- CrowdStrike Named a Leader in 2024 Gartner® Magic Quadrant™ for Endpoint Protection Platforms
CrowdStrike Falcon®
Free Trial FAQ
Contact the Trial team for assistance
falcontrial@crowdstrike.com
CrowdStrike Falcon®
Free Trial FAQ
Contact the Trial team for assistance
falcontrial@crowdstrike.com
1. Prepare for installation: For optimal performance, uninstall or disable other antivirus solutions before installing the Falcon sensor.
2. Activate your account via an email you should’ve received.
3. Log in and install sensors to your devices by following the instructions on the mainview once you log in. It includes video guides on how to install for your particular OS. You can also find instructions here.
You will know you’ve successfully installed the sensor when you log into falcon and see the shield on the mainview lit up green. You will also see below the number of devices with successfully installed sensors and if there are any detections.
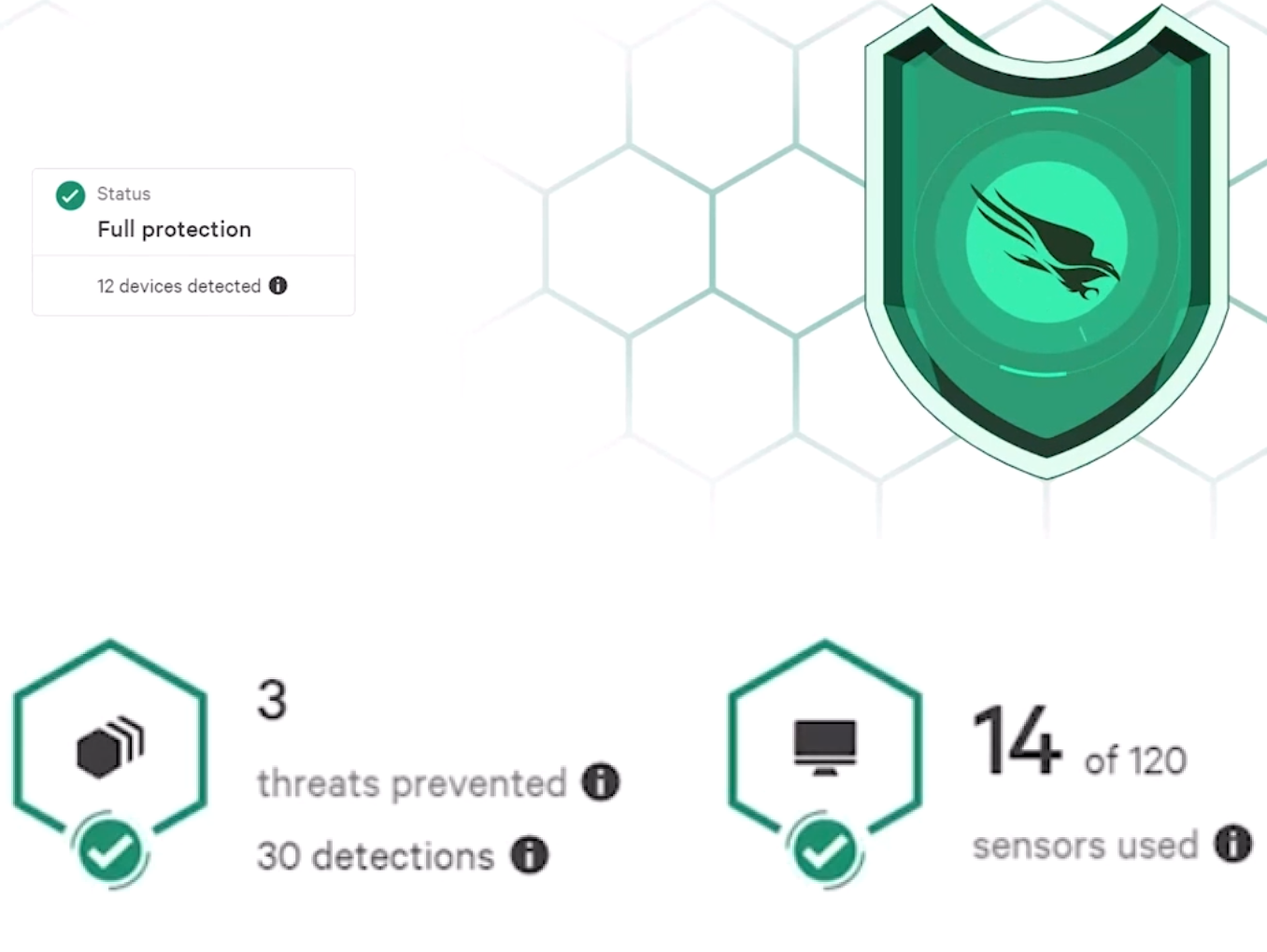
There are three CrowdStrike Falcon modules automatically included in the trial: CrowdStrike Falcon® Prevent, CrowdStrike Falcon® Device Control, and CrowdStrike Falcon® for Mobile. There are ten additional modules you can enable to customize your trial experience:
To test individual modules, open the console menu, select CrowdStrike Store → CrowdStrike Apps → Select your desired module → Try it for free. Note that some modules require another module to function properly. You can see dependencies for each module on the page under Falcon Requirements. It may take up to 30 minutes for all modules to become fully functional.
Yes. The CrowdStrike Falcon Prevent module is a fully certified AV replacement solution and allows organizations to confidently replace their existing legacy AV.
Falcon Prevent incorporates identification and prevention of known malware, machine learning for unknown malware, exploit blocking and advanced Indicator of Attack (IOA) behavioral techniques to protect against attacks whether your endpoints are online or offline. Falcon Prevent also features integration with Windows System Center, for organizations that need to prove compliance with appropriate regulatory requirements.
Falcon Prevent uses an array of complementary prevention and detection methods to protect against ransomware: