As part of June’s Patch Tuesday, an update for CVE-2021-1675 “Windows Print Spooler Remote Code Execution Vulnerability” was published. However, weeks later, researchers uncovered that the CVE-2021-1675 patch did not address many of the vulnerabilities associated with Print Spooler and published a working exploit that bypassed these updates.
Amid this confusion, Microsoft acknowledged a working exploit and assigned another CVE (CVE-2021-34527), stating that the recently disclosed exploit code leveraged a different attack vector. Before a patch was available, Microsoft suggested many of the same workarounds that the security community had already identified. In early July 2021, Microsoft pushed out an out-of-band (OOB) update to address CVE-2021-34527 directly to mitigate some of the issues that went unaddressed by the June patches.
The name “PrintNightmare” is apropos since it turns out that the July OOB updates did not fully address CVE-2021-34527. While Microsoft wrote that the OOB round of updates “fully addresses the public vulnerability,” this unfortunately did not prove to be the case — mere hours after the release of these patches, multiple security researchers found that it was not only possible but straightforward to bypass the new patch under certain conditions. Making matters worse, exploit code has been incorporated into popular tools such as Metasploit and Mimikatz, while a full patch remains elusive. CrowdStrike Intelligence assesses that PrintNightmare will almost certainly be adopted by threat actors of all types in the near term. Threat actors may take advantage of possible remote code execution (RCE) and local privilege escalation (LPE) abilities, drawing on the availability of examples in popular exploit frameworks. Adding in the difficulty that SecOps teams have in implementing workarounds and configuration changes, PrintNightmare becomes an attractive exploit for attackers.
Falcon Endpoint Protection Secures Enterprises Against PrintNightmare
The CrowdStrike Falcon® platform provides layered coverage against malicious threats by leveraging machine learning and indicators of attack (IOAs) to target the behavior of malicious processes or files on an endpoint even when dealing with previously unknown threats. As a result, CrowdStrike develops Falcon mitigations that target the tactics and techniques used by adversaries — and that equally applies to the activity and tradecraft associated with this PrintNightmare exploitation.
Our Falcon OverWatch™ team constantly hunts to identify whether adversaries are actively leveraging this vulnerability. Therefore, we recommend that CrowdStrike customers review their Falcon prevention policies and ensure that settings are consistent with best practices. In addition to prevention policy best practices, the Falcon Support Portal also includes additional hunting suggestions and guidance using Falcon Real Time Response to deploy mitigations. If you are not yet a customer, you can start a free trial of the Falcon Spotlight™ vulnerability management solution today.
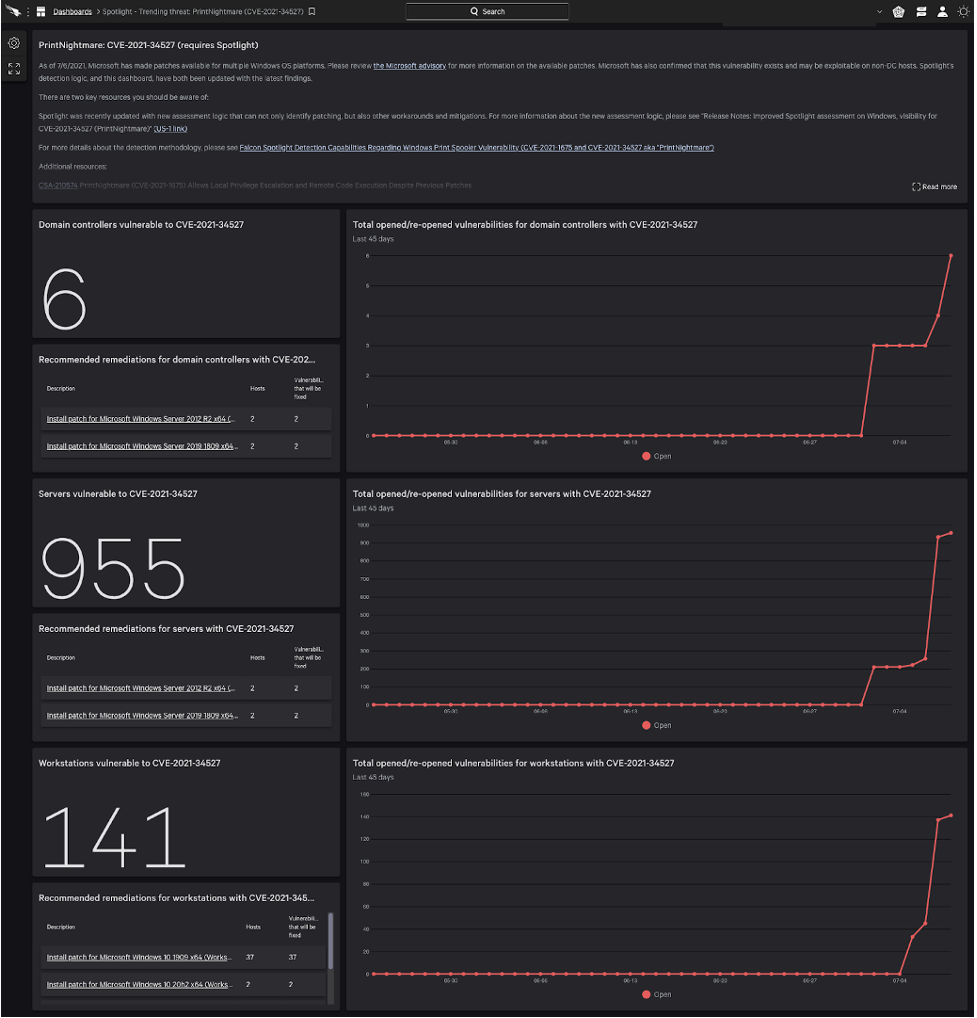 Figure 1. Falcon Spotlight provides a trending threat dashboard to monitor PrintNightmare (Click to enlarge)
Figure 1. Falcon Spotlight provides a trending threat dashboard to monitor PrintNightmare (Click to enlarge)CrowdStrike recognizes the criticality of this situation and has released detections for PrintNightmare vulnerabilities and a dedicated dashboard so organizations can easily track their exposure and remediation efforts (see Figure 1). Falcon Spotlight was also recently enhanced with new detection logic that takes into account multiple workarounds that may have been implemented, such as disabling the print spooler service or Point and Print. Updates will continue to be released as this situation evolves.
To see how Falcon Spotlight works in action, watch this Falcon use case video and learn how you can quickly see and resolve any vulnerabilities in your environment.
Additional Resources
- Learn more about Falcon Spotlight.
- Read CrowdStrike’s analysis on the June Patch Tuesday release.
- See how you can schedule secure, custom reports for your team within Falcon Spotlight.
- Watch how to use Falcon Spotlight and Real Time Response (RTR) for emergency patching.
- Read about the custom CrowdStrike dashboard developed for the Baron Samedit vulnerability.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































