Defend Against Ransomware and Malware with Falcon Fusion and Falcon Real Time Response
Both features are natively integrated into the CrowdStrike Falcon® platform
Adversaries are moving beyond malware and becoming more sophisticated in their attacks by using legitimate credentials and built-in tools to evade detection by traditional antivirus products. According to the CrowdStrike 2022 Global Threat Report, 62% of detections indexed by the CrowdStrike Security Cloud in Q4 2021 were malware-free. Adversaries are also likely to significantly increase their use of ransomware and ransomware-as-a-service (RaaS) operations to bypass security measures, conduct successful initial infections and attack critical infrastructures well into 2022.
Stopping today’s dedicated and sophisticated adversaries requires a combination of automated prevention utilizing the best machine learning (ML) and artificial intelligence (AI) along with human expertise and threat hunting. Detection and response technology is needed to search for and surface threats that have silently bypassed defenses as a result of adversaries’ sophisticated tradecraft and multistage attacks. And these technologies must act quickly, for as noted in the CrowdStrike 2022 Global Threat Report, the average breakout time — the time from when an adversary infiltrates a system to when they move laterally across the organization’s network — is 1 hour 38 minutes.
Reducing incident response time, including containment and automatic remediation, is one of the most effective ways to control the impact of such increasingly sophisticated attacks before they turn into devastating breaches. But security teams, already burdened by a shortage of skilled resources, are often impeded from responding in time because they lack visibility and contextual understanding of the threats.
The CrowdStrike Falcon®® platform, with Falcon Fusion and Falcon Real Time Response (RTR), provides powerful dynamic response capabilities to keep organizations ahead of today’s threats. By arming security teams with the right data, contextual detections and actionable insights, CrowdStrike empowers organizations to respond to incidents and remediate issues with speed and decisiveness.
Accelerating Custom Response and Remediation with Falcon Fusion
Natively integrated into the Falcon platform, CrowdStrike Falcon Fusion leverages the power of the CrowdStrike Security Cloud to orchestrate and automate any complex workflow. Falcon Fusion improves SOC and IT team efficiency and agility by enabling them to build real-time active response and notification capabilities with customizable triggers based on detection and incident categorizations. Fusion also dramatically reduces alert fatigue and frees up resources so analysts can focus on other critical and strategic tasks.
Falcon Fusion integrates with Falcon Real Time Response (RTR) to provide powerful incident response and remediation across the entire Falcon platform via a simple drag-and-drop experience that works at scale across a multi-platform technology stack. Falcon RTR provides powerful remote access capabilities across Windows, Linux and MacOS operating systems to help responders perform investigation and remediation tasks by executing commands on remote hosts. RTR scripts can directly access distributed systems to run a variety of commands to investigate, conduct forensic analysis and completely remediate remote systems, getting them back quickly to a known good state.
Post-remediation actions — like running checks on the system to ensure it is clean, issuing automated notifications via collaboration channels like email, Slack or Microsoft Teams, and updating ticket status on IT management systems — can be performed to ensure full-cycle incident response.
Real-life Customer Use Case for Automated Remediation
Responders need full endpoint activity details and attack visibility to understand each step of the attack. To empower them to take action, Falcon RTR helps contain a system outside the corporate network while still maintaining access to conduct tasks for investigation, hunting, remediation and recovery. Tasks include acquiring process information, file artifacts and memory dumps, searching for particular files or processes, killing malicious processes or deleting files, manipulating registries, deploying a patch or configuration changes, reverting a system snapshot or restoring a system. It helps analysts gather forensic information and arm them with the required surgical remediation capabilities while investigating a threat to quickly understand the full scope and risk magnitude of the incident. Using Fusion, analysts can ensure they leverage the power of RTR and deploy dynamic response actions with automated workflows across a multi-platform stack.
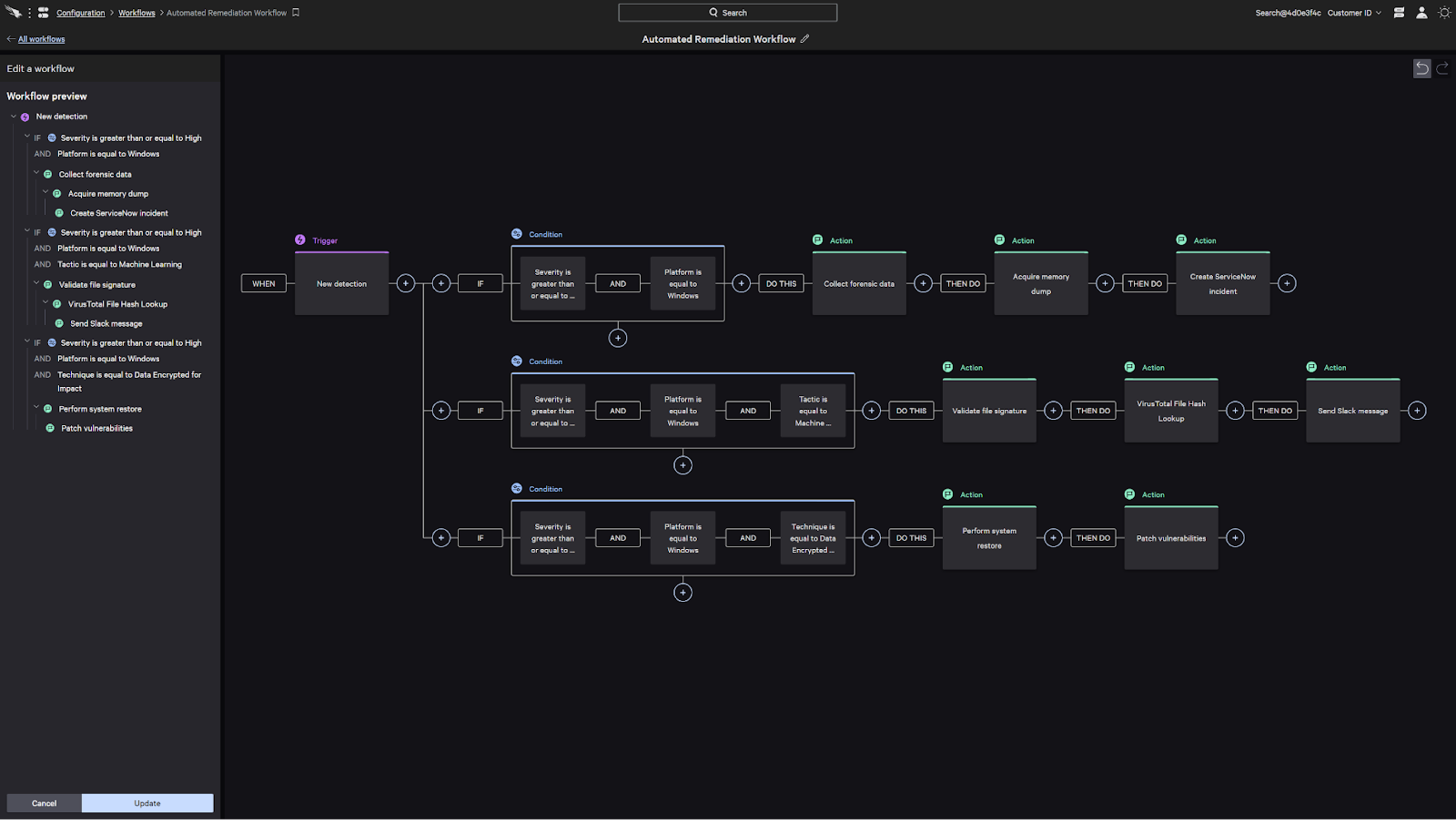
Let’s look at a use case where Falcon Fusion can be used to orchestrate an automated remediation effort. This example shows how a customer can set up automatic response workflows to be launched based on customizable conditions, depending on different scenarios.
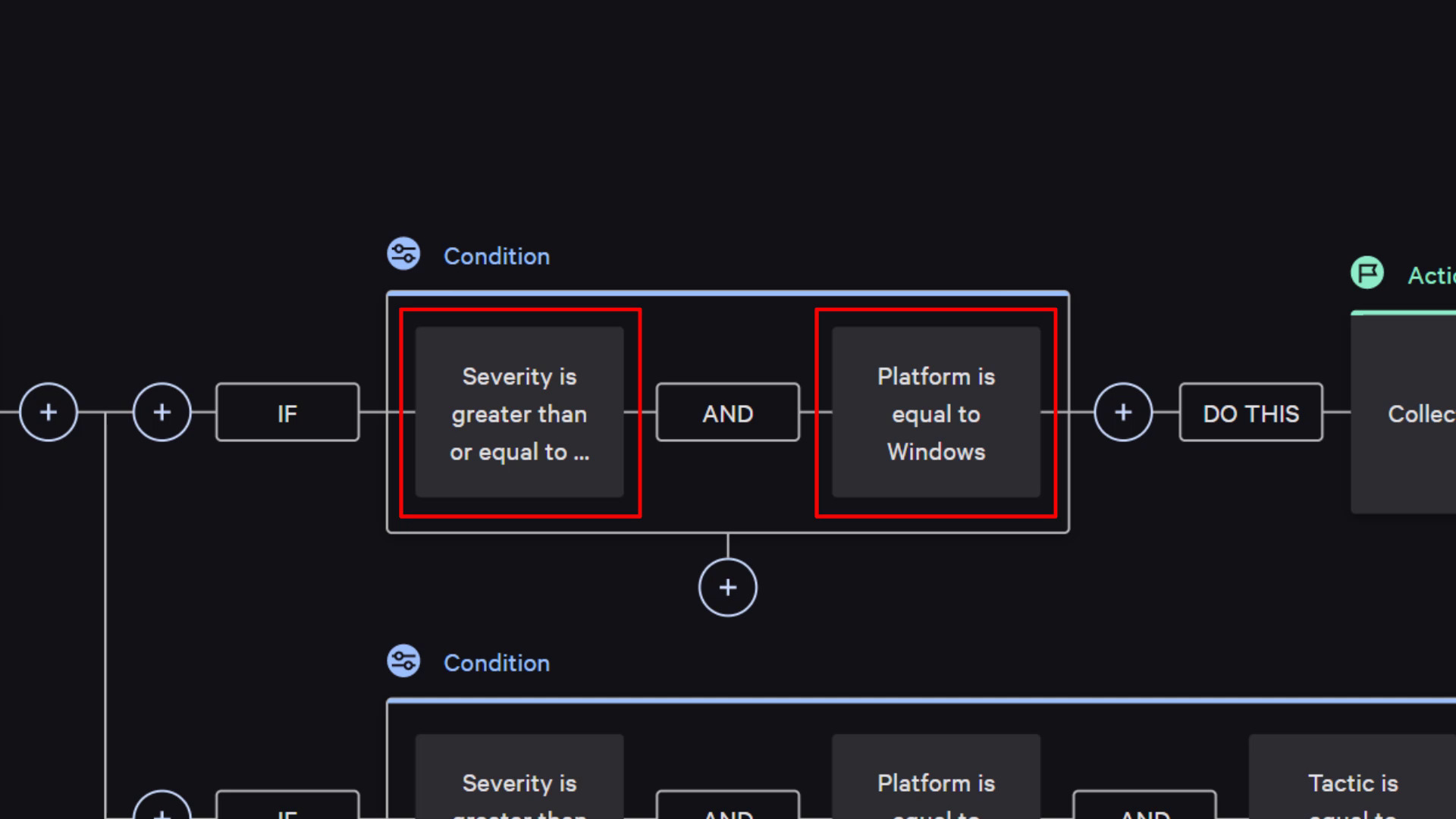
Scenario 1: For any high-severity alert detections, the security team can build a workflow that manages investigation in three steps:
- Complete Forensic activity to search and acquire files that need to be investigated
- Acquire memory dump for additional analysis and hunting
- Create a ticket through a third-party platform like ServiceNow to ensure existing detections are tracked and followed up on with the right attributes
Scenario 2: Taking advantage of Fusion’s if/then conditional logic, the team can add a requirement to the existing conditions to check if it is a machine-learning detection. Fusion helps perform additional context enrichment to aid investigation and communication for high-priority threats:
- Conduct hash lookup of the file using Google VirusTotal to verify the file signature
- Issue a Slack message to the assigned security analyst with the details of the detection
- As a further step, send the suspicious files to a sandbox for detonation and additional investigation
Scenario 3: If there is a similar detection and a MITRE technique has identified that data has been encrypted — indicating an advanced attack like ransomware — the workflow can help with remediation and recovery. It should be noted that such malicious processes are stopped with ML-based prevention policies. As part of layered defense strategy, automated workflows are built to:
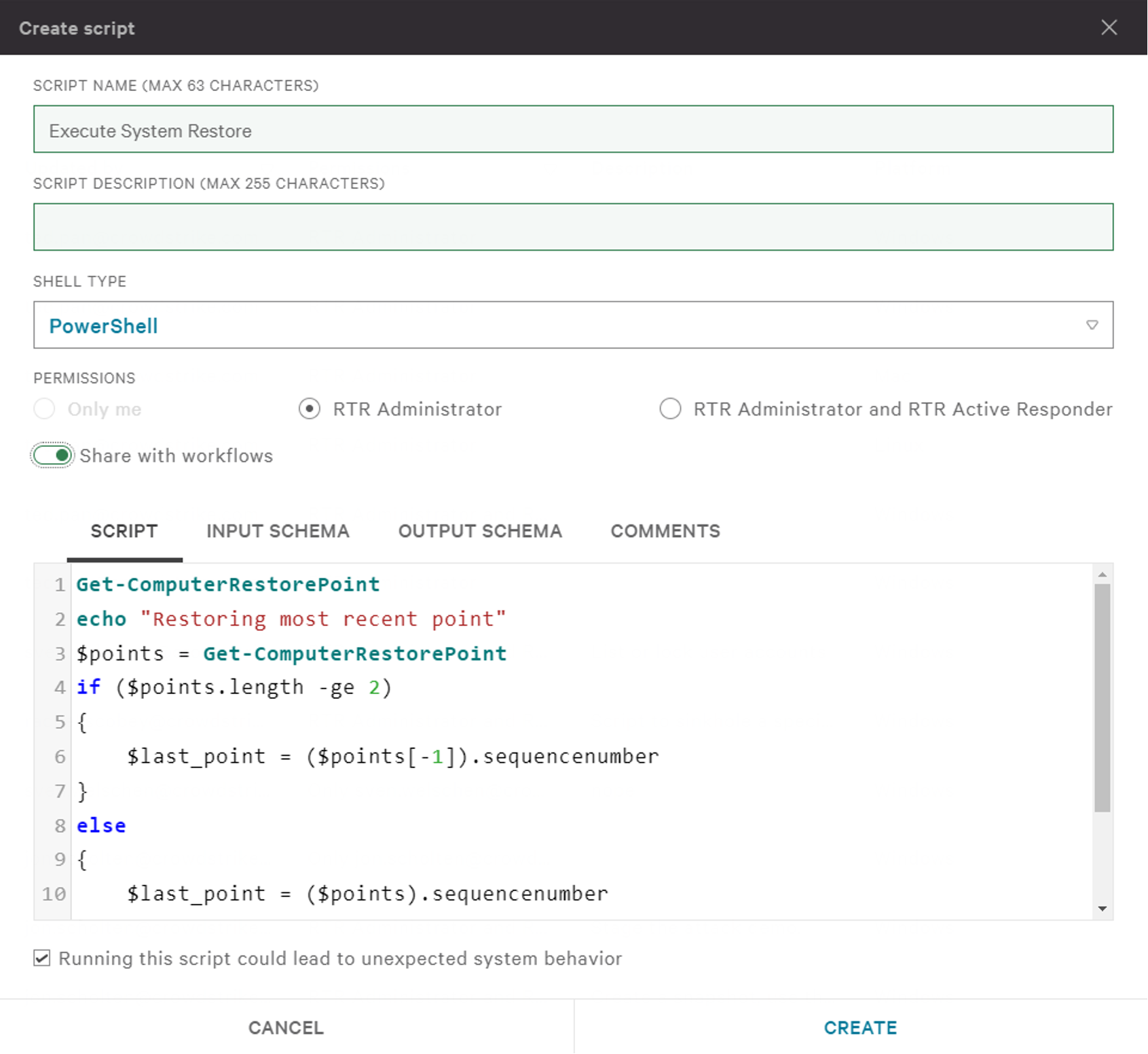
- Run a System Restore custom RTR script that restores the compromised system, containing the threat before it can move laterally in the network
- Run a post-health check to ensure that the malicious processes have been terminated and all signs of compromise have been removed
- Ensure that any existing vulnerabilities are patched and critical software updates are applied as part of the recovery process
Watch Falcon Fusion in action in this short demo
As shown in the different scenarios, Fusion and RTR combine the powerful ability to help custom scripts turn into remediation and recovery actions, allowing for limitless options and customized response actions that fit the customer’s business need when resolving security incidents.
Putting It All Together
When a cyberattack is discovered, responders have two urgent goals: to understand the threat and then take action to remediate. Ideally, organizations should strive to isolate or remediate the problem within 1 hour. Automation with Falcon Fusion and RTR helps restore hosts to their original state before they were compromised, with minimal downtime, and reduces alert fatigue. This also ensures that the spread of malware and sophisticated threats across environments is contained before it becomes a breach.
Customers can take advantage of Falcon Fusion with custom RTR scripts within the Falcon platform to orchestrate and automate incident investigation, response and remediation actions across distributed endpoints and workloads at scale, with minimal impact to productivity and user experience, starting today.
Start your free trial now and realize the benefits of the Falcon Fusion SOAR framework. Access Falcon Fusion from your Falcon console to see how you can simplify your SOC and IT workstreams, while achieving speed and precision.
Additional Resources
- Learn more about the Falcon Fusion integrated cloud-scale framework by visiting the product page.
- Get technical details about Falcon Fusion by viewing the data sheet.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.