Any cyberattack can have a significant impact on business operations, but perhaps none are as sophisticated as kernel attacks.
Kernel attacks exploit the zero-day operating system vulnerabilities in the kernel or other kernel drivers even after they have been patched. In a typical kernel attack, adversaries install and load a known vulnerable driver to gain access to the system, elevate their privileges and then make changes. While most operating systems only allow legitimate vendors to create and sign a driver, it is possible for cybercriminals to leverage these legitimate but vulnerable drivers.
Malicious actors can then leverage this vulnerable driver to access the kernel, where they can perform any number of actions, including deleting or deactivating security measures. Since these drivers are legitimately signed and certificate revocation is difficult, unpatched versions of the drivers can be used “in the wild” for years without being detected or blocked.
Kernel attacks are incredibly sophisticated and therefore somewhat rare. However, they are becoming more common. One prominent example of such an attack is a new zero-day vulnerability within Microsoft's Cryptography Driver (cng.sys), published by Google Project Zero late last year.
This vulnerability occurs within a specific input/output control (IOCTL) path inside the driver, allowing user-mode applications to easily exploit it. In addition to reporting the vulnerability, Google also disclosed that the code was actively being exploited as a way to escape Chrome’s security sandbox and carry out further attacks. Learn more about the Windows kernel vulnerability disclosed by Google's Project Zero.
The Solution: Upgrade to Falcon Sensor 5.41+
Unfortunately, the nature of how kernel drivers are signed and loaded makes it difficult for the operating system to defend or prevent these attacks. This means it is incumbent upon the end user to detect and prevent such attacks through a robust security strategy and toolset. For CrowdStrike customers, the latest releases (5.41+) of the CrowdStrike Falcon® sensor have made a number of improvements to help detect and prevent both vulnerable and malicious drivers from being loaded, and secure the vulnerable IOCTLs that those drivers expose. More importantly, these features are all cloud-controlled. As long as the user is running version 5.41 or later, CrowdStrike can provide the same level of security without having to upgrade the physical sensor.
Given how devastating kernel attacks can be, we urge our customers to help protect against such attacks by upgrading their Falcon sensor software today. We understand that customers often delay upgrades because they need to validate the update and test it on a few machines before rolling it out more broadly. But in this case, we strongly recommend upgrading immediately as kernel attacks can be very disruptive, costly and time-consuming to the business. For example, several high-profile ransomware attacks in 2019 by a group known as RobbinHood leveraged legitimate hardware drivers to exploit a known software vulnerability, CVE-2018-19320. They used this point of access to subvert kernel memory settings and delete cybersecurity defenses. This attack had several high-profile targets, including the City of Baltimore, and experts suggest that the total ransom across all victims could be in the millions. Learn more about the RobbinHood attacks.
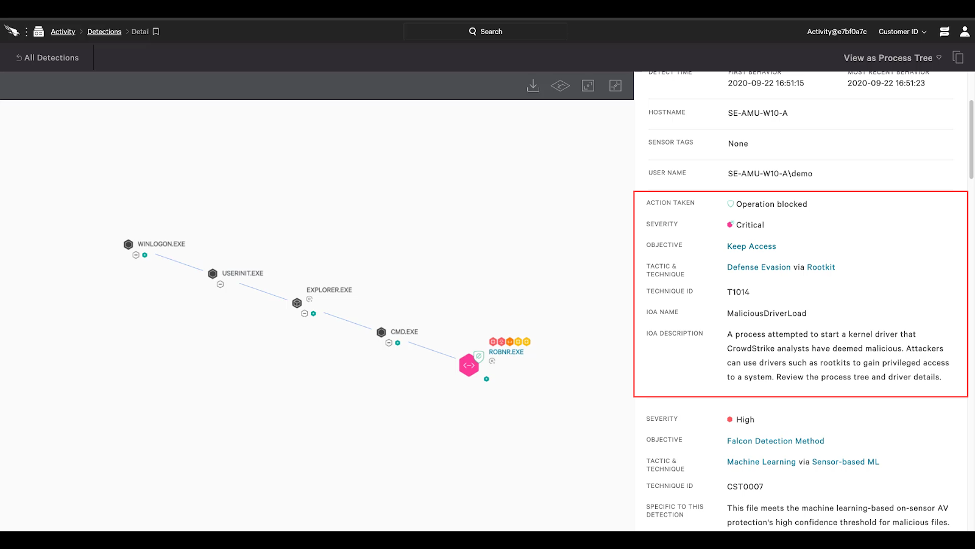 Figure 1. Blocking of the RobbinHood ransomware driver (click here to enlarge)
Figure 1. Blocking of the RobbinHood ransomware driver (click here to enlarge)Enabling These Improvements on the Falcon Sensor
In order for the Falcon sensor to have the detection capability of user-mode interaction (via IOCTLs) with vulnerable device drivers, Additional User-Mode Data (AUMD) must be enabled within the Falcon prevention policies. To enable the Falcon sensor to block and prevent exploitation of these vulnerable device drivers, the Suspicious Processes toggle (Malware Protection → Execution Blocking) must be enabled within Falcon prevention policies.
Blocking Malicious Drivers
Drivers that CrowdStrike has identified as malicious can be blocked from loading on Windows 10 / Server 2016 by enabling the Suspicious Kernel Drivers toggle (Malware Protection → Execution Blocking) within Falcon prevention policies.
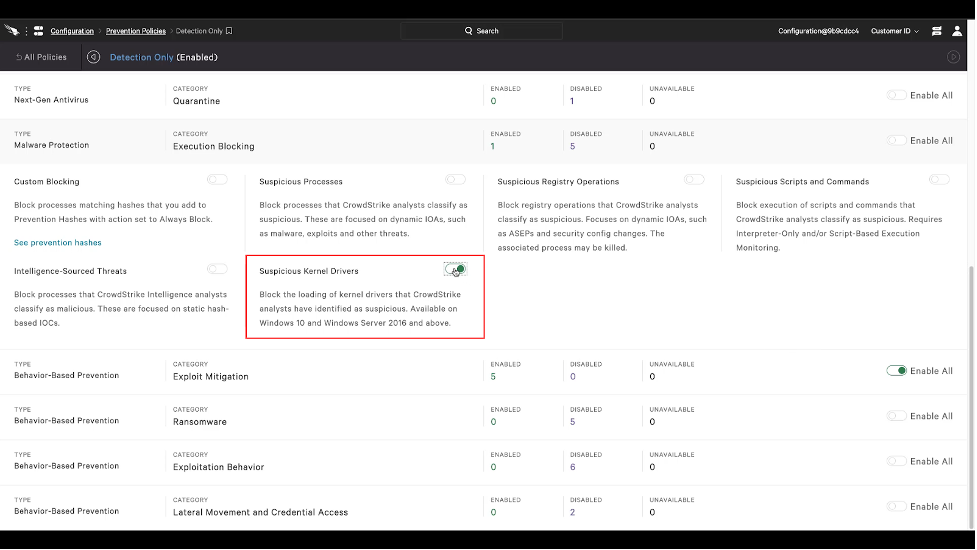 Figure 2. Policy toggle to enable Suspicious Kernel Driver prevention (click here to enlarge)
Figure 2. Policy toggle to enable Suspicious Kernel Driver prevention (click here to enlarge)Final Thought: Protect Your Organization From Kernel Attacks Today
It is important for all organizations to take the necessary steps to prevent kernel attacks. For CrowdStrike customers, we strongly recommend upgrading to Falcon Sensor 5.41 now if you haven’t already done so. Others should contact their cybersecurity partner to learn more about the steps being taken to protect against these attacks and the solutions available — you can also reach out to CrowdStrike to schedule a consultation and demo. References:
- https://bugs.chromium.org/p/project-zero/issues/detail?id=2104
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-17087
- https://www.crowdstrike.com/en-us/blog/how-to-detect-and-prevent-kernel-attacks-with-crowdstrike/
Additional Resources
- Read a white paper on the Evolution of Ransomware.
- Learn more about the CrowdStrike Falcon® platform by visiting the product webpage.
- Learn more about CrowdStrike endpoint detection and response by visiting the Falcon Insight™ webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
















































