Everything you need to stop ransomware in its tracks
Stop ransomware with a modern approach and an adaptive platform that stays ahead of the adversary.

The Problem
Legacy endpoint solutions can’t keep pace with adversaries and ransomware threats
75%
of attacks to gain access were malware-free1
76%
spike in data theft victims named on the dark web2
90%
of successful attacks begin on an endpoint3
Proactive
ransomware protection
Built on industry-leading adversary intelligence, the CrowdStrike Falcon® platform leverages AI-native defense to anticipate and stop known and unknown ransomware. Outpace sophisticated threat actors with a platform that provides:
70% reduction in mean time to response against live-attacks.
25% time-saving in security administration.
100% Protection, 100% Visibility, and 100% Analytic Detection Coverage in the 2023 MITRE ATT&CK® Round 5 Evaluation
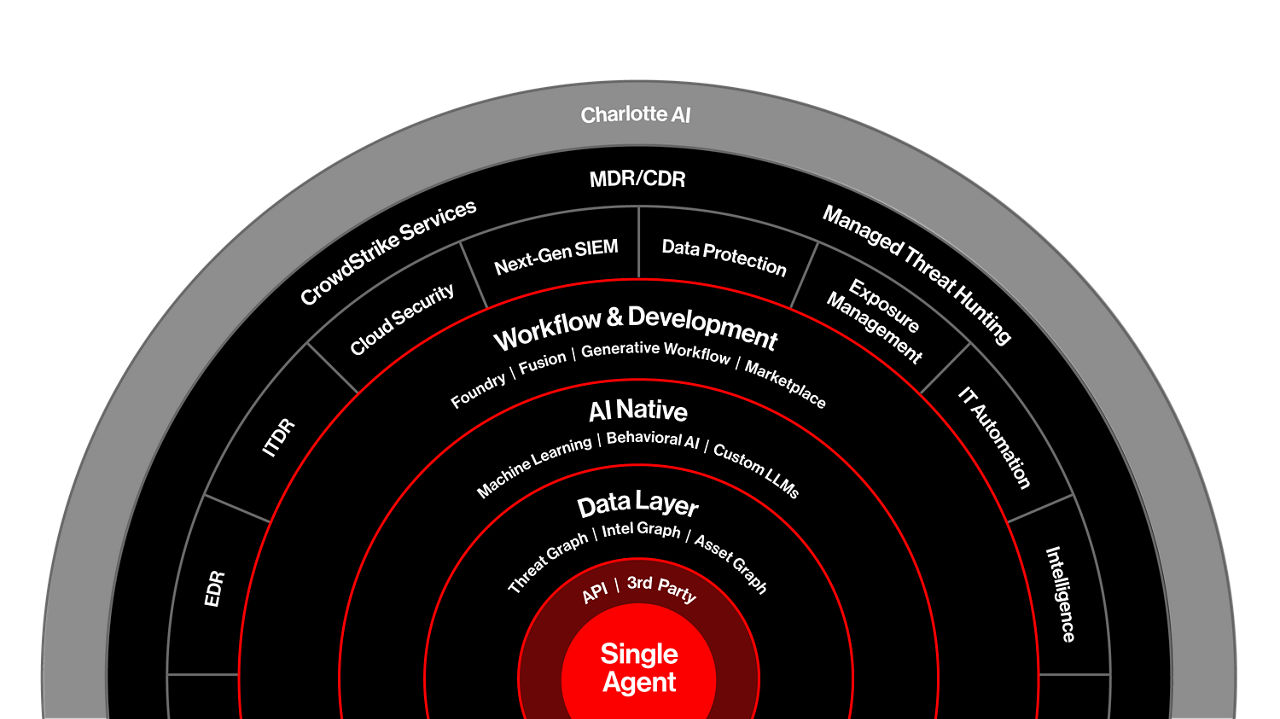
Beat them at their own game
CrowdStrike Falcon® Adversary OverWatchSM hunts relentlessly to see and stop the stealthiest, most sophisticated threats: the 1% of 1% who blend in silently, using “hands on keyboard” activity to deploy widespread ransomware attacks. Our threat hunters continuously innovate and operate to stop ransomware before it happens.

Ransomware
protection services
Tabletop Exercise: A tabletop discussion to walk through recent sophisticated ransomware attack scenarios and discuss how your teams would respond.
Red Team / Blue Team Exercise: A collaborative exercise designed to mimic ransomware activities in a step-by-step (red team) attack on your environment with advice from our security experts (blue team) so you can understand the gaps in your ability to detect and respond to ransomware.
Adversary Emulation Exercise: A covert exercise designed to mimic ransomware activities in an external targeted (black box) ransomware emulation attack on your environment to test your ability to detect and defend the network against ransomware.

Platform bundles to stop ransomware
Falcon Go
Annual pricing:
$59.95/device*
Build your cybersecurity strategy with next-gen antivirus protection, along with visibility and granular control over your devices.
What you get:
- Next generation antivirus
- Device control
FALCON PRO
Annual pricing:
$99.95/device*
Superior next-gen antivirus along with simple, centralized firewall management and device control, making it easy to manage and enforce protection policies.
Get everything in Go, plus:
- Firewall management
FALCON ENTERPRISE
Annual pricing:
$184.99/device*
Unify all security tools to provide a single source of truth: next-gen antivirus, EDR, XDR, managed threat hunting and integrated threat intelligence.
Get everything in Pro, plus:
- Endpoint detection and response
- Threat hunting
*Pricing includes all indicated bundle components for 5-250 endpoints. Billed annually. Contact CrowdStrike for details and pricing at time of purchase or renewal. Pricing is based on quantity of endpoints and Active Directory accounts. **The free trial includes a free Falcon Go subscription including Falcon Prevent, and Falcon Device Control. Additional products can be trialed in the platform by visiting the CrowdStrike app store. At the end of your free trial your subscription and corresponding features will adjust to the bundle you selected upon checkout.

ESG Survey Report: Ransomware Preparedness - Insights from IT and Cybersecurity Professionals
Read report
ESG Survey Report: Ransomware Preparedness - Insights from IT and Cybersecurity Professionals
ESG Survey Report: Ransomware Preparedness - Insights from IT and Cybersecurity Professionals
Read report
ESG Survey Report: Ransomware Preparedness - Insights from IT and Cybersecurity Professionals
Tested and proven leader
 CrowdStrike delivers 100% coverage
CrowdStrike delivers 100% coverage
CrowdStrike Achieves 100% Protection, 100% Visibility, 100% Analytic Detection in 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise.

CrowdStrike named as a “Customers’ Choice”

Named as a “Customers’ Choice” in the 2023 Gartner Peer Insights Voice of the Customer for Endpoint Protection Platform Report.
 CrowdStrike named a Leader in external threat intelligence
CrowdStrike named a Leader in external threat intelligence
CrowdStrike is named a Leader in the 2023 Forrester Wave for External Threat Intelligence Services Providers (ETISP).
29,000 customers trust CrowdStrike
“In the old days when we had only AV tools, everything was a thick client with power-hungry agents. Managing that was time-consuming and we had some challenges with resources on workstations — whereas CrowdStrike is cloud-based and has just one agent for all the different solution modules compared to competitor products that need multiple agents.“
CISO
@Berkshire Bank
Read the case study >
“CrowdStrike is the star of the show in our security operations center. Our detections dashboard shows us anything CrowdStrike deems malicious, be it a cloud worker node or endpoint, giving us end-to-end visibility and protection.”
Matt Bellingeri, CISO
@CoreWeave
Read the case study >
“You need a solution like CrowdStrike, actually on the endpoints, so you can see in real time something weirds happening here. Without that type of solution in place, you’re going to fall victim to ransomware.“
Matt Singleton, CISO
@State of Oklahoma
Watch the video >


