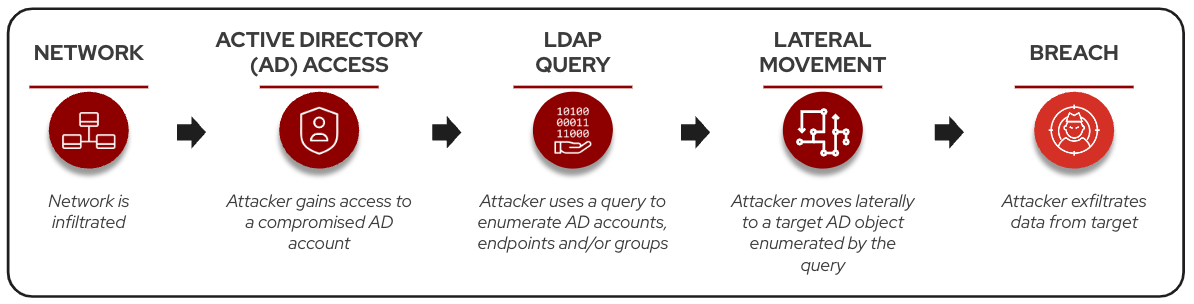
Early in the cyberattack kill chain, reconnaissance enables attackers to assemble critical network information to plan a tailored attack strategy. In this phase, adversaries aim to map out networks and their users, and locate system vulnerabilities, without setting off alarms. Proactive monitoring and early detection of this activity can disrupt attackers in their tracks and lower the risk of a breach.
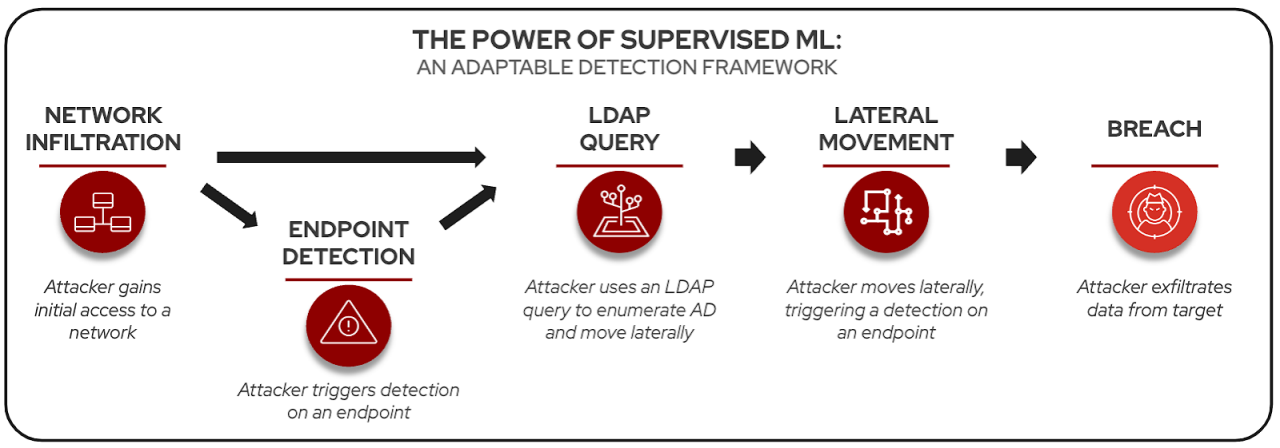
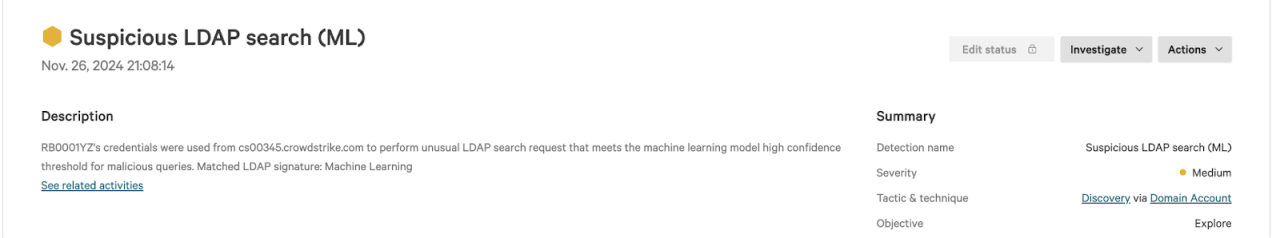
CrowdStrike has pioneered a new approach to detecting early signs of reconnaissance queries using AI. This capability generates Lightweight Directory Access Protocol (LDAP) search signatures to detect early signs of reconnaissance at scale, allowing security teams to quickly identify potentially malicious network activity before it escalates. The underlying model for this feature is rigorously trained on correlated insights from endpoint and identity telemetry, underscoring the value of a unified approach to uncover advanced detections faster, earlier and more efficiently.
This new feature is now available to all customers of CrowdStrike Falcon® Identity Protection.
Understanding LDAP and Its Role in Reconnaissance
LDAP is a widely used protocol for querying and managing directory data within Active Directory (AD) environments. This protocol is fundamental to accessing AD data and is often a first target in reconnaissance activities following a network breach, with common open source Active Directory attack tools like SharpHound and Rubeus using LDAP in their operations.
By design, LDAP allows standard domain users to read directory data without requiring elevated permissions, making it possible for attackers to gather intelligence to plan effective intrusion and lateral movement strategies. For instance, LDAP queries can help attackers identify sensitive group memberships or high-privilege accounts, such as domain admins, across a network. This gives them a list of high-value accounts to target for further infiltration.
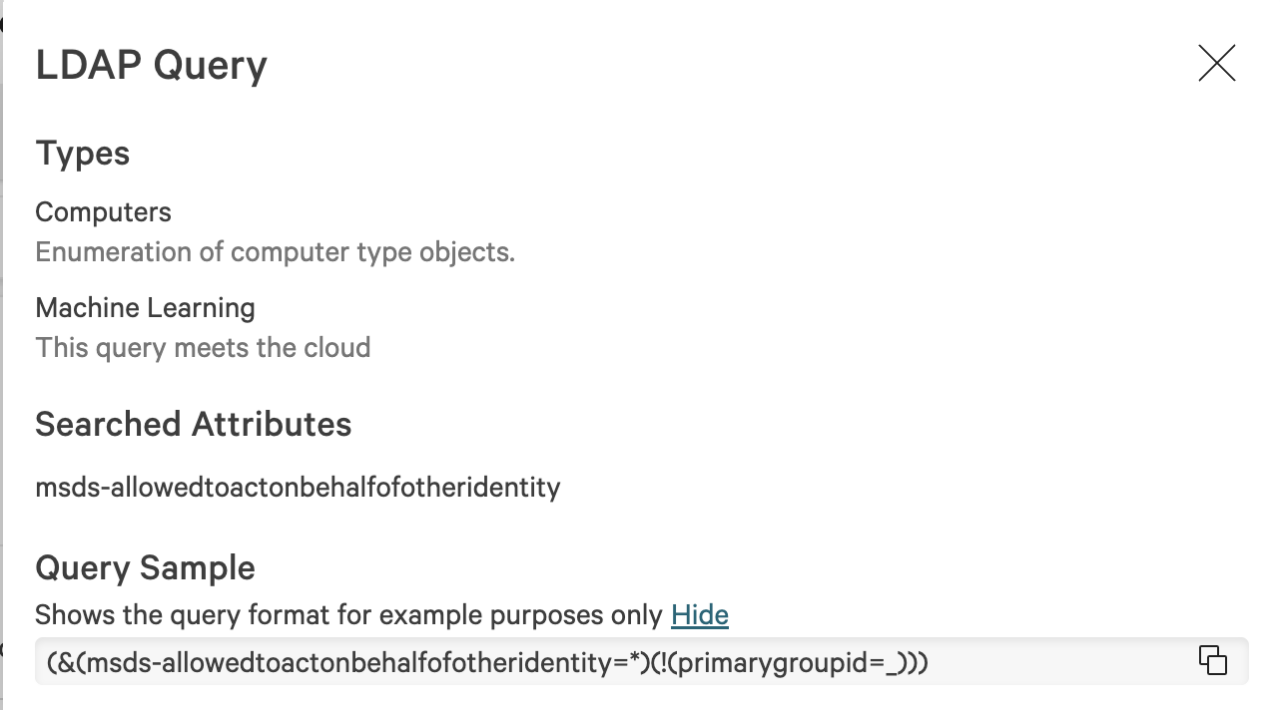
As LDAP is commonly used and can be used by standard domain users, distinguishing malicious queries from legitimate ones can be challenging, underscoring the need for advanced detection methods and behavioral baselining. Some threat hunting solutions provide specific LDAP detection rules, such as zeroing in on admin accounts, domain controllers, service principal names and more.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)