What is Threat Intelligence?
Threat intelligence is data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors. Threat intelligence enables us to make faster, more informed, data-backed security decisions and change their behavior from reactive to proactive in the fight against threat actors.
Threat intelligence is evidence-based knowledge (e.g., context, mechanisms, indicators, implications and action-oriented advice) about existing or emerging menaces or hazards to assets. – Gartner
Why is Threat Intelligence Important?
In the world of cybersecurity, advanced persistent threats (APTs) and defenders are constantly trying to outmaneuver each other. Data on a threat actor’s next move is crucial to proactively tailoring your defenses and preempt future attacks.
Organizations are increasingly recognizing the value of threat intelligence. However, there is a difference between recognizing value and receiving value. Most organizations today are focusing their efforts on only the most basic use cases, such as integrating threat data feeds with existing network, IPS, firewalls, and SIEMs — without taking full advantage of the insights that intelligence can offer.

2024 CrowdStrike Global Threat Report
The 2024 Global Threat Report unveils an alarming rise in covert activity and a cyber threat landscape dominated by stealth. Data theft, cloud breaches, and malware-free attacks are on the rise. Read about how adversaries continue to adapt despite advancements in detection technology.
Download NowCompanies that stick to this basic level of threat intelligence are missing out on real advantages that could significantly strengthen their security postures.
Threat intelligence is important for the following reasons:
- sheds light on the unknown, enabling security teams to make better decisions
- empowers cyber security stakeholders by revealing adversarial motives and their tactics, techniques, and procedures (TTPs)
- helps security professionals better understand the threat actor’s decision-making process
- empowers business stakeholders, such as executive boards, CISOs, CIOs and CTOs; to invest wisely, mitigate risk, become more efficient and make faster decisions
Learn More
Want to stay up to date on recent threat actor activities? Stop by the Research and Threat Intel Blog for the latest research, trends, and insights on emerging cyber threats.Research and Threat Intel Blog
Who Benefits from Threat Intelligence?
Threat intelligence benefits organizations of all shapes and sizes by helping process threat data to better understand their attackers, respond faster to incidents, and proactively get ahead of a threat actor’s next move. For SMBs, this data helps them achieve a level of protection that would otherwise be out of reach. On the other hand, enterprises with large security teams can reduce the cost and required skills by leveraging external threat intel and make their analysts more effective.
From top to bottom, threat intelligence offers unique advantages to every member of a security team, including:
- Sec/IT Analyst
- SOC
- CSIRT
- Intel Analyst
- Executive Management
Here’s how it can benefit each position, and the specific use cases that apply to each:
Threat Intelligence Lifecycle
The intelligence lifecycle is a process to transform raw data into finished intelligence for decision making and action. You will see many slightly different versions of the intelligence cycle in your research, but the goal is the same, to guide a cybersecurity team through the development and execution of an effective threat intelligence program.
Threat intelligence is challenging because threats are constantly evolving – requiring businesses to quickly adapt and take decisive action. The intelligence cycle provides a framework to enable teams to optimize their resources and effectively respond to the modern threat landscape. This cycle consists of six steps resulting in a feedback loop to encourage continuous improvement:
Let’s explore the 6 steps below:
1. Requirements
The requirements stage is crucial to the threat intelligence lifecycle because it sets the roadmap for a specific threat intelligence operation. During this planning stage, the team will agree on the goals and methodology of their intelligence program based on the needs of the stakeholders involved. The team may set out to discover:
- who the attackers are and their motivations
- what is the attack surface
- what specific actions should be taken to strengthen their defenses against a future attack
2. Collection
Once the requirements are defined, the team then sets out to collect the information required to satisfy those objectives. Depending on the goals, the team will usually seek out traffic logs, publicly available data sources, relevant forums, social media, and industry or subject matter experts.
3. Processing
After the raw data has been collected, it will have to be processed into a format suitable for analysis. Most of the time, this entails organizing data points into spreadsheets, decrypting files, translating information from foreign sources, and evaluating the data for relevance and reliability.
4. Analysis
Once the dataset has been processed, the team must then conduct a thorough analysis to find answers to the questions posed in the requirements phase. During the analysis phase, the team also works to decipher the dataset into action items and valuable recommendations for the stakeholders.

5. Dissemination
The dissemination phase requires the threat intelligence team to translate their analysis into a digestible format and present the results to the stakeholders. How the analysis is presented depends on the audience. In most cases the recommendations should be presented concisely, without confusing technical jargon, either in a one-page report or a short slide deck.
6. Feedback
The final stage of the threat intelligence lifecycle involves getting feedback on the provided report to determine whether adjustments need to be made for future threat intelligence operations. Stakeholders may have changes to their priorities, the cadence at which they wish to receive intelligence reports, or how data should be disseminated or presented.
Find this article informative? Then watch the Threat Intel episode of our Cybersecurity 101 Webinar Series:
Threat Intelligence Use Cases
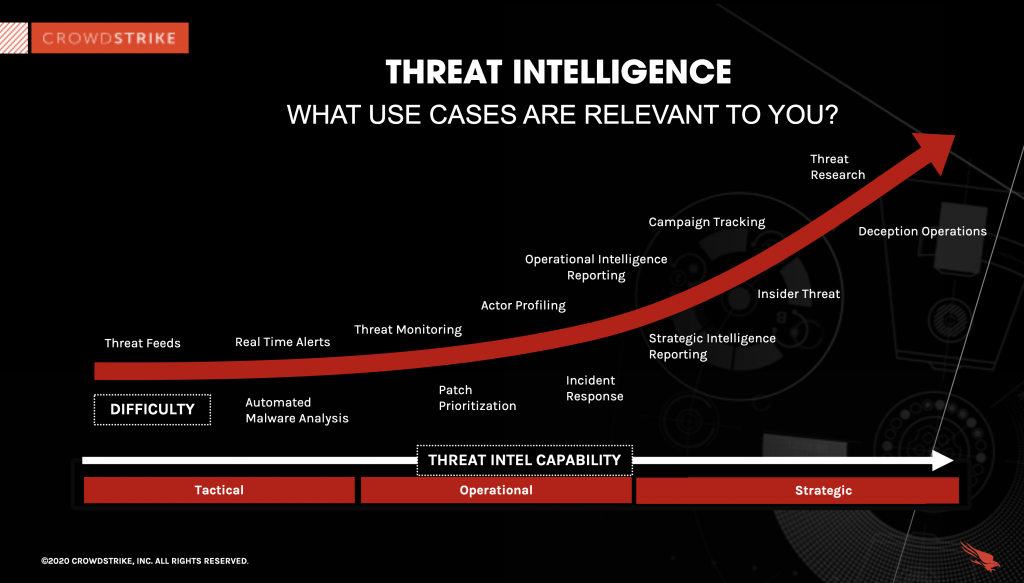
Below is a list of use cases by function:
| - Integrate TI feeds with other security products - Block bad IPs, URLS, domains, files etc |
|
| - Use TI to enrich alerts - Link alerts together into incidents - Tune newly deployed security controls |
|
| - Look for information on the who/what/why/when/how of an incident - Analyze root cause to determine scope of the incident |
|
| - Look wider and deeper for intrusion evidence - Review reports on threat actors to better detect them |
|
| - Assess overall threat level for the organization - Develop security roadmap |
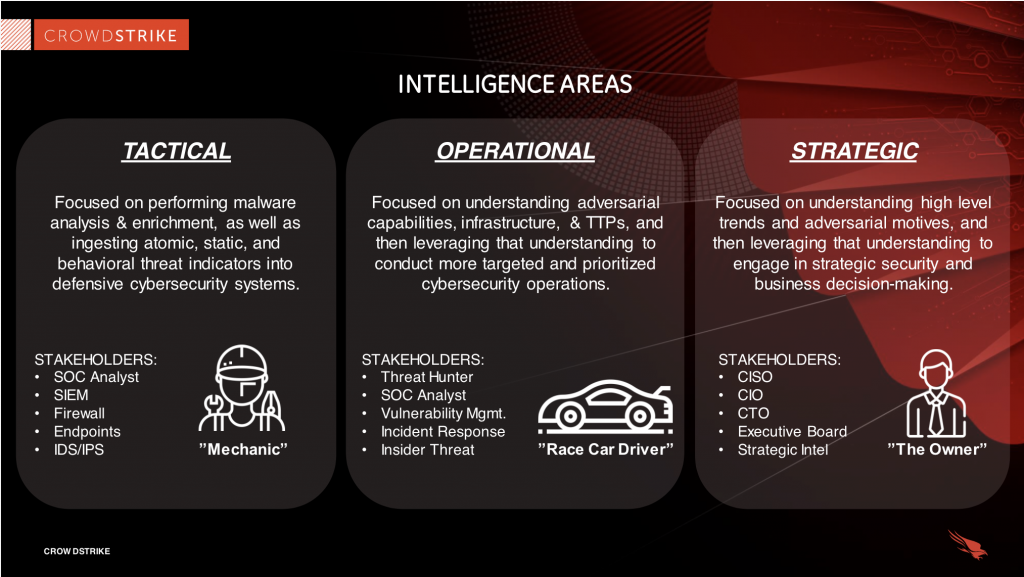
3 Types of Threat Intelligence
We discussed in the last section how threat intelligence can empower us with data about existing or potential threats. The information can be straightforward, such as a malicious domain name, or complex, such as an in-depth profile of a known threat actor. Keep in mind that there is a maturity curve when it comes to intelligence represented by the three levels listed below. With each level, the context and analysis of CTI becomes deeper and more sophisticated, caters to different audiences, and can get more costly.
- Tactical intelligence
- Operational intelligence
- Strategic intelligence
Tactical Threat Intelligence
Challenge: Organizations often only focus on singular threats
Objective: Obtain a broader perspective of threats in order to combat the underlying problem
Tactical intelligence is focused on the immediate future, is technical in nature, and identifies simple indicators of compromise (IOCs). IOCs are things such as bad IP addresses, URLs, file hashes and known malicious domain names. It can be machine-readable, which means that security products can ingest it through feeds or API integration.
Tactical intelligence is the easiest type of intelligence to generate and is almost always automated. As a result, it can be found via open source and free data feeds, but it usually has a very short lifespan because IOCs such as malicious IPs or domain names can become obsolete in days or even hours.
It’s important to note that simply subscribing to intel feeds can result in plenty of data, but offers little means to digest and strategically analyze the threats relevant to you. Also, false positives can occur when the source is not timely or of high fidelity.
Questions to ask yourself:
- Do you have an IOC feed?
- Are IOCs timely and relevant?
- Is malware analysis automated?
Operational Threat Intelligence
Challenge: Threat actors favor techniques that are effective, opportunistic, and low-risk
Objective: Engage in campaign tracking and actor profiling to gain a better understanding of the adversaries behind the attacks
In the same way that poker players study each other’s quirks so they can predict their opponents’ next move, cybersecurity professionals study their adversaries.
Behind every attack is a “who,” “why,” and “how.” The “who” is called attribution. The “why” is called motivation or intent. The “how” is made up of the TTPs the threat actor employs. Together, these factors provide context, and context provides insight into how adversaries plan, conduct, and sustain campaigns and major operations. This insight is operational intelligence.
Machines alone cannot create operational threat intelligence. Human analysis is needed to convert data into a format that is readily usable by customers. While operational intelligence requires more resources than tactical intelligence, it has a longer useful life because adversaries can’t change their TTPs as easily as they can change their tools, such as a specific type of malware or infrastructure.
Operational intelligence is most useful for those cybersecurity professionals who work in a SOC (security operations center) and are responsible for performing day-to-day operations. Cybersecurity disciplines such as vulnerability management, incident response and threat monitoring are the biggest consumers of operational intelligence as it helps make them more proficient and more effective at their assigned functions.
Questions to ask yourself:
- Is the SOC deriving use cases from threat actor TTPs?
- Is CTI being used to prioritize vulnerabilities?
- Are you leveraging CTI derived Yara/Snort rules to engage in hunting?
Learn More
Watch the on-demand webcast on “Cyber Threat Intelligence Demystified” to learn how to proactively defend against adversaries targeting your business.Watch Crowdcast
Strategic Threat Intelligence
Challenge: Poor business and organizational decisions are made when the adversary is misunderstood
Objective: Threat intelligence should inform business decisions and the processes behind them
Adversaries don’t operate in a vacuum — in fact, there are almost always higher level factors that surround the execution of cyber attacks. For example, nation-state attacks are typically linked to geopolitical conditions, and geopolitical conditions are linked to risk. Furthermore, with the adoption of financially motivated Big Game Hunting, cyber-crime groups are constantly evolving their techniques and should not be ignored.
Strategic intelligence shows how global events, foreign policies, and other long-term local and international movements can potentially impact the cyber security of an organization.
Strategic intelligence helps decision-makers understand the risks posed to their organizations by cyber threats. With this understanding, they can make cybersecurity investments that effectively protect their organizations and are aligned with its strategic priorities.
Strategic intelligence tends to be the hardest form to generate. Strategic intelligence requires human data collection and analysis that demands an intimate understanding of both cybersecurity and the nuances of the world’s geopolitical situation. Strategic intelligence usually comes in the form of reports.

2023 Threat Hunting Report
In the 2023 Threat Hunting Report, CrowdStrike’s Counter Adversary Operations team exposes the latest adversary tradecraft and provides knowledge and insights to help stop breaches.
Download NowCrowdStrike’s Threat Intelligence Tools
CrowdStrike’s intel solution, CrowdStrike Falcon® Adversary Intelligence, helps organizations easily consume intelligence, take action, and maximize the impact of their intelligence investment.
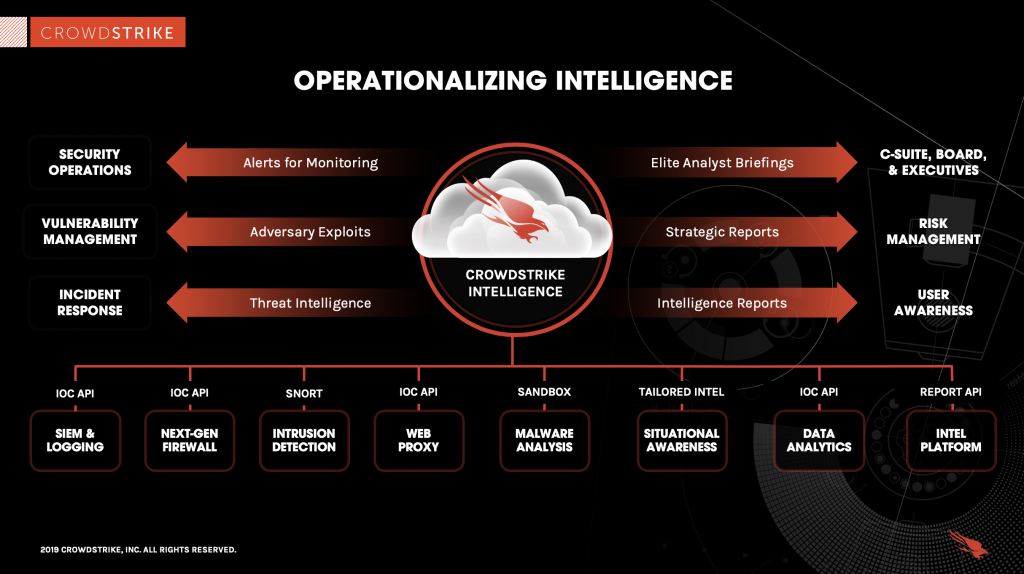
How CrowdStrike operationalizes threat intelligence
Integrated Intelligence, Tailored to Your Organization
CrowdStrike Falcon® Adversary Intelligence automates the threat investigation process and delivers actionable intelligence reporting and custom IOCs specifically tailored for the threats encountered on your endpoints. With this level of automation, you can stop picking and choosing which threats to analyze and start analyzing the most relevant threats to your organization.
CrowdStrike Falcon® Intelligence combines the tools used by world-class cyber threat investigators into a seamless solution and performs the investigations automatically. The integrated tool set includes malware analysis, malware search, and CrowdStrike’s global IOC feed. CrowdStrike Falcon Adversary® Intelligence enables all teams, regardless of size or sophistication, to understand better, respond faster and proactively get ahead of the attacker’s next move. CrowdStrike also supports threat intelligence platforms (TIPs) by offering prebuilt integrations and API access to CrowdStrike Falcon Adversary Intelligence.
CrowdStrike Falcon® Adversary Intelligence Premium: The Human Element
CrowdStrike Falcon® Adversary Intelligence Premium reporting enhances your organization with the expertise of CrowdStrike’s Global Intelligence team to better fight against your adversaries. The CrowdStrike Intelligence team is a pioneer in adversary analysis, tracking more than 121 nation-state, cybercrime, and hacktivist groups, studying their intent and analyzing their tradecraft. This team of intel analysts, security researchers, cultural experts, and linguists uncover unique threats and provide groundbreaking research that fuels CrowdStrike’s ability to deliver proactive intelligence that can help dramatically improve your security posture and help you get ahead of attackers
Interested in learning more about CrowdStrike Falcon® Adversary Intelligence? Check out the resources below: