First-Ever Adversary Ranking in 2019 Global Threat Report Highlights the Importance of Speed

The most essential concept in cybersecurity today is speed. Whether you are a defender or an attacker, you have to be faster than your opponent, or get inside of their OODA Loop, as the military strategists will tell you, in order to achieve success. The OODA Loop is a concept invented by U.S. Air Force Colonel John Boyd, initially applied to military combat operations, but since then expanded to cyber conflict and even business strategy. One of the key ideas behind it is that all the opponents on a battlefield — physical or virtual — go through a four-stage rapid decision cycle: Observe, Orient, Decide, and Act. The actor who can process this cycle the fastest, or get inside the other’s decision cycle, will prevail
In last year’s Global Threat Report, we highlighted the new key concept of breakout time, which is the time it takes for an intruder to begin moving laterally, beyond the initial beachhead they’ve established, to other systems in the network. I believe it is a critical metric to track how fast adversaries can operate within targeted networks, and it provides valuable information for defenders to evaluate their own detection and response times, against what I call the 1-10-60 rule. Last year, we tracked an average breakout time of 1 hour and 58 minutes. This means that in order to stop a breach and contain an adversary before they “breakout” of the initial beachhead and get to critical resources within the network, a defender has to detect, investigate and remediate or contain the intrusion, on average, within roughly two hours. If it takes longer, you risk the adversary achieving their objective of stealing or destroying critical data and assets from deep inside your organization.
The 2019 Global Threat Report, “Adversary Tradecraft and the Importance of Speed,” takes an even deeper dive into breakout time by presenting the average time of major adversary groups whose intrusions were attributed in 2018. For the intrusions where we detected lateral movement and had attribution, we calculated averages across five categories: Russia, China, Iran, North Korea and eCrime groups (which were consolidated into a single category for simplicity).
This first-ever ranking of major adversary groups by breakout time, which is a good proxy for their operational sophistication and tradecraft, is an illuminating look at which actors operate the fastest within networks they have gained access to, and how effective and rapid the defenders have to be to defeat some of the most capable adversaries. Breakout time is the ideal metric for tracking the quality of operational tradecraft because it encompasses key adversary actions from the time they first establish a beachhead in a network (e.g., get someone to click on a link or compromise a system via an exploit), to the time they spend performing on-network reconnaissance, privilege escalation and credential theft, until they ultimately achieve their initial goal of moving laterally to other systems in the network.
Breakout Time Results Per Adversary Category
It’s important to note that these are averages, so there are variances when looking at individual intrusions. However, we think it’s a good indicator, in general, of how fast different adversaries tend to be. Here are the speeds per adversary category, using the naming conventions established by CrowdStrike® Intelligence:
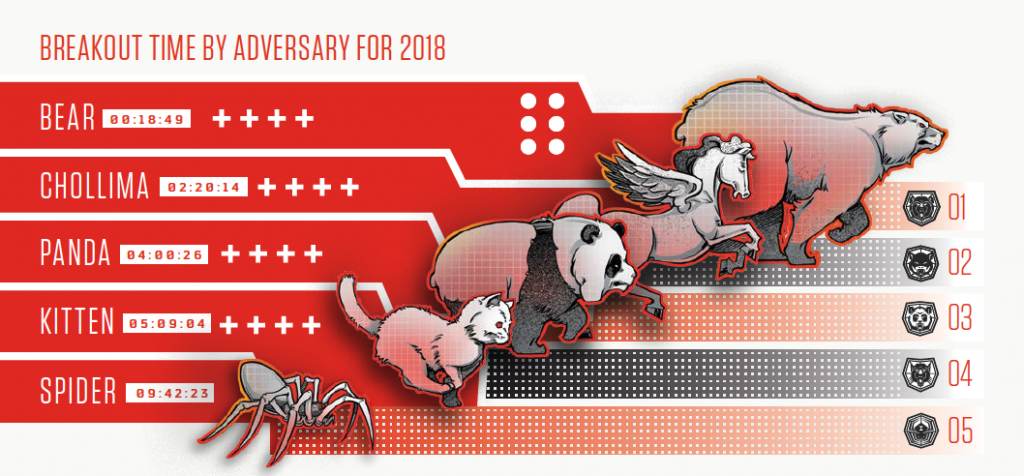
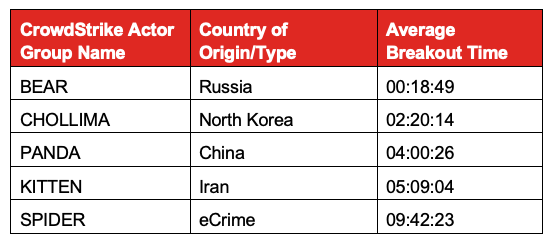
State-sponsored adversaries out of Russia (BEARS) ranked first — almost eight times faster, on average, than their nearest competitor. While we certainly expected them to come out on top, given how effective their tradecraft usually is in comparison with other threat actors, even we were surprised by the data and how fast they can move inside a network once they get a foothold.
Another big revelation was who took the second-place ranking. North Korean-based threat actors were on average almost twice as fast as Chinese state-sponsored adversaries. This is likely due in part to North Korean actors having almost 20 years of experience in pursuing a very aggressive cyber offensive program. In fact, I consider them to be the most innovative threat actors in terms of their use of cyber offensive operations. They were among the first nation-states to employ destructive attacks back in 2009 and one of the earliest to use information operations, as the 2014 attack on Sony Pictures exemplified. And they are the leading offender among nation-states when it comes to leveraging cybercrime operations to enrich government coffers through compromises of global banking institutions, financial transaction networks, and increasingly, cryptocurrency exchanges and infrastructure. In other words, people underestimate North Korea at their own peril — their tradecraft and capabilities are quite advanced and their fast breakout times are evidence of that.
It is also important to keep in mind that results for individual actor groups within these categories can vary widely. Although SPIDERS are ranked last with an average breakout time of over nine hours, some individual eCrime groups can act much faster than their average time indicates.
The 1-10-60 Rule and the Importance of Metrics
The ranking of breakout times by adversary also serves to underscore the significance of the 1-10-60 rule that I have long advocated. That’s why tracking these metrics — the time it takes to detect, investigate and remediate an incident — is crucial to mounting an effective defense. We call it the 1-10-60 rule because the recommended times are: one minute to detect, 10 minutes to investigate, and one hour to remediate. In short, this is what it takes to be faster than adversaries.
Depending on the adversaries you face, even meeting the 1-10-60 rule can sometimes be insufficient, and certain organizations may have to act even faster. If you’re facing Russian state-sponsored adversaries, for example, and it takes you an hour to remediate, they might have already broken out, and you’ll soon be dealing with a major breach. The important thing to remember is that there will be times when adversaries are faster than their breakout averages, and times when they are slower. However, these averages allow organizations to adjust their target response times to meet their individual needs, based in part on which adversaries types they are most likely to confront, given the business sector they are in or their regional focus. I highly recommend that every organization consistently track their detect/investigate/remediate metrics against the 1-10-60 rule to ensure they are making sufficient progress in driving down those times with each investment in new capabilities, people, or change in processes.
Why Breakout Time is an Effective Method for Ranking Adversaries
This focus on speed in general — and breakout time in particular — is a major theme in this year’s threat report because, while there are other ways to assess adversaries, we believe this is one of the more effective proxies for their operational aptitude. You could rank them based on the sophistication of their malware, or number of zero-day exploits they employ, but you might not be getting the real story, since those capabilities can be acquired or stolen. In contrast, assessing adversaries based on breakout time is an indication of how adroit they are at actual hands-on-keyboard activity. Anyone with sufficient interest and money can purchase a zero-day exploit. However, that doesn’t mean they also have a highly capable cadre of cyber operators to carry out campaigns.
Of course, breakout time isn’t a universal metric. It can vary widely based on the capabilities of defenders — so if an adversary consistently targets networks with as many holes as Swiss cheese, moving laterally is much easier and can be done a lot faster. The threat actors tracked and ranked by CrowdStrike do target numerous industries and regions where defensive capabilities vary widely, so these fluctuations will diminish over time. We plan to continue focusing on this type of analysis and providing more detailed data points on breakout times in the future, which will be useful in ongoing research.
Critical Metrics Plus the Right Technology
Ultimately, your best defense is to make sure your organization is deploying the most effective technology and integrating the 1-10-60 rule into your cybersecurity strategy. Meeting the challenge of this benchmark will require true next-generation solutions, such as the CrowdStrike Falcon® platform that offers endpoint detection and response (EDR), managed threat hunting, next-gen AV with behavioral analytics and machine learning, and automated threat intelligence. These tools are key to gaining the visibility and context you need to meet these critical, outcome-driven metrics, and win the race against even the most sophisticated adversaries.
Additional Resources
- Download the 2020 Global Threat Report.
- Join a webcast on the 2019 Global Threat Report.
- Learn more about the CrowdStrike endpoint protection platform.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.