Ransomware Definition
Ransomware is a type of malware that encrypts a victim’s data where the attacker demands for a “ransom”, or payment, in order to restore access to files and network. Typically, the victim receives a decryption key once payment is made to restore access to their files. If the ransom payment is not made, the threat actor publishes the data on data leak sites (DLS) or blocks access to the files in perpetuity.
Ransomware has become one of the most prominent types of malware targeting a wide variety of sectors including government, education, financial, and healthcare sectors, with millions of dollars extorted worldwide every year.
How Do Ransomware Attacks Work?
Regardless of the different types of ransomware, which we will discuss shortly, they tend to follow the following process.
Step 1: Infection
Ransomware operators often use phishing emails and social engineering techniques to infect their victim’s computer. In most cases, the victim ends up clicking a malicious link in the email, introducing the ransomware variant on their device.
Step 2: Encryption
After a device or system has been infected, ransomware then searches for and encrypts valuable files. Depending on the variant, the malicious software may find opportunities to spread to other devices and systems across the organization.
Step 3: Ransom Demand
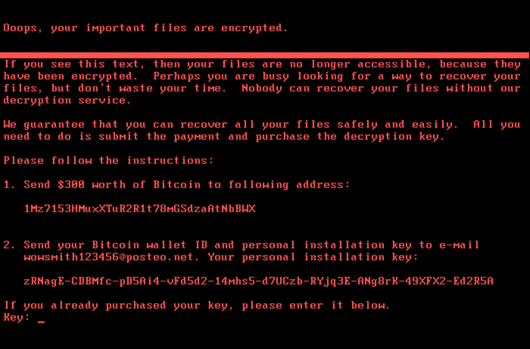
Once the data has been encrypted, a decryption key is required to unlock the files. In order to get the decryption key, the victim must follow the instructions left on a ransom note that outline how to pay the attacker – usually in Bitcoin.
Ransom Letter from Hackers Demanding Bitcoin
Types of Ransomware
- Encrypting Ransomware: In this instance the ransomware systematically encrypts files on the system’s hard drive, which becomes difficult to decrypt without paying the ransom for the decryption key. Payment is asked for using BitCoin, MoneyPak, PaySafeCard, Ukash or a prepaid (debit) card.
- Screen Lockers: Lockers completely lock you out of your computer or system, so your files and applications are inaccessible. A lock screen displays the ransom demand, possibly with a countdown clock to increase urgency and drive victims to act.
- Scareware: Scareware is a tactic that uses popups to convince victims they have a virus and directs them to download fake software to fix the issue
Ransomware Examples
Knowing of examples of ransomware attacks can help understand how specific variants work and how to best protect for each one. Some variants include:
| Variant | Description |
|---|---|
| CryptoLocker | CryptoLocker ransomware was revolutionary in both the number of systems it impacted and its use of strong cryptographic algorithms. The group primarily leveraged their botnet for banking-related fraud. |
| NotPetya | NotPetya combines ransomware with the ability to propagate itself across a network. It spreads to Microsoft Windows machines using several propagation methods, including the EternalBlue exploit for the CVE-2017-0144 vulnerability in the SMB service. |
| Ryuk | WIZARD SPIDER is a sophisticated eCrime group that has been operating the Ryuk ransomware since August 2018, targeting large organizations for a high-ransom return. |
| REvil (Sodinokibi) | Sodinokibi/REvil ransomware is commonly associated with the threat actor PINCHY SPIDER and its affiliates operating under a ransomware-as-a-service (RaaS ) model. |
| WannaCry | WannaCry has targeted healthcare organizations and utility companies using a Microsoft Windows exploit called EternalBlue, which allowed for the sharing of files, thus opening a door for the ransomware to spread. |
| Conti | Conti’s utilization of compiler-based obfuscation techniques, such as ADVobfuscator, provide code obfuscation when the ransomware’s source code is built. Portions of Conti’s source code are restructured or rewritten regularly with the intention of avoiding detection and disrupting automated malware analysis systems. |
| Maze | Maze ransomware targets multiple industries and organizations across the whole globe. It is relatively new and is known for releasing private data into the public if the victim of a ransomware attack does not give into the attacker’s demands. |
| BlackCat | Blackcat ransomware is popular because it is one of the first professional ransomwares that was written in Rust, a more secure programming language. This makes it easier to customize the malware for different operating systems. |

2024 CrowdStrike Global Threat Report
The 2024 Global Threat Report unveils an alarming rise in covert activity and a cyber threat landscape dominated by stealth. Data theft, cloud breaches, and malware-free attacks are on the rise. Read about how adversaries continue to adapt despite advancements in detection technology.
Download NowWho Are the Main Targets of Ransomware Attacks?
Ransomware was originally introduced to target individual systems such as the personal computers of ordinary citizens. Nevertheless, attackers realized its full potential when they began to target organizations that were willing to pay to retrieve and protect their employee and customer data. Nowadays, most ransomware attacks happen to businesses and other organizations, including small and medium organizations who lack the resources to fully shield themselves from such attacks.

Small Business Cybersecurity Survival Guide
Get CrowdStrike’s Small Business Cybersecurity Survival Guide to learn how to identify threats and stop them, even with limited resources.
Download NowSome of the most affected industries include banking, utilities, education, government, and manufacturing. Attackers also execute more ransomware attacks on affluent regions and countries of the world, like the United States, Canada, and Australia. They do this for 2 reasons: wanting to extort more money from rich companies situated in these regions, and these regions tending to have higher PC adoption rates.
Should You Pay the Ransom?
The FBI does not support paying a ransom in response to a ransomware attack. They argue paying a ransom not only encourages the business model, but it also may go into the pockets of terror organizations, money launderers, and rogue nation-states. Moreover, while few organizations publicly admit to paying ransoms, adversaries will publicize that info on the dark web – making it common knowledge for other adversaries looking for a new target.
Paying the ransom doesn’t result in a faster recovery or a guaranteed recovery. There may be multiple decryption keys, there may be a bad decryption utility, the decryptor may be incompatible with the victim’s operating system, there may be double decryption and the decryption key only works on one layer, and some data may be corrupted. Less than half of ransomware victims are able to successfully restore their systems.
How Much Does a Ransom Payment Cost?
Ransomware remains one of the most profitable tactics for cybercriminals. The average ransom payment in 2023 is $1.85 million.
How to Remove Ransomware?
There is a variety of ways a ransomware infection spreads. Once ransomware penetrates a device on your network, it can wreak havoc and cause a disruption that grinds business operations to a halt. With confidential data, financial wellbeing and brand reputation at stake, knowing what to do if you get ransomware is critical, but the best ransomware defense relies on proactive prevention.
Expert Tip
Follow these tips to help keep your operations secure:
- Train all employees on cybersecurity best practices
- Keep your operating system and other software patched and up to date:
- Implement and enhance email security
- Integrate threat intelligence into your security strategy
- Develop ransomware-proof offline backups
- Implement a robust identity protection program
If you do encounter ransomware, it’s important to take the following steps:
1. Find the Infected Device(s)
Every device connected to the network – both on and off-site – should be disconnected. If necessary, disable any wireless connectivity, too – including Wi-Fi and Bluetooth – as this helps stop a ransomware infection from traversing the network, seizing, and encrypting crucial data.
If ransomware penetrates your network, it’s important to identify and isolate any infected devices immediately – before the breach spreads to the rest of the network.
Firstly, look for any suspicious activity on the network, such as file renaming or file extensions changing. It’s likely that the system was breached by human error – for example, an employee clicking a suspicious link on a phishing email – so, employees can be a useful source of information. Ask if anyone has received or spotted any suspicious activity that may help pinpoint infected devices.
2. Reboot to Safe Mode
Depending on the type of ransomware, rebooting the device and restarting it in safe mode can halt the spread. Although some trojans like ‘REvil’ and ‘Snatch’ can operate during a safe-mode boot, this isn’t true of all ransomware and safe mode can buy you valuable time to install anti-malware software. However, it’s important to note that any encrypted files will remain encrypted even in safe mode and will need to be restored via data backup.
3. Install Anti-Ransomware Software
Once the infected device(s) have been identified and disconnected from the network, the ransomware needs to be removed using anti-malware software. If you attempt business as usual before the devices are fully decrypted, you risk a resurgence of the undetected malware, resulting in further spread and more compromised files.
4. Scan for Ransomware Programs
When you believe your devices are clear of any ransomware or other worms, make sure you scan the system – both by manually searching for any suspicious behavior like file extension changes, and using next-generation firewalls. A thorough scan should reveal any hidden trojans that could wreak havoc again once you restore your computer.
5. Look to your Backups
In a day and age where cybersecurity risks lurk around every corner, having backups of all your digital data – separated from the centralized network – is crucial to getting things up and running again quickly, and minimizing downtime, in the event of a breach.
Once all devices have been decrypted and fitted with antivirus software, it’s time to turn to your backup data to restore any compromised files.
However, before you do, run a quick check on any backup files. The increasing sophistication and resilience of modern ransomware means these files may also have been corrupted and rolling this data out to the network could simply put you back to step one.
6. Report the Attack
While the immediate priority post-breach is to stop the spread and start the recovery phase, consideration must also be given to the wider consequences of the attack. Compromised data not only impacts the business but also its employees and clients.
As ransomware typically involves the threat of data leaks, any attack should be reported to the relevant authorities as soon as possible.
American data legislation doesn’t really exist on the federal level. However, a mix of individual states and some federal regulations issue strict fines to those data compliance regulations. If you suffer a data breach in California for example, you must report it to the CCPA, and any individual violation results in $7,500 fines per violation.
Ransomware and other forms of malware should also be reported to law enforcement authorities, who can help identify those responsible and prevent future attacks. You can report the attack here:
Learn More
Read this post to learn the steps you can take to recover data after suffering a ransomware attack. Read: Ransomware Recovery
Ransomware Solutions – Crowdstrike’s Approach
As previously discussed, a ransomware attack can be detrimental to business operations and data privacy. To call taking a proactive approach essential when protecting from ransomware is an understatement. CrowdStrike’s ransomware protection solutions help you take this proactive approach. Depending on the size of your organization, the Falcon Go, Falcon Pro, or Falcon Enterprise product bundles help defend your organization’s attack surfaces, including endpoints and cloud workloads, identity, and data.