CROWDSTRIKE FALCON® ENDPOINT PROTECTION ENTERPRISE
Unifies the technologies required to successfully stop breaches, including true next-gen antivirus and endpoint detection and response (EDR), managed threat hunting, and threat intelligence automation, delivered via a single lightweight agent.
Watch demo-
Falcon PreventNext-generationantivirus
-
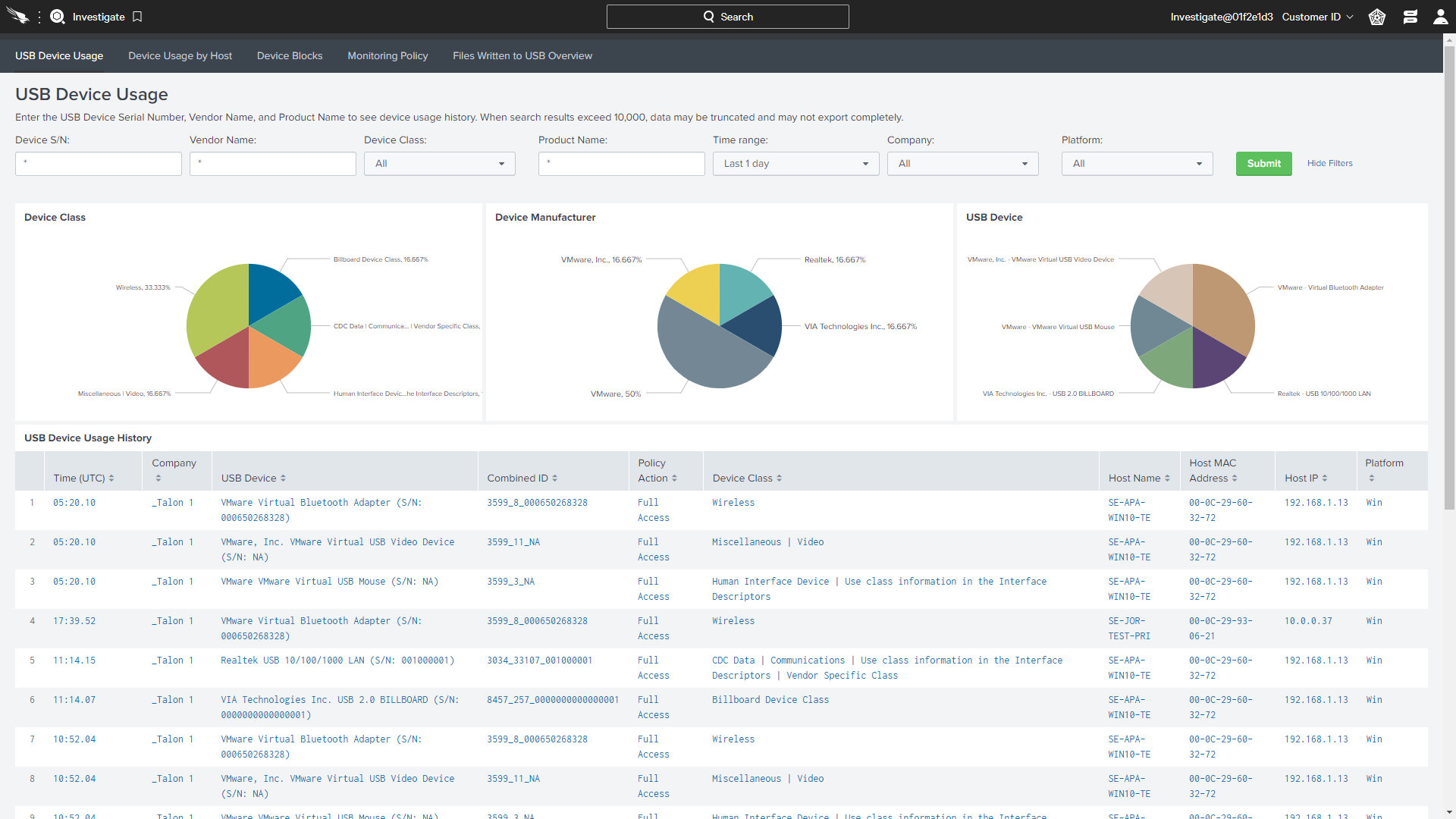
Falcon Device ControlUSB device control
-
Falcon Firewall ManagementHost firewall control
-
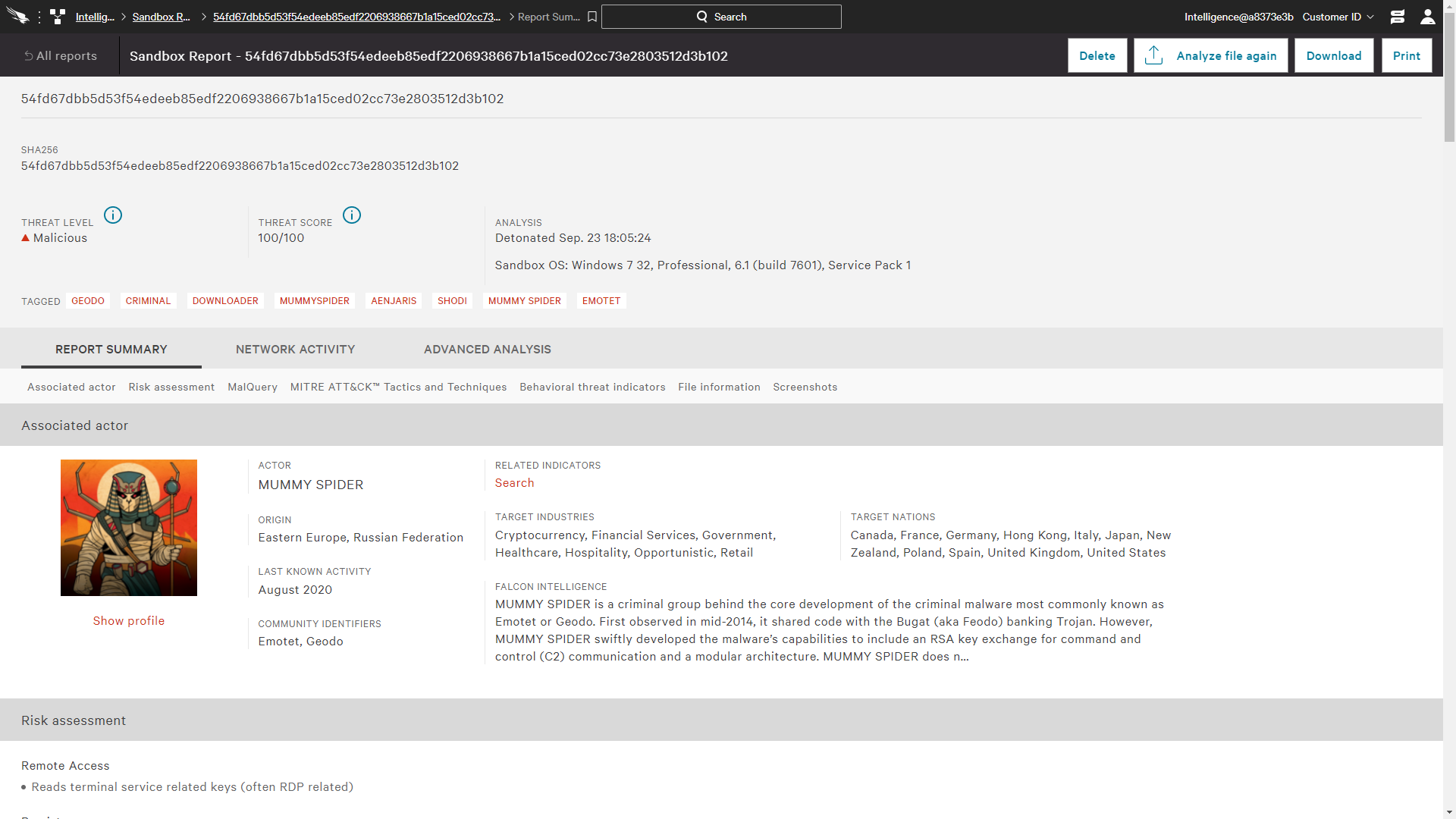
FalconAdversary OverWatchThreat hunting and intelligence
-
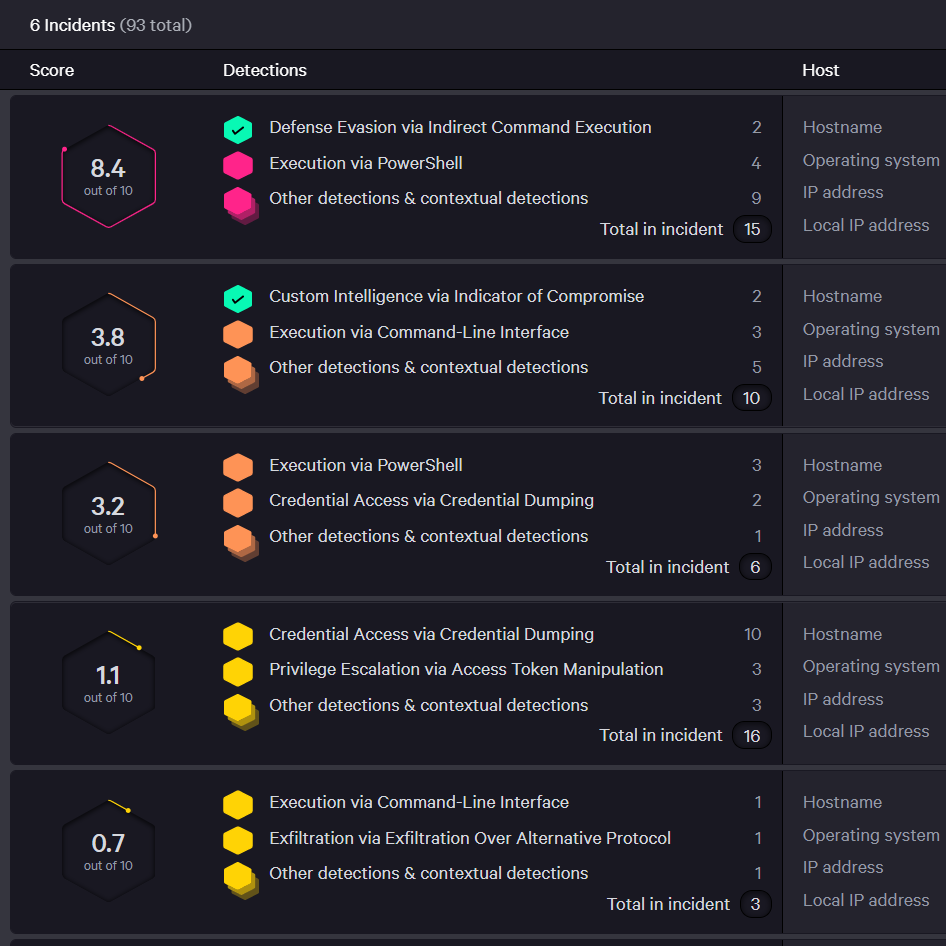
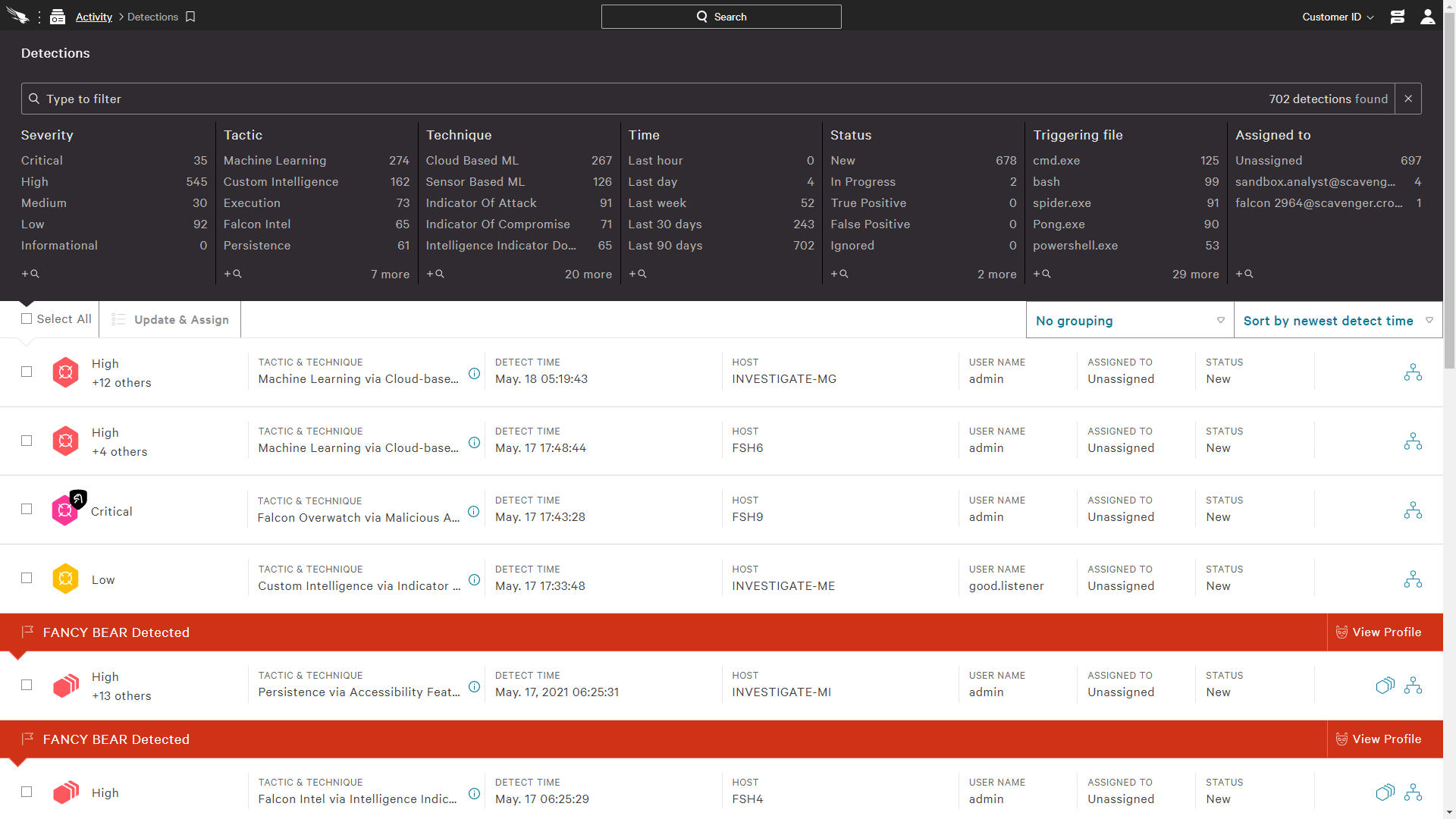
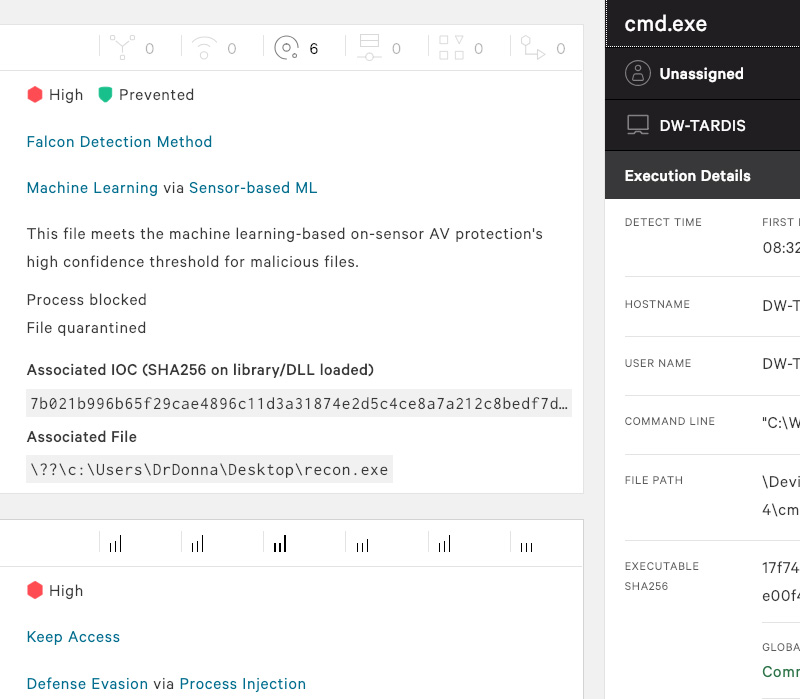
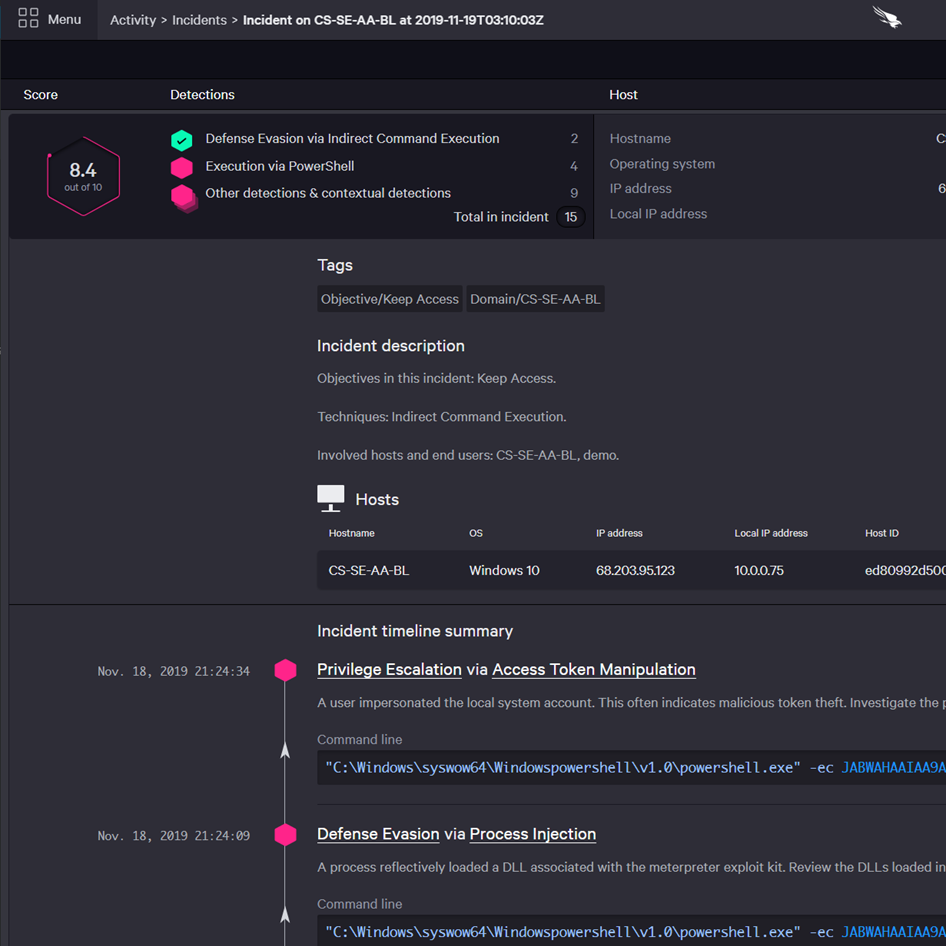
FalconInsight XDRDetection & response
-
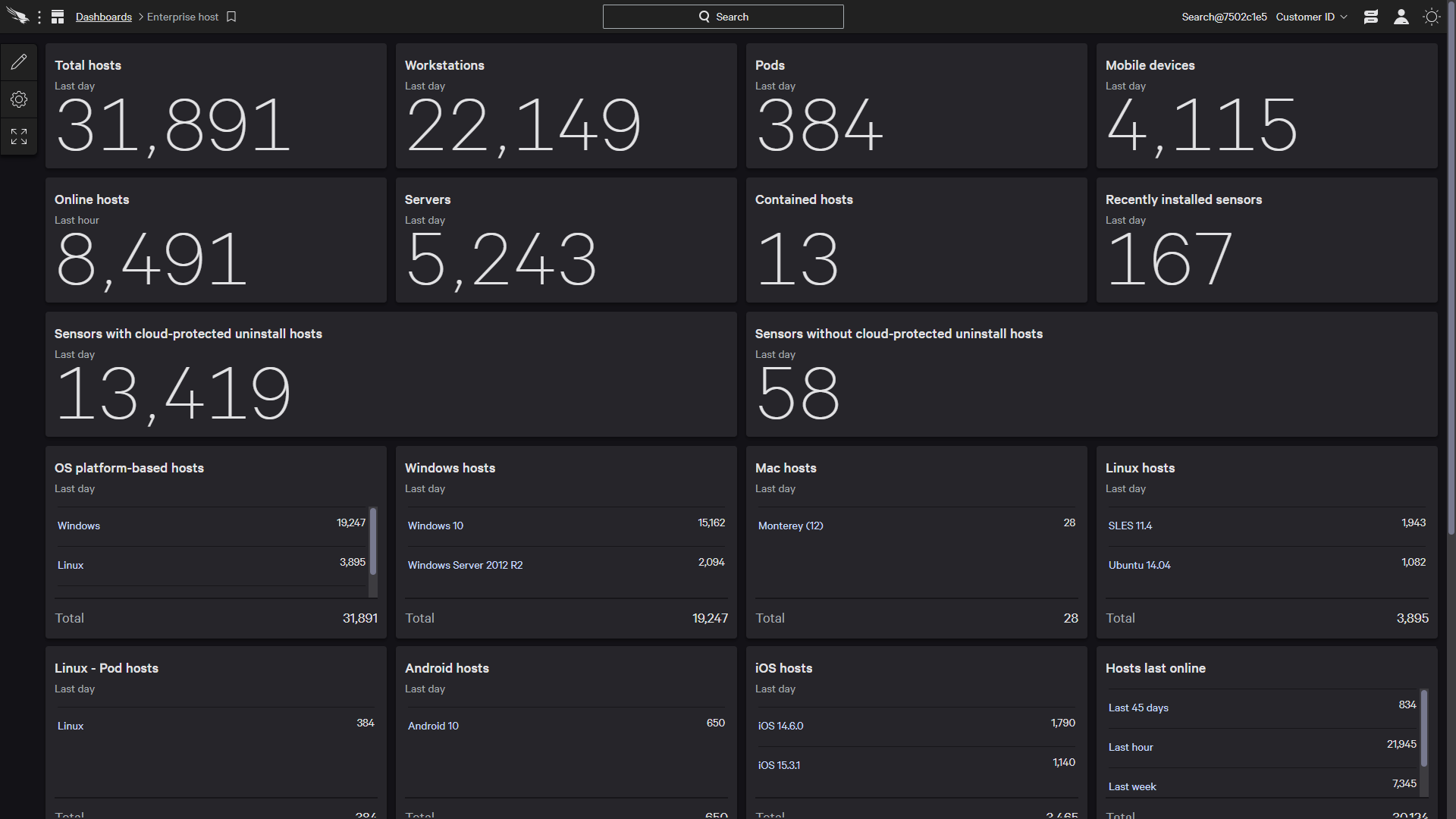
Falcon DiscoverIT hygiene
-
Falcon IdentityProtectionIdentity protection
-
CROWDSTRIKE
SERVICESExpress support
- Falcon Enterprise Unified NGAV, EDR, XDR, managed threat hunting and integrated threat intelligence
- -
- -
Flexible Bundles:
Included Component
Add-on
REAP THE BENEFITS OF CROWDSTRIKE’S
FALCON ENDPOINT
PROTECTION ENTERPRISE
Sets the new standard with the first cloud-native security platform that delivers the only endpoint breach prevention solution that unifies NGAV, EDR, XDR, managed threat hunting and threat intelligence automation in a single cloud-delivered agent.
BUSINESS VALUE
-
Increases security
efficiency -
Improves
productivity -
Decreases risks
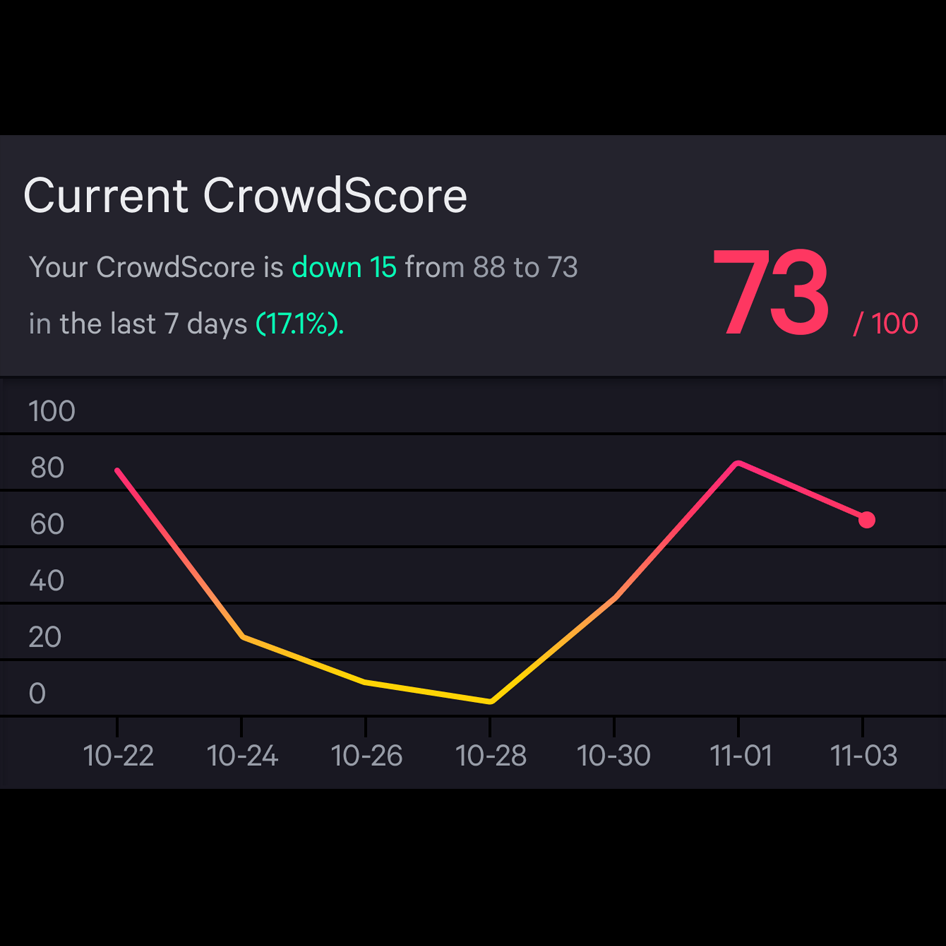
of breach -
Reduces time
to respond
MODULES INCLUDE
Compare CrowdStrike
See how CrowdStrike’s endpoint security platform stacks up against the competition.
Compare