“We were asked to disable identity protection capabilities to let the testing proceed — and still achieved 100% prevention.”
The weeks following the release of the MITRE Engenuity ATT&CK Evaluation can be confusing when trying to interpret the results and cut through the noise. But one thing is crystal clear in this year’s evaluation that every organization should know: The CrowdStrike Falcon®® platform stands alone in delivering native identity protection capabilities that shut down adversaries and stop the breach before it even starts.
 MITRE evaluators found this out firsthand as testing kicked off. At the onset, the Falcon platform immediately identified that breached passwords and compromised accounts were being used. This prevented the test evaluator from gaining initial access to the environment — stopping the test before it could even start. CrowdStrike Falcon® was the only solution among those being evaluated where a protection component in the platform had to be disabled for the test to continue!
We were asked to disable our identity protection capabilities so that the actual “evaluation” could start — and we still achieved 100% prevention across all nine steps without identity protection enabled.
MITRE evaluators found this out firsthand as testing kicked off. At the onset, the Falcon platform immediately identified that breached passwords and compromised accounts were being used. This prevented the test evaluator from gaining initial access to the environment — stopping the test before it could even start. CrowdStrike Falcon® was the only solution among those being evaluated where a protection component in the platform had to be disabled for the test to continue!
We were asked to disable our identity protection capabilities so that the actual “evaluation” could start — and we still achieved 100% prevention across all nine steps without identity protection enabled.
Why does this matter? Today’s adversaries continue to become more sophisticated in their attacks, using stolen credentials to bypass legacy defenses. Analysis from the CrowdStrike Falcon® OverWatch™ threat hunting team indicates that 80% of breaches are now identity-driven. Stopping the adversary in real time and preventing attacks from progressing requires a unified approach to security that enforces Zero Trust on the endpoint, the identity and the data.
This year, Zero Trust and identity-based protections were not part of the official MITRE evaluation. We’ll continue to work closely with the MITRE Engenuity team and advocate for a modernized test methodology that supports identity-based defenses and Zero Trust in the future.
In this blog, we will explore in more detail how the identity protection capabilities built into the Falcon platform keep customers ahead of adversaries like WIZARD SPIDER and VOODOO BEAR and can stop attacks before they start.
Falcon Platform’s Identity Defense in Action
Let us re-examine some of the MITRE Engenuity defined tests from the perspective of identity-based attacks and show the power of Falcon’s identity-based defenses.
Credential Access
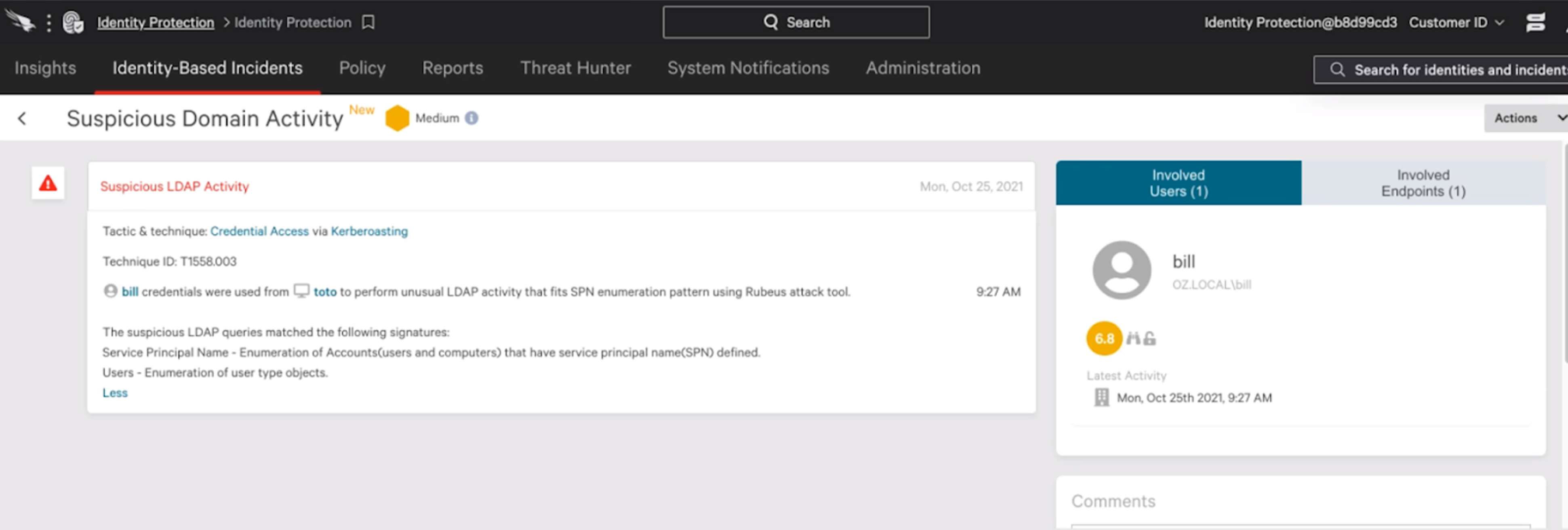
In the Initial Access step during the VOODOO BEAR emulation scenario (step 11.A.1), the evaluator used stolen access credentials to initiate the attack. Similarly, the WIZARD SPIDER scenario used the same valid account for access technique during Lateral Movement (step 7.A.2), but on a high-value target. Through Active Directory (AD) hygiene capability, Falcon’s Identity Protection capabilities determined that the password was known to be compromised well before being used. This permitted Falcon to leverage its security orchestration, automation and response (SOAR) capability and put that user on a watchlist, blocking the use of that credential. In addition, Falcon auto-classified this account as a valuable target, enabling additional security controls based on risk levels and behaviors. In a real-world configuration, the Falcon platform would trigger a multifactor authentication (MFA) challenge if those credentials were used. It's also important to note that MFA, an essential security component, was not used in MITRE Engenuity’s test environment.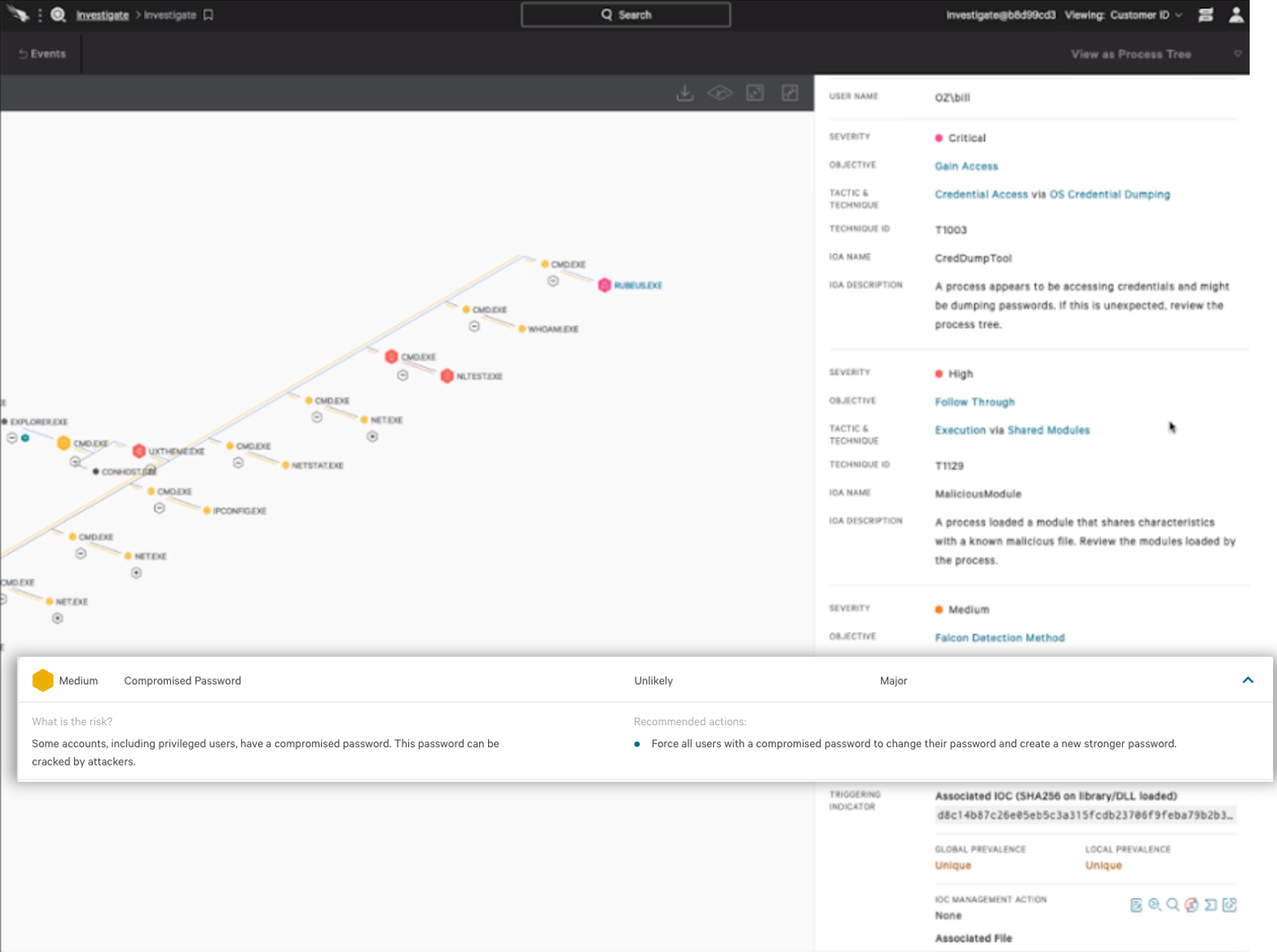 Figure 1. Falcon platform alert on the use of compromised credentials for the monitored account (Click to enlarge)
Figure 1. Falcon platform alert on the use of compromised credentials for the monitored account (Click to enlarge)Kerberoasting
The WIZARD SPIDER scenario featured a Kerberoasting attack on the domain controller (step 6.A.2), where the evaluator attempted to obtain domain admin credentials. The Falcon platform detected this immediately via the Service Principal Name (SPN) enumeration. In a real attack, the adversary would never gain access to the domain controller. Further, since Falcon detected a local file download that was considered an elevated risk, Falcon placed user credentials associated with that activity on a watchlist to ensure they could not be used anywhere else.In real-world configurations, Falcon Identity Protection’s built-in Active Directory (AD) hygiene capabilities provide security teams with instant awareness of accounts susceptible to Kerberoasting before an actual attack takes place.
Lateral Movement
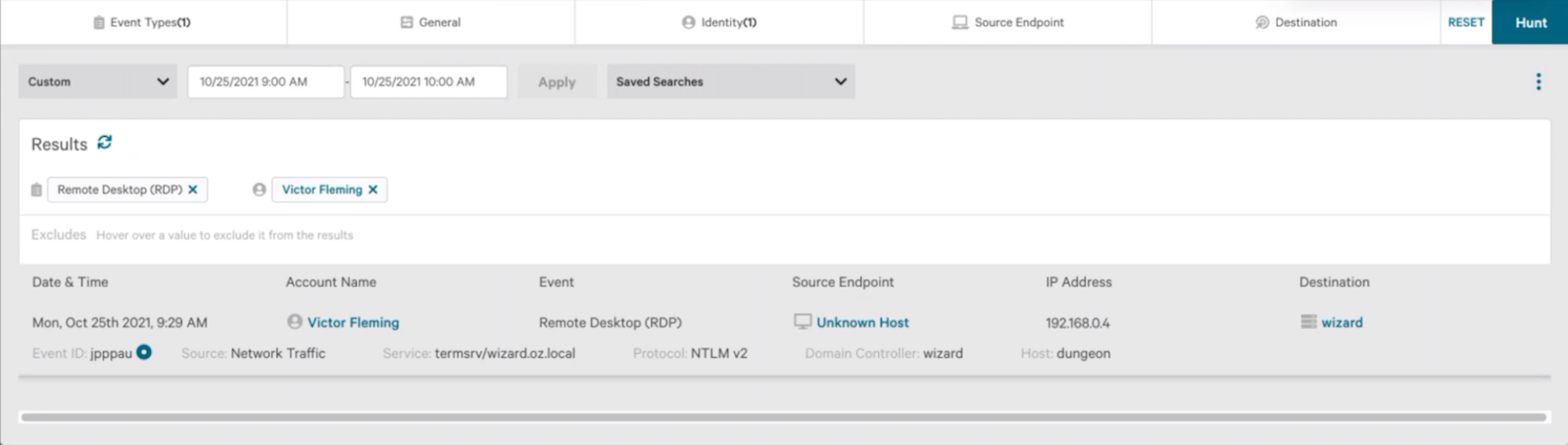
During WIZARD SPIDER Lateral Movement (step 7.A.1, similar to the RDP attempt in lateral movement and the TrickBot deployment tactic from step 4.A.1), the evaluator performed a remote desktop connection to a domain controller. In a real-world environment, Falcon Identity Protection’s capabilities would immediately restrict the remote desktop connection altogether due to the origin and/or destination IP or automatically trigger an MFA because the destination is a domain controller. In addition to policy controls, since the user was identified as involved in malicious activity and as a high risk, the authentication activity would trigger MFA challenges. Any of these security controls would halt the progress of the adversary. It is important to note that a RDP to a DC is not an attack per se and is a common activity for admins. However, the risk level it represents means additional controls need to be in place.Stop Modern Identity-based Attacks with the Falcon Platform
When thinking of modern attacks like ransomware, these advanced threat response capabilities are essential. For example, in a two-part attack like ransomware, if an endpoint is determined to be compromised, the Falcon platform can automate workflows to put credentials associated with that compromised endpoint on a watchlist. This limits the ability to leverage compromised credentials in identity-based attack techniques, such as lateral movement or privilege escalation. Adversaries only need to be right once — they can choose the ingress point and the timeline of an attack, and they frequently adapt their tactics, techniques and procedures (TTPs). Defenders, on the other hand, need to stop breaches 100% of the time. As demonstrated in the MITRE Engenuity ATT&CK Evaluation, the Falcon platform and Falcon Identity Threat Protection deliver exactly what defenders need.Additional Resources
- Learn more about CrowdStrike’s Zero Trust solution.
- Learn how CrowdStrike Falcon® Identity Protection reduces costs and risks across the enterprise by protecting workforce identities.
- Watch this video to see how Falcon Identity Threat Protection detects and stops ransomware attacks.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)