With the current threat landscape and likelihood of targeted attacks, organizations are dealing with myriad attempts to breach their network on a daily basis. This makes understanding how attackers learn about your organization’s network, employees, and business practices crucial. Having visibility into an attacker’s reconnaissance (recon) activities, whether it is active network scanning or passive information gathering through social media, enables an organization to better protect themselves from a large-scale breach.
First, I would like to clarify some terminology. When referring to active network reconnaissance (recon), I mean sending packets to the target organization’s network or assets. This may be through automated scanning or manual testing. Passive recon entails collecting information about an organization through third party sites, such as social media sites. Active network recon poses the risk of being detected, which is why attackers often opt for the “low and slow” method you will see demonstrated in this post.
Often, attackers default to spear phishing campaigns over active network recon because the likelihood of being detected is greater while scanning. Spear phishing allows for the targeting of certain individuals within an organization and follows the thinking that individuals are more vulnerable than say, a web server. 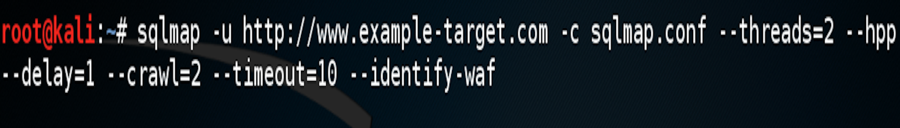 Screenshot 1
The options in Screenshot 1 illustrate a “low and slow” scan with sqlmap.
Screenshot 1
The options in Screenshot 1 illustrate a “low and slow” scan with sqlmap.
 Screenshot 2
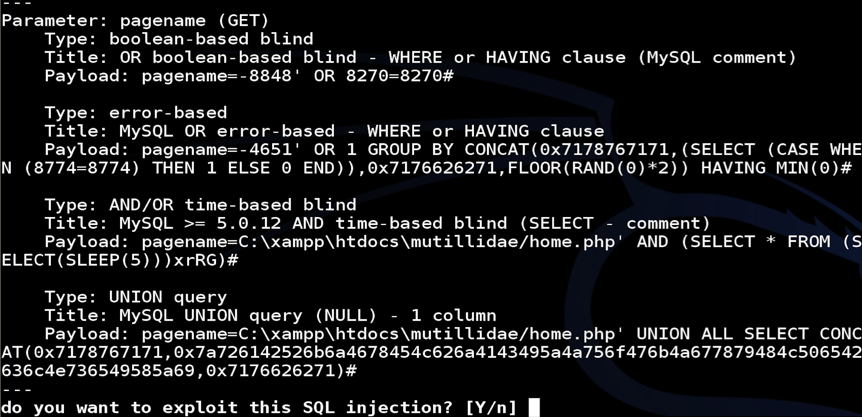
Once injectable parameters are found, sqlmap will attempt to exploit the discovered injection points. If successful, sqlmap will execute the options given in the scan parameters such as dumping the backend database or uploading a shell.
Screenshot 2
Once injectable parameters are found, sqlmap will attempt to exploit the discovered injection points. If successful, sqlmap will execute the options given in the scan parameters such as dumping the backend database or uploading a shell.
 Screenshot 3
The options in Screenshot 3 illustrate a “low and slow” scan with Nikto.
Screenshot 3
The options in Screenshot 3 illustrate a “low and slow” scan with Nikto.
 Screenshot 4
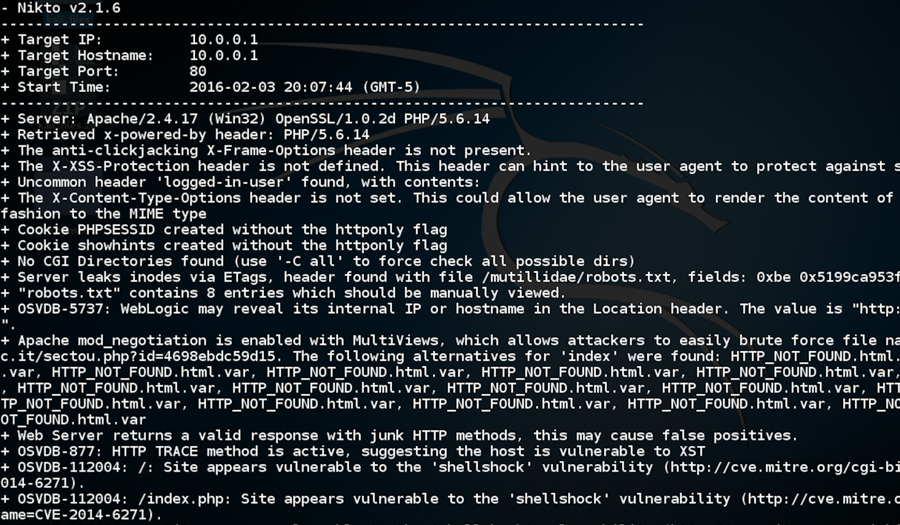
In Screenshot 4, we see an example of Nikto output. Nikto first reports target and configuration information followed by the findings of the scan. Each finding is denoted by a “+” symbol.
With recon being a vital part of any penetration test (or attack) it is important to remain unseen. Nothing ends a penetration test sooner than showing your hand. Many organizations classify recon activities as low risk, but these activities may culminate into larger incidents since powerful and freely available tools make this step easy for a wide range of attackers.
Screenshot 4
In Screenshot 4, we see an example of Nikto output. Nikto first reports target and configuration information followed by the findings of the scan. Each finding is denoted by a “+” symbol.
With recon being a vital part of any penetration test (or attack) it is important to remain unseen. Nothing ends a penetration test sooner than showing your hand. Many organizations classify recon activities as low risk, but these activities may culminate into larger incidents since powerful and freely available tools make this step easy for a wide range of attackers.
However, with employee education and email security on the rise, we see active network recon frequently accomplished in the wild. When actively scanning a network, there are two main schools of thought. The first is automated scanning. Automated scanning is done with tools such as sqlmap, Nessus, and Nikto. These tools allow for rapid identification of vulnerabilities and can even exploit found vulnerabilities. The second method is manual testing. Some would not consider manual testing actively scanning, but you are sending packets to the network in order obtain more information about the network. Manual testing can take large amounts of time, however the amount of traffic sent to the network is reduced. We are going to look at two open source automated scanning tools, sqlmap and Nikto, from the standpoint of an attacker.
How can we try to evade detection and take advantage of the features that each tool offers? It is important to know your enemy and understand a tool’s capabilities and how they can benefit an adversary. In our next post, we will show the defender’s view and identify where you may have visibility during targeted recon.
Sqlmap
Let’s start by looking at sqlmap. For those not familiar, sqlmap is a web application-scanning tool that attempts to identify and exploit Structured Query Language injection (SQLi) vulnerabilities. Sqlmap will also attempt to identify cross-site Scripting (XSS) vulnerabilities. Many penetration testers and even nation states commonly use sqlmap to achieve their goals. A command in sqlmap looks something like this: Screenshot 1
The options in Screenshot 1 illustrate a “low and slow” scan with sqlmap.
Screenshot 1
The options in Screenshot 1 illustrate a “low and slow” scan with sqlmap.
Sqlmap options:
- The first option, -u http://www.example-target.com specifies the target webpage for sqlmap to scan. This option can include testable parameters or can be the starting point for sqlmap’s crawl option, which we will discuss later.
- Next we have -c sqlmap.conf. This directs sqlmap on what configuration file to use. If a configuration file is not specified, the default scanning options will be applied. If a configuration file is applied, any options provided via the command line will override the options specified in the configuration file. There are a few options a penetration tester needs to keep in mind when running an sqlmap scan. The default user-agent string used by sqlmap contains the name of the tool --“sqlmap”. This is similar to other vulnerability scanning tools such as nmap and Nikto. Many Intrusion Detection and Prevention Systems (IDS/IPS) alert on these default user-agent strings, thus if we want to avoid detection the user-agent must be changed. Mimicking a common user-agent reduces your chances of being detected.
- The third option --threads=2 reduces the speed in which sqlmap scans a target. This essentially makes scanning less noisy. If time is a major factor, you should assess the speed versus stealth objectives.
- Looking at the --hpp option, this will allow for a HTTP Parameter Pollution Attack against ASP .NET pages. This helps a penetration tester spread data across multiple HTTP parameters in order to bypass IDS/IPS.
- The --delay=1 option directs sqlmap to wait a certain number of seconds between HTTP requests. This is helpful to avoid detection due to the number of HTTP requests some web servers see on a daily basis as well as spacing out your scanning attempts. If the target organization is reviewing or running signatures against web logs, delaying each scanning request will improve your chances of going undetected. Please note that increasing the delay duration will increase your scan time significantly.
- The --crawl=2 option allows sqlmap to spider the target web page following links and discovering testable parameters.
- The --timeout=10 option sets the time that sqlmap will wait before a link has timed out before moving on to the next link. By reducing the connection time to a target a penetration tester essentially reduces their chances of being caught due to the reduced amount of traffic and logs being generated on the target network.
- The final option given, --identify-waf helps the penetration tester determine if they are dealing with a Web Application Firewall (WAF). Typically, when a WAF is in play you know the chances of being detected are higher.
- Additional options to consider: sqlmap allows for fully customizable HTTP headers, Google dork implementation, and tor/proxy support. When stealth is important all options should be evaluated.
Sqlmap results
 Screenshot 2
Once injectable parameters are found, sqlmap will attempt to exploit the discovered injection points. If successful, sqlmap will execute the options given in the scan parameters such as dumping the backend database or uploading a shell.
Screenshot 2
Once injectable parameters are found, sqlmap will attempt to exploit the discovered injection points. If successful, sqlmap will execute the options given in the scan parameters such as dumping the backend database or uploading a shell.
Nikto
Nikto is another popular open source web application scanning tool. Nikto differs from sqlmap with a focus on many types of web application vulnerabilities and not just SQLi. A command in Nikto looks something like this: Screenshot 3
The options in Screenshot 3 illustrate a “low and slow” scan with Nikto.
Screenshot 3
The options in Screenshot 3 illustrate a “low and slow” scan with Nikto.
Nikto options:
- The –host http://www.example-target.com option, similar to the –u option in sqlmap, specifies the target for Nikto to scan.
- The next option, –evasion 147AB specifies what preconfigured evasion techniques Nikto should use. Some of the evasion techniques include random Uniform Resource Identifier (URI) encoding, including fake parameters, prepending long strings, etc. Utilizing evasion techniques improves your chances to avoid detection.
- The –Pause 1 option directs Nikto to wait one second between vulnerability tests. This will help break up the scanning attempts and space out the web log entries Nikto will generate. Using a longer pause duration will increase the scan time significantly.
- The –timeout 10 option is exactly like the timeout option in sqlmap. This will reduce the connection time to the target.
- The last option, –config nikto.conf tells Nikto what configuration file to use. Similar to sqlmap, Nikto’s default user-agent contains the string “nikto”, which is alerted on by many IDS/IPS tools. The user-agent should always be changed within the configuration file.
Nikto results
 Screenshot 4
In Screenshot 4, we see an example of Nikto output. Nikto first reports target and configuration information followed by the findings of the scan. Each finding is denoted by a “+” symbol.
With recon being a vital part of any penetration test (or attack) it is important to remain unseen. Nothing ends a penetration test sooner than showing your hand. Many organizations classify recon activities as low risk, but these activities may culminate into larger incidents since powerful and freely available tools make this step easy for a wide range of attackers.
Screenshot 4
In Screenshot 4, we see an example of Nikto output. Nikto first reports target and configuration information followed by the findings of the scan. Each finding is denoted by a “+” symbol.
With recon being a vital part of any penetration test (or attack) it is important to remain unseen. Nothing ends a penetration test sooner than showing your hand. Many organizations classify recon activities as low risk, but these activities may culminate into larger incidents since powerful and freely available tools make this step easy for a wide range of attackers. Equipping your organization with the capability to write custom IDS/IPS signatures or intelligence backend detections greatly improve your chances to detect recon activity and get in front of an attack. <1> http://sqlmap.org/ <2> https://cirt.net/Nikto2





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































