16 Ransomware Examples
Ransomware is malware that encrypts a victim's important files in demand of a payment (ransom) to restore access. If the ransom payment is made, ransomware victims receive a decryption key. If the payment is not made, the malicious actor publishes the data on the dark web or blocks access to the encrypted file in perpetuity.
Below we explore 16 recent ransomware examples and outline how the attacks work.
- BitPaymer
- Cryptolocker
- DarkSide
- Darma
- DoppelPaymer
- GandCrab
- Maze
- MedusaLocker
- NetWalker
- NotPetya
- Petya
- REvil
- Ryuk
- SamSam
- WannaCry
- Hive
1. BitPaymer
CrowdStrike Intelligence has been tracking the original BitPaymer since it was first identified in August 2017. In its first iteration, the BitPaymer ransom note included the ransom demand and a URL for a TOR-based payment portal. The payment portal included the title “Bit paymer” along with a reference ID, a Bitcoin (BTC) wallet, and a contact email address. An example of this portal is shown below:
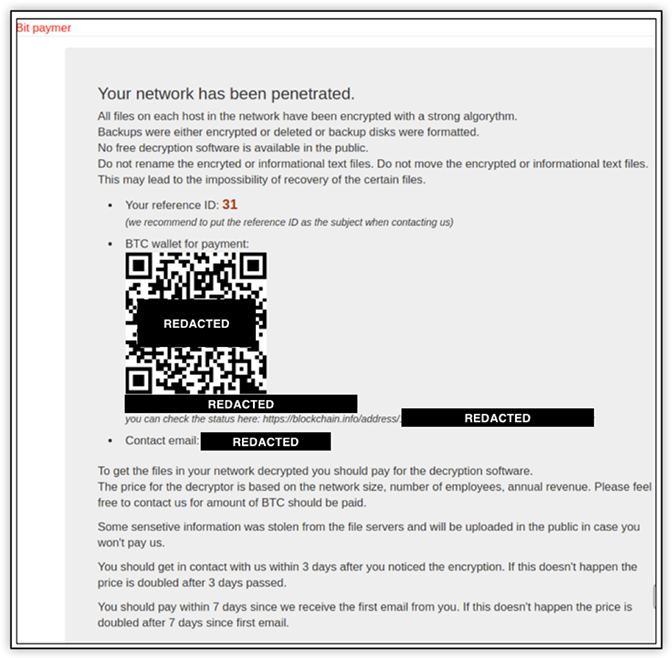 Learn more -> CrowdStrike's full Bitpaymer analysis.
Learn more -> CrowdStrike's full Bitpaymer analysis.2. Cryptolocker
Screen lockers virtually disappeared after the introduction of a ransomware group known as CryptoLocker in 2013. CryptoLocker ransomware was developed by the so-called BusinessClub that used the massive Gameover Zeus botnet with over a million infections. The group decided to develop their own ransomware and deploy it to a subset of their botnet’s infected systems. The ransom demand for victims was relatively small — an amount between $100 and $300 USD — and payable in a variety of digital currencies including cashU, Ukash, Paysafe, MoneyPak, and Bitcoin (BTC).
3. DarkSide
DarkSide ransomware is a RaaS operation associated with an eCrime group tracked by CrowdStrike as CARBON SPIDER. DarkSide operators traditionally focused on Windows machines and have recently expanded to Linux, targeting enterprise environments running unpatched VMware ESXi hypervisors or stealing vCenter credentials. On May 10, the FBI publicly indicated the Colonial Pipeline incident involved the DarkSide ransomware. It was later reported Colonial Pipeline had approximately 100GB of data stolen from their network, and the organization allegedly paid almost $5 million USD to a DarkSide affiliate.
4. Dharma
Dharma has been in operation since 2016 under a ransomware-as-a-service (RaaS) model, where developers license or sell ransomware to other criminals who then carry out an attack using the malware. Dharma affiliates do not appear to discriminate among industries.
CrowdStrike identified that the original author of Dharma released the source code in 2016 before ceasing activity. Since this threat actor’s departure, Dharma has been marketed and sold by multiple, apparently independent actors, two of which were active in 2019 — and at least one remains active as of January 2020. Separately, while the Phobos ransomware is likely to have been inspired by Dharma, the codebase of Phobos appears separate from Dharma.
Learn more -> Dharma ransomware's intrusion methods
2023 CrowdStrike Global Threat Report
The 2023 Global Threat Report highlights some of the most prolific and advanced cyber threat actors around the world. These include nation-state, eCrime and hacktivist adversaries. Read about the most advanced and dangerous cybercriminals out there.
Download Now5. DoppelPaymer
While the first known victims of DoppelPaymer were targeted in June 2019, CrowdStrike was able to recover earlier builds of the malware dating back to April 2019. These earlier builds are missing many of the new features found in later variants, so it is not clear if they were deployed to victims or if they were simply built for testing.
The ransom note used by DoppelPaymer is similar to those used by the original BitPaymer in 2018. The note does not include the ransom amount; however, it does contain a URL for a TOR-based payment portal, and instead of using the keyword KEY to identify the encrypted key, the note uses the keyword DATA as shown in Figure 4.
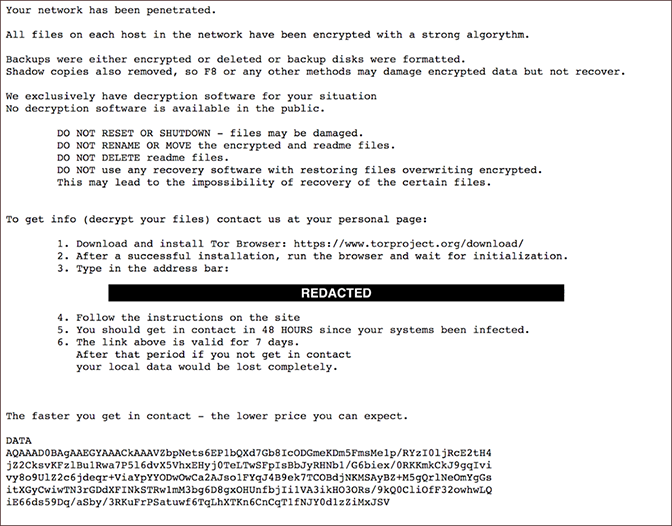 Learn more -> DoppelPaymer Origins and Analysis
Learn more -> DoppelPaymer Origins and Analysis6. GandCrab
GandCrab has established itself as one of the most developed and prevalent ransomware families on the market. Development of the ransomware itself has been driven, in part, by PINCHY SPIDER’s interactions with the cybersecurity research community. GandCrab contains multiple references to members of the research community who are both publicly active on social media and have reported on the ransomware.

PINCHY SPIDER has continued to promote the success of its ransomware in criminal forum posts, often boasting about public reporting of GandCrab incidents. In February, PINCHY SPIDER released version 5.2 of GandCrab, which is immune to the decryption tools developed for earlier versions of GandCrab and in fact, was deployed the day before the release of the latest decryptor.
Recently PINCHY SPIDER has also been observed advertising for individuals with remote desktop protocol (RDP) and VNC (Virtual Network Computing) skills, and spammers who have experience in corporate networking.
Learn more -> How Pinchy Spider deploys GandCrab for 'Big Game Hunting'7. Maze
Maze ransomware is a malware targeting organizations worldwide across many industries. It is believed that Maze operates via an affiliated network where Maze developers share their proceeds with various groups that deploy Maze in organizational networks. Maze operators also have a reputation for taking advantage of assets in one network to move laterally to other networks.
Learn more -> CrowdStrike's technical analysis on maze ransomware.Learn More
While its explosive growth over the past few years may make it seem otherwise, ransomware didn't come out of nowhere. Follow along as we outline how ransomware has evolved over the years into a sophisticated weapon for adversaries.
8. MedusaLocker
MedusaLocker is a ransomware family that was first seen in the wild in early October 2019. In January 2020, a fork of MedusaLocker named Ako was observed, which has been updated to support the use of a Tor hidden service to facilitate a RaaS model. Operators of the Ako version of the malware have since implemented a DLS (see below)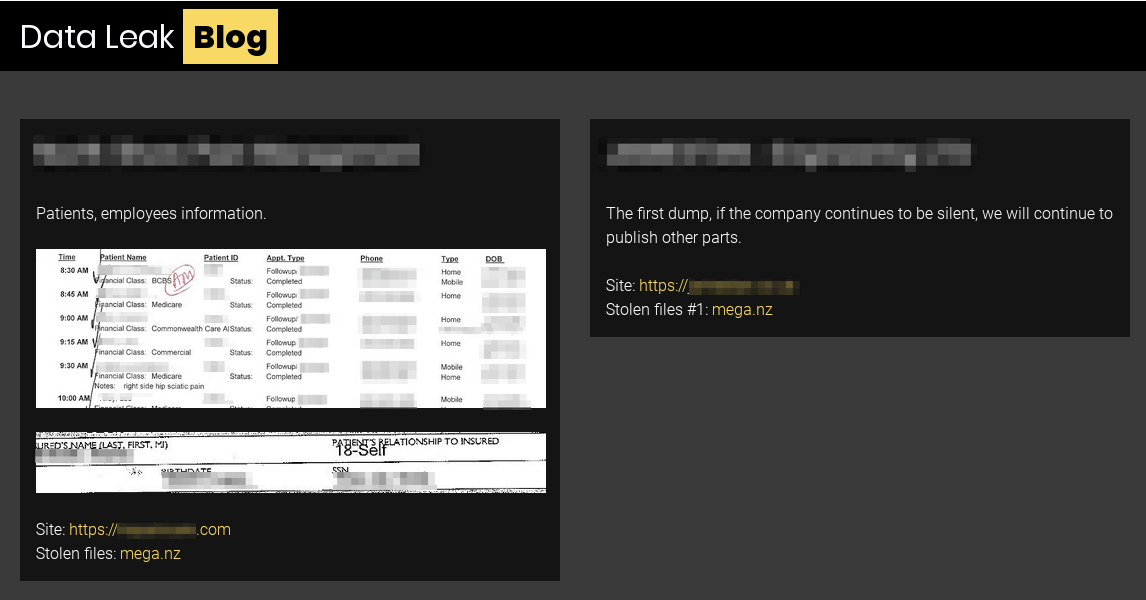
Learn More
Discover which ransomware defense approaches are the most effective by downloading our detailed white paper on:
9. NetWalker
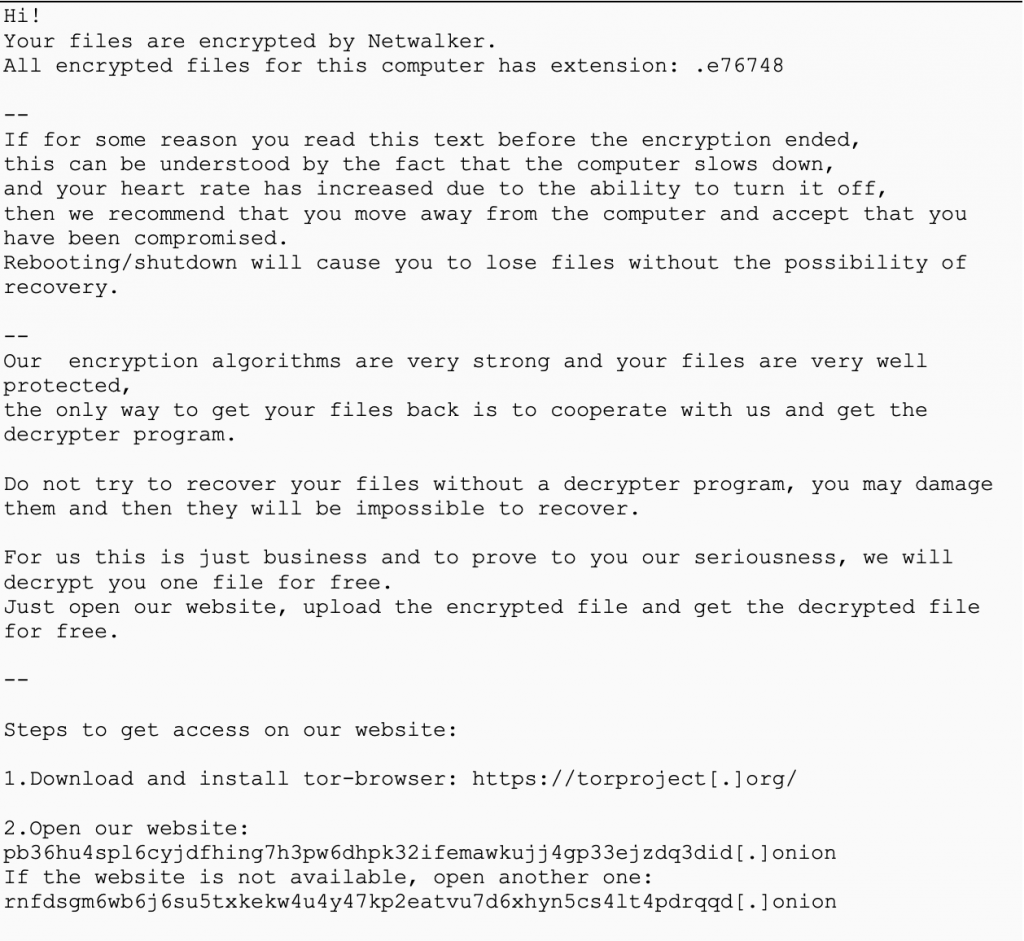
NetWalker is ransomware written in C++ and advertised as a Ransomware-as-a-Service (RaaS) on forums by a user known to be part of a group designated as CIRCUS SPIDER.
NetWalker encrypts files on the local system, mapped network shares and enumerates the network for additional shares, attempting to access them using the security tokens from all logged-in users on the victim’s system.
Below is an example of their ransom note:
 Learn more -> Download Netwalker Ransomware Intelligence Report
Learn more -> Download Netwalker Ransomware Intelligence Report10. NotPetya
NotPetya is a ransomware variant of Petya was first detected in 2017 rapidly infiltrating systems across multiple countries. What’s particularly nasty about this family of ransomware is its use of stealthy propagation techniques that allow it to swiftly move laterally to encrypt other systems across an organization. NotPetya ransom notes have demanded $300 USD for each infected machine.
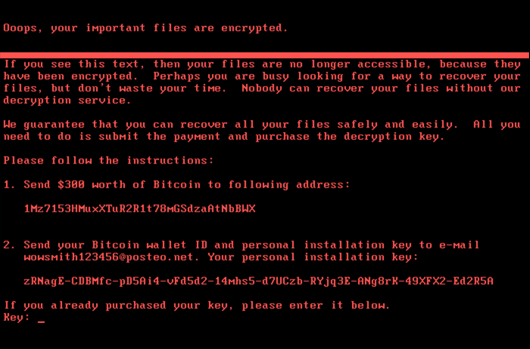 Learn more -> NotPetya Technical Analysis
Learn more -> NotPetya Technical Analysis11. Petya
Discovered in 2016, encrypts the Master File Table (MFT) and the Master Boot Record (MBR), making it impossible for you to access anything on the drive. Often it is launched with another exploit call Mischa, so that if Petya lacks the privileges necessary to gain access to the MFT or MBR, Mischa is enabled to one by one
12. REvil
On December 9, 2019, a vendor of PINCHY SPIDER’s REvil ransomware as a service (RaaS) posted a threat to leak victim data to an underground forum. This is the first time CrowdStrike Intelligence observed the group or their affiliates making such a threat, and it appeared to be in frustration over failing to monetize compromises at a U.S.-based managed service provider (MSP) and a China-based asset management firm. Since that time, affiliates of PINCHY SPIDER have posted data on more than 80 victims.
13. Ryuk
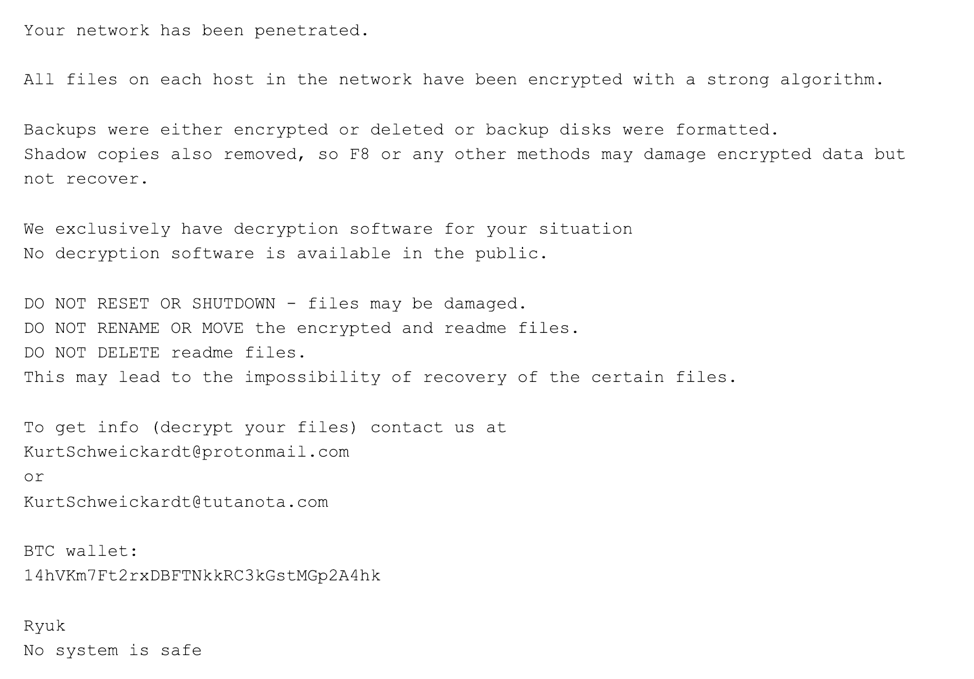
Ryuk is specifically used to target enterprise environments. Code comparison between versions of Ryuk and Hermes ransomware indicates that Ryuk was derived from the Hermes source code and has been under steady development since its release. Hermes is commodity ransomware that has been observed for sale on forums and used by multiple threat actors. However, Ryuk is only used by WIZARD SPIDER and, unlike Hermes, Ryuk has only been used to target enterprise environments.
Here's an example of a Ryuk ransom note:
 Learn more -> Ryuk Technical Analysis
Learn more -> Ryuk Technical Analysis14. SamSam
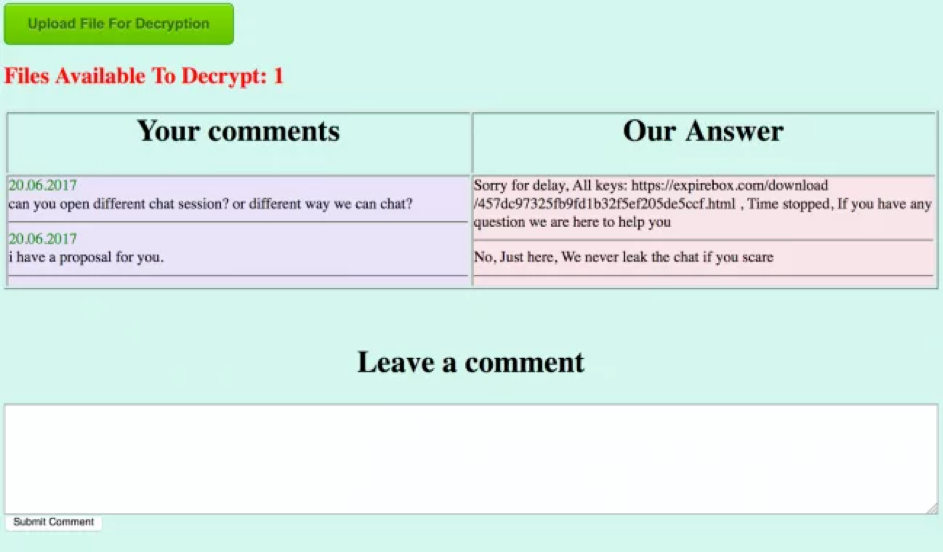
Developed and operated by the cyber adversary, BOSS SPIDER, SamSam has been observed using unpatched server-side software to enter an environment. Most notably, SamSam was behind the 2018 ransomware attack on the city of Atlanta, Georgia. The attack left 8,000 city employees without their computers, and citizens were unable to pay their parking water bills and parking tickets.
Below is an example of a SamSam operator's response after the ransom has been paid. The response typically includes a URL for the victim to download decryption keys.
 Learn more -> Lessons learned from SamSam
Learn more -> Lessons learned from SamSam15. WannaCry
Also referred to as WCry, WanaCrypt, or Wanna, WannaCry was identified in May 2017 during a mass campaign affecting organizations across the globe. WannaCry has targeted healthcare organizations and utility companies using a Microsoft Windows exploit called EternalBlue, which allowed for the sharing of files, thus opening a door for the ransomware to spread.
Learn more -> CrowdStrike's technical analysis of WannaCry.16. Hive
Hive is a Ransomware as a Service (RaaS) platform that targets all kinds of businesses and organizations, but is more well known for going after healthcare organizations. In April 2022, Hive leveraged a pass-the-hash technique to coordinate an attack that targeted a large number of Microsoft’s Exchange Server customers. Affected sectors included the energy, financial services, nonprofit, and healthcare sectors.
Hive leveraged a vulnerability within Microsoft's Exchange Server known as ProxyShell, which Microsoft was able to quickly patch. Nevertheless, the attackers had already planted a backdoor web script which was used to run malicious code on the Exchange server. They then took control of the system via the pass-the-hash, using Mimikatz to steal the NTLM hash. Finally, Hive performed reconnaissance on the server, collected data, and deployed the ransomware payload.
On January 26, 2023, the Justice Department of the United States announced it disrupted operations from the notorious RaaS group knows as Hive, which had over 1,500 victims worldwide to date. DoJ personnel received a court order to seize to back-end servers that belonged to Hive. Attorney General Garland said while the group has seized operations, ransomware attacks are still prominent and organizations should take the threat seriously.





