In support of the Executive Order on Improving the Nation’s Cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA) recently published a Binding Operational Directive (BOD) 23-01, designed to improve cybersecurity for the Federal Civilian Executive Branch (FCEB) enterprise and their respective unclassified assets. In the BOD, CISA is mandating continuous and comprehensive asset visibility, focusing on two major activities that pertain to any asset that is routable via IPv4 or IPv6: Asset Discovery and Vulnerability Enumeration. By April 3, 2023, all FCEB agencies are required to implement multiple steps and are expected to meet or exceed the following:
- Perform automated asset discovery every 7 days
- Initiate vulnerability enumeration across all discovered assets every 14 days
- Load a report of detected vulnerabilities into the CDM Agency Dashboard within 72 hours of discovery completion
- Establish and have reliable operational capability to initiate on-demand asset discovery and vulnerability discovery within 72 hours of receiving a request from CISA and provide the available results to CISA within 7 days of request.
The CrowdStrike Falcon®® platform is FedRAMP-authorized, provides comprehensive, best-in-class protection across endpoints, mobile devices, cloud workloads, identities and data for modern government organizations. Our platform addresses the key requirements of this operational directive through powerful natively integrated modules, including asset discovery and vulnerability management capabilities. Learn more about CrowdStrike’s FedRAMP-authorized, cloud-delivered solution that provides unrivaled protection and helps meet the strictest federal standards.
Asset Discovery and Vulnerability Enumeration
You cannot protect what you cannot see. In a rapidly expanding hybrid work environment, with increased use of the cloud, seeing all networked assets becomes even more challenging. Mobile devices are in scope for the BOD as well, and bring-your-own-device (BYOD) practices have increased the number of assets that need to be discovered and managed.
The cloud-native, single-agent architecture of the Falcon platform empowers federal customers to gain visibility and deploy best-in-class protection across critical areas of risk, all from a single, uniform platform. The platform modules that enable federal customers to achieve compliance with the BOD include the following.
Endpoint
CISA selected CrowdStrike for its best-of-breed EDR capabilities — Falcon Insight XDR™ — which helps our federal customers discover assets, monitor for cyber risk detections and incidents, and automate the response and remediation to such events. You can see who, what and where entities are accessed within your organization with Falcon Discover™, CrowdStrike’s IT hygiene solution, which offers central visibility and entity inventory around applications, assets and accounts spread across your enterprise. Security operations teams use Falcon Discover to efficiently manage and maintain their organization’s environments to ensure the health of their systems and to maintain a defensible security posture. As Falcon Discover sits within the Falcon platform, it is easy and efficient to cross-reference suspicious data and connect with broader SecOps for context around vulnerabilities and other incidents. Falcon Discover leverages the same lightweight-agent architecture used for the Falcon platform.
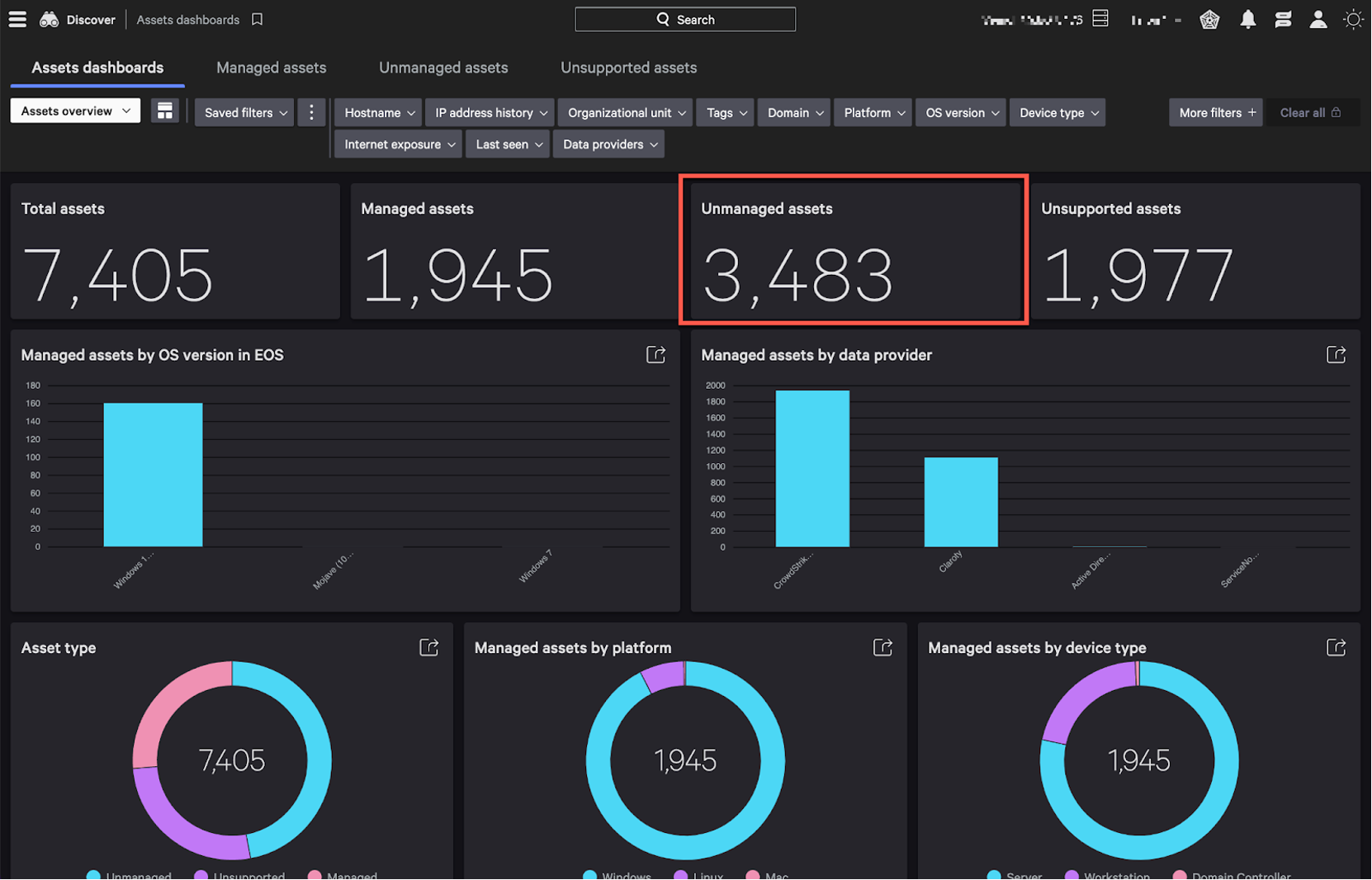 Figure 1. Falcon Discover identifying managed and unmanaged assets while providing a single view of high-level asset data (click to enlarge)
Figure 1. Falcon Discover identifying managed and unmanaged assets while providing a single view of high-level asset data (click to enlarge)Security operations staff often have only a limited number of hours each week to monitor all of the hundreds of thousands of endpoints that exist within an organization's environment. Even if your team only focuses on those endpoints that indicate a vulnerable opening, or potential abuse of an account, monitoring can quickly eat up all available resources and time. Falcon Discover offers data in real time and a robust set of reporting capabilities, and your staff can reap the immediate benefits of accurate reporting that is fully automated and helps you exceed the thresholds and response times in the directive.
Vulnerability Enumeration
Falcon Spotlight™, CrowdStrike’s unified threat and vulnerability management solution, establishes vulnerability management capabilities using the same agent and sensor that provides Falcon Insight XDR.
Falcon Spotlight is a scanless vulnerability management solution that provides real-time visibility across your enterprise. Spotlight enumerates common vulnerabilities and exposures (CVEs) with the same agent while prioritizing vulnerabilities based on prevalence and availability as seen in the wild. With “one-click patching,” customers can deploy Microsoft Windows Update patches to specific hosts, enabling customers to identify and patch in a single console. With Falcon Spotlight, CrowdStrike enables you to go above and beyond the requirements of the BOD and leverage continuous vulnerability scans of your assets. The Falcon platform compares discovered vulnerabilities against real-world cyber intrusions — including fusing findings and discoveries with CISA’s Known Vulnerability Catalog — helping our customers prioritize exposures that are actively being exploited by adversaries.
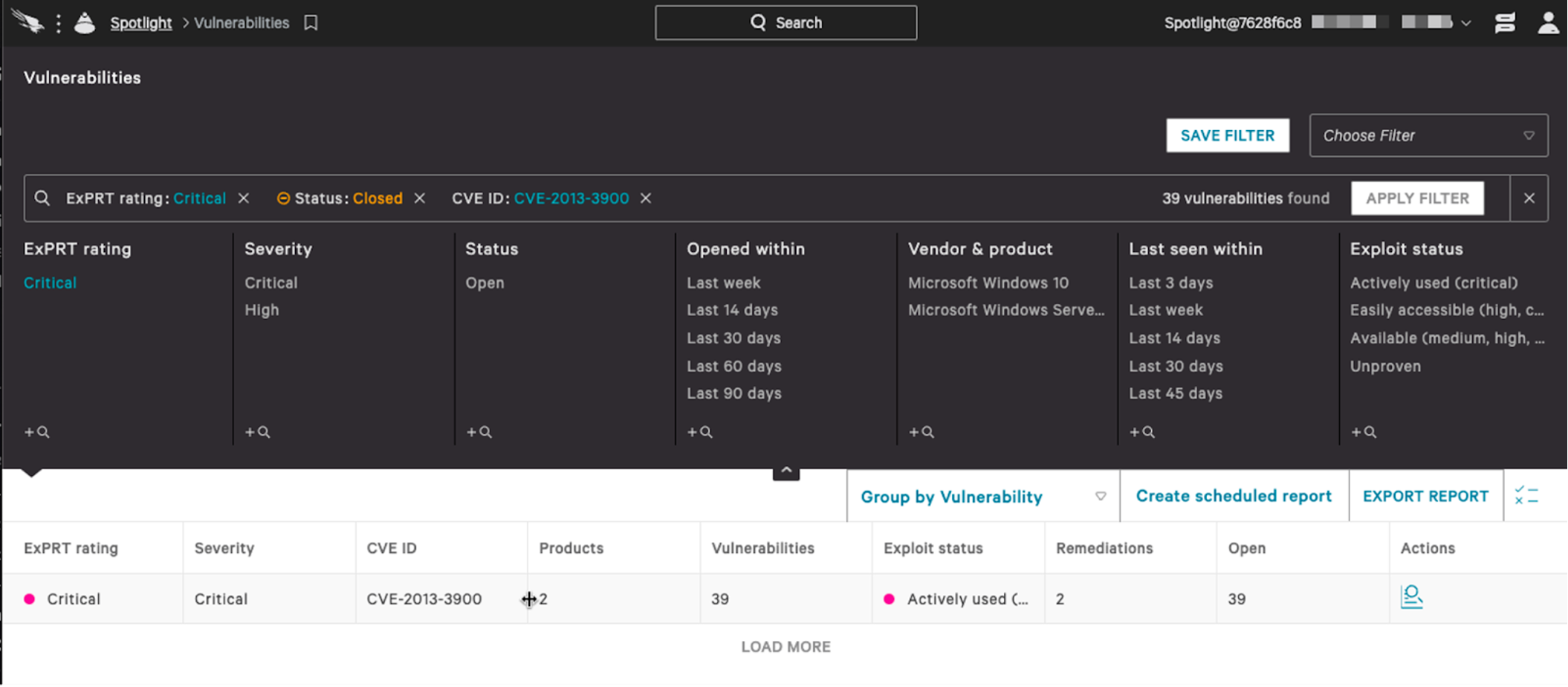 Figure 2. Falcon Spotlight identifying a vulnerability that is actively being exploited by the adversary (click to enlarge)
Figure 2. Falcon Spotlight identifying a vulnerability that is actively being exploited by the adversary (click to enlarge)Mobile: iOS, Android
Similar to endpoints, mobile devices are also routable via IPv4 and IPv6 and, for most, are used to access corporate and federal resources, consequently falling in scope of the BOD. CrowdStrike Falcon® for Mobile extends breach prevention to iOS and Android. For both mobile platforms, we help our federal customers get visibility of their mobile assets while also continuously evaluating those systems for vulnerabilities and misconfigurations. Falcon for Mobile can detect when a system is jailbroken or rooted, or even when it has a malicious application installed that poses a risk to the entire mobile device, data and networks.
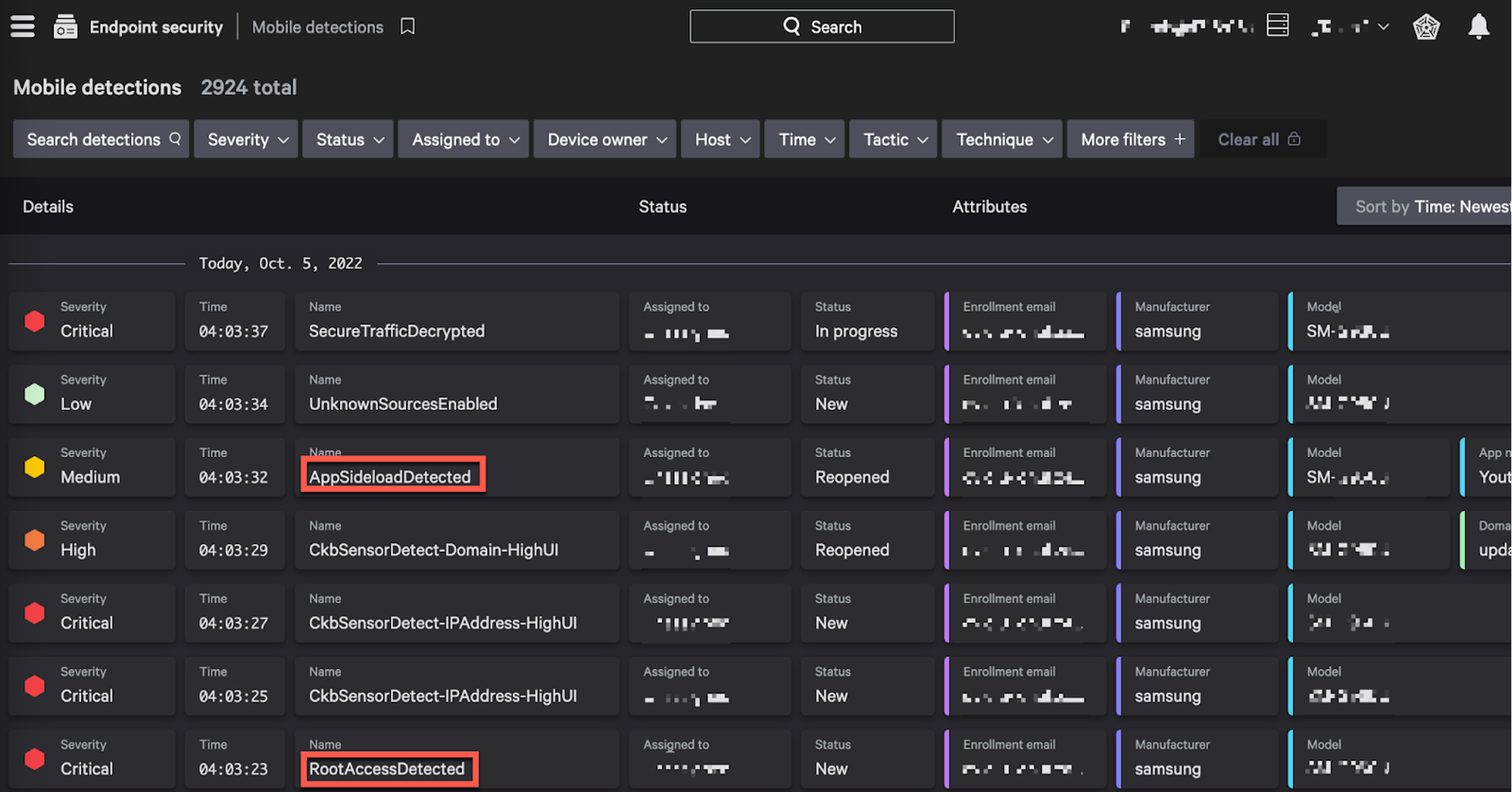 Figure 3. CrowdStrike Falcon® for Mobile providing information on EDR and compliance issues on mobile assets — including Root Access (Android) and Jailbroken (iOS) (click to enlarge)
Figure 3. CrowdStrike Falcon® for Mobile providing information on EDR and compliance issues on mobile assets — including Root Access (Android) and Jailbroken (iOS) (click to enlarge)Multi-Cloud
Of course, cloud resources are only good if we can actually route to them. As federal customers continue to shift toward adopting the cloud, on-premises and cloud infrastructures become more intertwined. Having asset visibility with vulnerability and compliance visibility of our multi-cloud infrastructures is increasingly important. The Falcon platform delivers comprehensive cloud security, combining agent-based and agentless protection in a single, unified platform experience. With CrowdStrike’s powerful cloud-native application protection platform (CNAPP) capabilities, federal customers can identify managed and unmanaged assets in the cloud. CrowdStrike can also ensure cloud objects, at instantiation time, have the Falcon agent deployed for inline security purposes and managed for both visibility and security purposes. Even assets in the cloud that are not infrastructure-as-a-service (IaaS) are still routable and could even be internet facing. Examples include platform-as-a-service (PaaS) and software-as-a-service (SaaS). Above and beyond securing cloud assets from real-time threats — a mission for Falcon Cloud Workload Protection — PaaS and SaaS, similar to IaaS, can be misconfigured and have their vulnerabilities. Falcon Horizon™ helps paint exactly that picture, enumerating cloud assets across Amazon Web Services (AWS), Azure and Google Cloud Platform (GCP) into a single dashboard and platform.
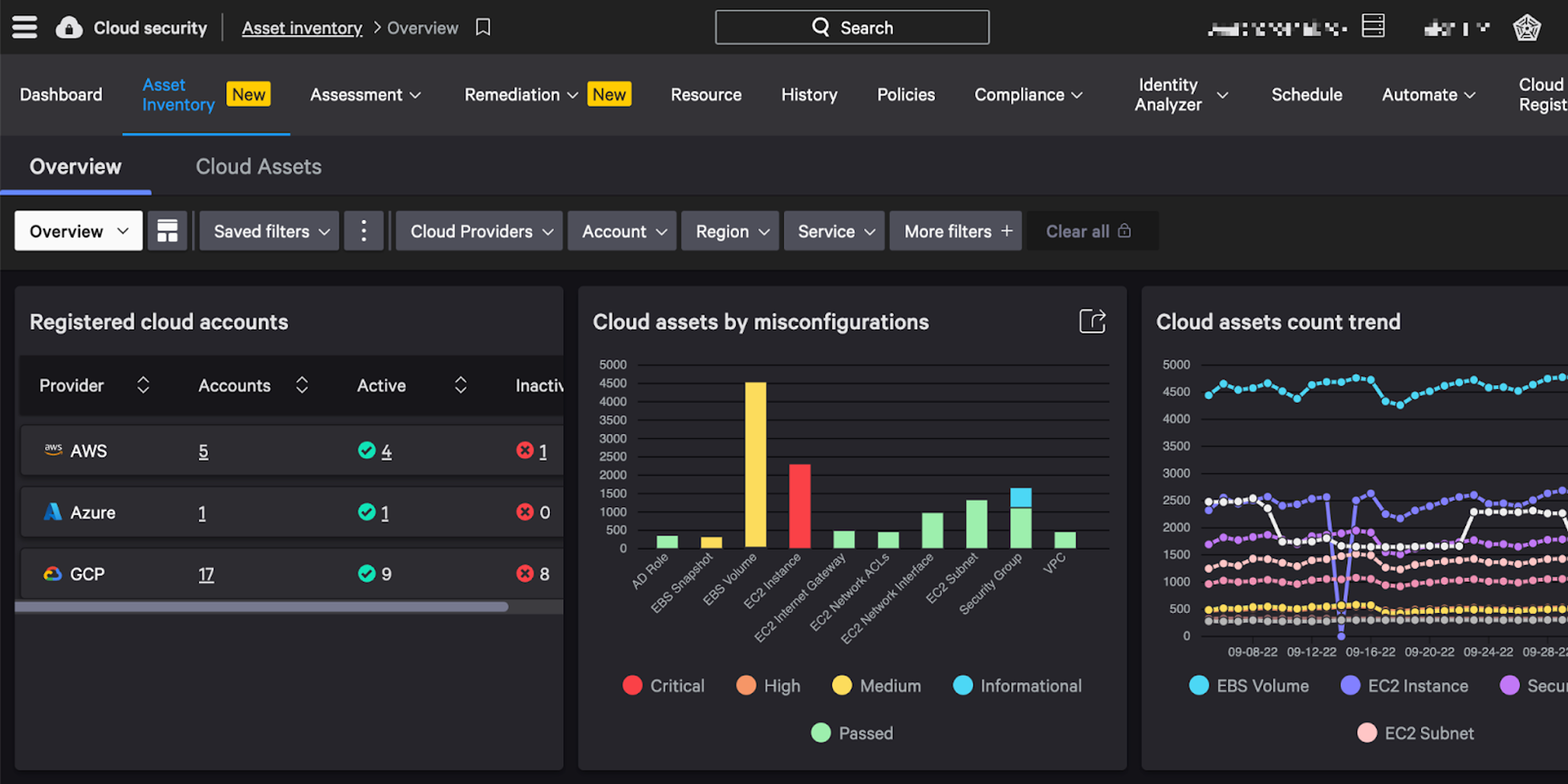 Figure 4. Falcon Horizon discovers all cloud assets in the three largest cloud service providers while providing continuous compliance assessments in a single, extensible (click to enlarge) dashboard
Figure 4. Falcon Horizon discovers all cloud assets in the three largest cloud service providers while providing continuous compliance assessments in a single, extensible (click to enlarge) dashboardCrowdStrike Falcon® enables customers to start with the Center for Internet Security (CIS) benchmarks and also allows the creation for custom policies.
Identity
Beyond endpoints, mobile and cloud, identity is a critical area of concern. If an endpoint is compromised due to vulnerabilities or misconfigurations, all of the identities and credentials they are exposed to are also at risk. The addition of Falcon Identity Threat Protection™ or Falcon Identity Threat Detection™ can provide additional capability to see new assets. The identity plane can become a great data source to discover unmanaged assets that are authenticating with domain accounts. CrowdStrike's Falcon Identity Protection modules give visibility of any asset that is used to authenticate a corporate domain account.
 Figure 5. Falcon Identity Threat Protection showing unmanaged endpoints that are authenticating with domain accounts but not actually domain-joined to Active Directory (click to enlarge)
Figure 5. Falcon Identity Threat Protection showing unmanaged endpoints that are authenticating with domain accounts but not actually domain-joined to Active Directory (click to enlarge)In Figure 5, “unmanaged” assets are endpoints that are not domain-joined yet are exposed to domain credentials, posing risks to the federal agency — or worse, signs of compromised credentials that are now being misused. As our federal customers continue to migrate and leverage the cloud, there is a need to fuse on-premises Active Directory with authentication flows in the cloud. For that reason, Falcon Identity Threat Protection provides that visibility as well, including for Azure AD and Okta. The CrowdStrike Falcon® platform collects and analyzes trillions of endpoint events every day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.
External Attack Surface
Vulnerabilities are not only internal-facing but can expose assets to the internet too. Adversaries are constantly conducting reconnaissance to identify weak points across infrastructure to exploit. Unfortunately, our adversaries sometimes discover unmanaged infrastructure before our cyber network defenders do.
For this reason, CrowdStrike has agreed to acquire Reposify, a powerful external attack surface management (EASM) platform that scans the internet for vulnerable and exposed assets to identify and eliminate risk before an adversary can exploit them. We firmly believe that understanding the adversary’s view of your risk is an important step in defending increasingly complex environments. Merging the external attack surface view with our internal view of assets and their respective vulnerabilities — and compliance levels — will further enable our customers to minimize their total attack surface.
Putting It All Together
Building on our dominant EDR/XDR capabilities, agencies can use Falcon Discover and Falcon Spotlight to extend visibility of assets and gain deeper insights with proactive, actionable and prioritized vulnerability information, all within the same agent — and you can extend to mobile devices and the cloud. All of these solutions not only provide visibility but also compliance, vulnerability and configuration details. Additional visibility from our identity plane, across authentication flows, also helps identify unmanaged devices. The CrowdStrike Falcon® platform delivers the comprehensive capabilities enabling federal agencies to meet and exceed the requirements of Binding Operational Directive (BOD) 23-01 by combining asset visibility and vulnerability detection with industry leading protection across the most critical areas of risk.
Finally, departments and agencies should treat the 7-day and 30-day windows as a performance floor rather than a performance ceiling. Many legacy vulnerability scanning technologies are resource-intensive and may tax federal networks to perform more frequent scans. The technologies described above operate on a real-time basis, so performance would far exceed these minimum standards. Ultimately, CISOs across the FCEB are most empowered with information that reflects conditions now rather than information that is days or even weeks old. Contact CrowdStrike to discuss and receive more details about how we can help you secure your organization while complying with industry regulations and directives. REQUEST INFORMATION
Additional Resources
- Learn more: CISA Selects CrowdStrike to Protect the Nation’s Critical Endpoints and Workloads
- Read about our latest acquisition: CrowdStrike to Acquire Resposify to Reduce Risk Across the External Attack Surface
- Learn how CrowdStrike’s Falcon Spotlight Fuses Endpoint Data with CISA’s Exploited Vulnerabilities Catalog
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)















































