Korea and Taiwan among other countries. In the United States, the President has asked the Homeland Security advisor to coordinate efforts to respond to the attacks and find those responsible. The attacks are estimated to have affected hundreds of thousands of computers with far-reaching effects across a wide range of industries. CrowdStrike Falcon® Intelligence™ identified this new variant of Windows ransomware, named Wanna or WannaCry, and observed it quickly spreading across multiple countries, after first being reported as an attack on England’s National Health Service on Friday. According to CrowdStrike VP of Intelligence Adam Meyers, this ransomware is complex and challenging because it’s basic structure can be easily modified by criminal hackers, making it difficult to trace. This also contributes to its staying power, as modifications to the WannaCry variant are likely to crop up for some time to come. Fortunately, CrowdStrike® customers are protected against this ransomware variant with exclusive technology in the CrowdStrike Falcon® platform. Falcon’s advanced endpoint protection offers next-gen antivirus that incorporates machine learning augmented with behavioral analysis that looks for indicators of attack (IOAs) — detecting suspicious behavior before an attack occurs. These prevention features, if enabled, will block the WannaCry ransomware and keep it from executing and encrypting the target organization’s data. The WannaCry ransomware attacks have been extensive, targeting healthcare organizations, including doctor’s offices and hospitals, as well as telecommunication systems and gas and electric companies. Early infection reports originated in Europe but have since spread across the United Kingdom, Spain, Russia, Pakistan, and many other regions. Meyers explains that this attack vector has all the hallmarks of a traditional computer worm with the capacity to replicate itself, but he says it is quite unique for such a massive ransomware campaign to use self-propagating techniques at this scale. Meyers outlined how this attack might be unfolding:
- Early analysis of the worm reveals that it’s taking advantage of a recent Microsoft Windows exploit called EternalBlue that enables the sharing of files, which is how the ransomware spread.
- Update May 16: Though phishing emails were originally suspected, CrowdStrike Falcon® Intelligence has since determined that this exploit was solely distributed via the Microsoft vulnerability in MS17-010
- Once an infection takes place, Wanna encrypts victim files using the AES cipher, and demands a Bitcoin ransom that increases in value as time passes.
- The ransom demands observed require victims to pay either $300 or $600 USD worth of Bitcoin for a decryption key that can release the victim’s data.
- CrowdStrike Intelligence has verified at least several thousand dollars’ worth of ransom payments already made to criminal-controlled Bitcoin (BTC) addresses.
- Unfortunately, this strain of ransomware has the potential to encrypt backup files, making remediation even more challenging.
Meyers advises that organizations act quickly to ensure they are not impacted by this wave of attacks.
He recommends that swift action to patch against Windows exploits is critical (the EternalBlue exploit is patched by MS17-010), as is ensuring that backup data files are disconnected from the core network. For more information on how the CrowdStrike Falcon® platform defends against ransomware and other modern attacks, read the white paper,
“Ransomware, a Growing Enterprise Threat.” For additional details on WannaCry, see “Falcon Intelligence Report: Wanna Ransomware Spreads Rapidly; CrowdStrike Falcon® Prevents the Attack.”





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)