Kovter is a well known form of clickjacking malware that has been around for years. While it is mostly nuisance malware, it incorporates neat tricks that are far more advanced than its use case would indicate. It’s notable for its (mostly) fileless architecture and application whitelist bypass capabilities using normal Windows tools. OWASP defines clickjacking, also known as a "UI redress attack," as a malicious technique that “uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page.” While Kovter has been reverse engineered and written about numerous times over the past few years, it's still being seen in the wild. We've decided to pull together a process flow for remediation and some PowerShell commands that can be used by analysts as an alternative to sending the IT helpdesk for yet another rebuild request. This blog post is for those interested in learning how this malware works. It also provides a step-by-step guide that will show you how to stop it in its tracks.
Processes
The first step in remediating Kovter is to kill the running processes. Kovter utilizes either Explorer.exe or Regsvr32.exe to launch and run in memory. There are at least two processes, which are watcher processes. They’ll watch to make sure the other process is running and they’ll also watch for the artifacts on disk and in the registry, and drop them back out from memory if the processes aren’t both killed at the same time. In most normal environments, it’s not typical to see any Regsvr32.exe processes running for any length of time in memory. If it’s running, it’s potentially nefarious and should be reviewed. Additionally, you don't typically see more than one explorer.exe process running. (If you have different users "switch" logins, you'll see multiple explorer.exe instances running, but otherwise, more than one could mean bad things). Finally, Kovter utilizes the 32bit binaries, thus, the executable path will be syswow64 – a dead giveaway on 64bit systems. To identify bad versions of explorer and Regsvr32.exe, look at the number of libraries loaded in its memory space and where on disk the process was launched. Here are a few PowerShell (PS) commands to help identify the Kovter processes (there are at least two, but we've seen up to six).
Identify Bad
When the normal Explorer.exe loads, it requires numerous DLL files to operate. Kovter launches at least two new instance of Explorer.exe or Regsvr32.exe. Looking at its process memory space, you won’t find but a few DLLs loaded, as it only loads what is needed. This script looks for any explorer.exe files that have less than 10 DLLs loaded, and outputs the process ID labeled good or bad.
foreach ($proc in (get-process explorer).id) { $modules = (get-process -id $proc).modules | Measure-Object if ($modules.Count -lt 10) { Write-Host "$proc bad"} else { Write-Host "$proc good" } }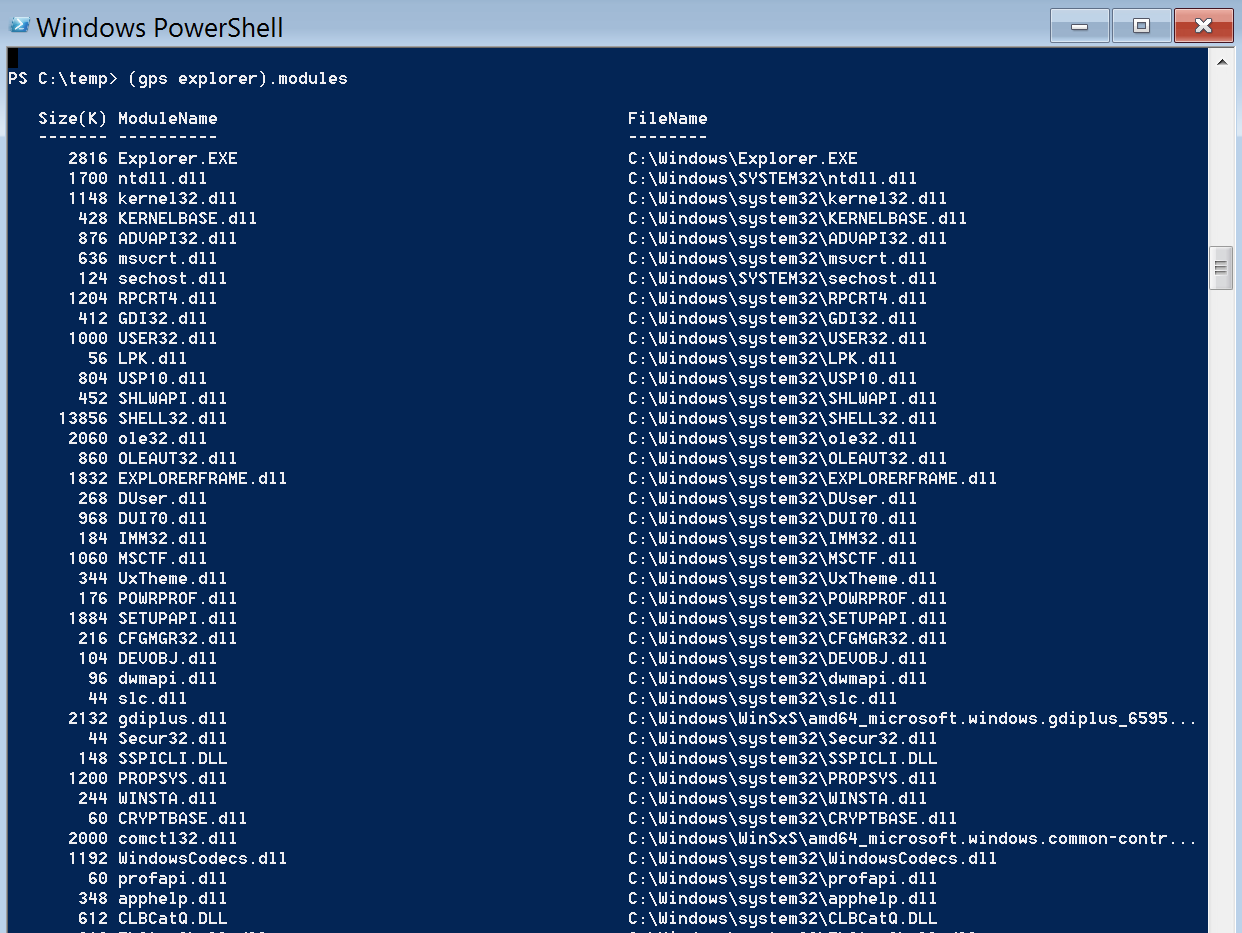
Snippet of good Explorer.exe
This script provides the path for each explorer process. get-process explorer |select name,path
Kill Bad
After checking to make sure the processes are indeed bad, and that you're comfortable killing known bad processes, this script will kill the tasks for you.
foreach ($proc in (get-process explorer).id) { $modules = (get-process -id $proc).modules | Measure-Object if ($modules.Count -lt 10) { stop-process -id $proc -force } }Files on Disk
As stated earlier, Kovter is "mostly" fileless. The purpose of the files on disk might surprise you. They're there for persistence, and it's really quite ingenious. Generally, a .lnk file will be placed in the user’s start menu startup folder (c:\users\<user>\appdata\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\) that calls a file on disk. The extension for this file is registered in the registry under hkcu\software\classes\.<4-9 chars that match the file extension on disk>. Once the file is called, Windows needs to know how to open it, so it looks to the classes key in the registry. This kicks off a string of events that eventually calls the malware code stored in registry keys; more on that later. Common locations and naming schemes: %localappdata%\<random>\<random>.<4-9 file ext> %localappdata%\<random>\<random>.lnk %localappdata%\<random>\<random>.bat %appdata%\<random>\<random>.<4-9 file ext> %appdata%\<random>\<random>.lnk %appdata%\<random>\<random>.bat C:\windows\<random 4 chars starting with digit> C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\*.lnk Below are two scripts to identify bad file extensions. You’ll want to watch out for false positives. Modify the “-exclude” and “-not” match switches if necessary. Always review the output before taking action.
Get-ChildItem c:\users\*\appdata\local\* -exclude temp -force -ea silentlycontinue | ?{$_.extension -match '{4,10}$|lnk' -and ($_.extension -notmatch 'json|html')} | select -expandproperty fullnameLook at Roaming, Too
Get-ChildItem c:\users\*\appdata\roaming\* -exclude temp -force -ea silentlycontinue | ?{$_.extension -match '{4,10}$|lnk' -and ($_.extension -notmatch 'json|html')} | select -expandproperty fullnameNon Autorun Registry Keys
The file extensions registered in the registry simply point to another key under classes. This next key has the mshta.exe or cmd.exe code which calls yet another key. hkcu\software\classes\.<4-9 chars> (note the period before the 4-9 random chars) Points to this: hkcu\software\classes\<4-9 chars>\shell\open\command The mshta.exe or cmd.exe calls a key containing the actual malware using a command similar to this:
"C:\windows\system32\mshta.exe" "javascript:KMo6XCO="S8";OC35=new ActiveXObject("WScript.Shell");ifW25z="RxM9IO";J1bNb=OC35.RegRead("HKCU\\software\\vjeiyyhuv\\colku");D5tNUwC="Isgg";eval(J1bNb);uAqn53="yc";"Which calls this: HKCU\Software\<6-10 chars> HKLM\Software\Wow6432node\<6-10 chars> The contents of these keys will resemble this:
HKEY_USERS\S-1-5-21-0000000000-0000000000-00000000-500\software\rbdurfz
gqkh
REG_SZ
¨ø5'&aA ? >DO IUAo$P+Yñ'EU_m ö.IA{x,«U5¥I1'?=k¯£%Z„{æi§or<™Ÿ,6rE3`Q¥@hI', ~-e#¡-A#Dú
ddeuavxkdd
REG_SZ YBhBU8KlAFQjjo="oVd2iDQ8035WsbYy7TeBZ";hCGKpNJhaz4="0hPD7yXYWXeeQkLQNqx5VcB4Gt3sx1Gr";kOPoPylr6gsrnfkbq="IfuAhNSu9z3vgOh";zgzYGcEcvs5fBNwwVl="frdA4TykXO9xg2HBH";lwHdDvGAHk4XgUR="OivoPSC8sYE";p1JkcMHFbHtJaqRdGZ="bAk1VlfxAkC2JVB7z2nzi6cdOTsvxUc72LduzPq";Bp3p="3C1B033F1C200F3E04304579032B110D0137194E5E0A1A213481D130A495…
foqqecrz
REG_SZ Q/NZxIzXPbA==
gajrfyarg
REG_SZ Efc4iaZ1Z+Zpk7C9nJ+xGpeA=
zzudifjy
REG_SZ S6Bdyc4eJ5ZZ+aWUgQI=
ceioplwdce
REG_SZ EPFYk4icN/PDM2KOEMBIxJ7SGCfWDG7+08gD76R/2h0CD+1tea7YZaCDP4mtJ3N0m/+pphQ4spw/xu7uss
fahsc
REG_SZ E/NdlN6ZMuCjM4L7xpE4K7nu9Wro1nZnEWCygpV4/dwYgg==
rlvofd
REG_SZ QqdXkovMMvGOlgaYjS6wWTrjo8maNr3q7G+IgqiJIJdHObsEHUDLWjFcp1bByx8v3G1WLdWvGCOeaug6wOzTi+AGjyDHeVAmDYpNp4LAtf…
$keylist='<keyname>','<keyname>' $keys = @() $keys += foreach ($key in $keylist) { reg delete $key /f }Autorun Registry Keys
If you thought registering file extensions in the registry was a cool persistence trick, the run key that Kovter implements will really blow you away. Kovter will create a new registry entry under a few different run keys. The value data contains the same mshta.exe or cmd.exe code as the file extension keys point to, which calls the hkcu\software or hklm\wow6432node\software key containing the malicious code to run. The value name of this registry key contains either a null byte or an unreadable ascii character. When accessing this key through regedit, it gives an error message such as this: 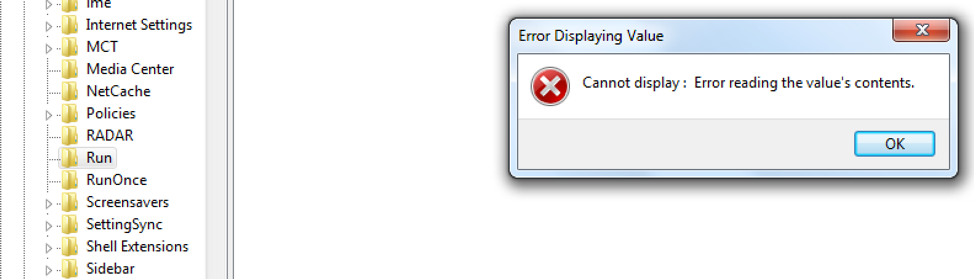 If using the command line with reg query or PowerShell, you'll see "(Default) REG_SZ (value not set)". This is unique because you should only see the "(Default)" key without the "(value not set)". Regedit, reg query, or any other tool that we've sampled cannot read the value name. They don’t know how to present the null byte value. One thing of note is that Autoruns does see the value data, but the value name is, again, represented as "(Default)". The most common run keys are these:
If using the command line with reg query or PowerShell, you'll see "(Default) REG_SZ (value not set)". This is unique because you should only see the "(Default)" key without the "(value not set)". Regedit, reg query, or any other tool that we've sampled cannot read the value name. They don’t know how to present the null byte value. One thing of note is that Autoruns does see the value data, but the value name is, again, represented as "(Default)". The most common run keys are these: HKLM\software\wow6432node\microsoft\windows\currentversion\policies\explorer\run HKLM\software\wow6432node\microsoft\windows\currentversion\run HKCU\software\microsoft\windows\currentversion\run In order to remove the bad values without being able to reference the value, we decided to delete the entire run key and recreate it. That works great, unless there are other values that are needed in the run key. There are a few ways to recreate the good entries: You can do it manually, but where’s the fun in that? We decided to whip up some PowerShell. Interestingly, since PowerShell cannot reference the malicious entries, you can copy the contents of the run key to a temporary location without copying the bad stuff, as it is only capable of reading/copying the good entries. The PowerShell below accomplishes the task:
- Create a temporary key
- Copy the contents of the run key to the temp location (this will fail and error on the bad value, but that’s what we want)
- Delete the run key
- Recreate the key fresh
- Copy the temporary key contents back into the new run key
$regpath = (gp
registry::\<regkey>).psparentpath New-item "$regpath" -name temp Get-Item "$regpath"\run | select -ExpandProperty Property |foreach { Copy-ItemProperty -Path "$regpath"\run -Destination "$regpath"\temp -Name $_ -Verbose } Remove-item "$regpath"\run
-rec New-item "$regpath" -name run Get-Item "$regpath"\temp| select -ExpandProperty Property | foreach { Copy-ItemProperty -Path "$regpath"\temp -Destination "$regpath"\run -name $_ -verbose } remove-item "$regpath"\temp -recIt is important to keep in mind that if other users have logged onto the system during the time it was infected, those user registry hives will need to be remediated as well. The key here is that the file extension is registered under the users “usrclass.dat” hive. Hkcu\software\classes is a virtual alias of hku\<usersid>_classes. In order to fully remediate Kovter from all users’ registry hives, you’ll need to load both the ntuser.dat hive to remove the malicious run key entry, and the usrclass.dat file for the malicious file extension and shell\open\command keys. Reg load hku\<user_ntuser> c:\users\<user>\ntuser.dat And: Reg load hku\<user_usrclass.dat> c:\users\AppData\Local\Microsoft\Windows\Usrclass.dat
Conclusion
We've heard from a handful of security analysts who say they just send their tech support team a rebuild ticket whenever they find a system infected with Kovter. It is a tough malware to remediate. It uses some advanced tricks for persistence and hides quite well in the registry. While it has been written about many times over the years, we’ve not seen any actual removal instructions – only a few product-specific binaries available to download and run on your system to do “who knows what?” Hopefully, armed with an understanding of the mechanics – and some PowerShell – you can kill this malware in its tracks without having to bother your support team, or the user. The author will be conducting a session at the Fal.Con POWER UP 2018 cybersecurity conference in Miami, Sept. 17-19, 2018, where he will discuss more about remediation and strategies SOC analysts can use in their day-to-day jobs.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
















































